DHCP on Port vs VLAN
-
I'm migrating from an SG-2100 to SG-4200. The current struggle is to assign IP addresses in a VLAN.
What I think I want is to have Port 3 carry all the VLAN 30 traffic and have addresses in the 10.10.10.30.1/24 range using static assignments.
I configured this as:
- Port 3 (igc1) enabled and assigned a static IP of 10.10.3.1/24.
- VLAN 30 added to Port 3 on igc1 and assigned a static IP of 10.10.30.1/24.
- Configured DHCP on Port 3 and VLAN 30 with a pool of .100 to .200 with IPs under 100 for static assignments.
What I get when connecting Port 3 to my switch is IPs in the 10.10.3.x range rather than the desired 10.10.30.x range.
The corresponding switch port on my Netgear GS316EPP switch is configured for VLAN 30 with PVID of VLAN 1.
Hopefully something simple I'm not grokking.
-
@mhd353 If you have the physical port spare, why use a vlan?
Just put the 10.10.30.0/24 network on the physical port itself. -
@Jarhead
I wondered about that. Wouldn't that mean it would be the only subnet available on that physical port? Or could a second VLAN be added to that port?The end game has several more VLANs, some propagated to wifi networks. In my research it seems VLANs are necessary for different networks on same wifi AP.
I assume that regardless of VLAN or physical port, pfSense rules can be written that pass/block network acesses. Is that correct?
-
@mhd353 A port can have 1 untagged network and additional tagged networks. Keep in mind, you're sharing the bandwidth between all of them.
So you can set the .30.0 as the untagged on that port and add to it if needed. Or you can use the port without an untagged network. Up to you.
It just seemed like you have the physical port to use.
As for the AP's, you would be better off trunking a switchport to bring multiple vlans to them. Would work either way but chances are your switch would provide POE to power the AP's. Makes more sense.You're correct about the rules providing pfSense does the layer 3 for all vlans.
-
@Jarhead said in DHCP on Port vs VLAN:
Keep in mind, you're sharing the bandwidth between all of them.
Yep. I have 2 vlans that will benefit from not sharing and several that won't have enough load to matter.
So my physical port 3 with the .3.1 and .30.1 vlan DHCP are plugged into a switch port that is configured with VLANs 1 and 30. The PVID on that switch port is the default VLAN 1.
Would you recommend removing the default VLAN on the Netgear switch port or set a different PVID?
The switch is a Netgear GS316EPP in Advanced 802.1Q VLAN mode if that matters. I think this mode assigns the default VLAN as the PVID to all ports.
One other question related to the default VLAN, is there ever a reason to define a VLAN 1 in pfSense on the physical ports?
@Jarhead said in DHCP on Port vs VLAN:
As for the AP's, you would be better off trunking a switchport to bring multiple vlans to them. Would work either way but chances are your switch would provide POE to power the AP's. Makes more sense.
I agree. In my early configs I ran the unifi with its vlans trunked direct off a 2100 physical port. Since then I moved that traffic to a trunk off the pfSense → switch → unifi.
-
@mhd353 Are you using the 3.1 network?
The PVID is just the vlan the port will use for untagged traffic.
So if you're using the 3.1, leave it at 1 and tag the 30.1 vlan on it.Vlan 1 is a generic ID. Pretty much everything is on vlan 1 until you define another. So no need to ever define vlan 1 in a router. If you take your LAN port and plug it into a switchport with a pvid of 1, that router port will talk to any other switchports on vlan 1. If you change the switch pvid to 2, the same router port will talk to anything on vlan 2. The difference comes in when you use a trunk with tagged vlans on it, or a tagged router port itself.
-
@Jarhead said in DHCP on Port vs VLAN:
Are you using the 3.1 network?
Not really. I was having trouble getting IP assignments when my laptop was plugged directly into the pfSense physical port. Adding the port to interface assignment along with the corresponding DHCP lets the direct connect work.
These are my assignments currently:
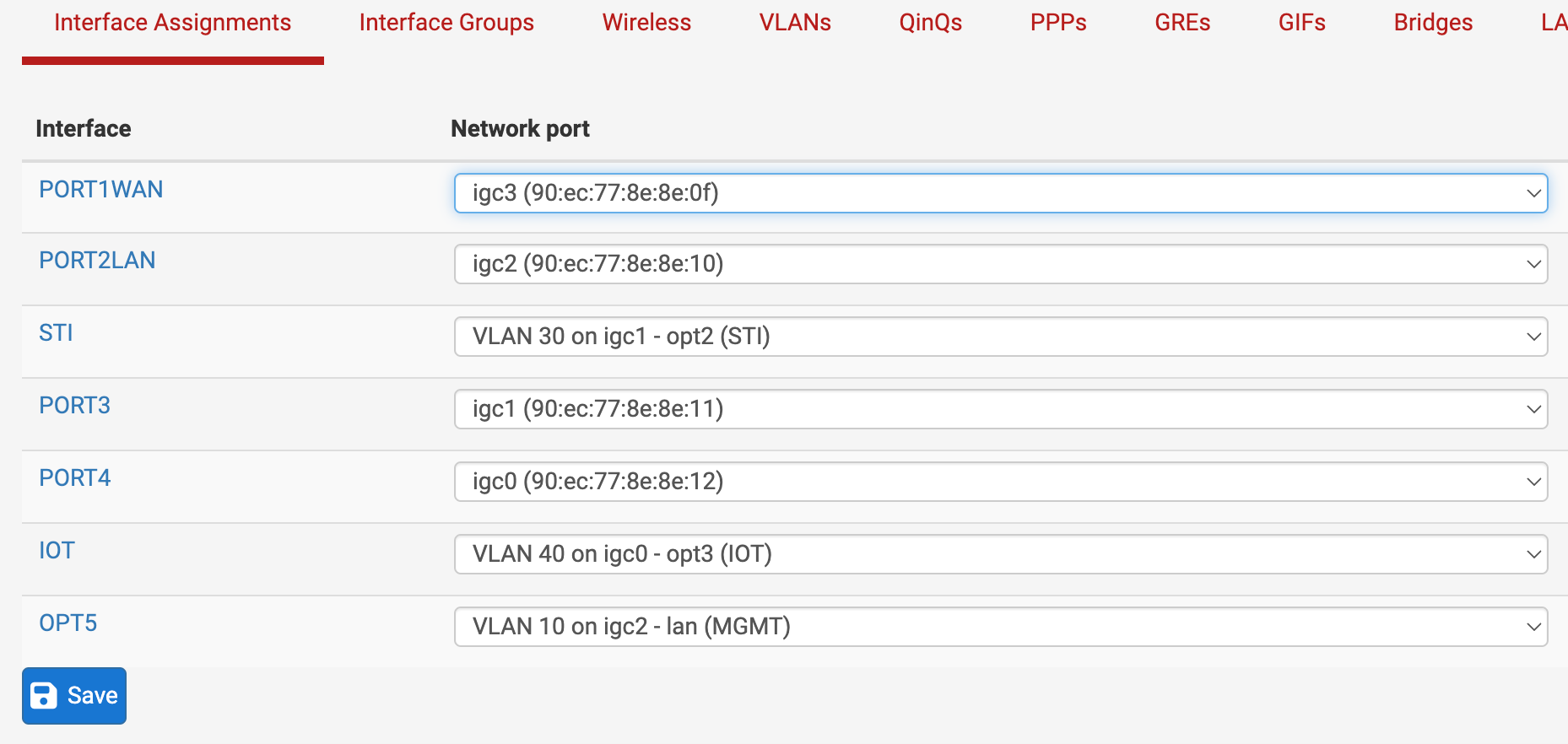
Since I don't really need the .3.1 network, should I be able to delete the PORT3 assignment without affecting the STI (xx.xx.30.1) VLAN?
This is my last question today. Tonight I need to do some more experiments to better get my head around all this. Thank you for your patience.
-
@mhd353 Yeah you could do that. Or like I said earlier, just change the 3.1 to 30.1 and use it as the native on that port, you can then add vlans later if needed. I've done it where I name the physical port "Trunk" and had no native network on it. I've also read recently that the physical port doesn't even need to be enabled but I never did that and doesn't sound like something that would work to me. Maybe I'll try it sometime just to find out.