Captive Portal not working on iOS devices only (DHCP 114)
-
@basharsaba said in Captive Portal not working on iOS devices only (DHCP 114):
Here are the new settings screenshots. Let me know why you think it's still not working.
DHCP 114 String is now "https://pfsense.afamiahotelresort.net:8003/rfc8910.php?zone=cpzone"As far as the general settings are concerned, there is no need for them to align with the domain you register. I don't think there is an issue though, it just might be a source of confusion when your pfSense firewall has the same name as your captive portal.
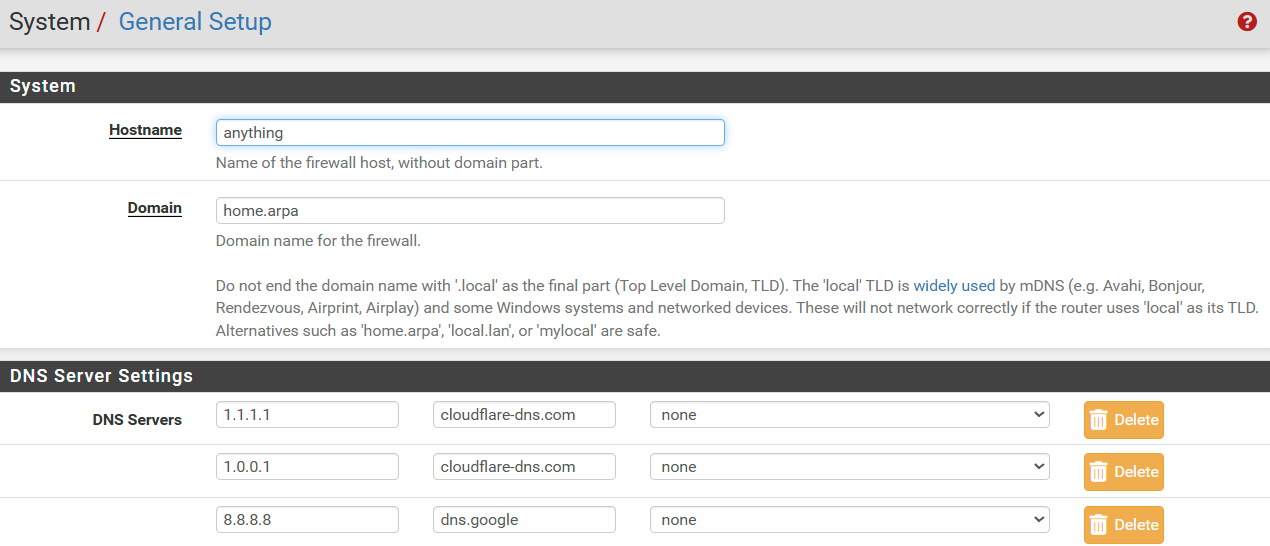
The DHCP114 string looks fine based on your previous setup info.
You need to move on from staging to the production environment for your certificate to work.
On Cloudflare you should have at least two records, afamiahotelresort.net pointed at your pfSense webconfigurator, and pfsense.afamiahotelresort.net pointed at the subnet of your captive portal. Yes, the proxy has to be off. Your SANs suggest you have that. For a "normal" setup using vlans, they would not be on the same subnet but it appears from prior communication from you that your captive portal is also on the default 192.168.1.1 subnet. That means the same DHCP server gives out addresses for your captive portal as for your LAN. It also means that all your visitors can launch the pfsense webconfigurator and only need to guess the user/pwrd to get in but as long as you are OK with that.....
For the DNS Resolver, I would put both SANs in there.
I would enable production at this stage and only then test it. It looks good from here.
-
@basharsaba said in Captive Portal not working on iOS devices only (DHCP 114):
You previously said I should have a subdomain.domain.tld that will be used for the Captive Portal. So I went to CloudFlare and created A record for pfsense.afamiahotelresort.net that is resolving to 192.168.1.1
I got an error when the Proxied option was enabled, so I had to disable it and the record was created as DNS only. Is this ok?
Perfectly ok.
You already asked and got a wild card certificate.
So "pfsense.afamiahotelresort.net" or "portal.afamiahotelresort.net" or "whatever.afamiahotelresort.net" is already accounted for.Um' not sure what you are doing here :
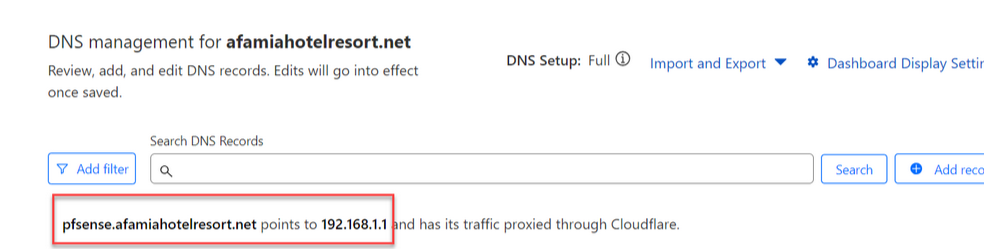
Where is this ?
On pfSense, there where "192.168.1.1" has a meaning (192.168.1.1 = RFC1918 = only locally and never 'on the Internet').
You should have :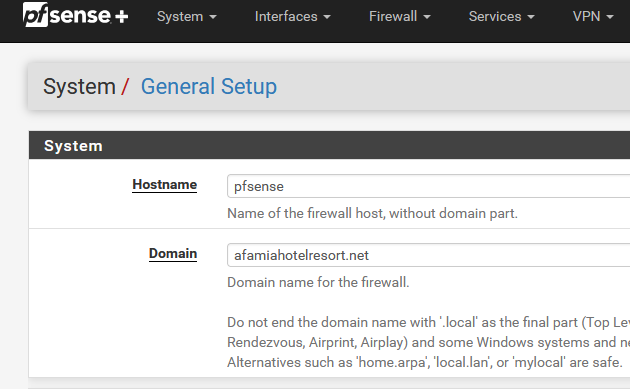
and your good.
@basharsaba said in Captive Portal not working on iOS devices only (DHCP 114):
Is it because I used the ACME Staging, not Production?
"Staging" is for testing. Useful as you can test the DNS API as long as you want.
Maybe it's time to actually read the Letsencrypt manuals, guidelines etc ??
The "production" isn't good for testing, as you can only fail a couple of time, and then you have to wait for days to get a new cert.
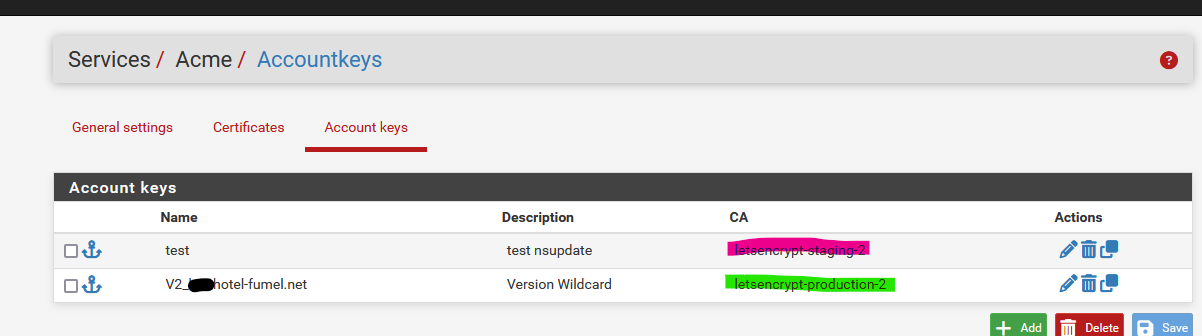
-
I had to wait all this time until LE finally allowed me to issue a Production Certificate.
I want to update you that all the devices of all kinds are finally working without issues and getting a secure connection with a valid certificate. Having a dedicated domain on Cloudflare was a very wise idea.
I wouldn't be able to achieve that without your advice and assistance. You guys rock.
One last question. I have enabled Cron Entry. From your experience, will it really renew the certificate automatically after 90 days? Or am I still supposed to click the blue Issue/Renew button?
Apparently, the "Certificate renewal after" field doesn't matter at all because regardless of how many days I set, it's still 90 days as per LE.
-
@basharsaba
ACME will renew every 60 days and it works well with the default settings.
Congrats on your success.
-
@basharsaba said in Captive Portal not working on iOS devices only (DHCP 114):
From your experience, will it really renew the certificate automatically after 90 days? Or am I still supposed to click the blue Issue/Renew button?
Check the cron entry :
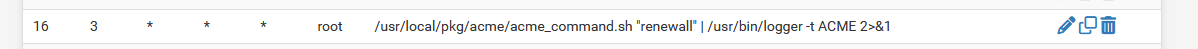
To see it, install; the pfSense Cron package first.
The need-to-renew-test runs every day, mine at : 03h16.
Now check the system log : to no surprise :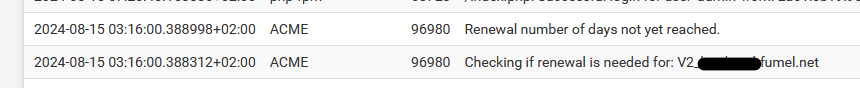
Don't use '90' as a certificate renewal, but something between 30 and 60.
That leaves you with 60 to 30 days to resolve an issue IF something went wrong.
"90" will leave you with no spare time to resolve the issue.Btw : I'm using acme for years now, and it never failed. if it did, it was because the admin (me) was messing up again.
That said, free services or even when you pay for them : don't auto trust them, think about putting in place automated checks like this (very old munin based monitoring system). You can see that I check 2 domains there, and they are renewed after 30 days, and the other 60 days. Is like clock work. -
I've noticed something.
The scenario :
My PORTAL network :
192.168.2.1/24 - DHCP pool 192.168.6 -> 192.168.2.254
192.168.2.2, 3, 4, 5 = 4 APs with a static IP setup, DNS and gateway set to 192.168.2.1Normally, when I connect with my iPhone, I always get the same IPv4 : 192.168.1.6 because I created a DHCP MAC lease for my iPhone.
Now, when I add my IPv4 192.168.2.6 to the "allowed IP address" list :
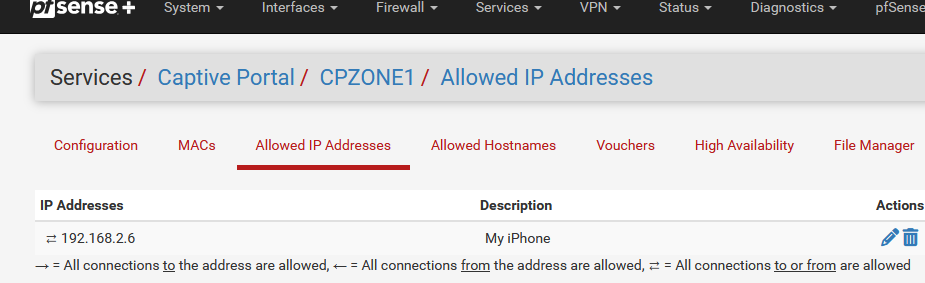
I killed all Portal sessions, relaoded the Portal on pfSEnse, and then reconnected my iPhone.
I still got the login page ....It took me the better half of this morning that .... this is totally 'ok' as my iPhone, as soon as it receives a DHCP lease, it knows right away it has to go to
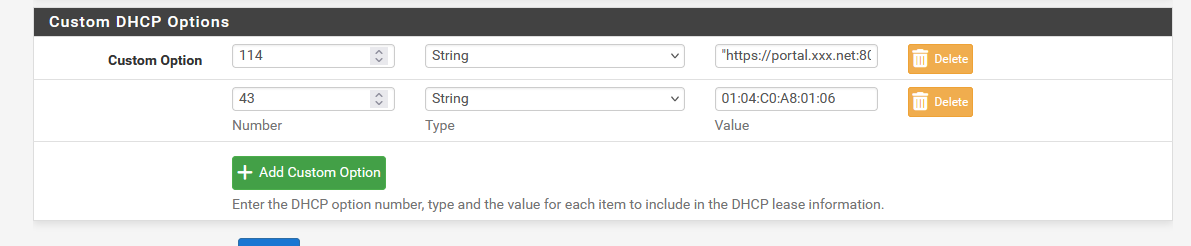
= "https://portal.xxx.net:8003/rfc8910.php?zone=cpzone1"
Before, when an IP was white listed like this, the portal became transparent for the device using that IP.
So, not really an issue, I was actually looking for a 'problem' that didn't exist.
Just : keep in mind that "rfc8910" method will not allow the bypass "allowed IP address" method.
edit : MAC list : probably same thing, didn't test yet.
-
Did you "forget" the iPhone "My Network"? I have noticed when testing RFC8910, DHCP 114 that it is/can be "sticky". As I switched between Kea and ISC, I had to remember to forget the old network on the iPhone, otherwise it appeared to be working under Kea when it actually had saved the login info from when it connected under ISC and received a 114 option, even though it got a different IP address. You can also switch "auto login" off and see if it has internet connectivity as that will prevent the captive portal page from loading, even if received via DHCP 114.
-
@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
Did you "forget" the iPhone "My Network"?
Yep, did that, as part of the 'clean slate' approach.
@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
I have noticed when testing RFC8910, DHCP 114 that it is/can be "sticky"
I have that impression also. Probably some iPhone side coding doing 'its' thing.
@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
As I switched between Kea and ISC
I saw your discussion with marcos on Github about the upcoming kea implementation.
Progress is looking fine.@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
You can also switch "auto login"
I'll experiment with that one

-
For the "rfc8910.php" file :
if (is_array($cpcfg['allowedip'])) { foreach ($cpcfg['allowedip'] as $ipent) { if ($ipent['ip'] == $clientip) { if ($ipent['dir'] != 'to') { // Bail out, 'clientip' is part of the 'allowedip' list ob_flush(); return; } } } }If there is an array with "allowedips"
For each IP in the array,
If the IP of the portal c;lient matches an IP in the list,
And if the direction in not 'to' (thus 'both' or 'from'),
Then flush and return.This will take of he devices that are on the "allowed IP" list, they won't get login page anymore.
Take note : this works for 'English' portals. Afaik, the text 'from' 'to' and 'both' might be different for another languages.
-
@Gertjan said in Captive Portal not working on iOS devices only (DHCP 114):
This will take of he devices that are on the "allowed IP" list, they won't get login page anymore.
I confirmed that the same symptoms are present for "allowed IP" in Kea as I assume you were using ISC. I also confirmed that the fix works in Kea.
It is important to note that in order to have DHCP allocate a Static IP to a Mac address, that address must be outside the dynamic allocation pool for that portal's DHCP server.
It is also important to note that many devices change the MAC address every time you connect so you must turn off the "Private Wi-Fi Address" option on the iPhone for example. When you forget and add it again, it will reset to a dynamic Wi-Fi Address so the MAC will change and your static mapping will no longer be used.
The fix to RFC8910.php suggested simply prevents the device from intercepting the "capture" from the captive portal and it goes directly to the captive portal where it is allowed through, exactly as desired. There are negative consequences to this, first amongst them for me is that the "Open Captive Portal Page" option is not available on the iPhone for example. We use this to inform the client as to time, data quota, number of simultaneous users, time to automatic reset of account and potentially other important information (like logout) about their status. This is possible because DHCP 114 is sending the login URL to the captive portal every time you either log onto the Wi-Fi or click that option under the circled i on the iPhone for example. Captive portal will load the logout page if the device is already logged into the Captive Portal. Thus, we use the logout URL to provide this info. Once you bypass DHCP 114 through RFC8910.php this information will no longer be available. Loading the login URL manually will simply load the login page because, of course, a passed through IP is not logged in.
For this reason, thermostats, other IOT devices may use/need this feature but it is defeating the purpose of RFC8910 and must be applied for that reason, not to bypass the captive portal login screen. Once you are logged into the Captive Portal, you stay logged in until conditions are met to log you out automatically, time, data, etc. That is a preferred method of solving the problem of simply avoiding the login screen itself. Even for thermostats and other devices, they typically ignore RFC8910, DHCP 114 anyway and simply work by passing through their MAC address or an allowed IP in Captive Portal thus we never even noticed this issue to date. You preserve the login over a reboot by checking: Preserve users database ->Preserve connected users across reboot. If enabled, connected users won't be disconnected during a pfSense reboot.
-
Your last to phrases :
The fix to RFC8910.php suggested ...
and
For this reason, thermostats, ....
That's what I had in mind : 'thermostats', APs, smart switches and whatever other devices hosted on the portal network, these devices are typically white listed by using "Allowed IP" (and/or MAC probably) are mostly automates that don't know sh#t about portal login and/or don't use DHCP 114 (RFC8910) anyway - as you said already.
These devices won't consult the the portal's "venue-info-url" neither.The same type of filtering against the two "Allowed IP" and "MAC" lists isn't needed in the original portal's index.php
That said, devices have their MAC listed as "blocked" do inform the connected user with a message that his MAC is blocked (inviting him to change his MAC address ^^).Updated : I've also added MAC listed handling :
if (is_array($cpcfg['allowedip'])) { foreach ($cpcfg['allowedip'] as $ipent) { if ($ipent['ip'] == $clientip) { if ($ipent['dir'] != 'to') { // 'clientip' is part of the 'allowedip' list ob_flush(); return; } } } } $clientmac = pfSense_ip_to_mac($clientip); if (!is_array($clientmac)) { if (!isset($cpcfg['nomacfilter']) || isset($cpcfg['passthrumacadd'])) { /* unable to find MAC address - shouldn't happen! - bail out */ captiveportal_logportalauth("unauthenticated", "noclientmac", $clientip, "ERROR"); echo "An error occurred. Please check the system logs for more information."; log_error("Zone: {$cpzone} - Captive portal could not determine client's MAC address. Disable MAC address filtering in captive portal if you do not need this functionality."); ob_flush(); return; } } else if (is_array($cpcfg['passthrumac'])) { foreach ($cpcfg['passthrumac'] as $macent) { if ($macent['mac'] == $clientmac['macaddr']) { if ($macent['action'] == 'pass') { // 'clientmac' is part of the 'allowed MAC' list ob_flush(); return; } } } }I took the initial MAC testing directly from the portal's 'index.php' file : if no MAC was found, but MAC usage isn't' disabled, then messages are logged/shown.
-
@Gertjan
Good Work, I tested the fix(es) under Kea/Plus 24.08 Dev (0925) and they work as advertised. I suggest you publish the full updated RFC8910.php here so others can quickly get the current result of this project to date. -
Lately, I see more and more devices making use of DHCP option 114, which means they load the rfc8910.php file as soon as they connect to the portal wifi :
In just 5 hours :
2024-11-11 17:03:50.982716+01:00 logportalauth 4858 Zone: cpzone1 - cpzone1: rfc8910, NEW SESSION : portal.portal-url.tld:8003, 192.168.2.19 2024-11-11 15:59:16.128747+01:00 logportalauth 55790 Zone: cpzone1 - cpzone1: rfc8910, NEW SESSION : portal.portal-url.tld:8003, 192.168.2.145 2024-11-11 15:27:08.008311+01:00 logportalauth 94285 Zone: cpzone1 - cpzone1: rfc8910, NEW SESSION : portal.portal-url.tld:8003, 192.168.2.192 2024-11-11 14:51:05.807693+01:00 logportalauth 74770 Zone: cpzone1 - cpzone1: rfc8910, NEW SESSION : portal.portal-url.tld:8003, 192.168.2.173 2024-11-11 11:59:40.897204+01:00 logportalauth 33392 Zone: cpzone1 - cpzone1: rfc8910, NEW SESSION : portal.portal-url.tld:8003, 192.168.2.248and for what it's worth : since I'm using this 'addon' file I have the strong impression the portal access is working better as the native 'http intercept' method that pfSense offers.
Close to none come to the hotel reception anymore to ask confirmation about how to connect to the hotel's Wifi. People connect, login, and do their thing. -
@Gertjan said in Captive Portal not working on iOS devices only (DHCP 114):
People connect, login, and do their thing.
Yes, very little support required. The most common inquiries are due to auto login getting turned off (they click "use without internet") and don't understand they have to forget and reconnect. Typically that happens only once though. With Captive Portals that have "last login" set it is not unusual to see 4 or 5 logins per minute as families just there for the day share a 24_Hr voucher so it can get quite a workout. It has been trouble free.
The other feature in iOS is the "Open Portal Page" feature under iOS 17 and above. This opens the Venue URL option in RFC8910 and we use it to provide time and data quota remaining information. Once shown this, all the questions about how much time or data remains on their account also go away. This is particularly true for those with weekly and monthly access, especially those Portals that provide multi user/account access where Data Quota and Time Quota are shared. Once shown this feature (click the circled i beside the WiFi Network name) they also tend to not require any further support. At any point in time during the busy summer period, this could involve up to 500 connected devices so having no support for that quantity is a real compliment to RFC8910 and DHCP 114. iPhone users are also getting familiar with these features and starting to demand them. The RV Park now hands out a info page on WiFi that mostly explains how iPhone and Android support logins and how to use the "Open Portal Page" feature to track their account status. That helps reduce support as well.
We need pfSense to support DHCP 114 under Kea (there is an unsupported patch (see Redmine feature #15321) which is working for me in the Lab under 24.11 Oct Beta. Kea now includes DHCP 114 as a built in option, not a custom one as per ISC. It is just the pfSense Plus GUI that doesn't support it yet and I have been told it won't in the stable release of 24.11 either but it should be there after that. ISC does work as a custom option so no excuse not to implement it.
-
@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
We need pfSense to support DHCP 114 under Kea (there is an unsupported patch (see Redmine feature #15321) which is working for me in the Lab under 24.11 Oct Beta. Kea now includes DHCP 114 as a built in option, not a custom one as per ISC. It is just the pfSense Plus GUI that doesn't support it yet and I have been told it won't in the stable release of 24.11 either but it should be there after that. ISC does work as a custom option so no excuse not to implement it.
It saw your redmine.
I was wondering for a while :
This - on the captive portal's configuration page - is not rocket science :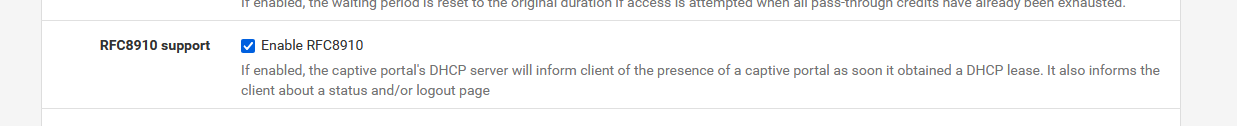
When the option is set, and the interface is known (and safety check : if a DHCP server is set up to run on this interface, which is imho pretty mandatory) then the portal setup page should modify the DHCP server settings of the interface to include :
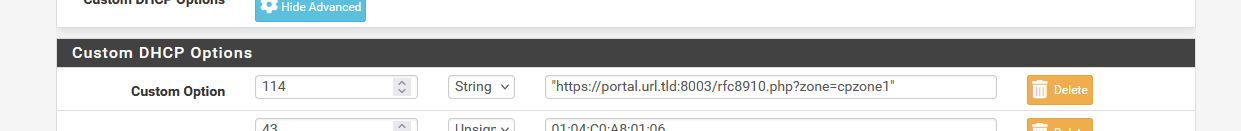
where the portal URL is :
If https was chosen, the interface IPv4 otherwise.
The port number (8003 here) is avaible in the portal config.
The zone ID (name) is avaible in the portal config.
The file name "rfc8910.php" is arbitrary, and must exists in the /usr/local/captiveportal folder.What I don't like about this way of implementing things : a configuration setting on the captive portal's configuration page will "add" (replace ? remove ?) a configuration 'option' setting on the related DHCP server page.
Something in my head says that that is not the way of doing things.So: Plan B : way easier, but needs some action from the admin :
When the RFC8910 option is checked on the portal configuration page, have it appear an extra help line that shows what to do :Go to the DHCP server page, and under "Custom DHCP Options" add : Number : 114 Type : String Value : "https://portal.url.rld:8003/rfc8910.php?zone=cpzone1" (with the double quotes).Forgetting to do this won't break anything.
But unchecking the RFC8910 portal option needs a reminder that manually this option needs to be removed under the "Custom DHCP Options".
Hummm, not perfect good neither. -
I personally see RFC8910, DHCP option 114, as belonging in the DHCP setup exclusively. Currently with ISC there is the warning to enable DHCP on the Captive Portal and that warning should include a statement to the effect that DHCP option 114 should be configured for DHCP as well. Option 114 in Kea is not a custom option, it is one of the supported options that are included in their standard setup, you simply fill in the info.
Having said that, it is not simple, especially when you consider that option 114 also offers up both at True/False (for the login page) determination and a vendor URL option that is potentially unrelated to the Captive Portal. You bring up a good point that simplifying that for end users wouldn't hurt. To that extent, it would be nice if the GUI within Captive Portal had a check box to provide a sample set of code, not unlike what it does for the login page. It could then place that code into the appropriate directory and have a button to populate (or suggest) the DHCP option 114 for that specific interface.
There is no point in modifying ISC any longer and with no GUI for Kea yet, we don't know how they intend to handle all DHCP options, not just DHCP option 114.
We do have a working solution for the Plus 24.11 Oct 31 Beta that works with the code presented in this discussion and it appears we will need to continue using this until the Plus release starts with a 25. For CE users it is up and running as a custom option, also workable.
Maybe Netgate is listening and will acknowledge that Captive Portal use represents a substantial number of installations of the product and deserves addressing this in the next GUI for all future releases of both CE and Plus?
-
You're right.
Instead of mentioning RFC8910 on the captive portal configuration page, it should be mentioned on the DHCP server page (ISC, KEA, whatever).The "option 8910" should show up if the interface used by this DHCP is also used on a configured captive portal.
The info needed to create the "DHCP Option 114" URL can be sourced from the captive portal instance that is using this interface.
This is a cleaner solution.At the bottom of the captive portal configuration page, a reminder should be added here :
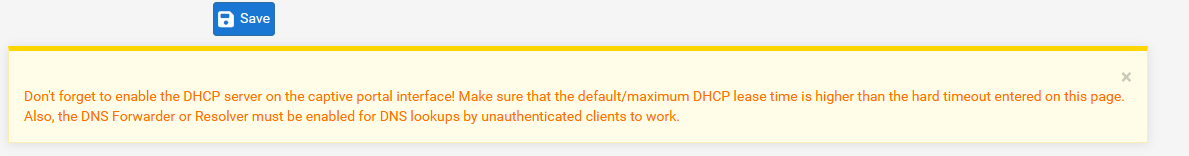
that an active captive portal has the new option "8910" available on the DHCP server page.
I get it, this will be something for the future.
For me, the RFC8910 is already working just fine for 6 months now, and it will also work for me whatever 24.11 offers (I'll patch it if needed).
Right now, adding 8910 is rather easy to do : adding a file and adding adding a "DHCP 114 option" and done.Normally, a DHCP server (ISC, Kea, whatever) offers DHCP options, and adding custom option isn't a ISC only thing. Kea supports them just fine. It's probably just the pfSense GUI front end that will be missing the needed logic to implement it.
-
@Gertjan said in Captive Portal not working on iOS devices only (DHCP 114):
Normally, a DHCP server (ISC, Kea, whatever) offers DHCP options, and adding custom option isn't a ISC only thing. Kea supports them just fine.
Yes, but as testing the patch demonstrated, Kea is very fussy about if the option is custom or built in. Enabling DHCP 114 as a custom option under Kea in the patch (https://redmine.pfsense.org/issues/15321) crashes Kea. It is essential you use the built in label for DHCP 114 in Kea, that label is "v4-captive-portal". You will place the string in association with that label in some unknown way as no GUI exists yet for Kea.
-
@Gertjan
Look at Redmine Feature #15904 at https://redmine.pfsense.org/issues/15904
and help move this along if you like the idea.The objective is to support RFC8910 on Captive Portal right out of the box by simply checking an automatic support checkbox in KEA when the GUI arrives.
I would also like to point out that the current RFC8910.php file is no longer compatible with the index.php implementation under 24.11, despite the fact it appears to work ... so far.
-
@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
Look at Redmine Feature #15904 at https://redmine.pfsense.org/issues/15904
and help move this along if you like the idea.That the file I'm - my captive portal users - using since ... 6+ month now.
@EDaleH said in Captive Portal not working on iOS devices only (DHCP 114):
I would also like to point out that the current RFC8910.php file is no longer compatible with the index.php implementation under 24.11, despite the fact it appears to work ... so far.
Strange.
I didn't change my copy of "RFC8910.php" for several weeks or month now.
The one I'm using now, is the one I was using for month with 24.03.That said, my copy is somewhat different - I've less lines.
This is the copy shown in the redmine 15904 : https://redmine.pfsense.org/attachments/6335
My version is a bit smaller :Line 13 : Not needed. I commented it out. ( all the globals aren't used, not referenced in the file)
Line 26 : Not needed, I commented it out ( $cpzoneid isn't used anywhere)and that's it. The rest is the same.
Again : I didn't modify this file for months now. Ugraded to 24.11 and everything was working as before.
True, When switching to kea, I had to apply the patch and make this 100 % correct :
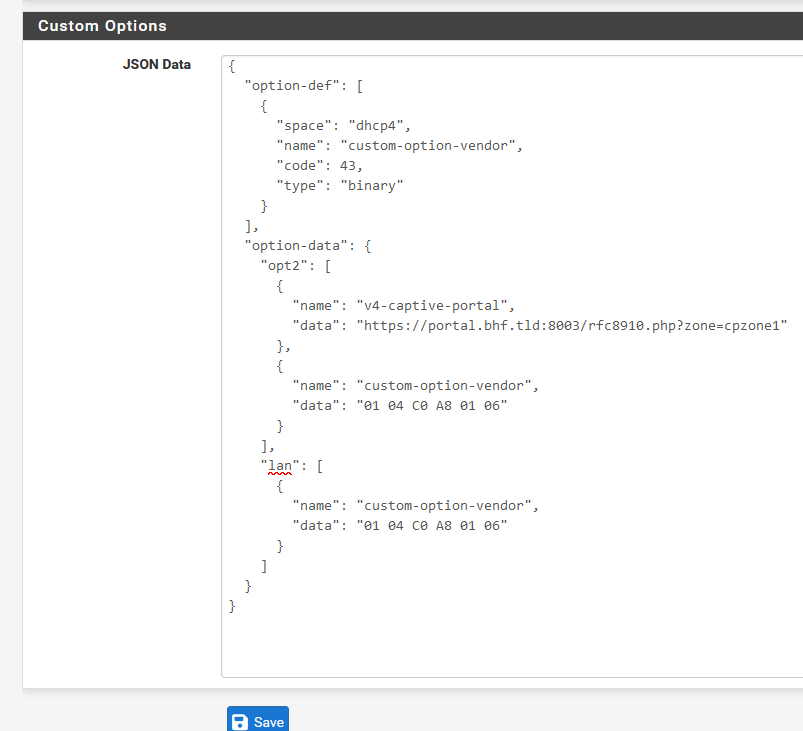
{ "option-data": { "opt2": [ { "name": "v4-captive-portal", "data": "https://portal.bhf.tld:8003/rfc8910.php?zone=cpzone1" } ] } }To make 'rfc8910' work.
"opt2" as my captive portal lives on "opt2", "rfc8910.php" is the name of the file. "cpzone1" is the name of my portal zone, "portal.bhf.tld:8003" is the URL of my https captive portal.
My entire JSON structure = kea config settings is somewhat bigger as I also use Unifi AP's for my captive portal and on my LAN interface ("lan") and these make use of a DHCP custom option 43.
This "43" one is special as it it not defined / not known to kea. The server needs to "learn" about it first, it has to be 'defined' before it's used.That's what the "option-def" and "name": "custom-option-vendor" and "data": "01 04 C0 A8 01 06" (== for me IP 192.168.1.6) is all about.
Actually, when you know what is needed, and what it does, it's really simple

For me, https://redmine.pfsense.org/issues/15321 was of great help.
Of course, the example Dale Harron showed missed a '{' quoto somewhere, but the general idea was ok.
You said it your self : kea does not allow mistakes - it doesn't allow fussy logic ^^