How to setup WireGuard on a dedicated OPT/ethernet port?
-
Hello
Using latest 2.7.2 pfsense on a hardware with 4 ethernet ports
Currently on Interface assignments
Ethernet port1: IF_WAN
Ethernet port2: IF_LAN
virtual port for WireGuard: IF_VPN_WG0I have setup WireGuard successfully following the available documentation but the traffic is going through my LAN ethernet port
I want to allocate one of my available ethernet ports e.g. ethernet port 3, on the pfsense just for the VPN so that only hosts connecting via ethernet port 3 have access to the remote VPN LAN for all traffic.
Traffic through LAN port should not have access to the VPN.Can you please refer me to any relevant documentation or any tips?
VPN_HQ LAN: 10.0.1.0/24 IF_VPN_WG0: 172.16.0.1/24 Gateway: GW_VPN_WG0 Interface: IF_VPN_WG0 Gateway: 172.16.0.2 StaticRoute: Destination network: 10.0.2.0/24 GAteway: GW_VPN_WG0 VPN_HQ Firewall Rules IF_WAN PASS Protocol:UDP From:SiteB_WAN_IP To:SiteA_WAN_Address port 51820 IF_VPN_WG PASS Protocol:ANY From:ANY To: ANY ################################## SiteA LAN: 10.0.2.0/24 IF_VPN_WG0: 172.16.0.2/24 Gateway: GW_VPN_WG0 Interface: IF_VPN_WG0 Gateway: 172.16.0.1 StaticRoute: Destination network: 10.0.1.0/24 GAteway: GW_VPN_WG0 SiteA Firewall Rules IF_WAN PASS Protocol:UDP From:SiteA_WAN_IP To:SiteB_WAN_Address port 51820 IF_VPN_WG PASS Protocol:ANY From:ANY To: ANY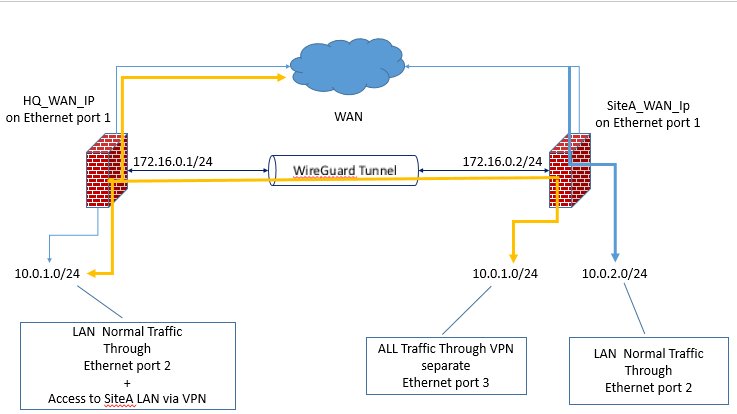
Kind regards
Nikolas -
@java4dev That is not a Wireguard question but a firewall rule question. Just make rules for your destinations and set the gateway accordingly.
-
@Bob-Dig I tried to assign OPT2 as IF_VPN_WG01 with IP 172.16.0.3/24 but pfsense complains that
IPv4 address 172.16.0.3/24 is being used by or overlaps with: IF_VPN_WG0 (172.16.0.2/24)I tried to create a gateway GW2_VPN_WG0 to 172.16.0.1 and I get
The gateway IP address "172.16.0.1" already exists.So how should I configure OPT2?
and do I need a separate gateway or can I reuse existing one GW_VPN_WG0? -
@java4dev Tunnelnetwork is only used for that tunnel, don't create yet another gateway. And don't use 10.0.1.0/24 on both sides, use it on one side (HQ) and use something different on the other side. Then make a route on "site A" for 10.0.1.0/24 to the wireguard gateway 172.16.0.1.
-
@Bob-Dig I already have a static route in place
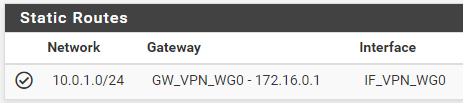
I setup the OPT2 as
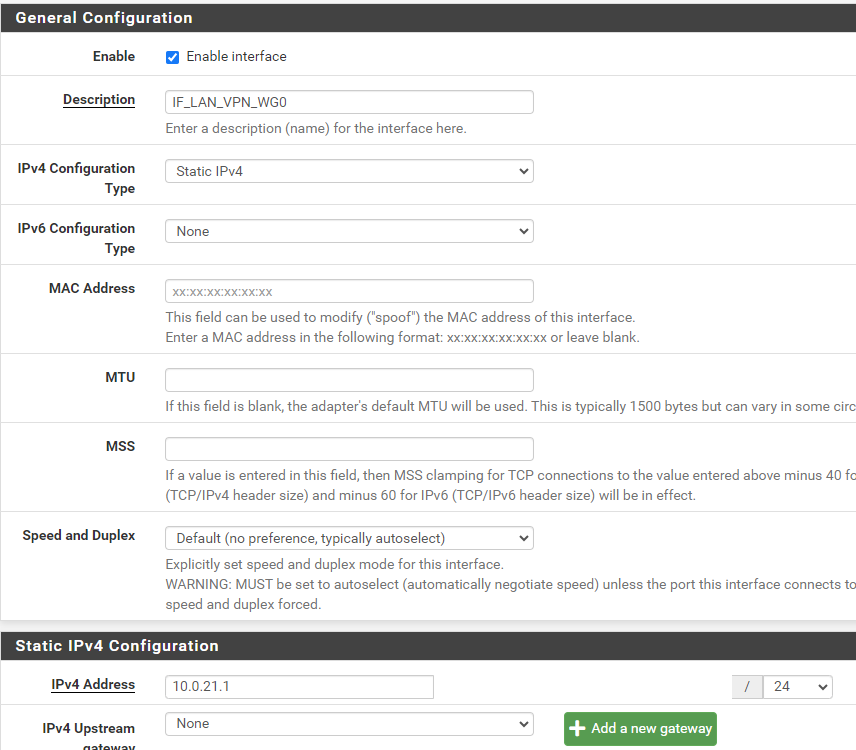
What are the next steps so that ALL traffic (both internet and to HQ_LAN) from IF_LAN_VPN_WG0 goes only via the VPN?
Any host connected on the LAN_VPN should see as WAN the HQ_WAN_IPI have updated the network diagram with comments to clarify the goal
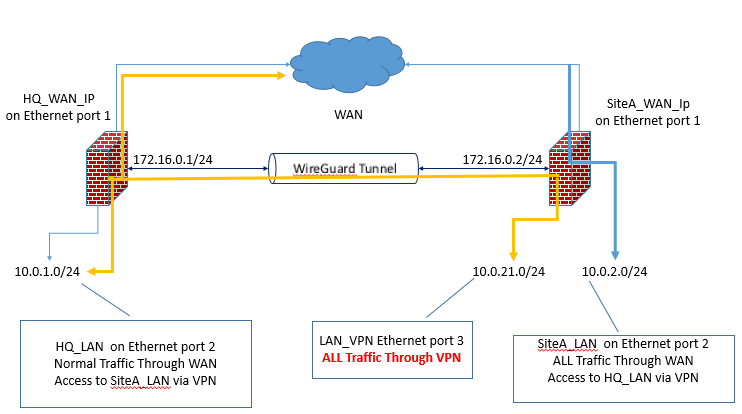
-
@java4dev Make a broad rule (Destination any) and set 172.16.0.1. as the gateway in the Advanced Options of this rule on your "port 3" network.
And if you had not til now, you have to add 0.0.0.0/0 as Allowed IPs to the peer HQ on "SiteA". -
@Bob-Dig That looked exactly what I was looking for and really thought that would be enough, but still no traffic from LAN_VPN to either HQ_LAN or internet.
I even tried rebooting pfsense but it didnt help -
@java4dev You also need routes and the correct config of Wireguard at Site HQ.
If you don't figure it out, post a lot of screenshots I guess.