pfsense firewall rules and frr for bgp
-
Successfully setup pfSense in firewall mode with no NAT and FRR for BGP, accepting Full Tables for IPv4 from my single upstream and successfully announcing my single /24.
How do I setup the firewall rules now?
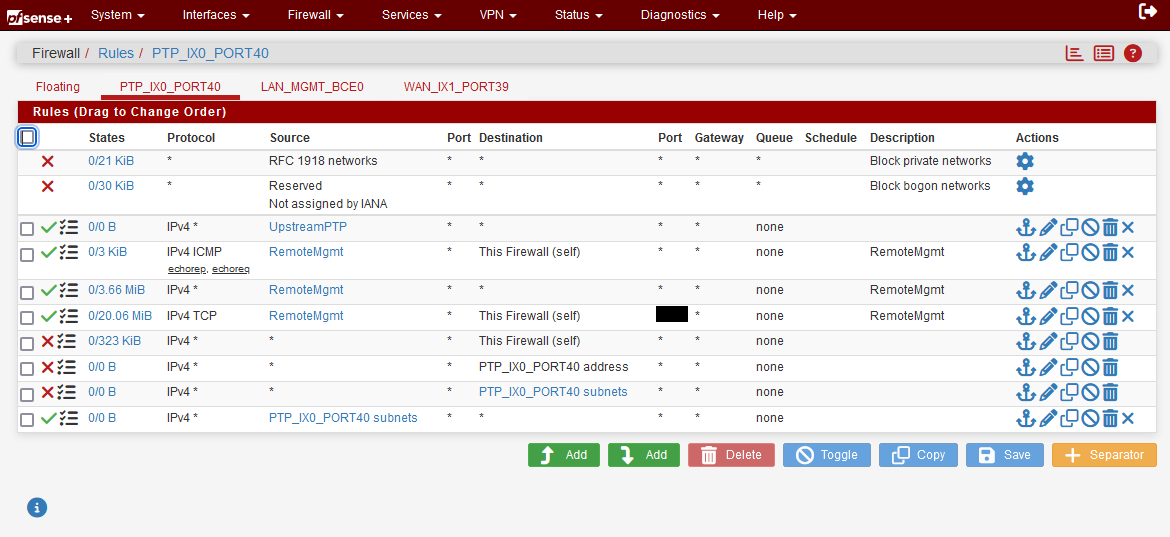
If I don't Allow All incoming on the PTP Interface to any any, then no traffic passes through.
If I allow All Incoming Any Any, my logs show the world scanning every port and every IP on my /24.
-
@ericlee Why would you take a full table if you only have one upstream? They can just default-originate instead.
Pass the BGP from the peer and pass the traffic you want to allow in to your /24. If that is zero inbound connections, then you're already done.
-
@Derelict - upstream will only send full tables, that's not my immediate concern, my concern is how do I run firewall rules so I can only allow legit traffic.
Behind it are a bunch of hosts and other pfsense firewalls with a single WAN from /24 and LAN from rfc1918 blocks doing traditional web/file/print/corp/vpn/etc...
Again I don't want to disable pf and make it as a plain router, hence my original post.
-
@ericlee Define legit traffic and make pass rules for that traffic.
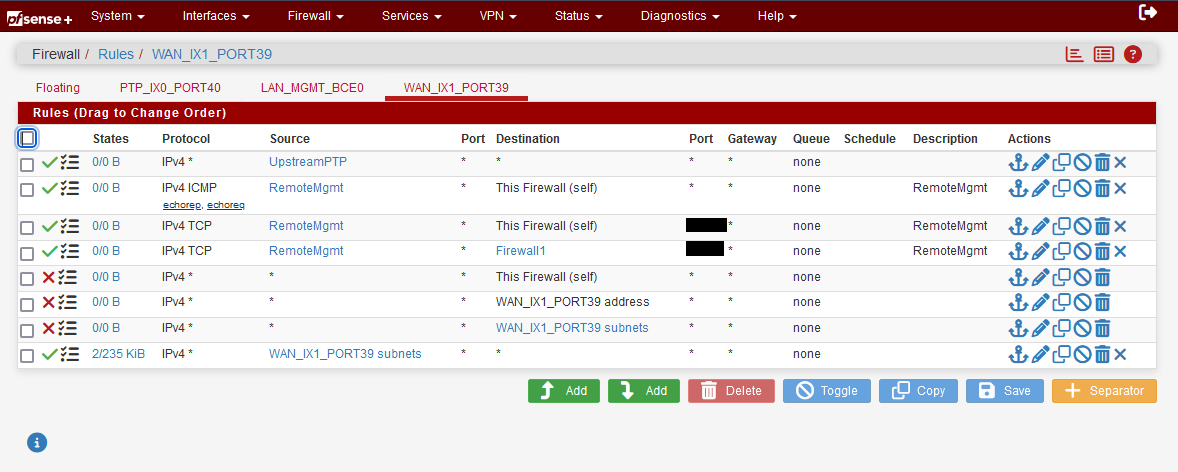
You do not need any rules on WAN except those necessary for the BGP session to come up should your peer connect to you instead of you connecting to them (it could happen either way).
Everything else inbound should be blocked except those connections you consider to be "legit."
-
@Derelict - Gave up on pfSense for BGP, switching to CHR instead and will continue to use pfSense for firewalling where it shines.
-
@ericlee
so confused from start to finish on this post... -
@michmoor - Let me summarize...sub-leasing a single cabinet at a datacenter, single 1g upstream, wanted to use pfSense with NAT disabled to announce 2 x /24 using FRR for BGP.
If I don't enable certain firewall rules, incoming traffic doesn't pass through. I was able to get it working for 1 day until everything stopped working, after a few days of troubleshooting and working with the upstream, I came to the conclusion I did something wrong.
So I tried CHR and that worked and then it stopped working also after a certain time.
Anyhow due to lack of time, the upstream is now temporarily announcing the netblocks instead, I was able to replicate data from old datacenter with minimal downtime.
Turns out that BGP was working for a bit and then somewhere up the chain, which I don't have visibility on, the packets were being discarded and this came to light only after the upstream tried to announce the networks.
When I have time I am going to move one of the /24 back to pfSense and test with FRR.
-
@ericlee Thank you for additional details. Did you ever disable the firewall on pfsense?
-
@michmoor - Yes, disabling the firewall didn't solve the issues, but I don't want a router only without any firewalling capabilities exposed to the public internet.