Suricata IPS block out trafic WAN interface
-
Hello,
I'm coming to you because I managed to configure Suricata's IPS mode without any problem.
I've configured it to block only SRC IPs.
The only problem is that I want it to block only traffic entering the WAN interface on the Internet side.
As soon as I get an alert the SRC IP is blocked, but it also blocks my LAN > WAN traffic.
Is there a configuration for this?Thanks in advance.
-
Local hosts and all firewall interfaces should be in the automatic default passlist and thus not get blocked. Have you modified the passlist setting in any way?
Can you be more specific with what IP addresses are getting blocked unexpectedly?
IPS mode drops individual packets and does not "block" an IP address. Do you have Legacy Mode Blocking enabled perhaps and not Inline IPS Mode? If you configure Inline IPS Mode, you will need to create appropriate SID MGMT configuration files to change the rule actions to DROP from their default of ALERT.
-
@bmeeks I haven't modified my configuration: IP Pass List
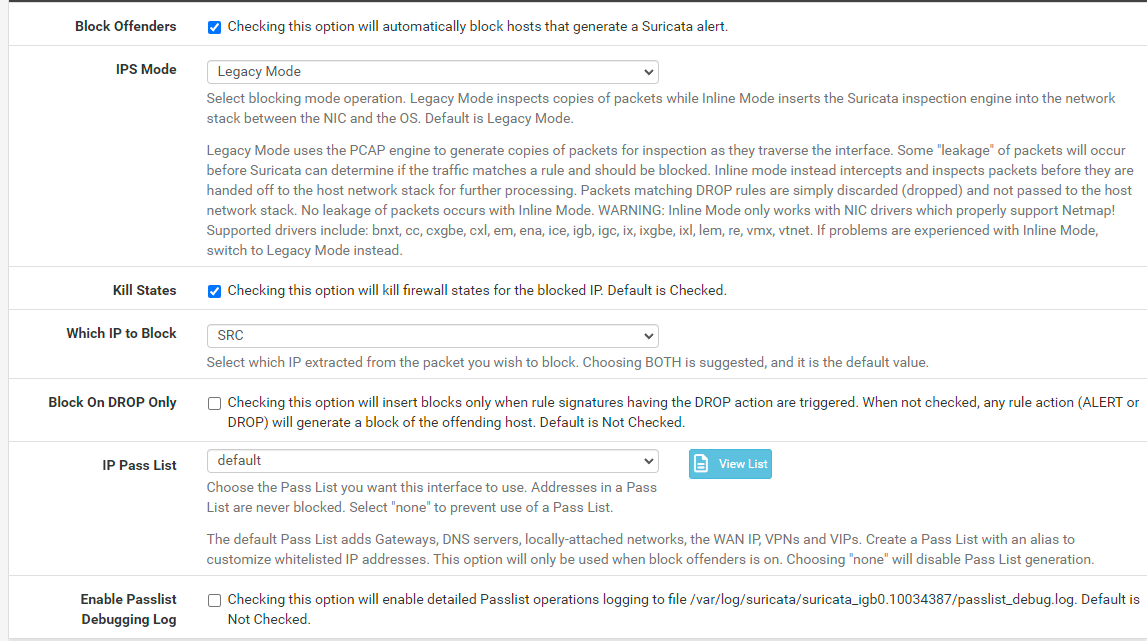
With this configuration, as soon as an alert is sent, the SRC IP is added to the Blocks list.
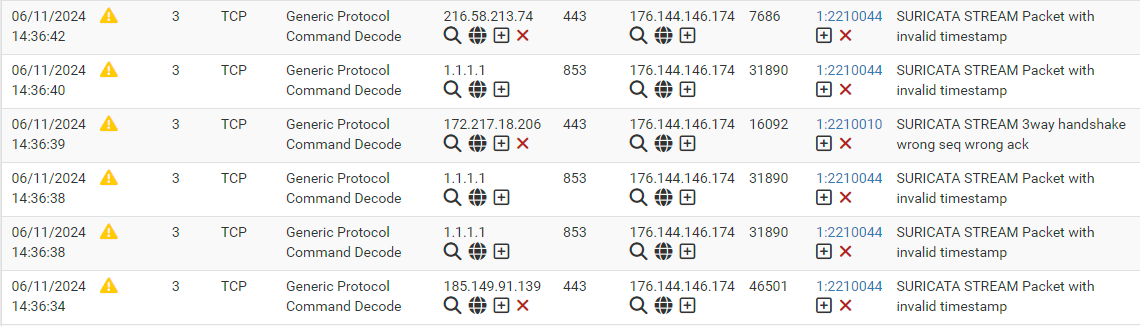
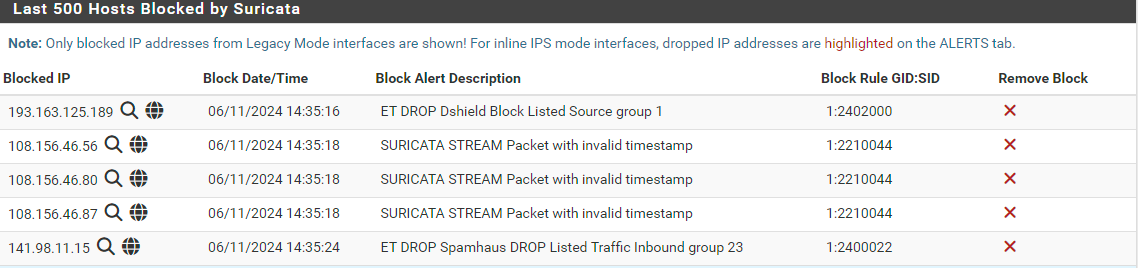
At this point it is impossible to communicate with the outgoing ip.
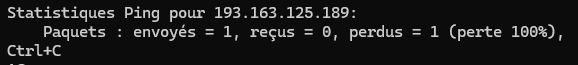
-
@focheur91300 said in Suricata IPS block out trafic WAN interface:
@bmeeks I haven't modified my configuration: IP Pass List

With this configuration, as soon as an alert is sent, the SRC IP is added to the Blocks list.

At this point it is impossible to communicate with the outgoing ip.

Not sure I fully understand your problem. Legacy Blocking Mode does indeed completely block ALL traffic to any IP that triggered an alert and thus subsequent traffic of any type to that IP is blocked. That's because that IP is added to a
pffirewall engine table called snort2c, and all IPs added to that table are blocked for all protocols and ports by a hidden built-in pfSense firewall rule.In short, it appears to be working exactly as designed. If you want to selectively block individual packets and not ALL traffic to/from the IP, then you would need to switch to Inline IPS Mode (if your NIC natively supports the FreeBSD netmap device). Check the Sticky Posts at the top of this sub-forum for details and examples of Inline IPS Mode operation.