Site to Site OpenVPN Setup with a Debian System (as VPN Gateway)
-
Hello everyone,
I have a Debian system to which i have full authority to perform any operation, on an existing LAN that is not under my control and can't change anything. The Lan is simple, with a simple router , a default gateway and DHCP Server and internet access.
I'm trying to access this LAN over a tunnel that will be established between my debian system and my pfSense OpenVPN Server (using the existing default gateway from the existing network). The debian system will be Open VPN Client (Site to Site if possible or Remote Access - to be examined).
then i will try to make 1:1 translation on the debian system, so everything is translated locally to the existing network IP, so we can have a reply from the nearby devices on the existing LAN. (Since they will be no routing to the tunnel nor static routing on the existing router).
So some questions arising for this task:
-
What is the difference on pfSense for OpenVPN clients site to site and remote access clients ? Assuming on site to site we also creating a route when we set the remote network for the client site, but for remote access clients there is no remote network. Is it absolutely necessary to do it with site to site configuration?
-
What if we set a static IP through Radius Server for the OpenVPN client, and then create a network routing over the established tunnel ? Can the client IP be set as gateway for the remote network ?
-
Can debian do both modes of OpenVPN Client ? site to site and remote access? or we have a limitation there ?
-
Is there debian packages to support the needed functions ?? like OpenVPN Client site to site , or remote access, add virtual adapter, 1:1 translation from the virtual adapter to LAN (masquerade packets), add routing etc... ?
Any suggestions and comments appreciated.
-
-
@viragomann can you give me some direction on that please?
is there any difference really if the client is remote access or site to site ?
it seems that the client as such, is not different as client. the difference is how the server handling the client and if the server create route back to the client with dedicated openvpn interface.i see online a lot of "edge" devices or edge gateways that they do this functionality on existing lans, by translating the packets to local LAN ip.
-
@Bambos said in Site to Site OpenVPN Setup with a Debian System (as VPN Gateway):
What is the difference on pfSense for OpenVPN clients site to site and remote access clients ?
There are no differences as far as I know, it's generally all just OpenVPN. Just the pfSense web GUI gives you different option to set.
If you need to access a network behind a client you have to choose the peer to peer mode to get the option to state the remote networks.
Additionally you have to configure a Client Specific Override for the respective client.What if we set a static IP through Radius Server for the OpenVPN client, and then create a network routing over the established tunnel ? Can the client IP be set as gateway for the remote network ?
No, don't set static routes for remote networks you're accessing via VPN.
The static IP can also be achieved with the CSO.
The "remote networks" in the server setting add to routes to the pfSense routing table and point it to the VPN server. The CSO is needed then to set the routes inside OpenVPN.
Can debian do both modes of OpenVPN Client ? site to site and remote access? or we have a limitation there ?
Is there debian packages to support the needed functions ?? like OpenVPN Client site to site , or remote access, add virtual adapter, 1:1 translation from the virtual adapter to LAN (masquerade packets), add routing etc... ?Likewise in pfSense it's basically just OpenVPN in Debian. All differences are done in the configuration.
In Debian you will have to enable routing to pass through the traffic.
The masquerading is done in iptables then. -
@viragomann said in Site to Site OpenVPN Setup with a Debian System (as VPN Gateway):
If you need to access a network behind a client you have to choose the peer to peer mode to get the option to state the remote networks.
Long ago we learnt this the hard way when we were troubleshooting why policy routing was failing to connect an external service through one network's WAN, across the tunnel to a server on another network and back again. The VPN server was originally set up for RA for its users. Changing modes to site-to-site allowed both roles to function as a workaround (but you obviously do not get access to openvpn-client-export anymore).
-
@Popolou
If you want to have the comfort of client export, as a workaround, I think, it should be possible to use the access server mode and assign an interface to it.
Then you get the option to add static routes for client site networks and point it to the VPN server.
CSOs are needed anyway in addition of course. -
@viragomann thanks a lot !
i already have a site to site and routing up and running.now i'm messing with iptables (first time).
what about client specific overrides ?? it seems that pfsense openvpn server has routing normally , the tunnel is ok, the gateway is ok.
These settings below on client specific overrides, are also in the site to site vpn server config. What is the difference ?
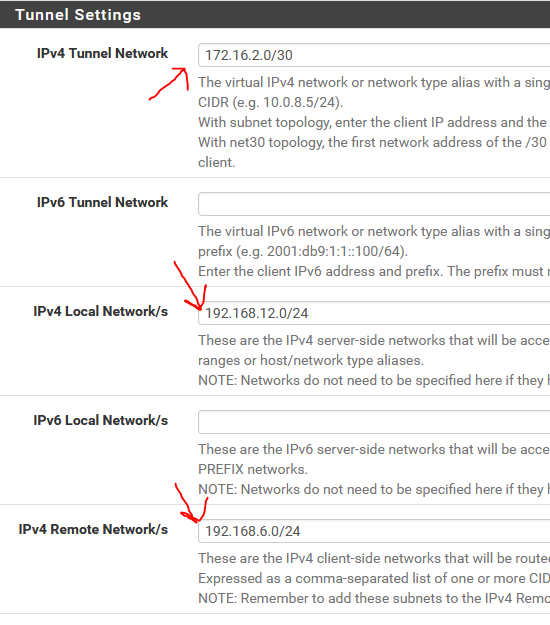
-
@Bambos
If you're using only a /30 tunnel network the CSO is superfluous.
However, remember that this does not work with DCO and you can connect only a singe client to the server. Because of the former, it isn't recommended anymore, even for a peer to peer setup. -
@viragomann hello !! yes, a single client is ok, and is working like below:
as i said the tunnel is ok and routing is ok, i can communicate with my client from pfsense openvpn server. (like a normal site to site). it doesn't seem that pfsense openvpn server configuration needs something more... my issue now is on the debian box to achieve routing and maybe masquerading to "device 30". final scope is to communicate with "device 30" over the tunnel and via debian box.
i'm checking iptables, firewalld and nftables to see what is easier for my purpose. any guidance is much appreciated.This is what i have for now:
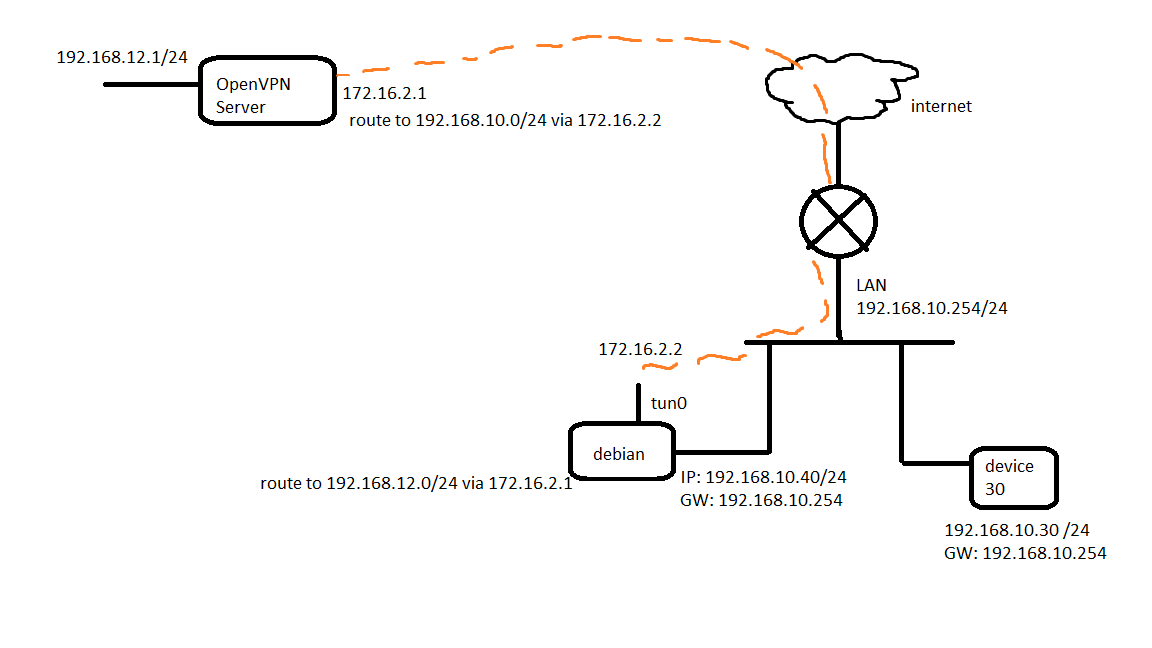
-
@viragomann Hello, and thank you for your useful comments as always. i had some progress with iptables gui on cockpit web gui management system on debian.
below i have a working setup on a pfsense openvpn client executing source NAT while outbounds any request to network 192.168.2.0/24 while having interface address 192.168.2.20/24.
like this is working, and this is what i need to replicate.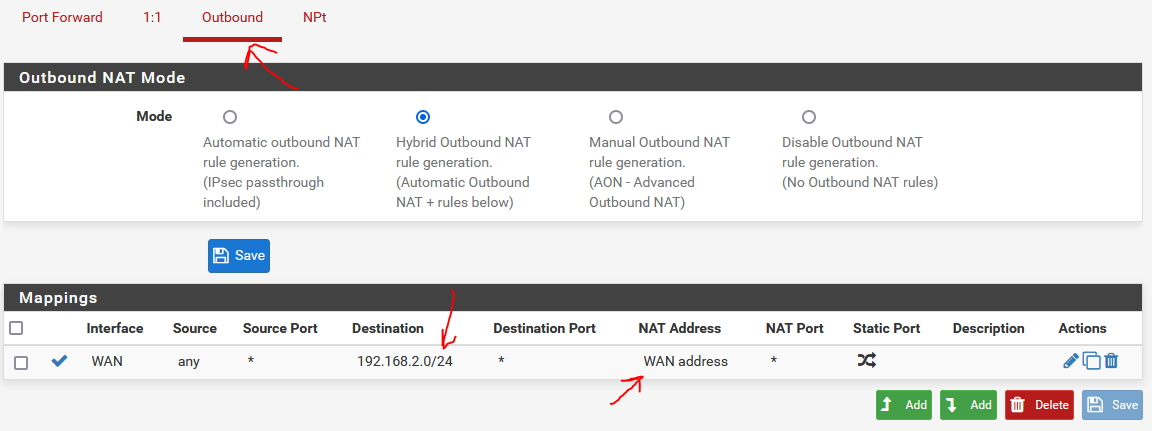
what might be the iptables equivalent ? (ip tables man page is not noobie friendly at all)
There are 2 sections: Filter and NAT. Since i need to work on NAT, i have filter some rules to allow all, and setup the NAT.
On NAT there are Chains: input - output - prerouting - postrouting
do i need prerouting and postrouting ?
Masquerade seems to be accepted only on postrouting.
any suggestions on what might work there ?possible options for NAT rules below:
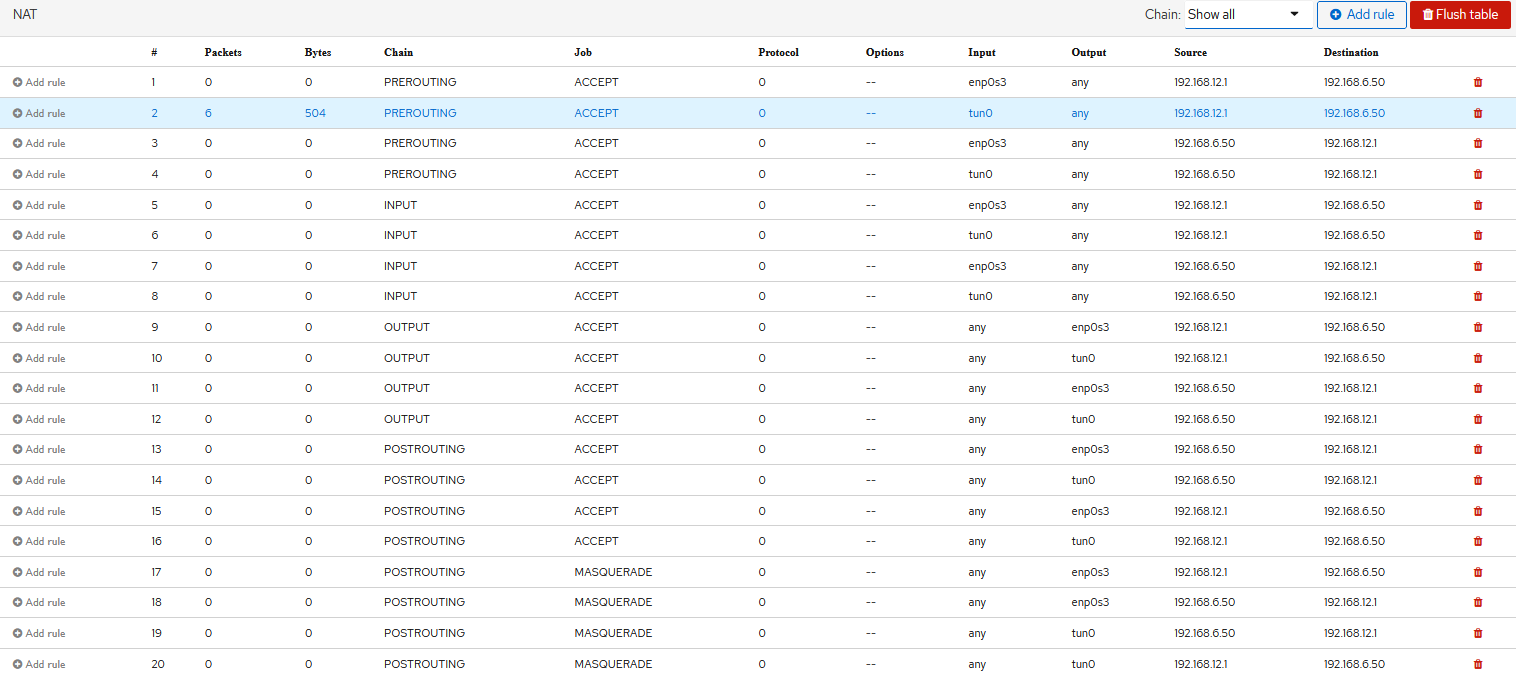
-
@Bambos
Why don't you ask a web search engine? I'm not as familiar with iptables, so I can't tell you.But what you need, is called "masquerading" in iptables and it has to be done after the routing, hence it's a postrouting action.
Yes, it's the same as outbound NAT in pfSense, but iptables use other terms for it.
-
@viragomann thank you very much, i will dig into it.
i ask a web search engine for the last week, saw many tutorials, ask any linux support channel i could find... (forum, discord etc...) still without finding the exact suitable commands for this task. -
@Bambos
The first hit:
Masquerading Made Simple HOWTOSomething like this should do the job.