pfblockerng dnsbl category blocking not working on Firefox and Safari. Works on Chrome
-
I have set up pfblockerng to block adult sites through the DNSBL categories. This works on Chrome and Arc (Chome-based) on my Mac and iPhone. However, when I use Firefox or Safari, nothing is blocked. What's weird is that I have set up forced safe search, and that does work on all browsers. I also have pfblockerng to block ads which works fine.
-
You want DNS requests emitted by Firefox to be handled by pfBlockerng (pfSense).
Firefox, as an application, can use the device's "system DNS", the one obtained by the system's DHCP client, or ... use its own DNS settings.
The question is : what are your Firefox DNS settings ?Menu => Tools => Settings, select "Privacy and Security", go to the bottom of the page :
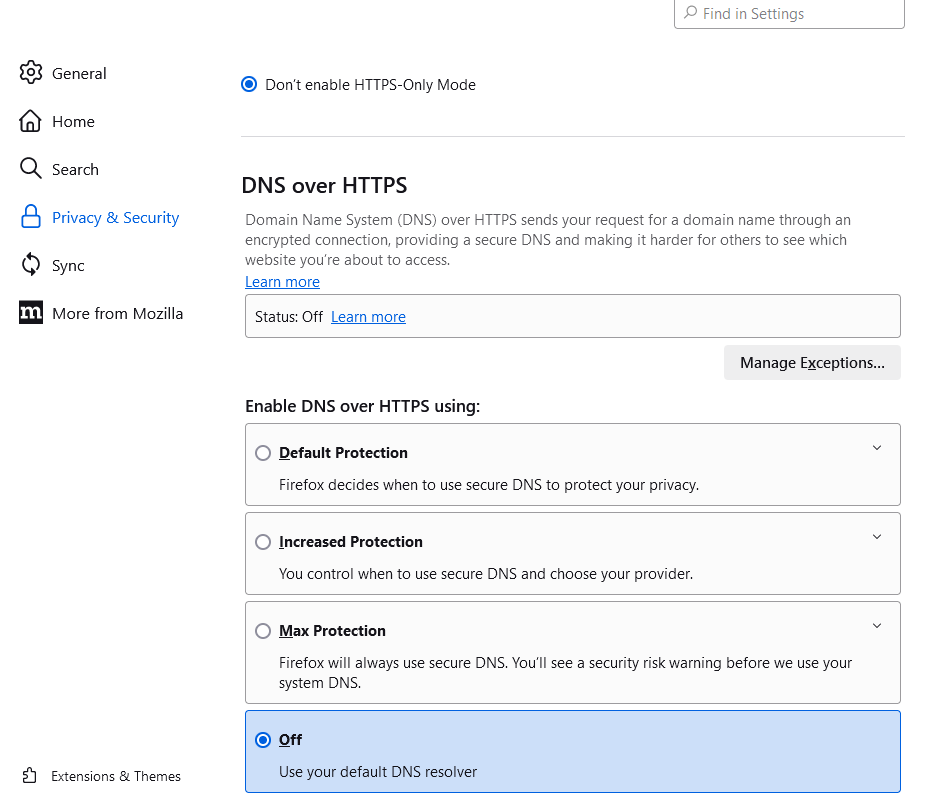
-
@Gertjan yes I’ve turned it off with no change.
-
Ok, nice, so it's more then probable that Firefox uses the resolver to resolves stuff.
Did you test ?I'll give an example :
My settings :
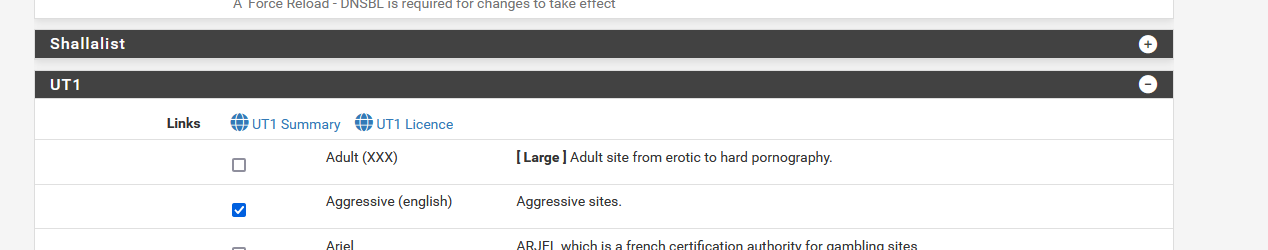
This is dnsbl file :
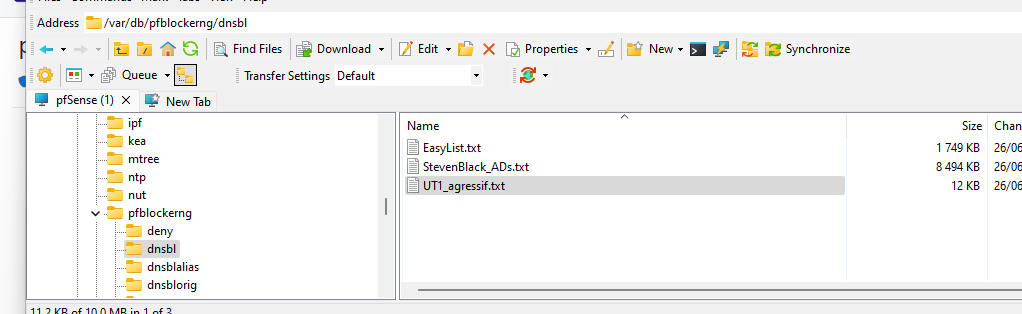
Let's pick one :
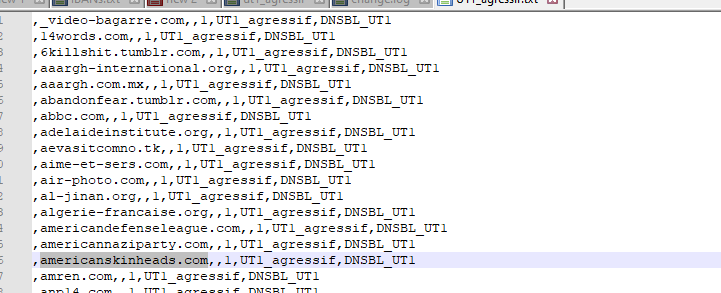
So, I set up a tailer : (SSH or console mode - No (never) GUI command line please):
[24.03-RELEASE][root@pfSense.bhf.tld]/root: tail -f /var/unbound/var/log/pfblockerng/dns_reply.log | grep 'americanskinheads.com'This command 'tails' de main dns_reply.log log file : every DNS request thatw as parsed by pfBlockerng (the python (!) mode parser).
Now I visit this site - and no surprise :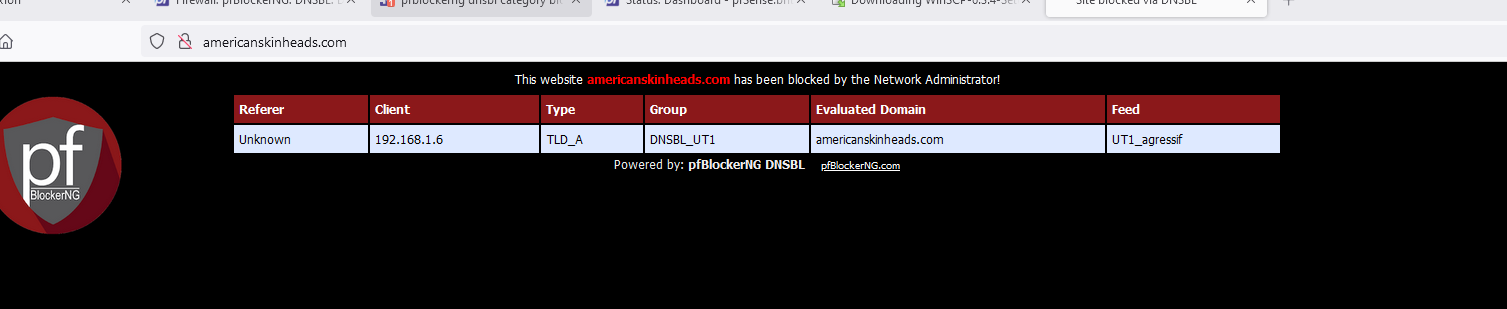
and the logs showes me :
DNS-reply,Jun 26 11:00:00,servfail,AAAA,AAAA,Unk,americanskinheads.com,2a01:cb19:907:dead::c7,ServFail,unk DNS-reply,Jun 26 11:00:00,servfail,AAAA,AAAA,Unk,americanskinheads.com,192.168.1.6,ServFail,unk DNS-reply,Jun 26 11:00:00,servfail,AAAA,AAAA,Unk,americanskinheads.com,2a01:cb19:907:dead::c7,ServFail,unk DNS-reply,Jun 26 11:00:00,servfail,AAAA,AAAA,Unk,americanskinheads.com,192.168.1.6,ServFail,unkBtw : 192.168.1.6 and ,2a01:cb19:907:dead::c7 are the IPs my PC with the web browser is using.
Recap :
My wanted to visit a site using a host name.
The local PC DNS cache didn't have that hostname / IP in it's cache, it was asking unbound (pfSense).
Unbound filtres everything trough the pfBlockerng python loop, that uses a big DNSBL database : it found a match (no surprise) and unbound answered back to my PC : my browser : the the IP that stands for "don't know that IP so here you have 10.10.10.1" which points to the pfBklockerng web server that showed me in turn : that domain you wanted to visit is blocked.