Подсети Pfsense-Mikrotik через OpenVPN - не видят друг друга.
-
Здравствуйте.
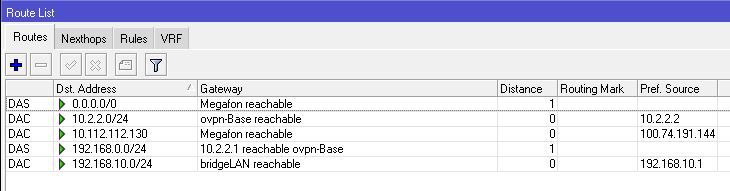
Имею следующее оборудование: сервер Pfsense версии 2.7.2 и Mikrotik (прошивка 6.49.13 long term). Сеть за сервером 192.168.0.0/24 , за микротиком 192.168.10.0/24 Создаю мост на основе OpenVPN (10.2.2.0/24)
Вот конфигурация сервера:
<openvpn>
<openvpn-server>
<vpnid>1</vpnid>
<mode>p2p_tls</mode>
<protocol>TCP4</protocol>
<dev_mode>tun</dev_mode>
<interface>wan</interface>
<ipaddr></ipaddr>
<local_port>31194</local_port>
<description><![CDATA[ovpn-Base]]></description>
<custom_options></custom_options>
<caref>667bb2ca68975</caref>
<crlref></crlref>
<ocspurl></ocspurl>
<certref>667d0de40ee20</certref>
<dh_length>2048</dh_length>
<ecdh_curve>none</ecdh_curve>
<cert_depth>1</cert_depth>
<remote_cert_tls></remote_cert_tls>
<data_ciphers_fallback>AES-256-CBC</data_ciphers_fallback>
<digest>SHA1</digest>
<engine>none</engine>
<tunnel_network>10.2.2.0/24</tunnel_network>
<tunnel_networkv6></tunnel_networkv6>
<remote_network>192.168.10.0/24</remote_network>
<remote_networkv6></remote_networkv6>
<gwredir></gwredir>
<gwredir6></gwredir6>
<local_network>192.168.0.0/24</local_network>
<local_networkv6></local_networkv6>
<maxclients></maxclients>
<connlimit></connlimit>
<allow_compression>no</allow_compression>
<compression></compression>
<compression_push></compression_push>
<passtos></passtos>
<client2client>yes</client2client>
<dynamic_ip></dynamic_ip>
<topology>subnet</topology>
<serverbridge_dhcp></serverbridge_dhcp>
<serverbridge_interface>none</serverbridge_interface>
<serverbridge_routegateway></serverbridge_routegateway>
<serverbridge_dhcp_start></serverbridge_dhcp_start>
<serverbridge_dhcp_end></serverbridge_dhcp_end>
<username_as_common_name><![CDATA[disabled]]></username_as_common_name>
<sndrcvbuf></sndrcvbuf>
<netbios_enable></netbios_enable>
<netbios_ntype>0</netbios_ntype>
<netbios_scope></netbios_scope>
<create_gw>v4only</create_gw>
<verbosity_level>1</verbosity_level>
<data_ciphers>AES-256-CBC</data_ciphers>
<ping_method>keepalive</ping_method>
<keepalive_interval>10</keepalive_interval>
<keepalive_timeout>60</keepalive_timeout>
<ping_seconds>10</ping_seconds>
<ping_push></ping_push>
<ping_action>ping_restart</ping_action>
<ping_action_seconds>60</ping_action_seconds>
<ping_action_push></ping_action_push>
<inactive_seconds>300</inactive_seconds>
</openvpn-server>
<openvpn-csc>
<server_list>1</server_list>
<custom_options>iroute 192.168.10.0 255.255.255.0</custom_options>
<common_name><![CDATA[mikrot]]></common_name>
<block></block>
<description><![CDATA[iroute 192.168.10.0 255.255.255.0]]></description>
<tunnel_network></tunnel_network>
<tunnel_networkv6></tunnel_networkv6>
<local_network></local_network>
<local_networkv6></local_networkv6>
<remote_network></remote_network>
<remote_networkv6></remote_networkv6>
<gwredir></gwredir>
<push_reset></push_reset>
<remove_route></remove_route>
<netbios_enable></netbios_enable>
<netbios_ntype>0</netbios_ntype>
<netbios_scope></netbios_scope>
</openvpn-csc>
</openvpn>Правило Firewall:
<rule>
<id></id>
<tracker>1719384450</tracker>
<type>pass</type>
<interface>wan</interface>
<ipprotocol>inet</ipprotocol>
<tag></tag>
<tagged></tagged>
<max></max>
<max-src-nodes></max-src-nodes>
<max-src-conn></max-src-conn>
<max-src-states></max-src-states>
<statetimeout></statetimeout>
<statetype><![CDATA[keep state]]></statetype>
<os></os>
<protocol>tcp</protocol>
<source>
<any></any>
</source>
<destination>
<network>wanip</network>
<port>31194</port>
</destination>
<descr></descr>
</rule>А это правило Client Specific:
<rule>
<id></id>
<tracker>1713344170</tracker>
<type>pass</type>
<interface>openvpn</interface>
<ipprotocol>inet</ipprotocol>
<tag></tag>
<tagged></tagged>
<max></max>
<max-src-nodes></max-src-nodes>
<max-src-conn></max-src-conn>
<max-src-states></max-src-states>
<statetimeout></statetimeout>
<statetype><![CDATA[keep state]]></statetype>
<os></os>
<source>
<any></any>
</source>
<destination>
<any></any>
</destination>
<log></log>
<descr><![CDATA[OpenVPN]]></descr>
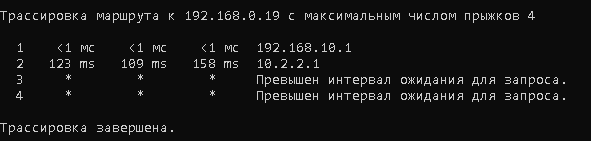
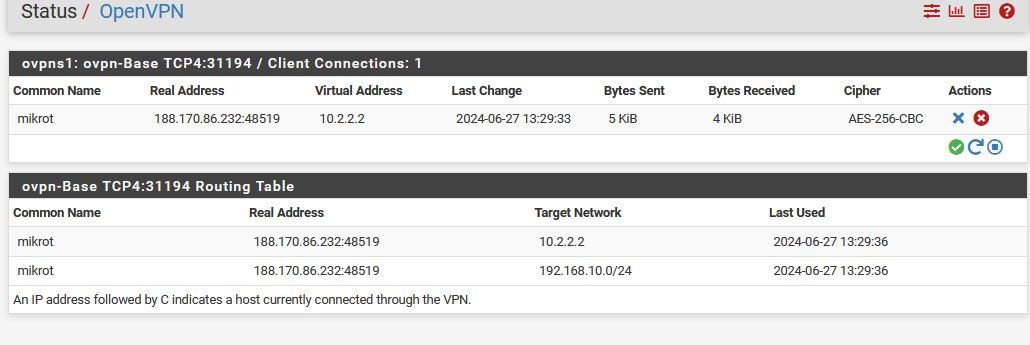
</rule>OpenVPN поднимается «на ура». Из сети за микротиком можно пингануть OpenVPN-сервер (10.2.2.1). Точно также можно из сети за Pfsrver (который одновременно сервер OpenVPN) можно достучатся до микротика.
Вот что показывает трассировка из сети за микротиком