Basic setup help, single VLAN from SG-1100 to Unifi switch
-
@the-other Yeah, I see what you are saying, however it's been set up this way for years with the exception of the OPT2 interface at the bottom. Also, note that it does show different VLAN numbers corresponding to the associated physical port (WAN, LAN, OPT) for each interface:
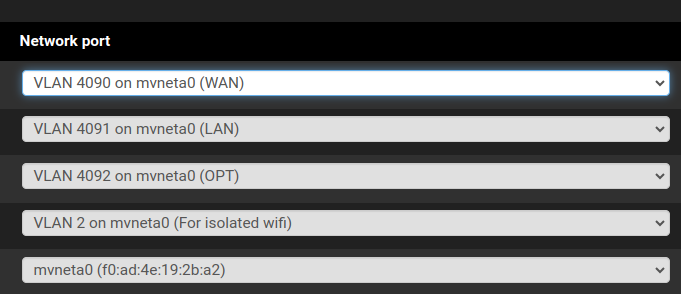
I'll proceed with setting up the DENY and PASS rules to allow the VLAN2 to pass only what I want and see how that works.
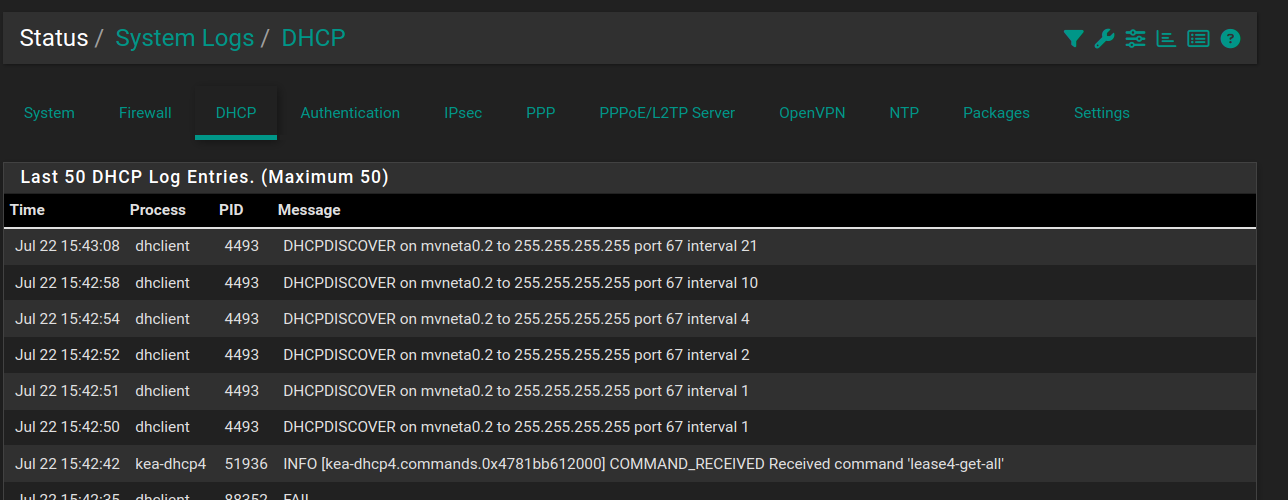
Thanks again.Edit: is this system log (DHCP) confirming that the client PC is trying to obtain a lease?
-
@NGUSER6947
hey there, just a short follow up...
never mind my wondering about your interfaces setup...just saw:
your hardware uses vlans to seperate those physical ports...so, all should be well and it is purely my mistake. sorry for any confusion.
Have you figured it out? Everything's working now?
:) -
@the-other I haven't had time yet (between other commitments, house projects, etc.) to create the firewall Deny/Pass rules.
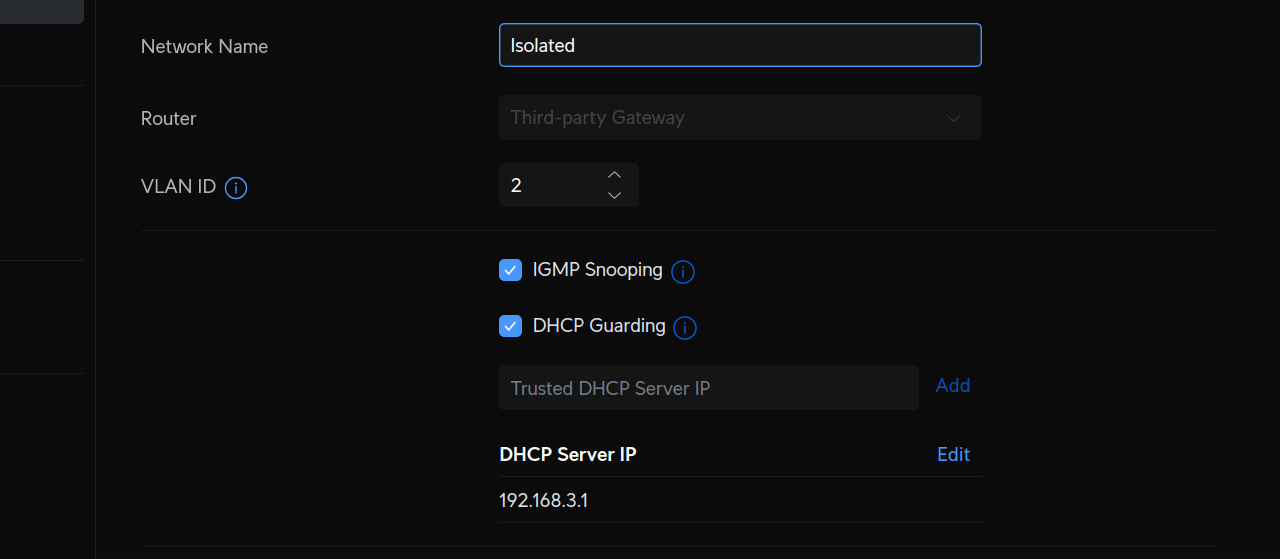
As of now I think that's the last thing left. I made sure that I gave the "virtual" interface an address of 192.168.3.1 and that matches the gateway defined for the VLAN on the Unifi side.
With the bottom-most screen capture above, does that confirm that the one client PC on the VLAN is requesting a DHCP license (or is it the other way around, meaning pfSense is trying to see if any clients are looking for a license)?
-
@the-other Here's where I am today. I created the Pass rule for the VLAN. pfSense's DHCP log I think is indicating that it's trying to issue a lease:
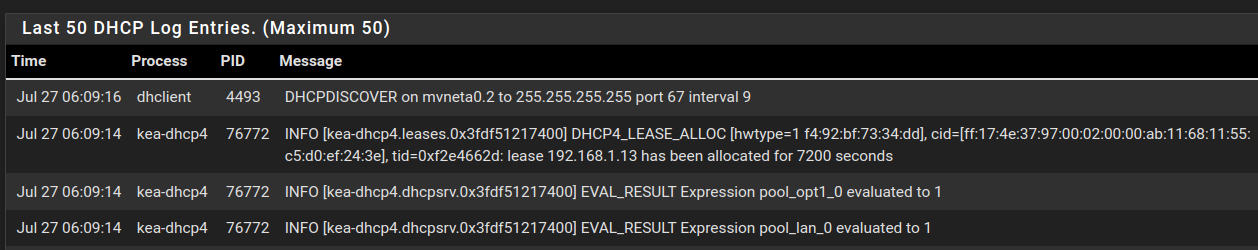
or at least some activity is taking place.However, the client never obtains an IP. Ipconfig shows that the wireless adapter is staying with its autoconfiguration IPV4 address.
This is the rule I created for OPT2 (the VLAN) to allow traffic out to the internet:
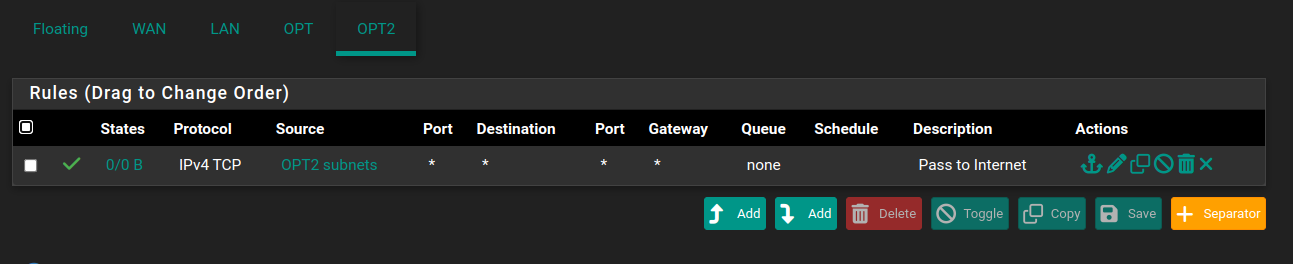
Starting at the client, it does have a connection to the AP, here (in Unifi) you can see it with the autoconfig IP:
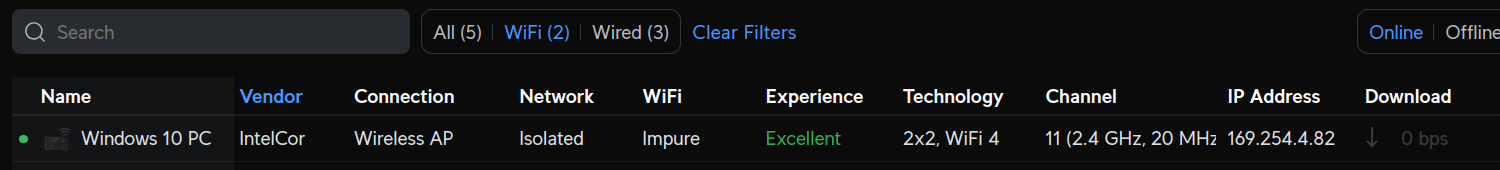
On pfSense, I have the OPT2 interface set with the same IP as set in Unifi as the DHCP server (192.168.3.1):
One thing I am not sure about, is (on the interface screen), is the MAC address for the interface:
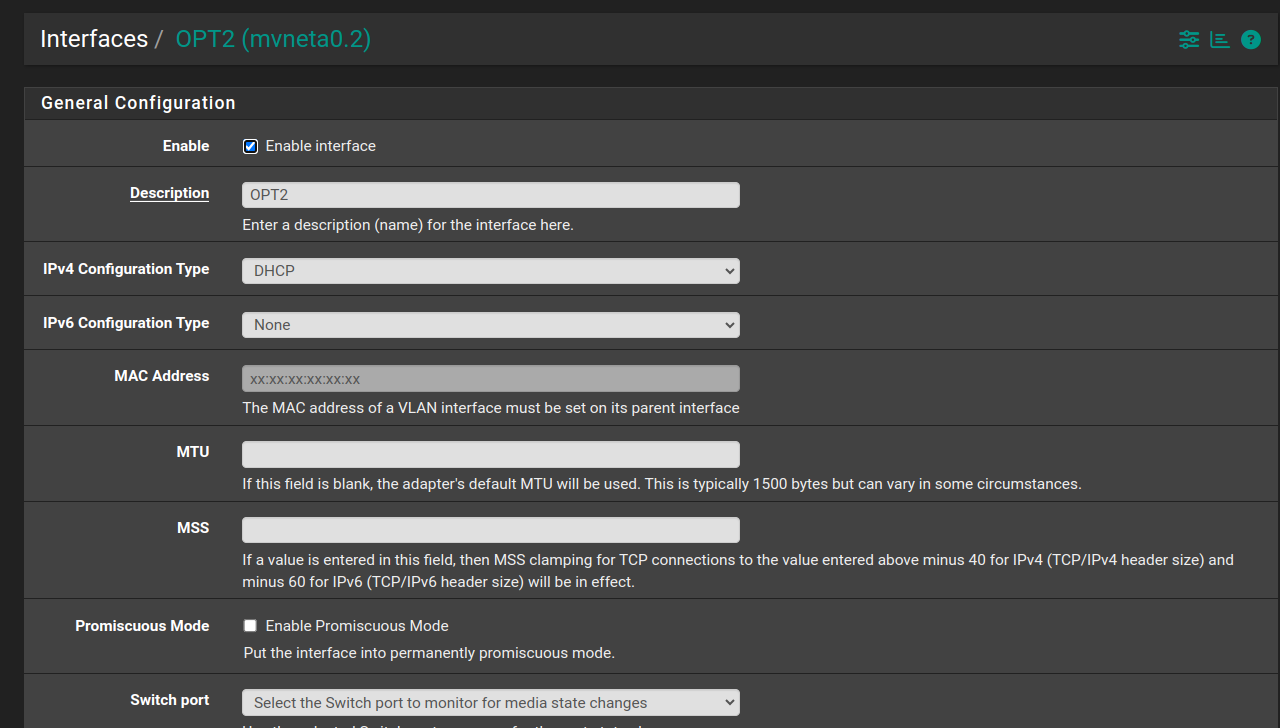
I'm not sure what to set it to. Suspecting this is part of the issue.Finally, here's what the Dashboard page shows for interfaces in pfSense:
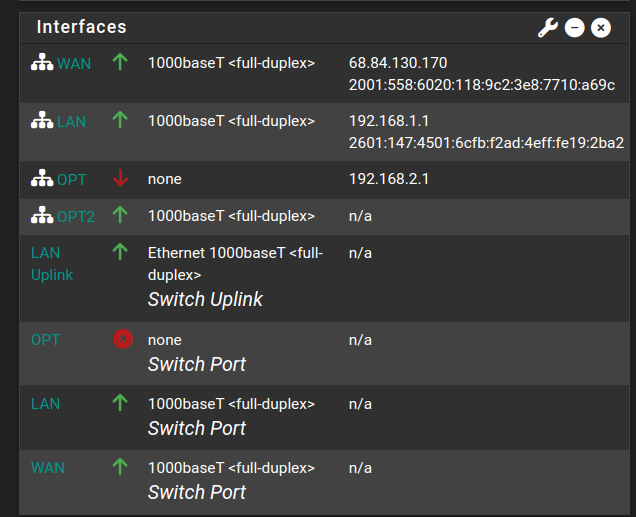
Edit: after rereading some documentation, I switched OPT2 to a static IP and set the address to 192.168.3.1. Now, in the DHCP server tab, OPT2 shows up. However, the client still doesn't get an IP.
-
@NGUSER6947
so...you are using the new KEA dhcp server mode...as do so many, mislead by that warning about "...ISC dhcp has reached end of life...".
My hint would be: go back to ISC dhcp....it is still working just fine whereas KEA is still...developing. I'm sure it will be all well, once it has settled in. But for now, ISC is just (still) fine.and: you try to configure a client with ip 192.168.3.1...shouldn't THAT be pfsense's IP for the "new" interface (for vlan 2 on interface opt2)?
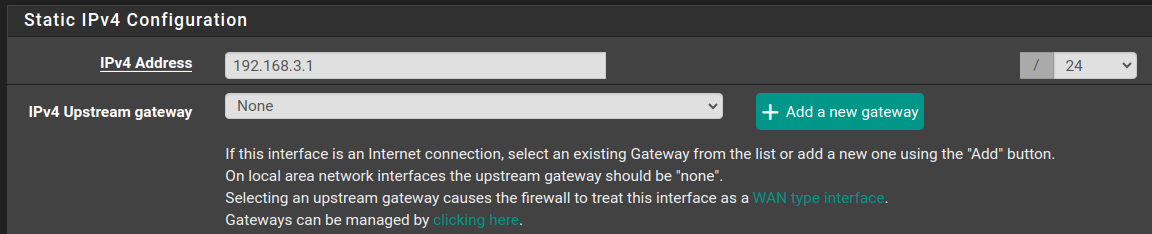
So under Interfaces...set a static IP for that one (VLAN2) with 192.168.3.1...no upstream gateway.
Then your vlan2 should show under Services > DHCP server. There enable dhcp, set IP range...then your client should get its IP (either dynamically or you set a reserved one with its MAC under Services > dhcp server > vlan2 > static mappings...) -
So yes I corrected the OPT2 by setting a static IP of 192.168.3.1.
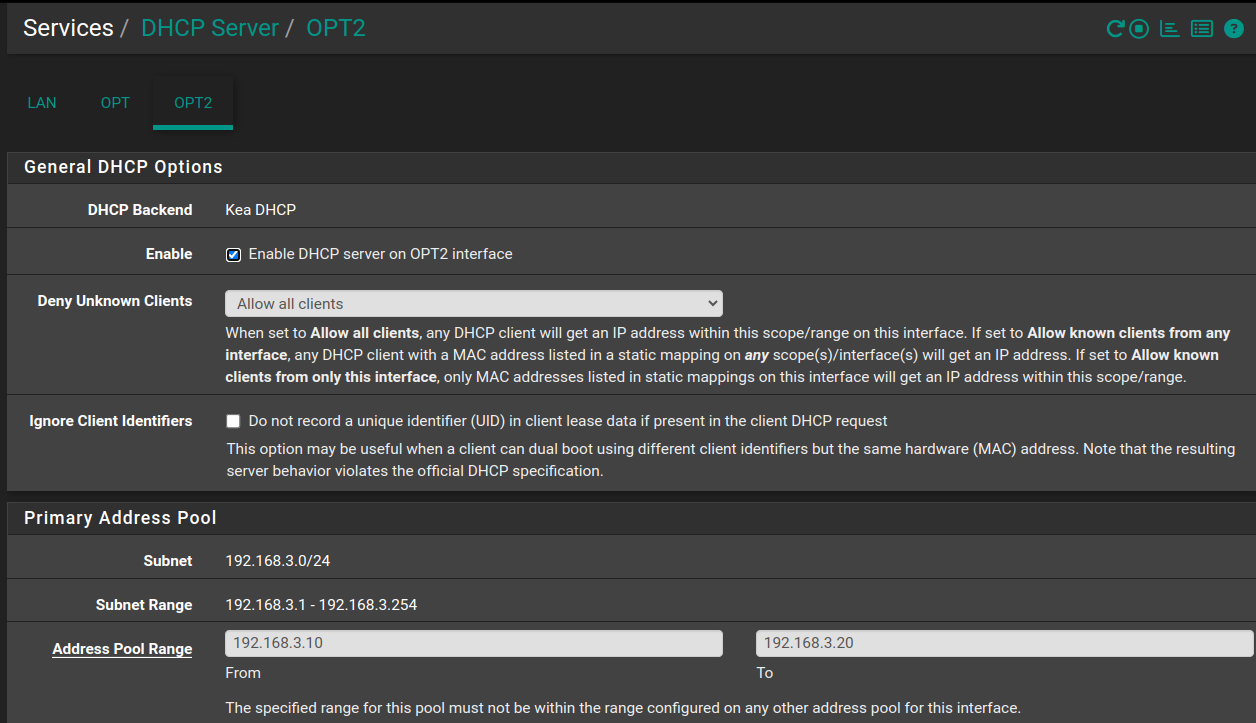
I do have VLAN2 showing up under the Services->DHCP page.
-
@NGUSER6947 yeah, and still runninge KEA... ;)
Given everything else is set your pc should (in auto mode) get its IP between .10 and .20...
Does it? -
@the-other No. The wifi adapter remains with it's default IP of 169.254.4.82.
I've reset the adapter, IPCONFIG /RENEWd, etc. to no avail.
I'm not seeing any errors in the pfSense DHCP logs either, though I'm also not seeing anything that indicates that it's trying to serve up a license for that PC.
On the Unifi side, I can view the live network topology and it shows that PC, with the isolated Wifi network, and online.
-
@NGUSER6947
well, how did you set it all up? as a trunked vlan?
So you have your lan, this carries vlan 1 as the default vlan in trunked vlan mode and vlans x, y, z...being carried on your lan.
so, all your productive vlans (incl your "isolated" one) go over one cable to your ap.
there you set your ssids, so that ssid x handles vlan x and so on.
that way all your vlans are carried to your ap and are being broadcasted with their own ssid. your ap also needs a management ip (default this is in vlan1).
is there another dhcp running (on that ap) by chance? -
@the-other There isn't any DHCP running on the AP. Yes, I have both a default (non-VLAN) and a separate VLAN network defined on the AP, each with separate SSIDs. Clients that I'm not trying to get onto the VLAN are connecting and operating fine on the default (non-VLAN) network. If I tell that one PC to connect to that SSID it works fine and it gets an IP and is good to go.