Multiple NIC ports with different VLANs connection to switch
-
Hi Johnposz
I have 3 physical nic ports on a nic card port 1 carries lan port 2 carries vlan2 and port carries vlan3. when I define the connection on the switch switch do I define the connection on the switch as a trunk? or is that only when you have 1 nic port with multiple vlans traveling on it? The documentation is not clear.
Best Regards
-
@Hoserman those really aren't "vlans" if you set the IP directly on the interface.. In such a setup the port on the switch would just be an access port in the vlan you want to use for that network on your switch
-
If you want the 3 ports to be connected to different VLANs, you can do that at the switch and run them without VLANs.
-
@johnpoz Not sure what your saying.... I defined each PFSense Nic Port as a different VLAN. How can they not be VLANS? On the switch I define 3 vlans each one is connected to their respective PFSense VLAN Nic port.
-
@Hoserman so you created a actual vlan and then put it on a physical interface.. But you put no IP address on the actual physical interface?
Not sure why you would do that - did you do that for your lan interface?
But sure if you want to tag vs native - then your port would would have to be looking for the tag on your switch.
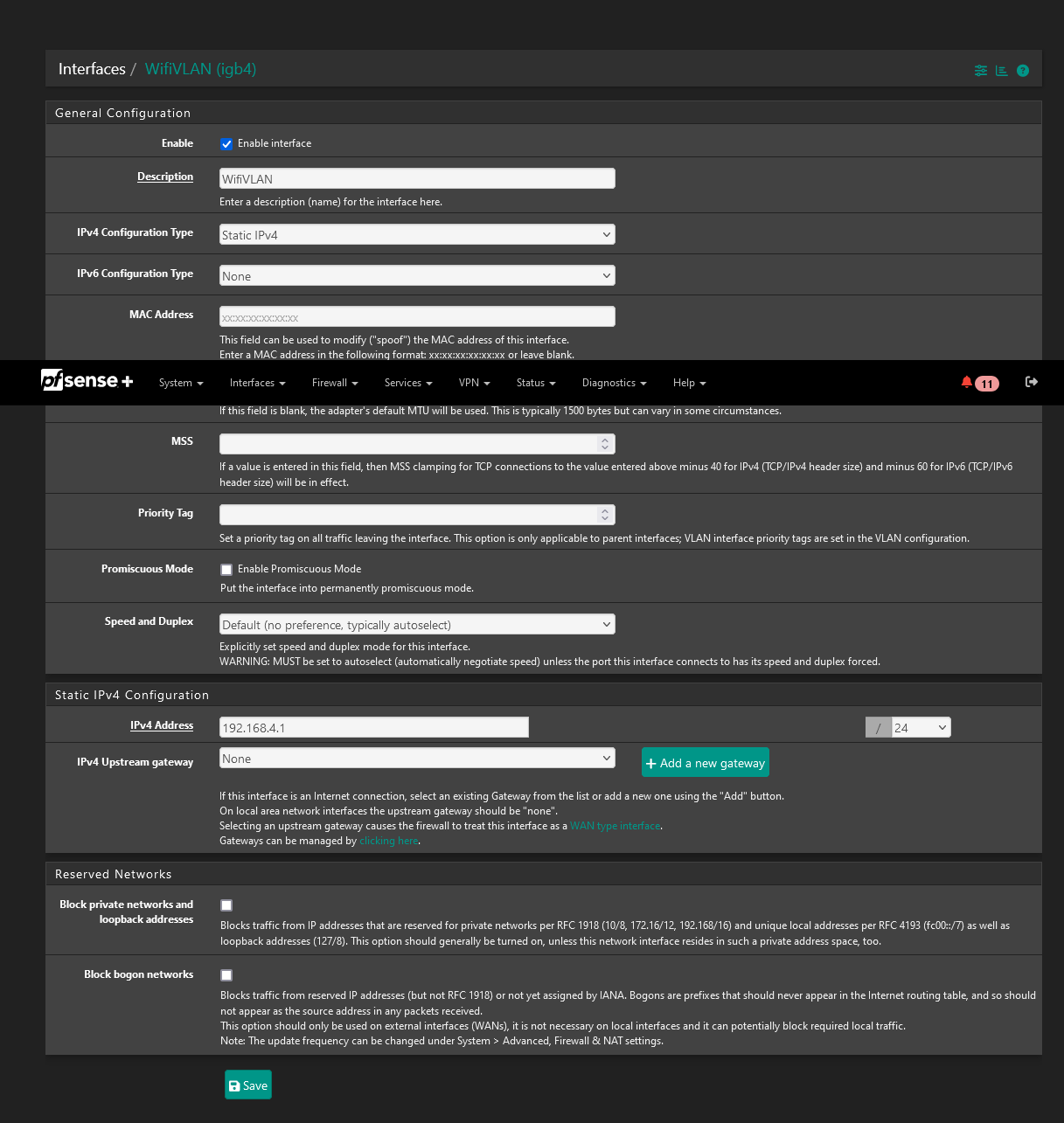
For example see some of my interfaces are native - and they are connected to my switch without any tagging. But then I have vlans that are on igb2 which do have tags.. And also a native untagged network.
-
"But you put no IP address on the actual physical interface?"
How do you put a physical address on a NIC except the MAC address?
-
@Hoserman Of course I define a physical IP4 address on my vlan interfaces...
-
@Hoserman Huh?
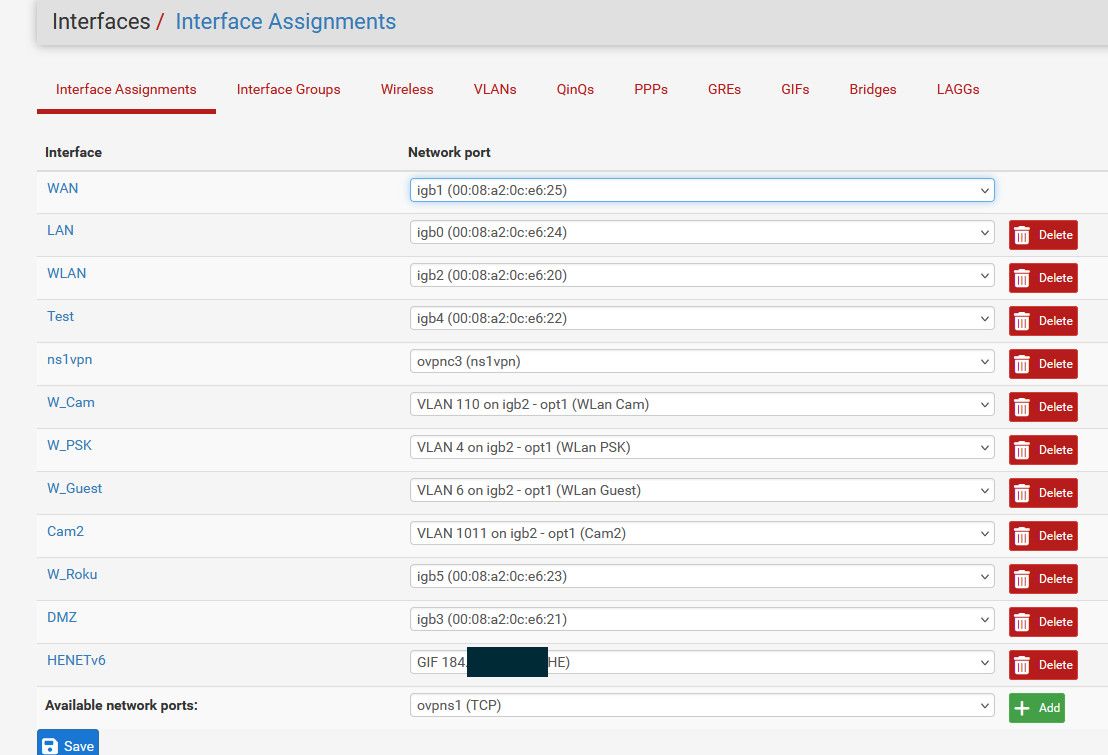
Here this is an IP directly on the physical interface - not a vlan, ie native no tag
And below that is IP address on a vlan interface, notice the igb2.4
So you have no native network on your lan - this is also a vlan, ie tagged? A native network directly on the interface would not be tagged.. A IP/network on an vlan interface, ie like the above igb2.4 would be tagged - in my example with the vlan ID 4.
If you only want to carry one network on the interface - why would you think you need to create a vlan and tag it? Vlans are when you want to carry more than 1 network over the same wire.. Sure you can tag and not use native (untagged) if you want to - but what is the point? Your just creating complexity.
-
I appreciate your help but we are definitely not communicating.
Thank you for your help...
-
@Hoserman Not sure what your not understanding..
I have 3 physical nic ports on a nic card
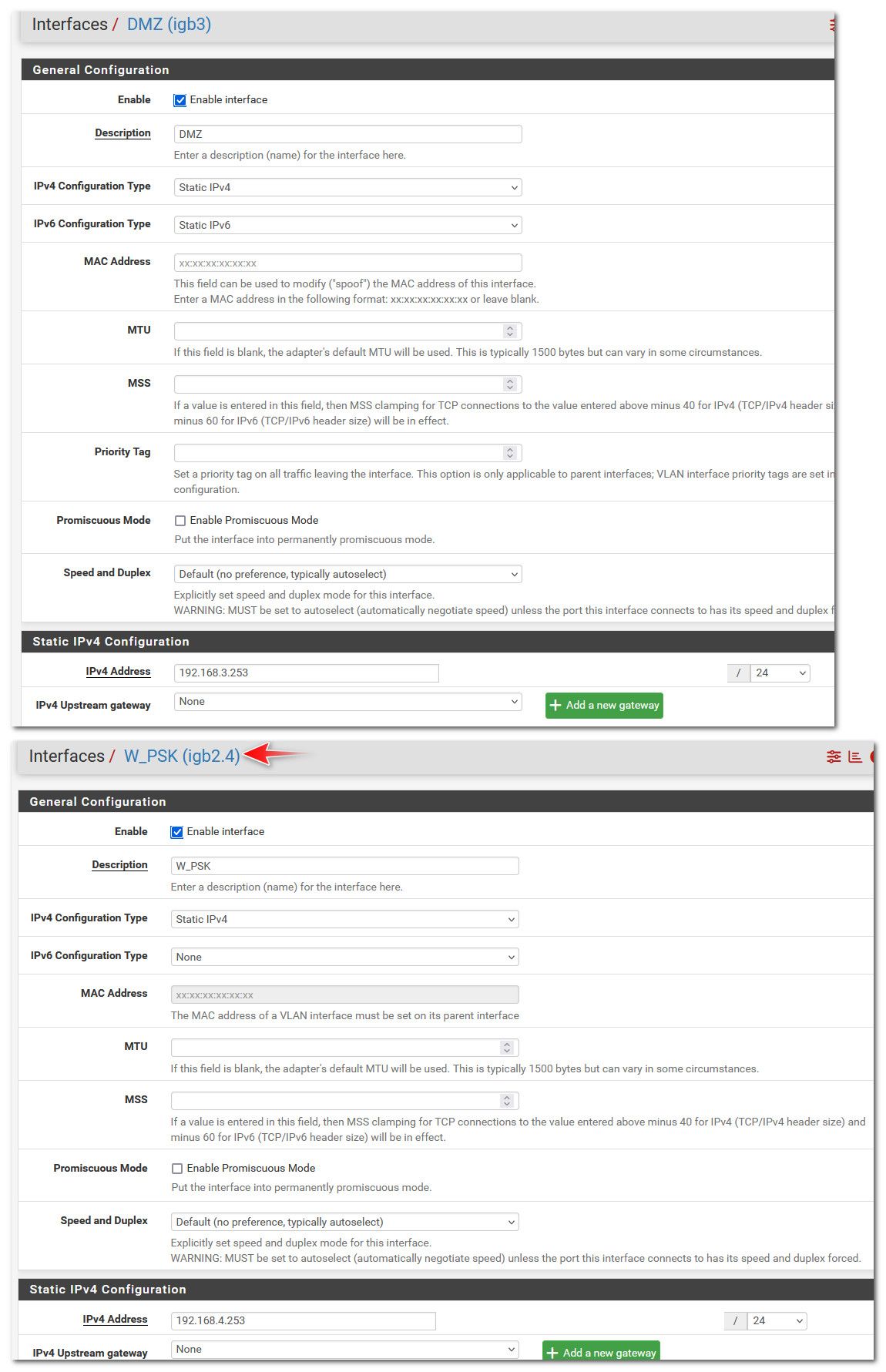
Did you put an IP address directly on the interface?? igb3 for example?? That is native and no tag.. If you create a "vlan" and assign that to the physical interface igb3.X then it would be tagged.. If your tagging traffic out of pfsense then you would setup the switch port its connected to use the same vlan ID, etc.
How about you just post some pictures. Lets see for example picture of your interface - like my igb3 interface.. Then your assignment page.. And your setup on whatever vlan you created.
-
-
@Hoserman that is not a "vlan" that is just the native on the interface.. Notice it just shows igb4
So your switch port you connect to that would be just whatever vlan you put on that port, ie cisco would call this access port.
So for example - my dmz network, which on my switch is vlan 3.. is connected to this port.
interface gigabitethernet6 description "sg4860 DMZ" switchport mode access switchport access vlan 3pfsense is not aware of any tag for this network.. its just a native network. But yes you would need to create a vlan on your switch - but pfsense would be oblivious to any tagging.. since this network is not tagged by pfsense.. But you would create a vlan on your switch to keep it isolated from other vlans on your switch, ie your "lan" for example which would be another untagged network.
-
@johnpoz So when I create a vlan in pfsense it's not a vlan? I dont understand? What am I missing? I have the same VLAN defined on my switch which is connected to the wifivlan on the pfsense interface....
-
@johnpoz but pfsense would be oblivious to any tagging.. since this network is not tagged by pfsense..
So how do I get PFSense to tag the network?
-
@Hoserman said in Multiple NIC ports with different VLANs connection to switch:
So how do I get PFSense to tag the network?
By adding a VLAN to an existing network. However, as I pointed out, it appears you can do what you want by applying the VLAN at the switch.
I have a VLAN here for my guest WiFi. It is on the same interface as my main LAN. This is what you can do in pfSense. Based on your description, you want an interface to be used entirely for a VLAN. Just configure the switch port to be whatever VLAN you want it to be and everything will be fine. No need to enable the VLAN on pfSense.
-
@Hoserman Why do think you need to tag this network?? How many networks are you going to carry over the wire from pfsense port to the switch port.. 1 then there is no need to tag..
When you create a vlan in pfsense - ie this..
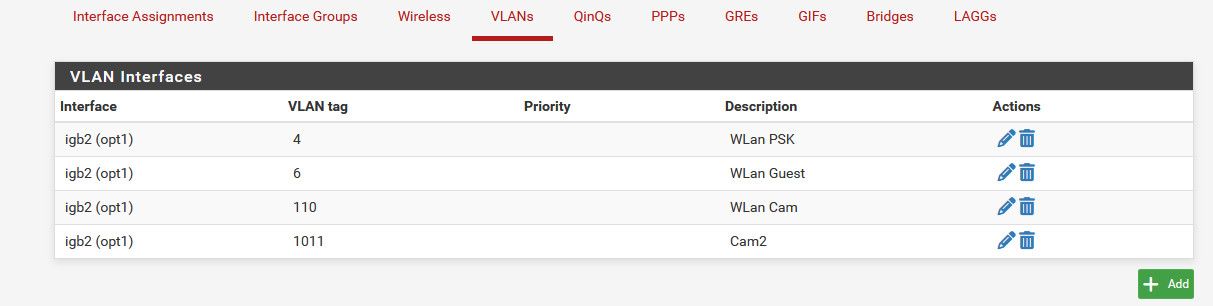
They are tagged - because they are all going to go over 1 wire..
See my assignments from above
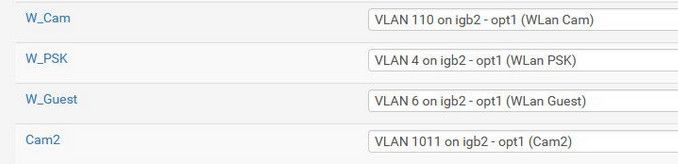
All those networks flow over 1 wire - the igb2 interface to the switch port.. So pfsense and the switch can tell what traffic is what, it has to be tagged..
So the switch the port is configured like this
interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 4,6,110,1011 switchport trunk native vlan 2So vlans 4,6,110, and 1011 are tagged.. See where it says the native vlan for this port is 2, this is vlan 2 on my switch.. This is the native network on the igb2 interface..
So create a vlan on your switch, maybe 4 since your network is 192.168.4/24 - and put your port in access mode, no tag in vlan 4 on your switch... Then put any other ports on this switch where you want them to be on that network also in vlan 4 on your switch..
-
@johnpozI have 2 Nic cards. What I want to do is separate my vlans on Separate Nic wires. Is that doable. What you describe is having my vlans go over one Nic Port wire. I am concerned about bandwidth. In the PFSense documentation it talks about connecting to pfsense via a trunk.
-
@Hoserman Really dude.. I am really at a loss on how else to explain this too you.. I showed using tags for when your going to carry more than 1 vlan over the wire.. Have already stated multiple times that you do not need to create vlans or tags on pfsense if your just putting the network native on the interface in pfsense.
Your interface lan - this is a native network.. All switches default vlan 1 it is not tagged.. Create another vlan on your switch, lets call it vlan 4.. Now on the port your other interface on pfsense that is connected to put that port in vlan 4 on your switch.. No tags.. Now put another port that you say connect your laptop too and on your switch put that in vlan 4 on your switch..
There you go your new 192.168.4 network is isolated from your lan network.
-
@Hoserman said in Multiple NIC ports with different VLANs connection to switch:
What I want to do is separate my vlans on Separate Nic wires.
As I said, you do that at the switch. You only have to use VLANs in pfSense if you're carrying more than one network over one interface, as in my example.
-
@Hoserman you are confusing the terminology of VLANS with separate networks.
VLANS = multiple virtual networks with a single parent NICYou have two NICs, well assuming you have at least 3 with one being your WAN, each NIC is a discrete physically separate network. Nothing virtual about it.