Using Managed Switch for Company and Private Networks
-
@bookie56 do you not have enough ports to just connect those 4 ports to your switch... Which then would give you more flexibility..
-
@johnpoz Can we leave at it is for now....

Here are the two settings now:
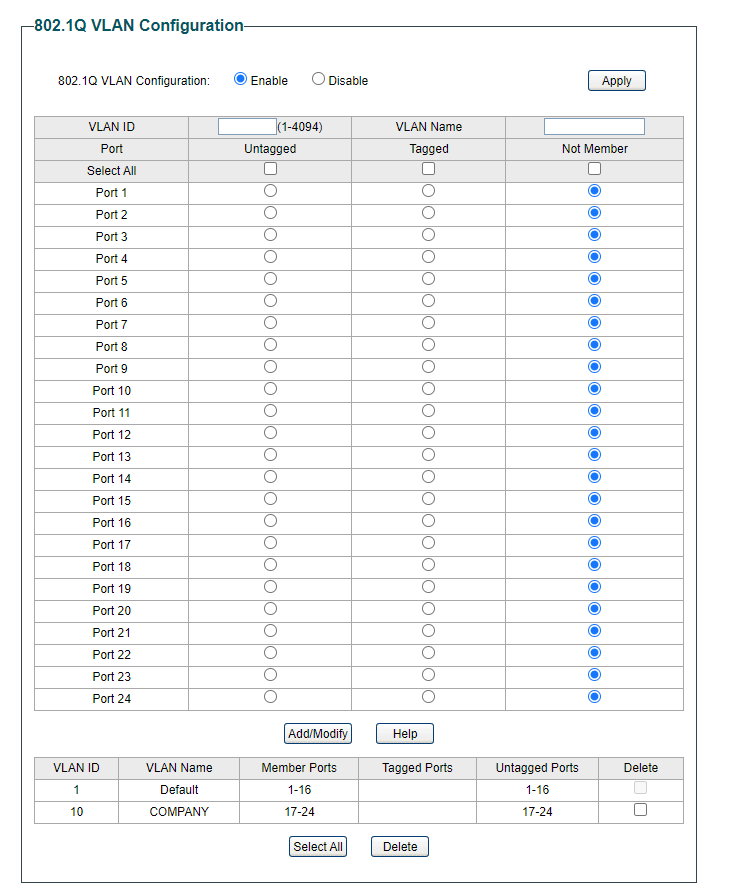
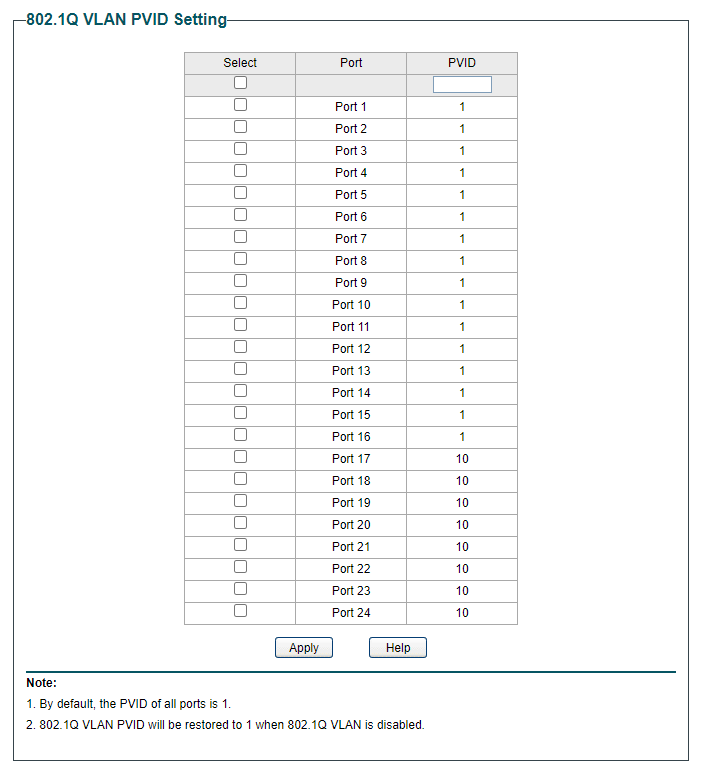
-
I have gone back to pfsense and added an IPv4 address and then in DHCP Server given it a range ...because I have no need for so many gone from 192.168.121.2 to 192.168.121.25 (example)
The existing firewall rules I had help with.....
What rules do I need to stop this network talking to LAN_PRIVATE and WIFI_PRIVATE?bookie56
-
@bookie56 Under Firewall > Rules you have the LAN_COMPANY and WIFI_COMPANY tabs.
Create new block rules above the allow all rule that look similar to this. In my case it's my GuestVLAN that I don't want accessing e.g. the IoT-network.
Select Block and the interface is your LAN_COMPANY, protocol any and source any.
Then it's a matter of selecting the destination you want to block, in this case you would pick LAN_PRIVATE and click Save.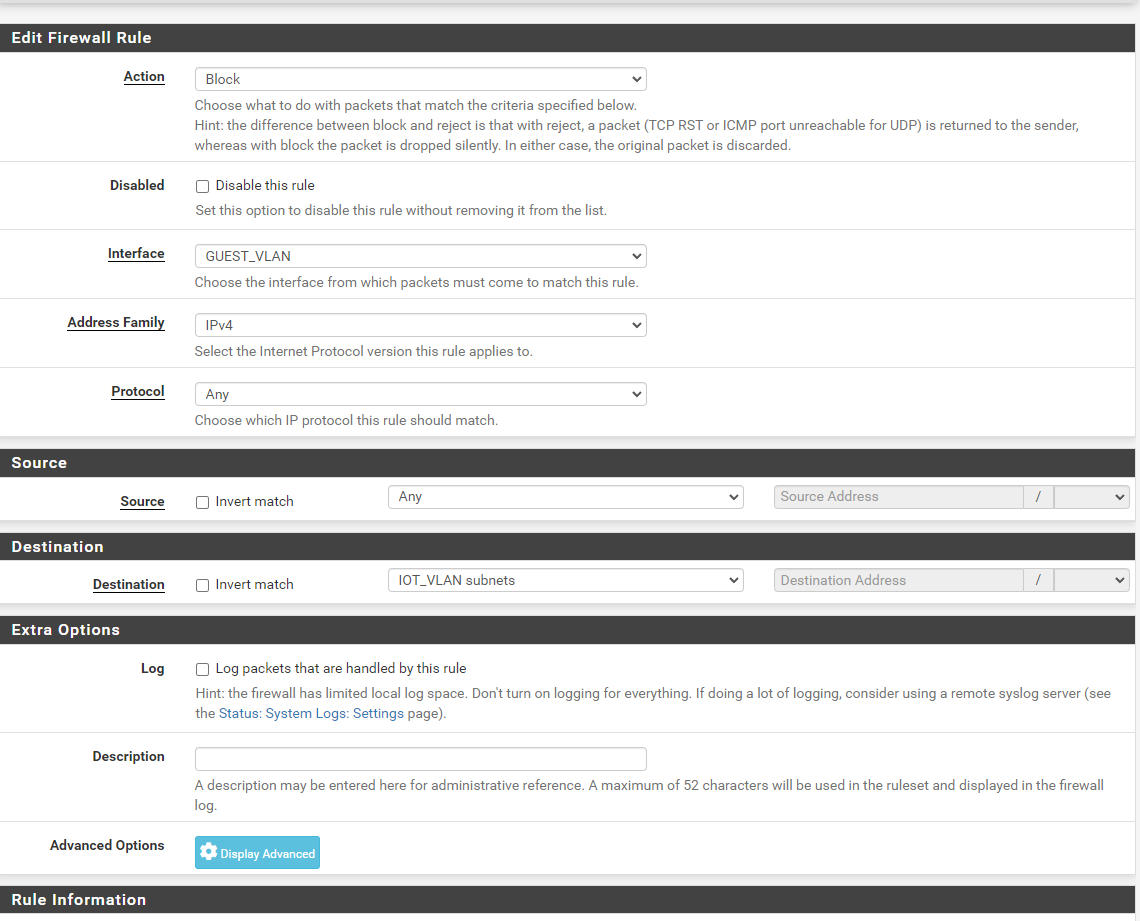
Then you create one more looking exactly the same but select WIFI_PRIVATE as the destination you want to block. Make sure they end up above the allow rule.
To test that it works you can try pinging anything on your PRIVATE netwórk from one of your COMPANY PC's.
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
Can we leave at it is for now
sure.. whatever you feel comfortable with doing, its your network..
So your lan private and lan company are working now.. depending on what port you plug them into on your switch? That switch config looks correct to me for just splitting the switch into 2 virtual switches.
-
@Gblenn said in Using Managed Switch for Company and Private Networks:
@bookie56 Under Firewall > Rules you have the LAN_COMPANY and WIFI_COMPANY tabs.
Create new block rules above the allow all rule that look similar to this. In my case it's my GuestVLAN that I don't want accessing e.g. the IoT-network.

Select Block and the interface is your LAN_COMPANY, protocol any and source any.
Then it's a matter of selecting the destination you want to block, in this case you would pick LAN_PRIVATE and click Save.
Then you create one more looking exactly the same but select WIFI_PRIVATE as the destination you want to block. Make sure they end up above the allow rule.
To test that it works you can try pinging anything on your PRIVATE netwórk from one of your COMPANY PC's.
Sorry not understanding this....I have fire rules implemented from LAN_COMPANY and WIFI-COMPANYnot having contact with my private network....but don't I need a rule for the VLAN? Or does that automaticaly fall under the rules for LAN_COMPANY and WIFI_COMPANY
bookie56
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
but don't I need a rule for the VLAN?
what vlans - you didn't create any vlans on pfsense - did you? The vlans are only on your switch.. to keep those networks at layer 2 isolated from each other. At layer 3, pfsense would filter any traffic trying to be routed across pfsense.
I thought you only had 4 networks on pfsense on your quad port nic, your lan private and company, and then wifi private and company that you plug your AP into.
So 4 interfaces, for these 4 networks.. This is where you would create rules.. There are no rules you would put on your switch.. The very act of creating a vlan on the switch isolates those ports in vlan X from vlan Y ports at layer 2.
But if you don not want lan private to talk to any of your 3 other networks, then you would need rule(s) to do that. You could do it in 1 rule if you wanted with alias that contains the networks you don't want to talk to.. When your creating rules that block access to your other networks its common to just create a alias that contains all of the rfc1918 space. 10.0.0.0/8, 192.168.0.0/16 and 172.16.0.0/12 this way you can use the alias in your block rule, and this network would not be able to talk to any other networks that you currently have or in the future might add.
You just need rules above this block rule that allows what you want.. Here is an example of a locked down network that can not talk to any other network I have on pfsense, nor any of pfsense other IPs, like say its public IP..
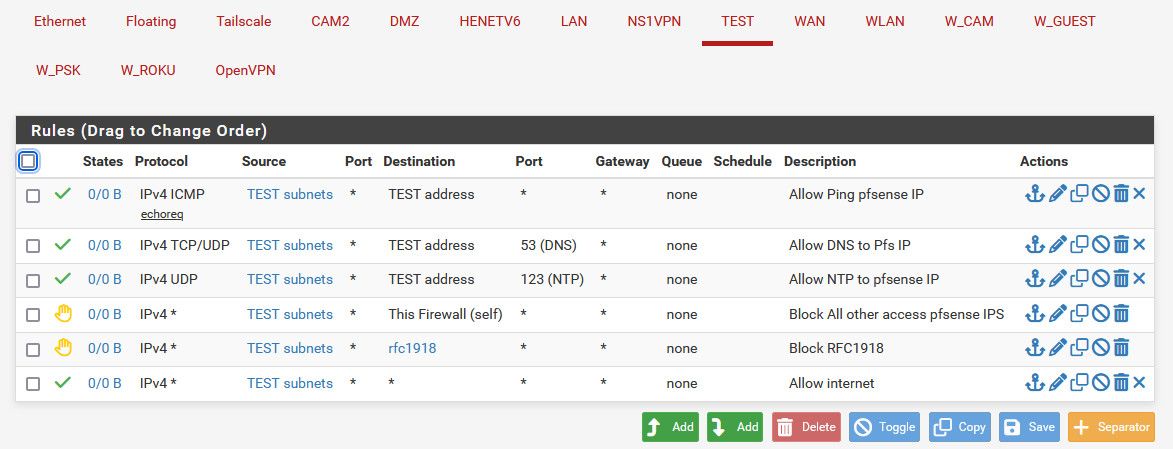
Rules are evaluated top down as traffic interfaces the pfsense interface from the network that interface is attached too, first rule to trigger wins and no other rules are evaluated
These rules allow devices on my "test" network to ping pfsense IP on the test interface, use dns and ntp to this test interface IP. It then makes sure clients on the test can not talk to any other IPs of pfsense, say the want public IP - or devices on this network would be able to access the pfsense web gui for example on its wan IP which is public. The use of the alias helps if that IP might change in the future to some other public IP.
They then block access to any other rfc1918 addresses - ie my other networks.. And then the last rule is what allows devices on this network to talk to any other IPs, ie the internet.
-
@johnpoz so I don't need a vlan on pfsense?
bookie56
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
@johnpoz so I don't need a vlan on pfsense?
bookie56
No you don't since you are instead reusing your existing setup. VLAN is only used here as a way of splitting the switch into two logical and separated portions.
My example sais GUEST_VLAN and IOT_VLAN but those are simply names, and I happen to have VLANs...
In your case though, we use my example FROM GUEST, which you simply replace with your existing LAN_COMPANY network interface. And IOT_VLAN in this case is replaced with LAN_PRIVATE for one of the rules, and WIFI_PRIVATE for the other rule.
You need a block rule for each of the other networks you do NOT want LAN_COMPANY to be able to access.
And of course you need to do the exact same thing on WIFI_COMPANY.It's easy to copy a rule in pfsense. Click the Copy symbol and a new rule opens up. Now you can simply change the Interface it relates to and it will end up on WIFI_COMPANY instead of LAN_COMPANY for example.
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
so I don't need a vlan on pfsense?
no you only need vlans on pfsense when you want to carry more than one network over the same physical interface.. But since your plugging in 2 different physical interfaces into your switch to 2 different ports then no pfsense does not need to send or understand any tags for these networks.
-
@johnpoz ok...I will reconnect my other switches to this one and test things....
I mentioned earlier about the fact I have a server that I use for cloning computers..
This server has two network cards one for my LAN_PRIVATE and the other for Clonezilla...
If I change the LAN_PRIVATE to just Port 1 to 12 and 13 to 16 for Cloning...where 13 would be the feed from the 2nd network card on my server...can I set it up in the same way as you guys have shown me ?
Would that work in the same way?bookie56
-
@bookie56 you could set up whatever ports you want on whatever vlans you want.. You could setup say 12 on this switch you wanted with just 2 ports in each vlan. I mean the switch can do more than that - but if your not going to tag, kind of need atleast 2 ports in each vlan ;)
-
@johnpoz thanks for all your help...
Dare I ask about tagging?bookie56
-
@bookie56 tagging vlans is when you want to carry more than one vlan/network over the same physical connection
see in my above post where show my interfaces - I have multiple networks going over that 1 physical interface igb2
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
@johnpoz thanks for all your help...
Dare I ask about tagging?bookie56
With the setup you now have, all ports are set to Untagged. Which still means packets have tags whilst inside the switch, moving between ports. Like going from 20 to 17 to reach pfsense LAN_COMPANY. The switch then knows to send any of those packets only to ports 17-24 because only those ports belong to VLAN 10.
All packets are however stripped of the tags as soon as they leave the switch to get to pfsense or a PC/server. Hence you are not tagging...Tagging on the other hand, means maintaining the VLAN ID also outside the switch, throughout the network, so packets can pass along towards the correct endpoint.
In my first suggestion, where I was assuming VLANs for your networks instead of the physical ports you now use. All of them were on one physical port. Packets then need to be tagged so they can be separated and end up in the right "VLAN-network" in pfsense, as well as the right ports in the switch.
Port 1 was then a TRUNK port (set to Tagged) which would maintain any tags already attached to packes coming from pfsense or the respective ports in the switch. If you had more managed switches you would typically connect them together using TRUNK ports that allow most or all your VLAN's to pass between the switches.
-
@Gblenn wow now this is why I love this forum....
You guys are amasing....
Thank you so much for all your help...
I will run with the setup as is for now and look into changing things later...bookie56