WAN with /64 Delegation
-
Hello. My ISP only offers /64 delegation on WAN side.
From pfSense, I can ping out the WAN side IPv6 addresses because it has an IPv6 address from the ISP.
But I cannot get LAN IPv6 working, I tried assigning my local LAN side fc00::/7 addresses. All my clients now have an IPv6 address within this subnet and can ping pfSense via IPv6 however, I don't know how to get them to get out on the WAN side.
I assumed I needed to setup NPt. So, I created an NPt rule as follows:
Interface: WAN
Source IPv6 Prefix: fc00:: / 7
Destination IPv6: NOT Prefix fc00:: / 7However this didn't get my clients online. Any thoughts on how I would go about doing this?
-
@meluvalli For a start, set your WAN IPv6 to DHCP, set one LAN IPv6 to Track Interface WAN and 0. See if this works.
-
@Bob-Dig It doesn't. The ISP is only providing /64. LAN side never gets IP with that setup because of this.
That's why I was trying to set fc00 internal IP addresses and having it NPt out.
-
@meluvalli said in WAN with /64 Delegation:
It doesn't.
Have you rebooted pfSense with this settings?
If it doesn't work, there is nothing you can do about it. -
@Bob-Dig
Yes. And it still didn't. The WAN get's an IPv6 address, but it's a /64 Delegation. So with providers that only supply a /64 delegation, you just can't use IPv6 with pfSense? -
@meluvalli What ISP, what country?
Usually you get one IPv6-Address for your WAN via DHCP and a Prefix for your LAN. If your Prefix is only /64, it is only enough for one LAN. But if even this isn't working, then there is nothing pfSense can do for you. -
@Bob-Dig
But the WAN and LAN can't both use the same Prefix can they? They would have to be different. So how would one ever get a /64 prefix to work if that's all that's provided by the provider?
The prefix range is big enough for sextillion IP addresses and I can't get it to work? That seems strange! -
@meluvalli said in WAN with /64 Delegation:
That seems strange
Strange to me is that you don't provide meaningful information about your setup, ISP, country etc. So we will never find what is wrong with your IPv6.
-
@Bob-Dig
Sorry, I can give more details...I am using Verizon 5G Home Internet here in the United States. I have a XCI55AX modem/gateway that is setup in Bridge mode. IPv4 works fine and obtains and outside IP address.
Unfortunately, IPv6 has very limited configuration in the gateway itself. It can only hand out Stateless and Stateful IP addresses with a LAN Prefix already defined in the gateway. It doesn't appear to "bridge".
-
@meluvalli said in WAN with /64 Delegation:
It can only hand out Stateless and Stateful IP addresses with a LAN Prefix already defined in the gateway. It doesn't appear to "bridge".
My guess is, that thing isn't in bridge-mode, maybe doesn't have it at all.
Anyways, if it uses the /64 for its LAN, then you can not use that /64 a second time. You only have IPv6 on your pfSense WAN-Address.
So the only thing you could do is to NAT that one IPv6-Address on your WAN the same way you already do with the IPv4-Address on WAN.
With that you will not gain any benefits you usually get with using IPv6. But if you really really want to use IPv6, you can do it like that.
For this to work, go to FirewallNATOutbound (not NPt), select Hybrid Outbound NAT and then mimic all the Automatic Rules for IPv4 with IPv6 yourself. You have to use ULAs on all your LANs. -
@Bob-Dig
Ok. That's what I was thinking. And I also attempted that once and couldn't get it to work. But, I will try that route again. I understand I wouldn't get all the benefits of IPv6, but at least my clients would be able to access a website that is strictly only IPv6 this way...So, to NAT it, I would just assign a static IP address then on the LAN side just as I would with IPv4 correct?
So for example, If I chose a prefix of fd00:0000:0000:0001, I would use Static IP of fd00:0000:0000:0001::1/64 with no gateway in pfSense on the LAN side and then all clients would have to have an IP of fd00:0000:0000:00001::/64 subnet with the gateway set as fd00:0000:0000:0001::1.
Then, as you stated, in Outbound Nat, I would create a rule on WAN interface with Source: fd00:0000:0000:0001::/64 NAT Wan Address.
Does this sound correct to you?
-
@meluvalli said in WAN with /64 Delegation:
But the WAN and LAN can't both use the same Prefix can they?
See it like this, using some twisted IPv4 analogy :
No, you can't have a LAN using 192.168.1.1 and a WAN using 192.1568.1.2 - that will break routing entirely.@meluvalli said in WAN with /64 Delegation:
So how would one ever get a /64 prefix to work if that's all that's provided by the provider?
That's the good question.
If an ISP providing just one /64 then that is actually completely wrong.@meluvalli said in WAN with /64 Delegation:
That seems strange!
Not really, its more like the same story all over again.
Like the early IPv4 days, when it became clear that "there might be not enough IPv4 for everybody".
NAT didn't existed yet. It was patched together later on by a simple guy who didn't realize that he just saved the Internet so it could serve the planet for a couple of decades more.
IPv6 was build from the ground up with a lot of knowledge already known. It's somewhat a written rule that every ISP end user should have a /56 or even a /48 (he.net does so).
Just offering a /64 is lie,; saying : just one 'LAN' network for you. This LAN network is the LAN of your ISP device, so, as usual, a user @home can now add 18446744073709551616 devices to its LAN.
If one of these devices is a router, it will need a IPv6 from this LAN and another block (prefix) of /64 of each LAN network (there can be more the one).
The thing is : this isn't implement well (understatement) by many ISP/their equipment.
Dono why ...
Maybe a simple /64 is for "home user", and if you want more, you have to sign up for a pro (?) subscription ? Something like that. -
@meluvalli They are called ULA for a reason. But technically you are not wrong.
Do it something like this:
LAN1= fd42:1966:a4fc:5941 : f866:8ab8:5f3b:1a61 /64
LAN2= fd42:1966:a4fc:5942 : f866:8ab8:5f3b:1a62 /64
LAN3= fd42:1966:a4fc:5943 : f866:8ab8:5f3b:1a63 /64
LAN4= fd42:1966:a4fc:5944 : f866:8ab8:5f3b:1a64 /64 -
@Bob-Dig
Perfect. I was able to get it up and running using NAT! All my clients can get out on the one single IPv6 address my pfSense has on the WAN side.Now for my next project... Incoming port forwarding.... I expected it to work the exact same way as IPv4 does using Firewall/NAT/Port Forwarding, but for some reason, it isn't that simple.... I guess back to the drawing board for that part :)
Either way, thank you so much @Bob-Dig for your help! I at least got my outbound IPv6 up and running!
-
@meluvalli said in WAN with /64 Delegation:
Now for my next project... Incoming port forwarding.... I expected it to work the exact same way as IPv4 does using Firewall/NAT/Port Forwarding
Actually it is. If it is not working it may be a problem with your ISP? It has been some days (years) when I ran pfSense like this though.

-
@Bob-Dig
I did a packet capture in pfSense for port 443 (It's a website) and it sees it coming in, but never gets to my server... So I know the ISP isn't blocking it... It's got to be something I have screwed up :(. I'll keep looking into it! Again, I really appreciate your help! Thanks again! -
@meluvalli said in WAN with /64 Delegation:
I expected it to work the exact same way as IPv4 does using Firewall/NAT/Port Forwarding, but for some reason
IPv6 - if implemented correctly, doesn't need NAT anymore.
Just a firewall rule on the WAN that says :
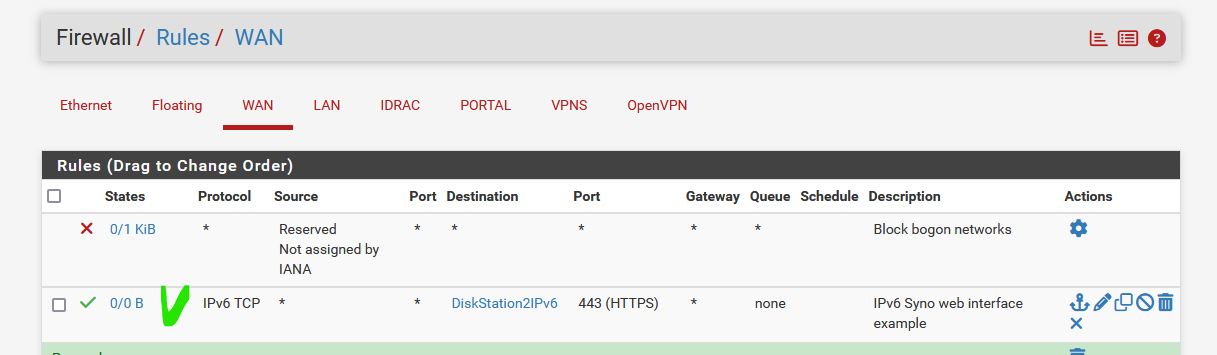
As the WAN interface will be "all the prefixes" so, a /56 or whatever
and- example here -the alias DiskSaton2IPv6 is the GUA IPv6 (an IPv6 in one of my prefixes used on one of my LANs)
this is all it needs to make it accessible.
There is no more Network Address Translation. You can of course still use Port Address Translation, like port "443" to "8443"
After all, the IPv6 my Diskstation2 is using is an IP address that is usable (addressable) world wide. -
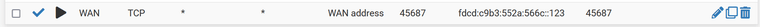
@meluvalli said in WAN with /64 Delegation:
I did a packet capture in pfSense
I did too and it is working. Now I don't run anything on that IP, will have to look if I find something to test easily.
-
@Bob-Dig
I got it working! It was my Linux server didn't have the gateway set :) Once I inputted the gateway for IPv6 all is well!Thanks again!!!!
-
@Gertjan said in WAN with /64 Delegation:
If an ISP providing just one /64 then that is actually completely wrong.
Not completely.

If you have only one /64, it is still good for some NPtv6. Because with that there is some end-to-end reachability for outgoing.
The firewall has not to "change ports" for outbound traffic, as long as real ULAs are used.Example: Lets say we have 3 interfaces with ULAs:
fd1::123
fd2::456
fd3::789fd2::456 gets translated to 2001::456 and goes out to google.
Now the firewall has a firewall state for google and fd2::456.
When traffic comes back in from google to 2001::456 it will be translated to all three ULAs. Two will be dropped but one will pass because there is a state.At least that is how I think this works.

For unsolicited incoming traffic this is not done, maybe it is to dangerous? It will be translated only to the first ULA-Prefix in the list.
Maybe I made this up and there is a NAT-Table for NPT, although it is said that NPT is stateless.
@stephenw10 can slap me if I am wrong. But I do think that you can use one GUA-/64 and use it with several ULA-/64 in pfSense for outgoing. Would be interesting to know how that is actually working.