PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!
-
@denitrosubmena said in PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!:
The only way to get access back to the web UI is to remove the LAN interface from the console
Or just create a rule to allow what you want.. Yes when you only have a wan, remote access is allowed to this wan.. And when you then create a lan this allow is removed. But if you want ssh/gui access to your wan, just add a rule.. if your source is going to be rfc1918 you would also want to disable the block rfc1918 rule that is there by default.
-
@johnpoz said in PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!:
Or just create a rule to allow what you want.. Yes when you only have a wan, remote access is allowed to this wan.. And when you then create a lan this allow is removed. But if you want ssh/gui access to your wan, just add a rule.. if your source is going to be rfc1918 you would also want to disable the block rfc1918 rule that is there by default.
How about remove this rule?!? We do not want the forcing of firewall rules. There is no other firewall in the world that does this thing. If i have WAN and LAN, why must you forcibly update firewall rules???
We know how to setup our own rules
ALso i said i did add rules but pfsense over writes it
I did have a rule to allow access by allowing all from any and placed at the bottom or does that have to be at the very top?
-
@denitrosubmena rules are evaluated top down yes, first rule to trigger wins.
Access is allowed via wan when there is only a wan, or otherwise user would be complaining that they can not access their pfsense to finish the setup.
-
@johnpoz said in PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!:
@denitrosubmena rules are evaluated top down yes, first rule to trigger wins.
otherwise user would be complaining that they can not access their pfsense to finish the setup.
NO please, leave it alone please
As you can see the side effect of this
Also am not sure if you like freedom, but please stop forcing firewall rulesTo prove my point if only WAN then what is difference???
So because one adds LAN all of a sudden it is helpful because of some people complain they can't finish setup?
Anyways let me get to resolve this
SO i have removed the LAN again and now i can access the web UI on WAN addresshere is what i have on the firewall rule, please let me know what to do to allow access on WAN address even after adding the LAN
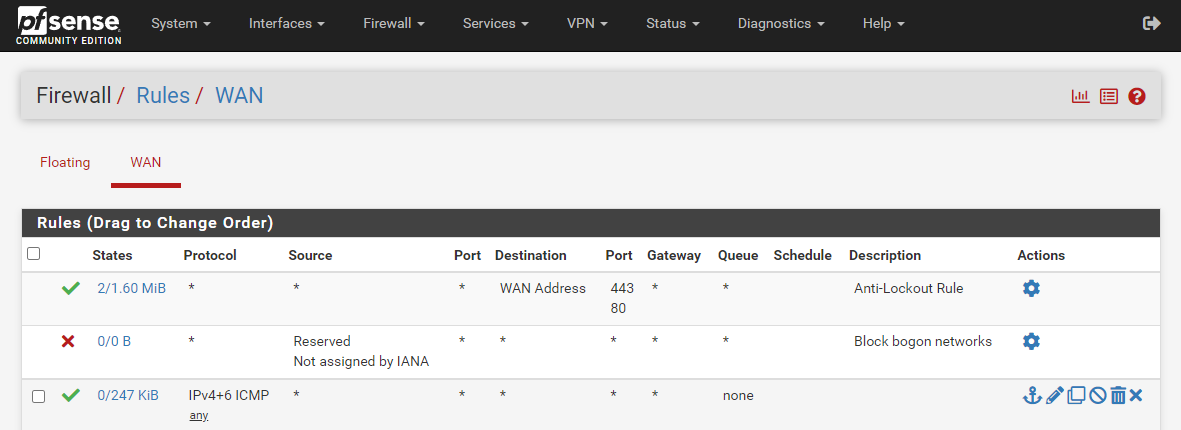
what do i need to do?
-
@denitrosubmena add a rule to allow to what you want..
Here I just duplicated your problem by deleting my lan interface on one of my test vms..
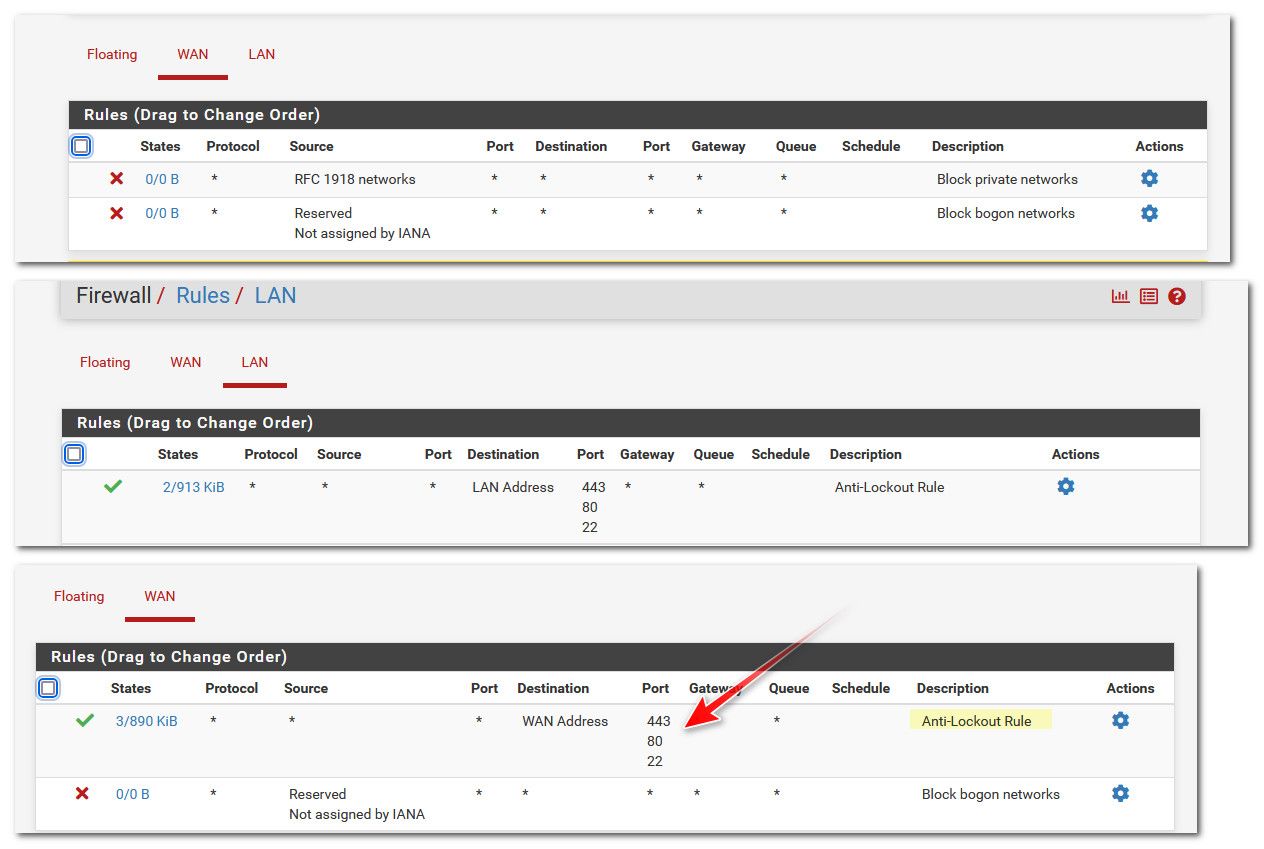
Notice in the last picture the antilock out was moved to the wan, because there is no lan.. So in this scenaro I create a rule to allow access to my gui port 443 before I enable the lan again..
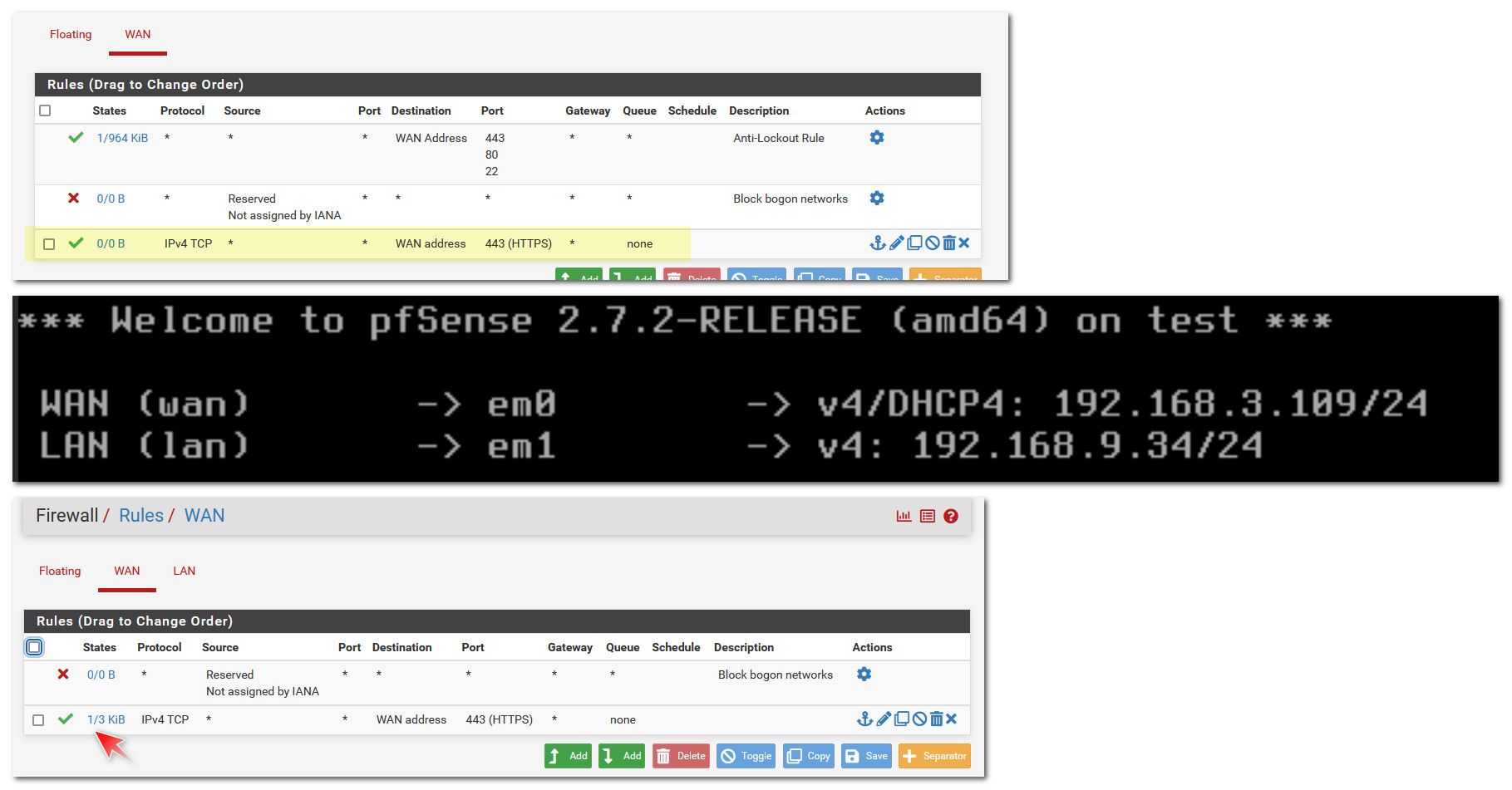
As you can see there I added a rule to allow access to my gui port 443, I then renabled lan.. And now the antilock out rule is gone, but my access to the gui via wan is still work.. See the state shown as connected.
-
Honestly i tried to understand your screenshots but i could not know how or what to do
First here is what i currently have below, so maybe if you write steps by step like steps 1 do this and step 2 add this
that will be a lot helpful
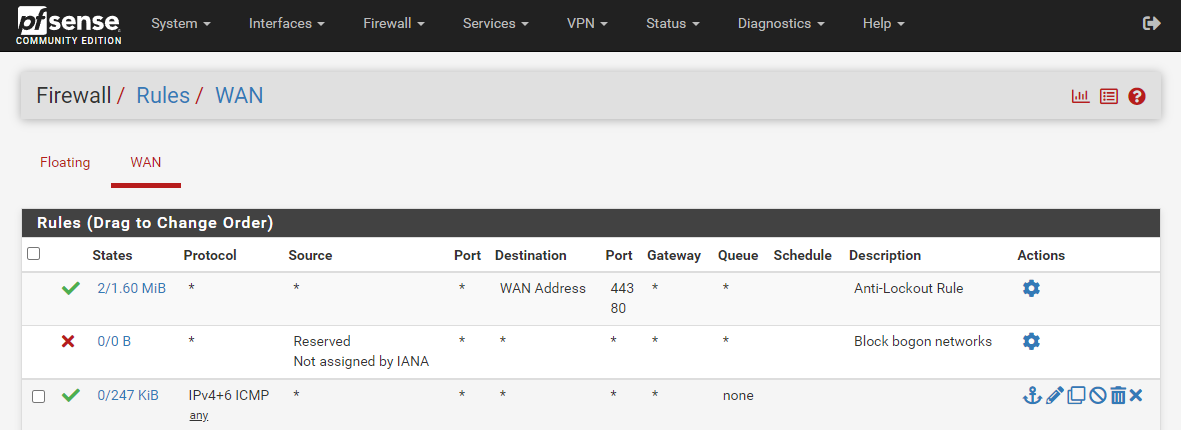
Also one issue is i can not move these 2 default rules, that is another thing with pfsense. It will not allow you to move or delete these default rules.
Remember i can not move or delete those default rules, so it is part of what confuses me about your screenshots because am not sure how you made changes to those rules
-
@denitrosubmena when you only have a wan the rfc1918 rule should go away on its own..
Not sure what sort of step by step instructions you need - I highlighted the rule I added to the wan.. Notice in the first screenshot the block rfc1918 is there by default.. once I deleted the lan interface that rule went away.
are you coming in via a bogon?? If so then before you enable your lan, go into your wan interface and uncheck the bogon network.
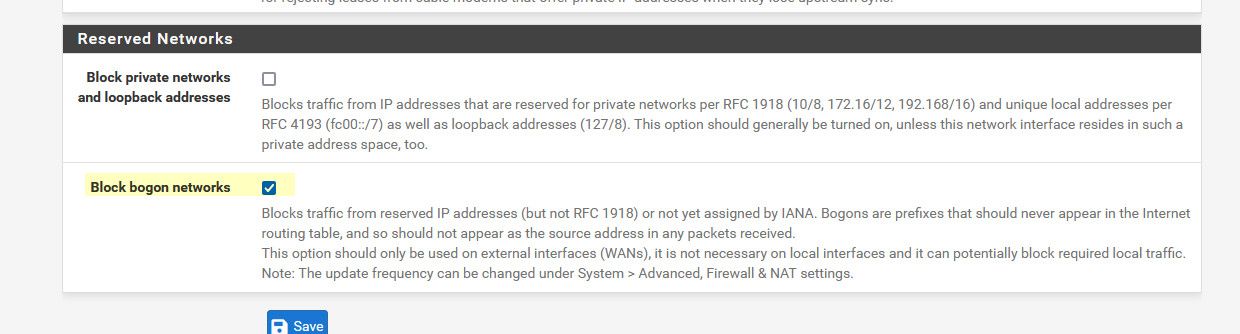
Or just edit your current rule you show on wan that is only allowing icmp to allow your gui port 443 on tcp.
-
Ok i think i see what my issue was i was allowing only ICMP instead of TCP
I updated the rule to TCP now and i also unchecked the block bogdon networks also
So looks good for now, will wait couple minutes to see if i get locked out again
thanks a lot for the help
-
@johnpoz seems my DHCP on LAN seems not to work anymore since i fixed the web UI on WAN address issue
I have tried many things and the VM i have to use the LAN can not get any ip address
this is insane man with this pfsense thing
i was able to get address from DHCP server when i used to have the web UI issue but now i fixed that now no more DHCP working
-
Just make an allow rule for your local computer to access your pfsense WAN IP.
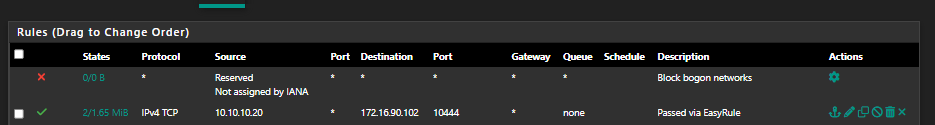
IP: 10.10.10.20 is my local computer I want access from
IP: 172.16.90.102 is the pfSense WAN IP it gets from your DHCP server. -
@MoonKnight said in PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!:
Just make an allow rule for your local computer to access your pfsense WAN IP.
i can access web UI via WAN address now but new issue is vms not able to get LAN ip from dhcp server
and when i did set the static ipv4 ip on the vm, i can not reach the internet and i can not even ping the pfsense gateway address for the LAN interface
so am stuck here wondering what else is going on here
before fixing the web UI access on WAN i was able to get LAN ip from dhcp and ping internet fine but now i cant
-
@denitrosubmena your wan rules have zero to do with dhcp on your lan.. when you try and ping the pfsense IP on the lan from some device on your lan.. Look in its arp table - do you see the mac address of pfsense.. If not then they are not on the same L2 network, if not then that would explain why your not getting dhcp.
What rules do you have on your lan? What rules would have nothing to do with if the device on lan can see the mac address of pfsense lan interface.
Maybe you didn't put in the dhcp rules? hahha just kidding, pfsense auto puts in those rules for you.. But maybe they should stop doing that because you know.. Let you manage your own firewall rules ;)
-
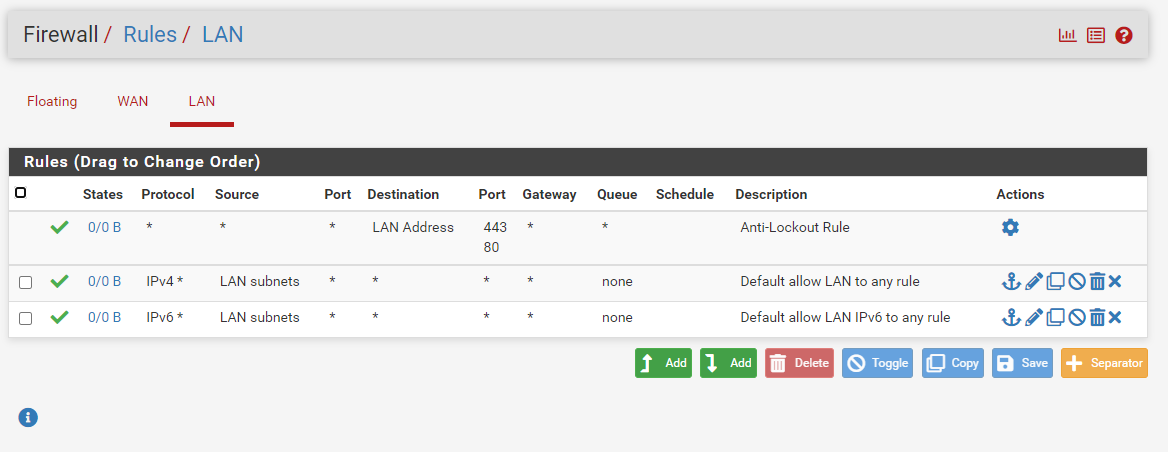
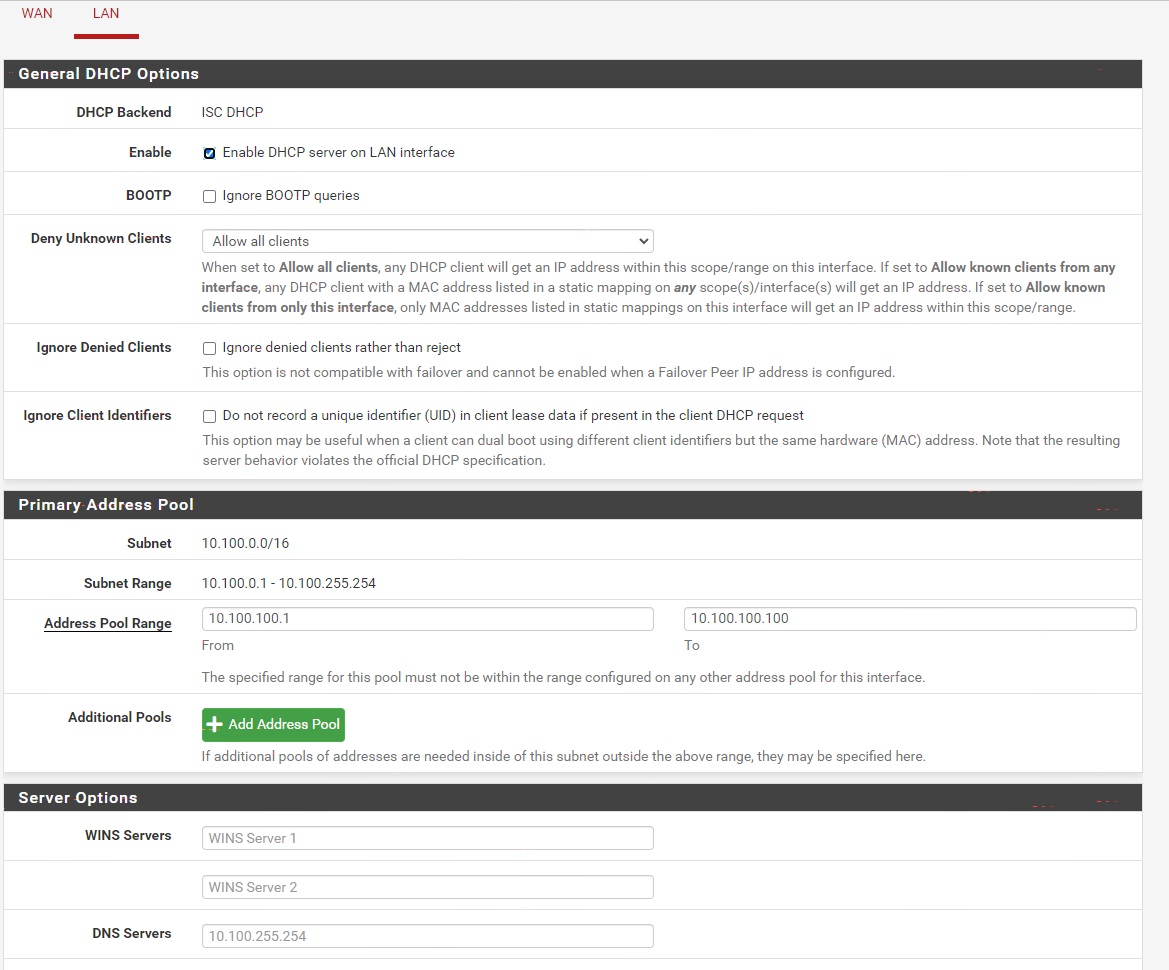
here is rules on LAN
so i restarted pfsense and also restarted the VM
so i can see the static ip address of the VM 10.100.0.1 but it is showing lease time as if it is DHCP lease but it is not and nothing shows up under DHCP lease either so am not sure why it has the expire time
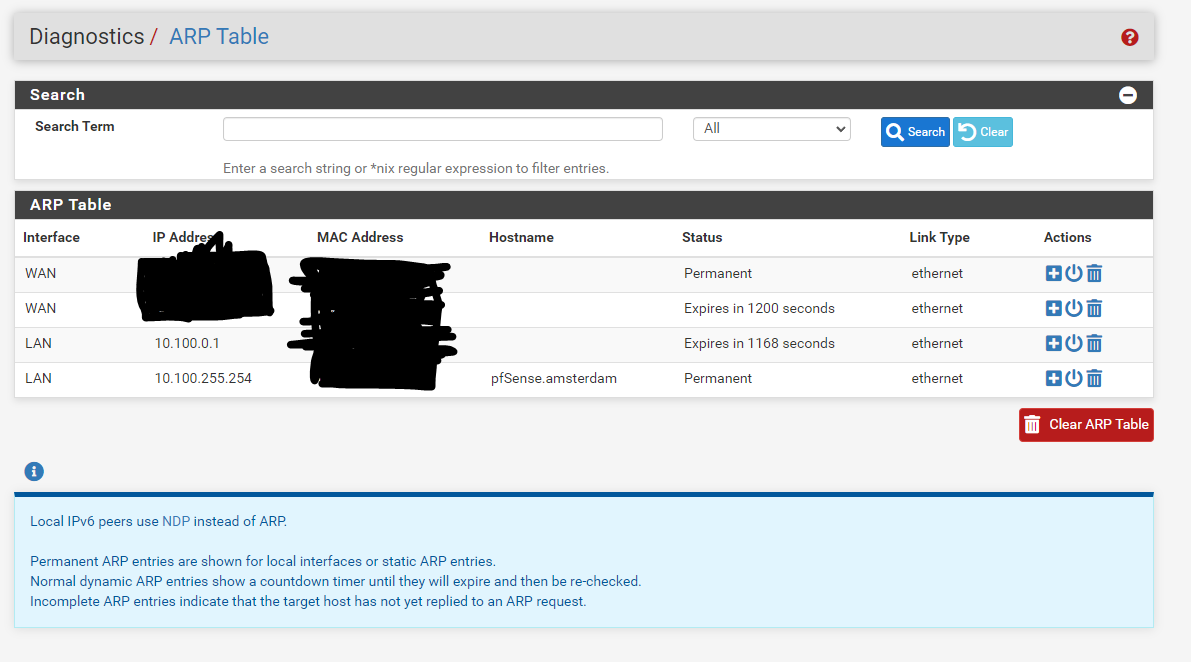
i still cant ping or connect to the internet from the VM and i cant ping the gateway address of the LAN subnet 10.100.255.254 from the VM 10.100.0.1
so am not sure what is going on here and i remembered i could ping the internet before i fixed the previous issue of not being able to access the web UI from WAN ip when LAN is added to pfsense but i can no longer do it
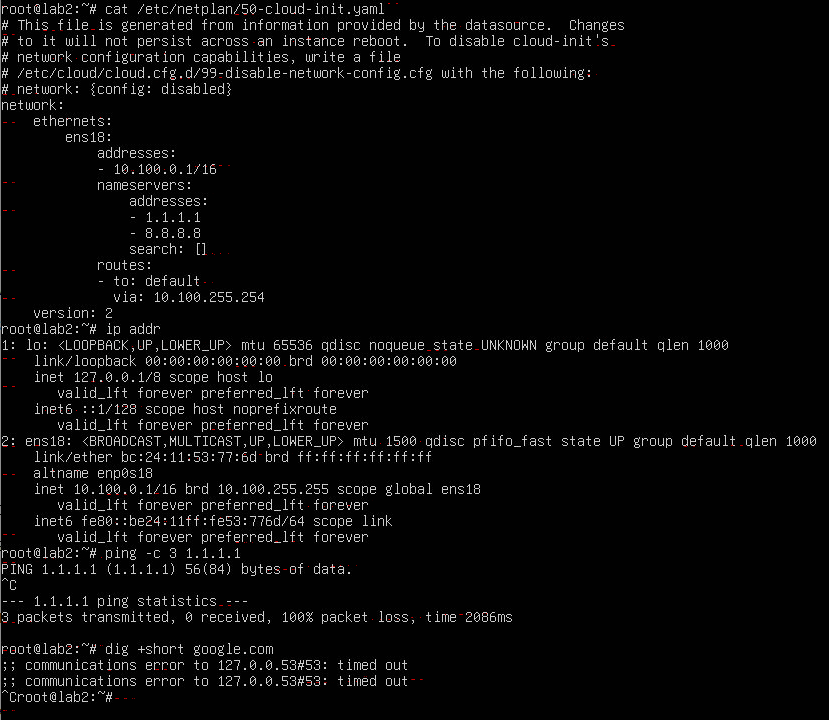
if you need any other info else let me know
-
@denitrosubmena that is not a lease, that is your arp cache..
Where is on your lab2 box its arp cache? do an arp -a.. Do you see pfsense lan mac?
Validate this is the correct mac if you see it.. Seems like pfsense can see the mac of 0.1
Where is your ping to just pfsense IP 10.10.255.254?
You plan on having a shit ton of clients I see with a /16 mask = 65k clients?? ;)
You have the same /16 mask on pfsense lan.. Many a user make a mistake and have it on /32 because that is what the drop down defaults too, etc.
-
here is screenshot with more commands, it simply cant connect to the internet and i cant ping the LAN gateway so that explains it
I have no idea how this is happening
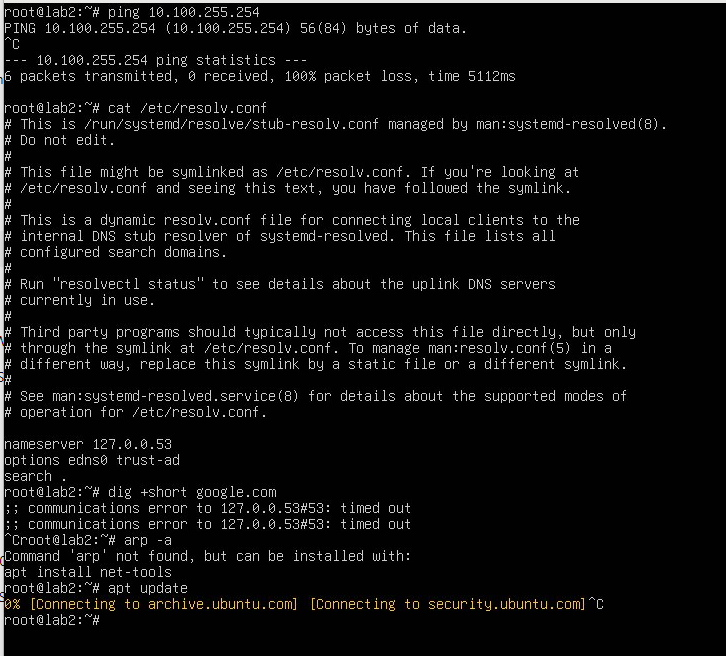
yes LAN is 10.100.0.0/16 it is lab as name suggests so yeah wanted to test with that large subnet
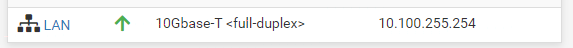
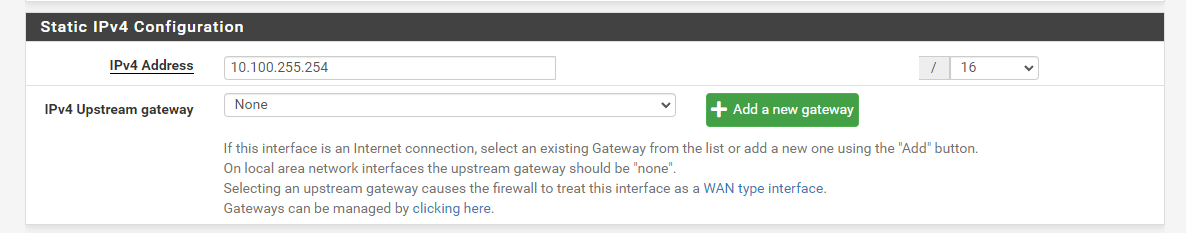
-
@denitrosubmena well if you can not even ping the gateway and your rules allow for ping, which they do - then no your not going to get to the internet..
Why would think you could update with apt if you can not even ping your gateway?
-
well i just tried all that so i can show you what am facing
i know if i cant ping gateway i cant reach internet, i know but just wanted to show what is going onSo any way out of this?
-
@denitrosubmena well since your error is just timeout with your ping from your client.. that points to it seeing a mac for that IP.. Is it the right one? can't tell without viewing your arp table.
so if a client doesn't know the mac address of an ip your trying to ping you would normally see an error like so
linux
user@UC:~$ ping 192.168.2.66 PING 192.168.2.66 (192.168.2.66) 56(84) bytes of data. From 192.168.2.13 icmp_seq=1 Destination Host Unreachable From 192.168.2.13 icmp_seq=5 Destination Host Unreachable From 192.168.2.13 icmp_seq=8 Destination Host Unreachablewindows
$ ping 192.168.9.44 Pinging 192.168.9.44 with 32 bytes of data: Reply from 192.168.9.100: Destination host unreachable. Reply from 192.168.9.100: Destination host unreachable. Ping statistics for 192.168.9.44: Packets: Sent = 2, Received = 2, Lost = 0 (0% loss),As to what is going on with your setup I not sure.. Is this real hardware, all on a vm - some hardware and vm?
When you ping from the client to pfsense lan IP while sniffing on pfsense lan interface - do you see those pings?
When you were messing around with rules - did you happen to put some rule in the floating tab that could be blocking. But that wouldn't stop dhcp since when you enable dhcp, pfsense puts in hidden rules above where floating rules that allows for dhcp..
Your wan IP (via dhcp?) not overlapping with the /16 you put on the lan is it?
-
here is packet capture when i ran ping from the VM to pfsense LAN gateway
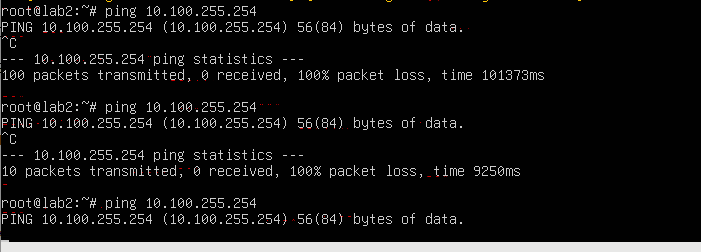
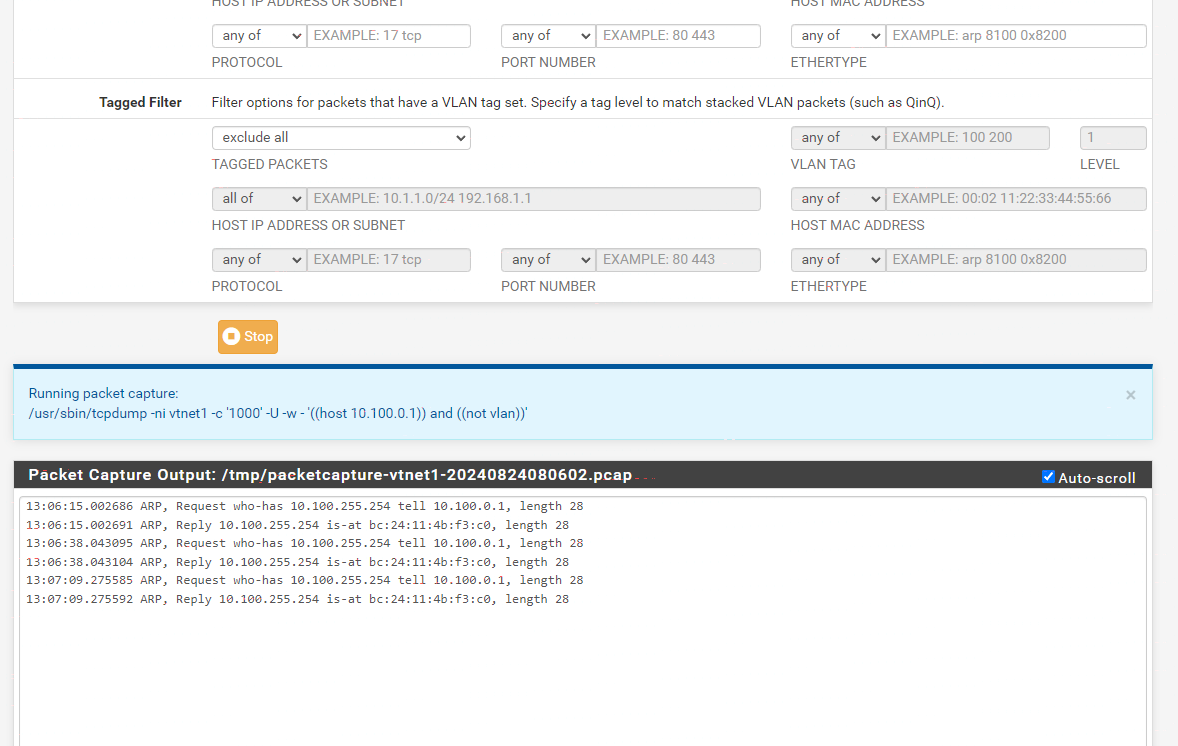
pfsense is VM in proxmox and then VM 10.100.0.1 will use pfsense as router
-
I fixed the issue!!!
stupid me, so i turned on firewall on the pfsense VM in proxmox which was blocking everythingI turned off the firewall and now am good, VM is working fine and can reach internet
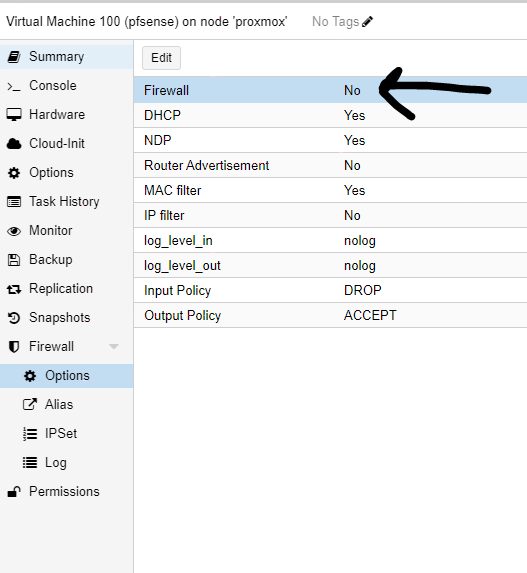
what a day
thanks for all your help