PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!
-
@denitrosubmena well since your error is just timeout with your ping from your client.. that points to it seeing a mac for that IP.. Is it the right one? can't tell without viewing your arp table.
so if a client doesn't know the mac address of an ip your trying to ping you would normally see an error like so
linux
user@UC:~$ ping 192.168.2.66 PING 192.168.2.66 (192.168.2.66) 56(84) bytes of data. From 192.168.2.13 icmp_seq=1 Destination Host Unreachable From 192.168.2.13 icmp_seq=5 Destination Host Unreachable From 192.168.2.13 icmp_seq=8 Destination Host Unreachablewindows
$ ping 192.168.9.44 Pinging 192.168.9.44 with 32 bytes of data: Reply from 192.168.9.100: Destination host unreachable. Reply from 192.168.9.100: Destination host unreachable. Ping statistics for 192.168.9.44: Packets: Sent = 2, Received = 2, Lost = 0 (0% loss),As to what is going on with your setup I not sure.. Is this real hardware, all on a vm - some hardware and vm?
When you ping from the client to pfsense lan IP while sniffing on pfsense lan interface - do you see those pings?
When you were messing around with rules - did you happen to put some rule in the floating tab that could be blocking. But that wouldn't stop dhcp since when you enable dhcp, pfsense puts in hidden rules above where floating rules that allows for dhcp..
Your wan IP (via dhcp?) not overlapping with the /16 you put on the lan is it?
-
here is packet capture when i ran ping from the VM to pfsense LAN gateway
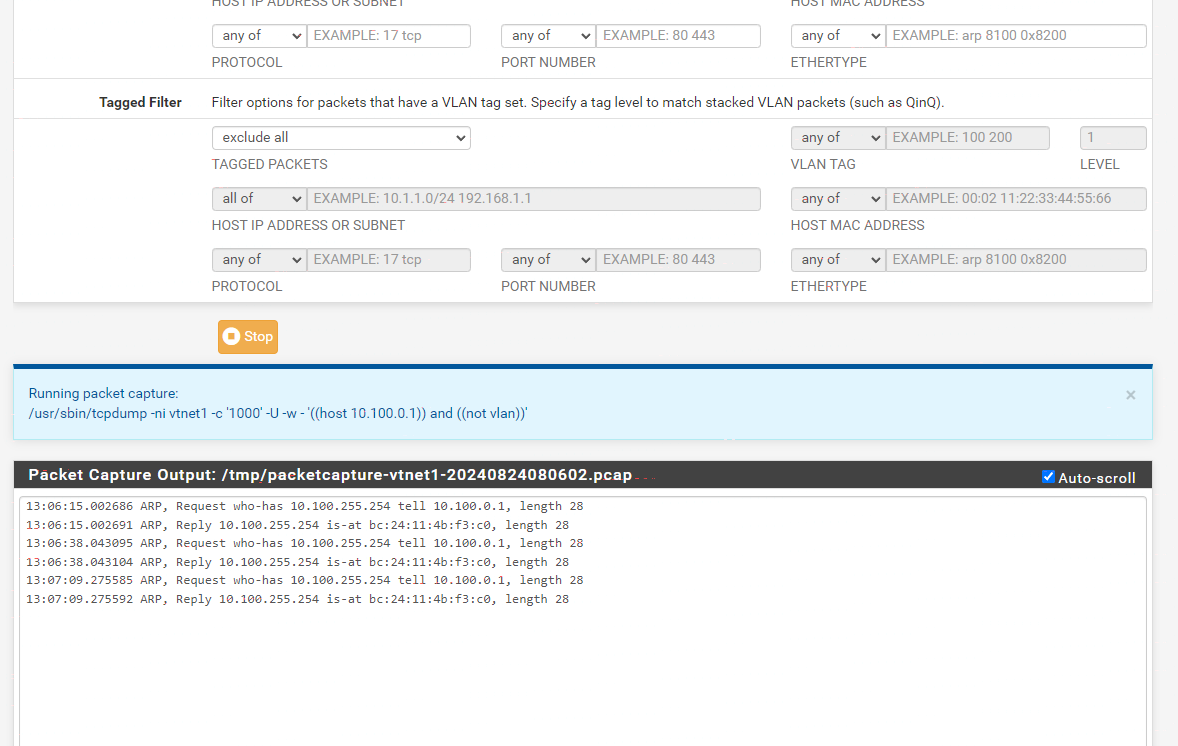
pfsense is VM in proxmox and then VM 10.100.0.1 will use pfsense as router
-
I fixed the issue!!!
stupid me, so i turned on firewall on the pfsense VM in proxmox which was blocking everythingI turned off the firewall and now am good, VM is working fine and can reach internet
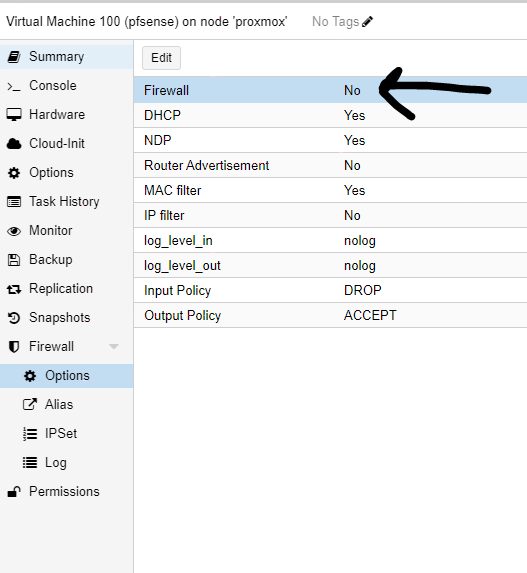
what a day
thanks for all your help
-
@denitrosubmena I was going to say you see the arp and the reply.. so that screams firewall between somewhere, be it on the client or something between. If was a firewall issue on pfsense, you would of still seen the pings - just they would not of been allowed up the stack to be answered.
-
@johnpoz New “laissez-faire” firewall technology…eh, it’s probably OK, sure, go ahead.
-
@SteveITS the best kind of firewall policy

-
@denitrosubmena said in PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!:
My use-case i have pfsense installed at the edge and i need to access it via the WAN address that is public, like every other hardware router in the damn world that is the one that connects directly to internet
To be fair, there's no router anywhere, sold commercially, that's set up to allow access from the public WAN to its webGUI. At least not any that didn't ship without being misconfigured by accident at the factory. Are you suggesting you wanted pf to forward 80 and 443 by default? This is all rhetorical anyway, as pf definitely allows a local connection to the WAN port during setup, which makes things much easier. When LAN has been set up, it's obviously not needed anymore.
@denitrosubmena said in PLEASE stop enforcing firewall rules on pfsense!!! Let us manage our own firewall rules!!!:
proxmox which was blocking everything
I'm new here, but even I think it would have been a great idea to mention right away that pfSense was being virtualized. And on top of that, behind some POS like Proxmox.