PfSense blocks traffic coming from SubnetA to SubnetB
-
Hi @viragomann,
I've made an error. Here are the new result from a fresh test
From SiteA - Interface VLAN2
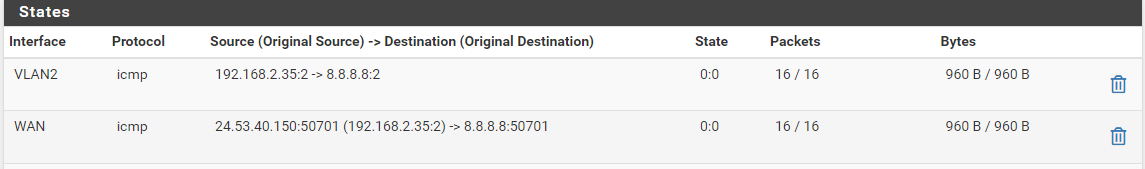
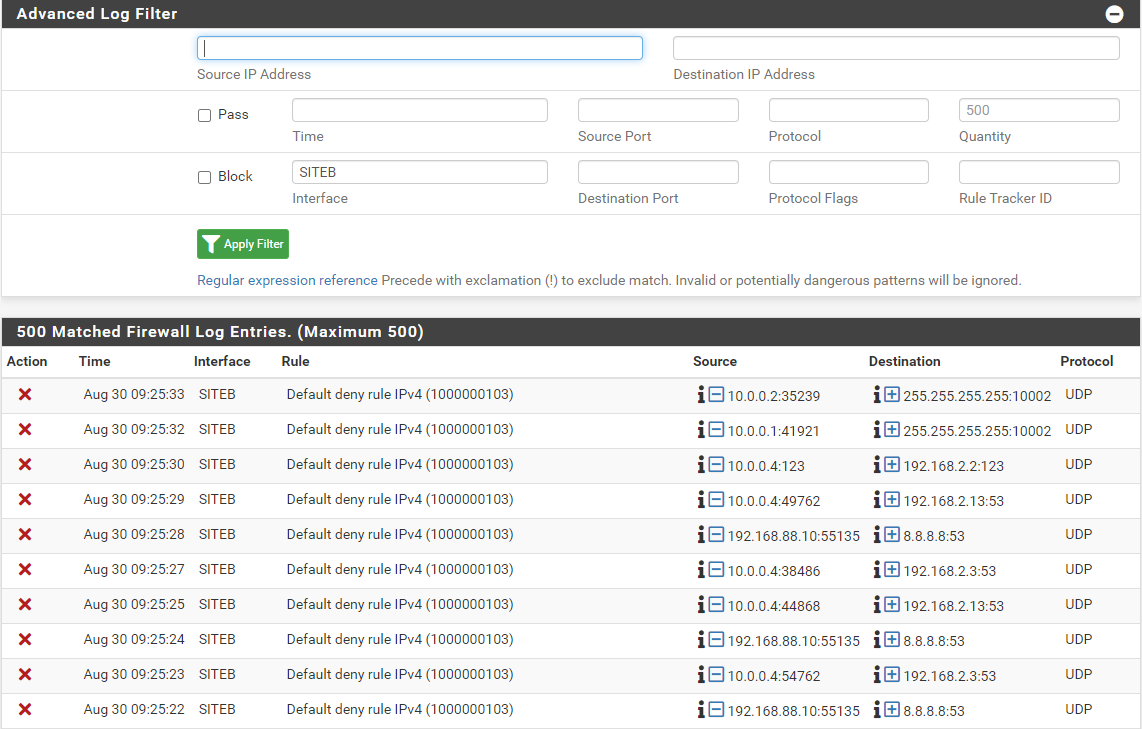
From SiteB - Interface SITEB
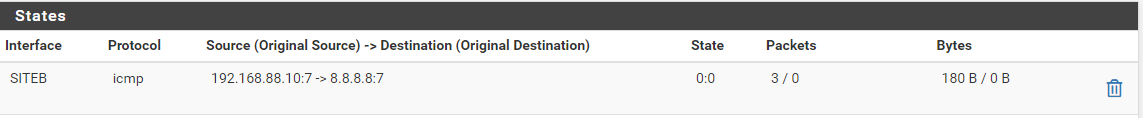
So we can see that nothing from Interface SITEB in going to the WAN Interface.
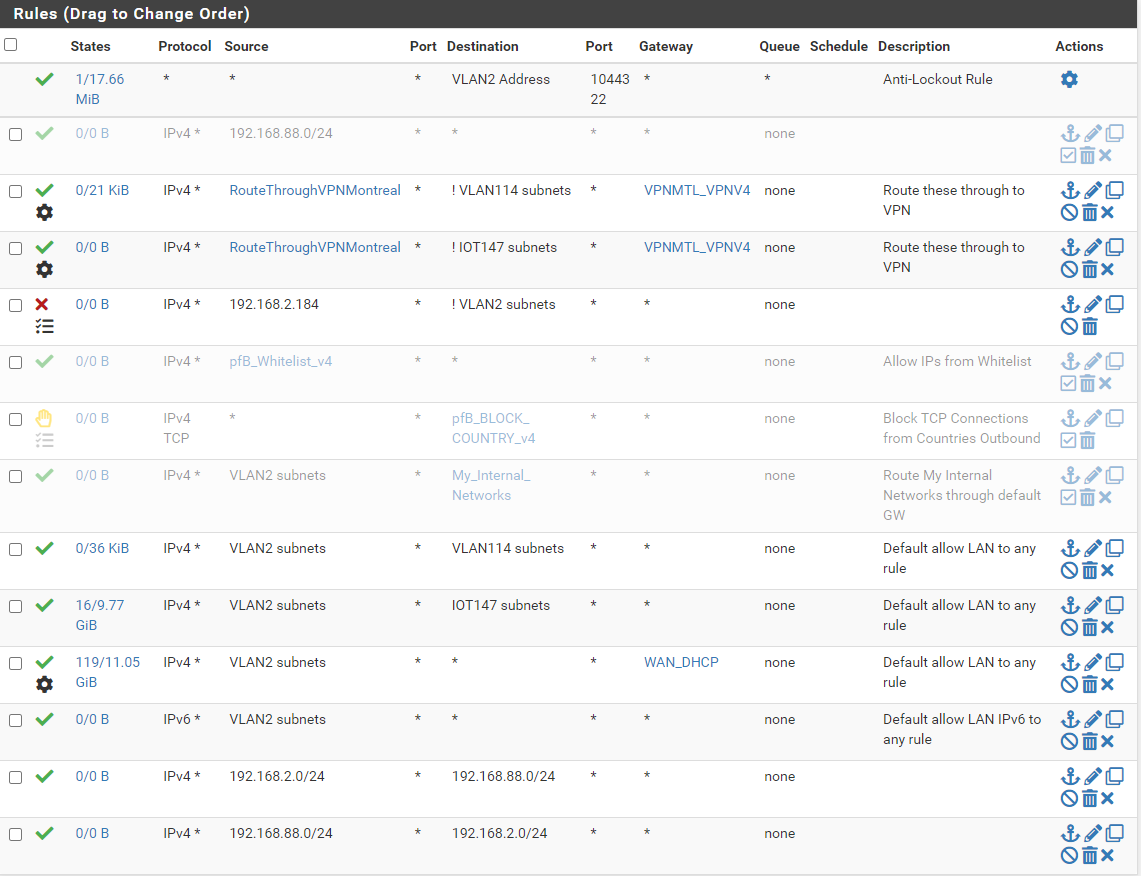
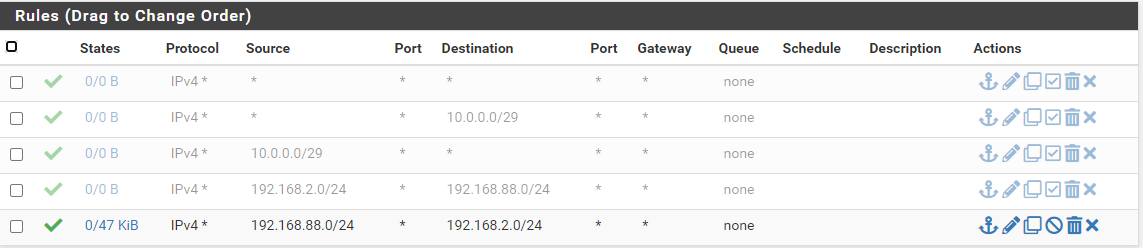
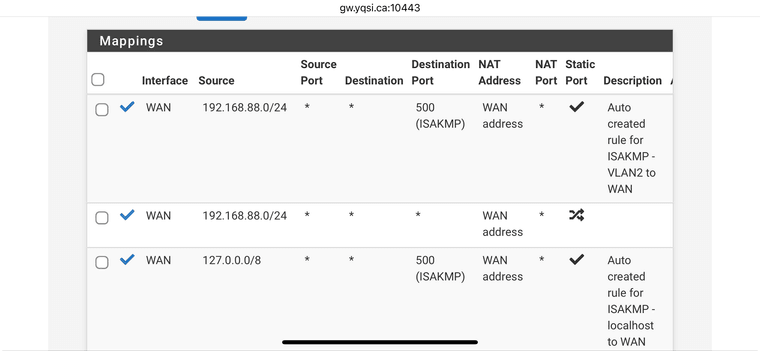
Here are the rules on the WAN interface:
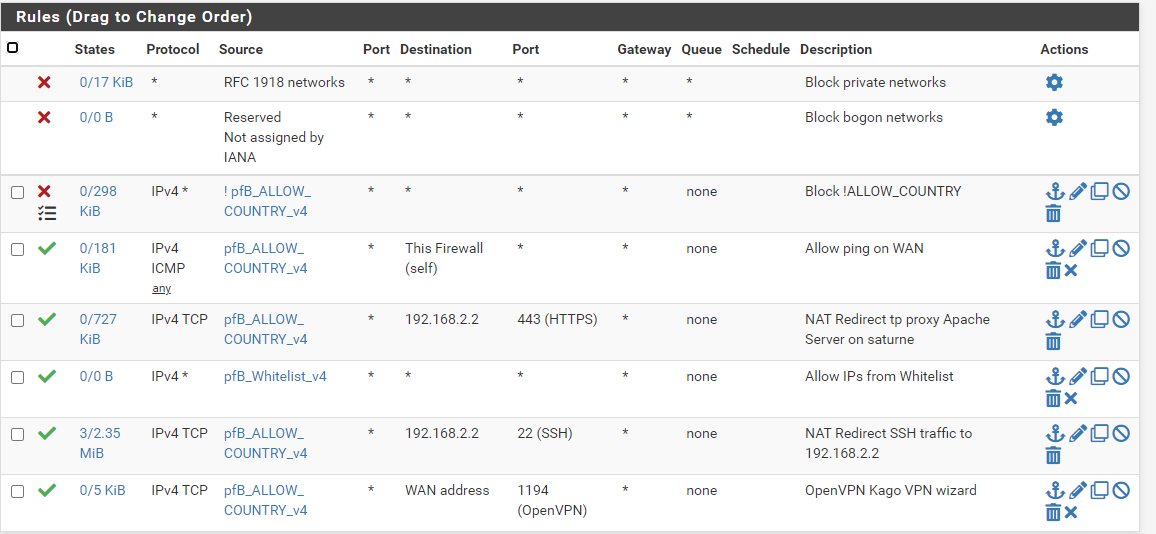
And the rules on the SITEB Interface:
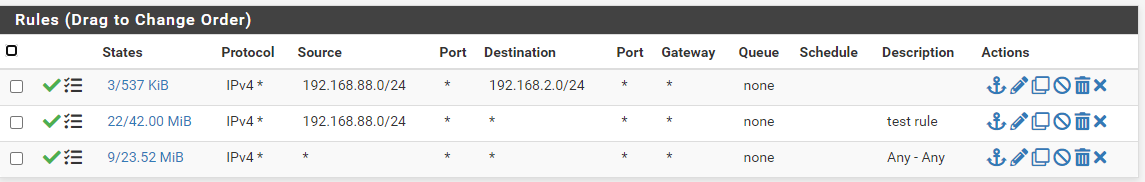
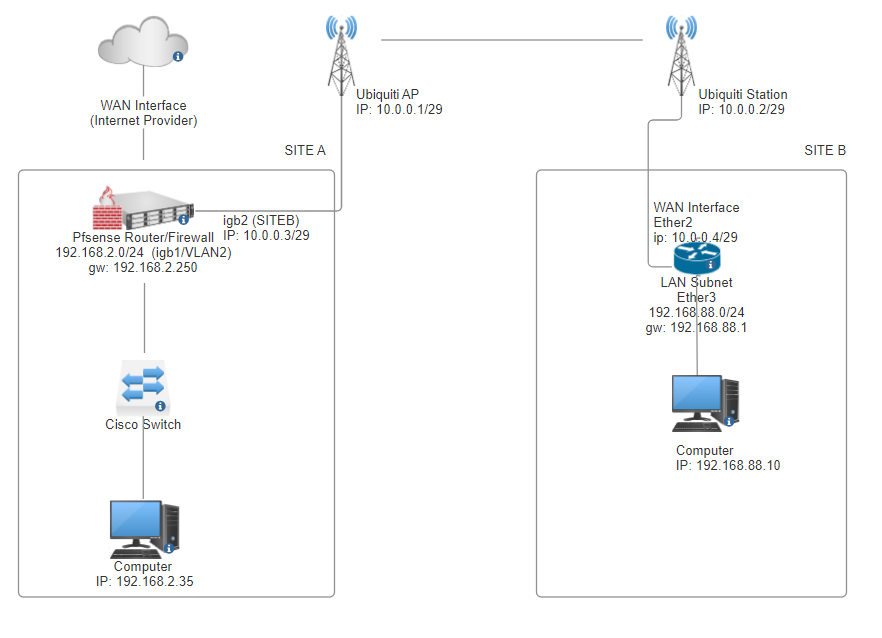
Here are the interface configuration:
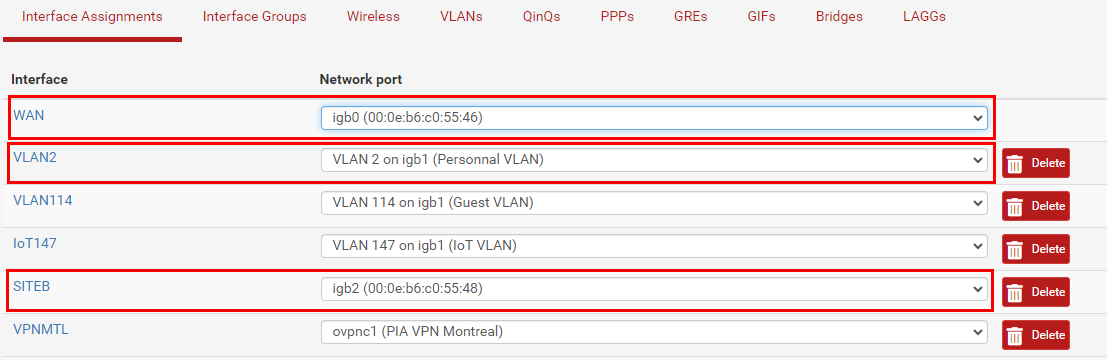
All those 3 interfaces are physical interfaces on my PfSense router.
Outbound rules:
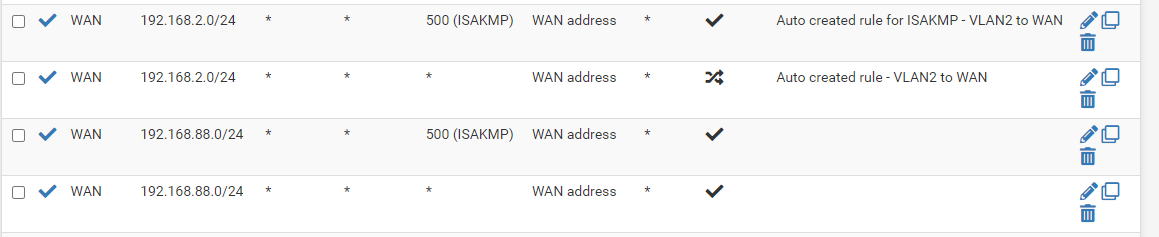
I really don't understand why nothing is going to the WAN interface from SITEB interface.
Thanks again!
Yanick
-
Hi @viragomann,
I found something.
Just after sending the reply, I did change this:
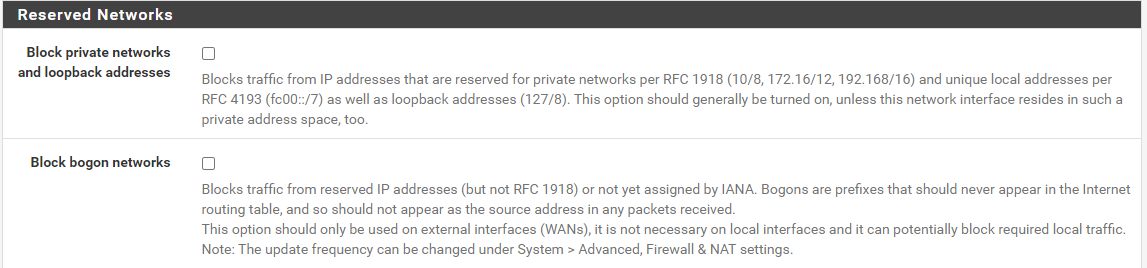
Those two options were selected on the WAN interface.
After that I see I could ping 8.8.8.8, but nothing else... Then if I stop the ping to 8.8.8.8, it won't restarts until I play again with those parameter (re-enable them).
I reset all states; no luck, I rebooted the pfsense, same thing...
At this moment I have a running ping from SITEB to 8.8.8.8. It works. I see the corresponding traffic on the igb0 (WAN) interface using
tcpdump.Now, if I stop that ping, then wait for the states being cleared, then restart it, it is no longer working.
Maybe I am running into a bug with pfsense, but all of this has no sense at all.
Thanks
Yanick -
@yquirion
WTF! Just noticed, that you have "static port" checked in the outbound NAT rule.
It wasn't checked before!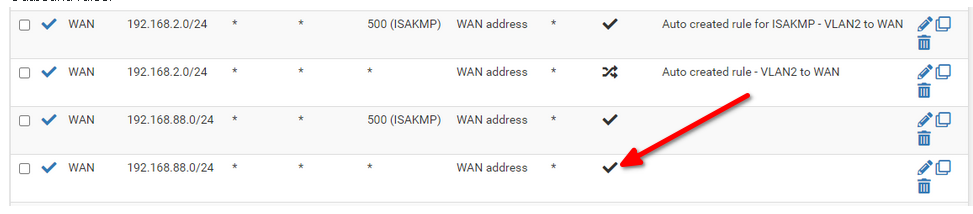
Why did you change things, you're not advised to change? You needed just to edit the rule and change the interface to WAN.
This makes it hard to help you with your issues.Those two options were selected on the WAN interface.
At A WAN this setting should be checked. At B not, mentioned in my very first post.
At A VLAN2 it has to be unchecked. But this might have been the case before, otherwise you were not able to access A from B at all. -
Hi @viragomann,
That is very odd. I never notice it. Sorry about that. However, I just look at it and since that post, it has been corrected.
Regarding the 2 options, I don't have those on siteB because siteB is using a Mikrotik router. From the pfsense router on sitea, those options are disabled on all interface (was only enable on the WAN before).
I'm not home for the weekend so I cannot make any other test on this.. But that os very strange that, while pfsense is applying the change of the
Block private networks and loopback addresses, for a second the ping will work until I cancel it and the connection is being cleared of the state table...Thanks again, and I'm really sorry having made that mistake. I'm just testing stuff between replies!
Yanick
-
Hi @viragomann,
I found it!
It was because of a miss configuration into my client OpenVPN connection.
Here is a post that explain what was my problem:
https://www.reddit.com/r/PFSENSE/comments/i125ig/default_route_now_set_to_vpn_client_instead_of/
I was looking into this because of this:
# route get 1.1.1.1 route to: one.one.one.one destination: default mask: 128.0.0.0 gateway: 10.4.112.1 fib: 0 interface: ovpnc1 flags: <UP,GATEWAY,DONE,STATIC> recvpipe sendpipe ssthresh rtt,msec mtu weight expire 0 0 0 0 1500 1 0That gateway of 10.4.112.1 was the gateway of my OpenVPN client connection. When I stop the service for that VPN connection, that was the result of the same command:
/root: route get 8.8.8.8 route to: dns.google destination: default mask: default gateway: modemcable001.40-53-24.mc.videotron.ca fib: 0 interface: igb0 flags: <UP,GATEWAY,DONE,STATIC> recvpipe sendpipe ssthresh rtt,msec mtu weight expire 0 0 0 0 1500 1 0So I made search on why the OpenVPN client was adding that route to the routing table:
0.0.0.0/1 <<VPN Interface Gateway IP>>And I found the post tjhat somve my issue.
I would like to thank you very much as well as @skenigma for your time helping me solving the issue.
Best Regards,
Yanick