How do I renew this Certificate Athority
-
Asked GPT to summarize the conversation above.
Summary of Actions for Expiring Let's Encrypt Certificates (ISRG Root X1)
-
Understand the Situation:
- The ISRG Root X1 certificate is expiring, and it was previously cross-signed by another authority to build credibility.
- The self-signed ISRG Root X1 certificate should now be used as the cross-signed version is no longer necessary.
-
Remove Expiring Certificates:
- You cannot renew the expiring ISRG Root X1 certificate directly. Instead, remove it from the System > Certificate > Authorities section in pfSense.
-
Import Updated Certificates:
- Obtain the self-signed ISRG Root X1 certificate and, optionally, the ISRG Root X2 certificate in PEM format from Let’s Encrypt.
- Import these updated certificates into pfSense under System > Certificates > Authorities.
-
Check and Renew Other Certificates:
- If you're using ACME for managing certificates, remove the existing ACME CA entry under System > Certificate > Authorities.
- Go to the Services > ACME section and manually renew the relevant ACME certificates. This should regenerate the required certificates and possibly download the newer CA certificates automatically.
-
Verify the Updated Certificates:
- After importing the updated certificates or renewing the ACME certificates, verify that the services depending on these certificates are still functioning correctly and that the warning messages have disappeared.
This process ensures that you are using the latest trusted root and intermediate certificates, avoiding issues with expired certificates.
-
-
@BobBrown lol love it.
-
@BobBrown said in How do I renew this Certificate Athority:
- The ISRG Root X1 certificate is expiring, and it was previously cross-signed by another authority to build credibility.
I read this thread and got confused. Why is the ISRG Root X1 certificate expiring? Letsencrypt shows "Validity: until 2030-06-04": https://letsencrypt.org/certificates/
Why do you want it in System > Certificates > Authorities? I only have the intermediates there: R10, R11, and now E6. I don't think I ever had the X1 there.
-
@pfpv said in How do I renew this Certificate Athority:
Why do you want it in System > Certificates > Authorities? I only have the intermediates there: R10, R11, and now E6. I don't think I ever had the X1 there.
I agree, it is confusing. The confusion is multiplied because the X1 and X2 CA certs are already part of the OS bundle, so it should be unnecessary to install via the GUI (your situation). In my case however, I am unable to have a functional system without the X1 CA cert being manually imported. For my IPsec VPNs I use mutual certificate authentication in the P1s, and if I do not have the X1 cert imported, the tunnels will not establish. I have tried several times to tear everything down and rebuild to no avail, so I have left it as a bit of an annoying puzzle for now. At some point I will get it beaten into submission though it feels like it may take a complete rebuild from scratch which I've just not wanted to invest the time in.
--Larry
-
@LarryFahnoe
OK, I understood. Do you also think that the X1 certificate is expiring soon? That was the most confusing part. -
@pfpv There was an older self-signed X1 cert that expires on Sept 30 if I recall correctly, hence some urgency for some.
-
@LarryFahnoe : "In my case however, I am unable to have a functional system without the X1 CA cert being manually imported."
Same here: I have IPSec tunnel between two data centers.
-
@BobBrown to be clear, are you running into the same problem: need to have the X1 cert manually imported in order to have functioning IPsec tunnel? If so, are you also using mutual cert auth between the P1s?
--Larry
-
@BobBrown said in How do I renew this Certificate Athority:
I have IPSec tunnel between two data centers.
Why would you be using acme certs for this??
I mean random sites would not be creating a tunnel with you, so why would you need a public trusted cert signed by a public CA. Just create your own CAs, they could even be different CAs on each side of the tunnel. Sign your own certs, you could make them valid for a lot longer than the 90 days any certs by amce would be good for.
-
@johnpoz said in How do I renew this Certificate Athority:
why would you need a public trusted cert signed by a public CA
I'm clearly not Bob, but... Why not use a publicly trusted cert? Perhaps I'm daft, but it seems to me that acme provides another potential benefit in that the certs are refreshed periodically which seems to be better than a cert that changes infrequently. I'm further inferring that Lets Encrypt has a better ability to manage their CA than I do--pfSense can be a CA, but can't very well meet the recommendation to keep your CA offline. I do not claim to be a PKI expert by any means.
Those comments aside, the puzzle I've still not worked out is why stronswan seems to require an imported X1 cert when one is already in the OS bundle. I've attempted to document some of this here https://forum.netgate.com/post/1177287
--Larry
-
@johnpoz lack of experience.
At the time of configuration I outsourced the PFSense configuration to a contractor. -
@LarryFahnoe said in How do I renew this Certificate Athority:
Why not use a publicly trusted cert?
Because its just another thing that could break for one.. And there is zero point to it.. Refreshing the cert does nothing.. Are you going to change something in the cert, like the key type or digest? Can't really do that with a refresh anyway.. This would be a new issue. Which using your own CA allows you to control when that happens easier vs having to renew something every 90 that has zero need to be renewed that often.
Just like I would never use acme for for road warrior vpn either.. There is zero point to it.. Since all the devices that would be connecting would be under my control.
Don't get me wrong acme is great, and use them myself for a couple of certs, but that is because there are clients outside of my control accessing them for sites I publish.
But for every other thing I just use my own CA and issue my own certs.. Like for the https on my nas, my switches, my unifi controller, my printer gui, my camera and nvr guis, etc. I can then add rfc1918 IPs as SAN, I can use whatever domain I want without it having to be public - using home.arpa currently.. And since they are issued by a private CA there is not 365 day limit.. I issue the certs for 10 years, and more than likely won't have to worry about redoing those certs until I replace the hardware, etc. A public CA and domain on those things make little sense because the only one accessing them is my or my devices that I control.
The access is local to my network, so the need of https is kind of pointless anyway - but browsers complain about accessing a web gui that is not https.. So I put a 10 year cert on them to shut the browser up ;)
-
@johnpoz said in How do I renew this Certificate Athority:
Refreshing the cert does nothing
Perhaps I am incorrect, but I thought that each cert was unique & thus provided unique keying material for use in the remainder of the connection.
Your other commentary is appreciated and is consistent with my own typical desire to be able to be responsible for the rest of the tools in use. I have simply held off from running my own CA as each time I've looked into it, the strong suggestions are to keep the signing CA offline which represents more hassle than I felt was warranted by my usage. LE & acme seem to provide a level of service for all the certs I need.
It is just a puzzle to me that strongswan on pfsense only seems to work when the X1 cert is manually imported, which makes no sense since the same cert is already in the CA bundle used by pfsense.
--Larry
-
@LarryFahnoe said in How do I renew this Certificate Athority:
each cert was unique
Yeah its unique - you think someone is going to brute force generation of your cert so you should change it every 90 day? But the uniqueness of the cert doesn't matter - any cert can auth that has been signed by the CA..
strong suggestions are to keep the signing CA offline
Really - are you working for the DoD or something? Come on, if some compromised your pfsense.. Access to the CA is the least of your worries.. There is security, and then there is tin foil hat cutting off the blood to your brain..
Are you wanting to become a public CA? And compete with acme? How is their signing CA offline when you can get a cert in 30 seconds.. How is any public CA offline when they issue certs in a few minutes.. They have an intermediate signing CA, which sure you could do that if you want.. But I would just not wear the tinfoil hat that tight.. Did you catch that really don't even need a cert because the guis are on my local network - its to shut the browser up.. But now you want to take your CA offline?
But sure if you want create the CA, then take it offline - I mean how often are you creating a cert for setting up a tunnel? I wouldn't do that if you were creating road warrior certs ;) Again you live the intermediate signing CA online, and take the Root CA offline.. But again this seems a bit over the top to me..
I have no idea about what strongswan is wanting to see, but if the CA is the same signing CA doesn't matter where it came from be it in the OS or you added it.. But does pfsense even use the OS ca's for stuff like openvpn, or ipsec?
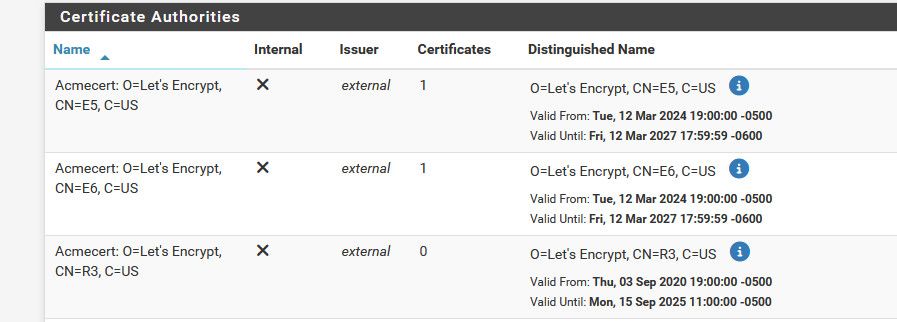
They are not presented to be chosen when you setup openvpn that is for sure - only the CAs listed in the cert manager auth are allowed to be picked from.
To that specific amce CA - I deleted that long time ago when they replaced it.. These are the only amce cas I have liste
-
@johnpoz said in How do I renew this Certificate Athority:
There is security, and then there is tin foil hat cutting off the blood to your brain..
Fair enough John. I've been round the block enough times to feel comfortable with my approaches to security but can certainly appreciate your perspective. I've acknowledged that I'm not expert in this area & am just seeking to improve my understanding of the technology in use, specifically why I need to manually import the X1 cert when it is already present in the system...apparently some tools in pfsense use the OS CA bundle & some do not; seems like strongswan doesn't and openvpn (if that is what you're using) does. In the meantime, thanks to the GD, we can listen to the music play.
--Larry
-
@LarryFahnoe said in How do I renew this Certificate Athority:
apparently some tools in pfsense use the OS CA bundle & some do not
This caused me some confusion. Then it dawned on me the acme certificate management package doesn't interact with system CA bundle.
Thanks @LarryFahnoe and @johnpoz for the very helpful discussion. -
@darcey If I were to guess, I would think packages like pfblocker or something that downloads lists from https urls would use the OSes trusted say to know those certs are valid.
Pfsense itself would CAs in its OS store for like checking for updates and stuff from pfsense.
But any packages or service that allows you to be specific for a CA or certs to auth with prob doesn't use the OS store and only stuff you have in the cert manager, like haproxy, openvpn, freerad server, etc.
-
@LarryFahnoe said in How do I renew this Certificate Athority:
thanks to the GD, we can listen to the music play.
You got that right ;) hahah - I think you might be the only person who as ever caught that quote, or at least commented on it!
If you let your hair grow a bit and let the stache get a bit longer you could maybe pass for Bobby with a quick glance btw ;)
-
Well then, for those who're not catching John's reference: http://gdradio.net The music plays the band!
--Larry
-
@LarryFahnoe here is a link to just before the line ;)
Grateful Dead - Franklin's Tower - 10/31/1980 - Radio City Music Hall, New York, NY
Couple good zoom ins of Jerry playing tiger, and a few good Jerry smile though out..