Question about inter-Vlan traffic and interface Concept
-
I would like to clarify 2 inter-Vlan traffic and Pfsense interface concepts that I can't seem to figure out.
I have setup Vlans on Pfsense using a modem, the Pfsense as a router, as well as an access point plugged to the pfsense LAN for wifi for the Vlans. So we have 4 networks: LAN, OPT, Vlan Home, and Vlan Guest. And I can only access the Pfsense GUI from the LAN and OPT networks via their respective address on port 443.
Lan Address and Subnet: 192.168.1.1 & 192.168.1.0/24
OPT Address and Subnet: 192.168.2.1 & 192.168.2.0/24
VLAN Home Address and Subnet: 192.168.10.1 & 192.168.10.0/24
VLAN Guest Address and Subnet: 192.168.20.1 & 192.168.20.0/24
(Additional info: Access Point ip address is 192.168.1.2)Given this, my questions are as follows:
1- My firewall rules on Pfsense prevent the Guest Vlan from communicating with the Home Vlan. But both Vlans are being used by devices over wifi, so doesnt that mean that the inter-Vlan traffic never reaches the Pfsense firewall and remains within that AP? I've read that this may just apply to traffic on same subnet on the AP (let's say devices on the same Vlan Guest contacting each other). Also I've read that the AP does not do routing, and thus any traffic has to go to router. Kindly confirm.2- I wanna ask which interface does the actual Pfsense router as well as the Access Point belong to? Like when I connect to Pfsense from let's say the OPT interface, then the OPT firewall rules apply. If OPT is disallowed internet access and only allowed GUI access on 443, then I can access the GUI but cant update the Pfsense firmware from the GUI. Is the logic here flawed?
3- Follow-up on above: Then how do I think about the Access Point which is plugged to the LAN port and is offering wifi at home and handling tagged traffic for my Vlan Guest and Vlan Home networks, while simultaneously holding an IP address of 192.168.1.2 belonging to the LAN interface subnet. Do LAN firewall rules apply to it when, let's say, I go to the firmware page to check for updates?
Hope this is clear and concise, thanks for any help with this!
-
@moji first off - if you have any questions about your rules it would be very helpful to actually let us see them.. No offense but users say they have done X all the time, and what they really did was y^2+7x(16-x^3)=Q
-
why would you think routing happens in an AP? True devices on the same network don't talk to the router to talk to each other. But if your AP has 2 different ssids on 2 different vlans then yes they would need to flow through the router.
-
if you can talk to the gui, you could tell pfsense to update itself.. What restriction you might have set for some device via firewall rules has no effect on what a client can tell pfsense to do, like update itself.
-
-
@johnpoz Thanks for your kind reply! I'm new to this, excuse me.
So I get that the pfsense router itself gets internet access regardless of the network setup and firewalls.
I'd appreciate if you could comment with a few words on the following:- Does the Access Point (which I set up with ip address 192.168.1.2 and its gateway being the pfsense LAN address of 192.168.1.1) belong to the LAN Network or any other interface?
Thank you and have a good day!
-
@moji well would depend if your management IP is in a vlan or not
So for example my unifi AP all have their management IPs in what is my wlan network, this is an untagged network 192.168.2/24, but the AP has multiple ssids for other wireless networks, that are tagged vlans
example
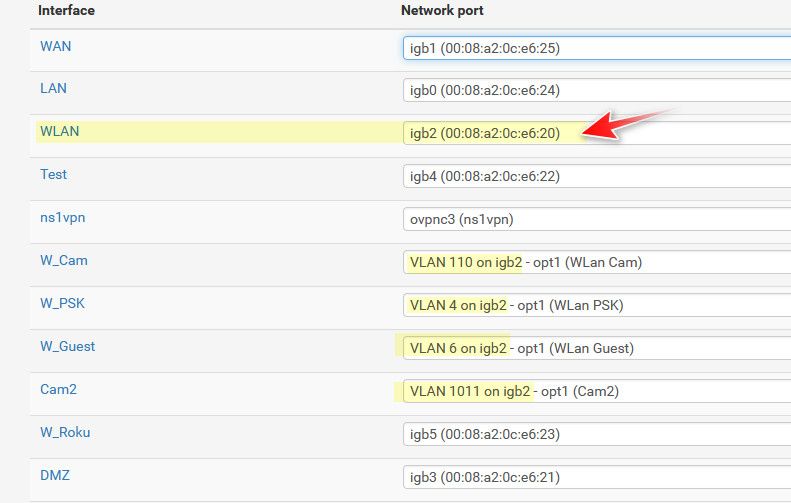
So the AP IP is on that native untagged network on my igb2 interface, while the vlans that are tagged that are tied to ssids that the AP provides are all still on that physical interface igb2, just they are tagged vlans.
The rules for those interfaces would all be per the interfaces in pfsense for the different vlans and the physical igb2 interface.
those vlan networks are all different L3 networks, example vlan 4 is 192.168.4/24 and vlan 6 is 192.168.6/24
My APs don't actually directly plug into pfsense, they are plugged into a switch with the appropriate vlans assigned to the port in the switch. Where the port connected to the AP on the switch has wlan untagged, and the others tagged.
-
@johnpoz Thanks a lot for the thorough answer!!!
-
hey there,
just as @johnpoz mentioned...in my setting I use the other way: my Ap (and switches) management IP is bound to a vlan. Works just as well...
I got lets say 5 VLANs, all carried on LAN. One of those networks/vlans is for "management purposes", so here I set my management IPs for all network related devices. So said management VLAN has PVID 3 (i.e. IP range 192.168.3.0/24 with my unifi APs having 192.168.3.5 and .6). So their gateway is pfsense's interface IP on that VLAN > 192.168.3.1.
Why? When I started with vlans I was reading here and there (being a noob with none whatsoever IT / tech background). I read somewhere (cisco forum I think) it is best practice to keep VLAN1 (untagged VLAN) free of productive traffic. That's why...not really necessary for my 1 person home network, but hey. It works just as well and it's not that much more effort. :)
I am with @johnpoz when it comes to connecting devices to a switch that is connected to pfsense's interface. -
@the-other yup depending on your AP you can sure run your management IP for this AP on a tagged vlan. Unifi at first did not allow for that and your management had to be on an untagged or native network.. They have since changed that, I just have no reason to change to a tagged vlan for my AP management..
I saw no reason or advantage to move to tagged. Now depending the network, maybe sure you want that to be a tagged vlan.
Just for sake of completeness, I also run a wireless SSID on that untagged wlan network, this is my trusted devices, and this wireless network uses eap-tls to auth.
-
@johnpoz hehe, I hear you...some devices cannot be configured like that and it was a pain with those unifis first as well...needed some kinde "trick" I cannot recall right now. :)
And yeah...if I had the need to build my network anew, I probably would put those management IPs in that untagged LAN/vlan1 as well. But (as you said): it works now so I just have no reason to change to an untagged VLAN for my AP management... ;)
Comes with age: I do not need to chase every "new" idea in my head and getting kinda lazy. So much other fun stuff to do, so little time. -
@the-other @johnpoz
Excuse me for the delay, I took the time to digest your super insightful, well-worded comments, looking stuff up along the way.
My AP is an old model that doesnt support management on a VLAN. So I can't give it an IP address that belongs to one of the tagged Vlans that it is providing an SSID for. So I gave the AP an IP address of 192.168.1.2 inside the 192.168.1.1/24 range.The Problem: I'm on my laptop with ip address 192.168.10.6 in the VLAN Home wifi SSID. I want to connect to the AP GUI management at 192.168.1.2. My Pfsense firewall rules allow All on the VLAN Home network. Somehow I can't reach the AP GUI. I can, from my VLAN Home wifi, access my gateway (which is 192.168.10.1- namely the Pfsense router GUI), but I cant access the AP at 192.168.1.2.
1- I suspect this is an issue with tagged and untagged traffic. My simple understanding tells me that my laptop on vlan Home wifi sends tagged packets which pass through the access point and make their way to the Pfsense successfully. Then the Pfsense needs to route this traffic to its destination- which is the AP GUI ip address. And given the AP ip address only does untagged traffic, and since the AP ip address also happens to belong to the network which is untagged (native) on that same LAN port on the Pfsense, then the packets do actually make their way to the AP GUI. But they don't. I'm missing something here, please correct me.
2- About setting up all interfaces including Management on Vlans, I get what you mean. So let's say after setting up all my Vlans, I create an Untagged Vlan native to that Trunk port to which the AP is being plugged. And that way any Untagged traffic generated intentionally or not, will simply be trapped in this fake Vlan instead of the default Vlan1 (plus I can add a DENY ALL firewall rule on this fake Vlan to trap that traffic there). Would this be enough to address your points on the matter?
Thanks a million, have a good day ahead!
-
@moji said in Question about inter-Vlan traffic and interface Concept:
1- I suspect this is an issue with tagged and untagged traffic
or its just that AP doesn't have a gateway.. To access a device on another network, that device has to know how to talk back to the source network.
Validate your AP gateway set to pfsense on the network its on. If you can not do that in this AP, then you could aways source nat your traffic so it looks like pfsense IP on that network is talking to it, and not the remote IP of your client your wanting to use to access the AP gui.
soho wifi router are known for this problem, where the native firmware doesn't allow you to set a gateway on the lan interface