How to best debug Wireguard
-
A little frustrated here. I've been running a road-warrior-configuration for wireguard from a Digital Ocean Droplet to a home pfSense Server running 2.7.2 for a couple of years. Everything just worked until a couple of days ago -- now the DO droplet can not connect:
[ +0.000053] wireguard: wg1: Sending handshake initiation to peer 3 (99.xx.xx.xxx:51821) [ +5.119909] wireguard: wg1: Handshake for peer 3 (99..xx.xx.xxx:51821) did not complete after 5 seconds, retrying (try 2)Within pfSense I've configured a dynamic endpoint with wireguard listening over port 51821.
I haven't changed anything from pfsense side which is frustrating.I've port scanned the pfsense from the remote computer using nmap:
# nmap -sU -p 58121 xx.xx.xxx Starting Nmap 7.80 ( https://nmap.org ) at 2024-09-07 14:28 CDT PORT STATE SERVICE 58121/udp open|filtered unknownI have a firewall rule on pfSense in regards to an open UDP port on WAN passing all traffic through 51821. I've setup logging on this rule.
I see nothing in the firewall logs when the remote tries to initiate the handshake from within pfsense. I'm really not sure what to try at this endpoint since I'm kind of stuck.
-
@kevdog The ports don't match (51821 versus 58121).
Ted -
@tedquade said in How to best debug Wireguard:
Reply
Hey thanks for catching my error -- however it was an error how I wrote the post -- not the configuration. Here is my updated "post correction":
# nmap -sU -p 51821 xx.xx.xx.xx Starting Nmap 7.80 ( https://nmap.org ) at 2024-09-07 14:47 CDT PORT STATE SERVICE 51821/udp open|filtered unknown -
@kevdog You can not expect an answer with nmap for a wireguard port.
-
@Bob-Dig Thanks -- I didn't know that in regards to port scanning WG ports. Are there any specific logs within pfSense I could use to see why the handshake isn't being established?
Looking through the firewall logs (after enabling all logging on port 51821) I see the following:
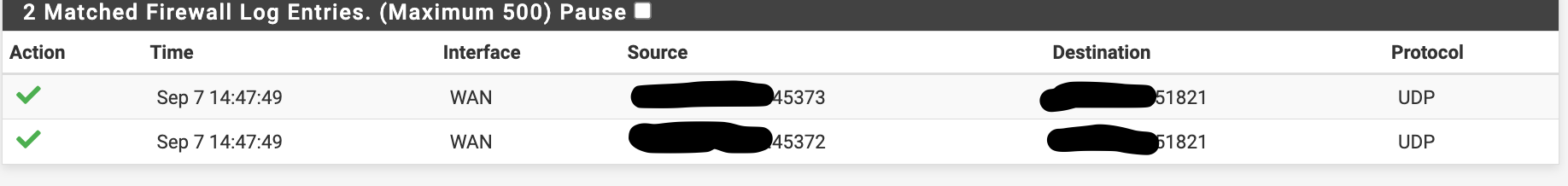
-
@kevdog said in How to best debug Wireguard:
I've been running a road-warrior-configuration for wireguard from a Digital Ocean Droplet to a home pfSense Server running 2.7.2 for a couple of years.
WireGuard hardly exists a couple of years for pfSense. Any why a road warrior setup?
There is no sudden problem with pfSense and WireGuard so your best chance might be to post a lot of screenshots what you did within pfSense. I don't know about Digital Ocean Droplet.
-
@Bob-Dig
Hey thanks for chiming in just really stumped why things exactly 2 days ago stopped working.
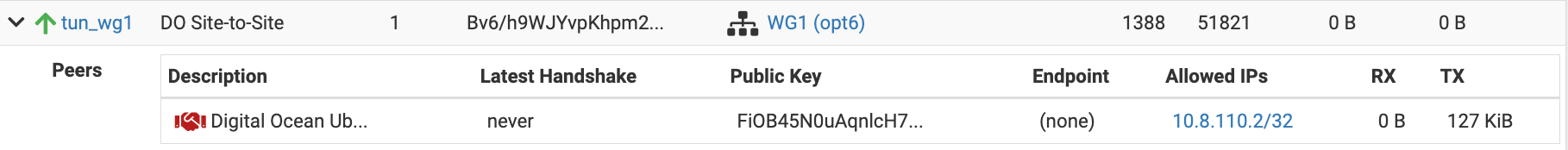
Hopefully this might help from the pfsense side:
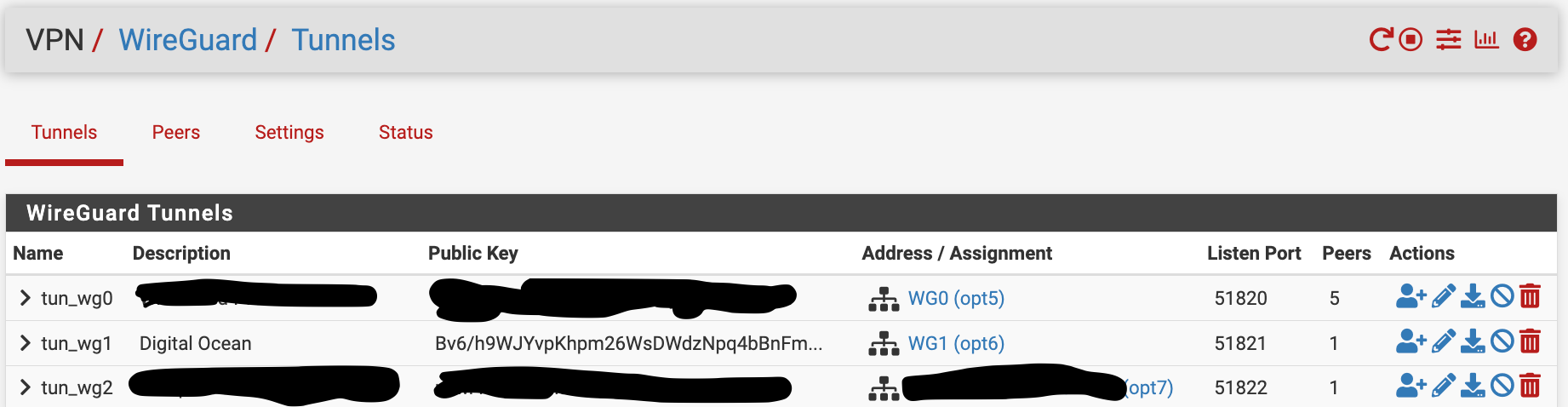
Wireguard Tunnels:
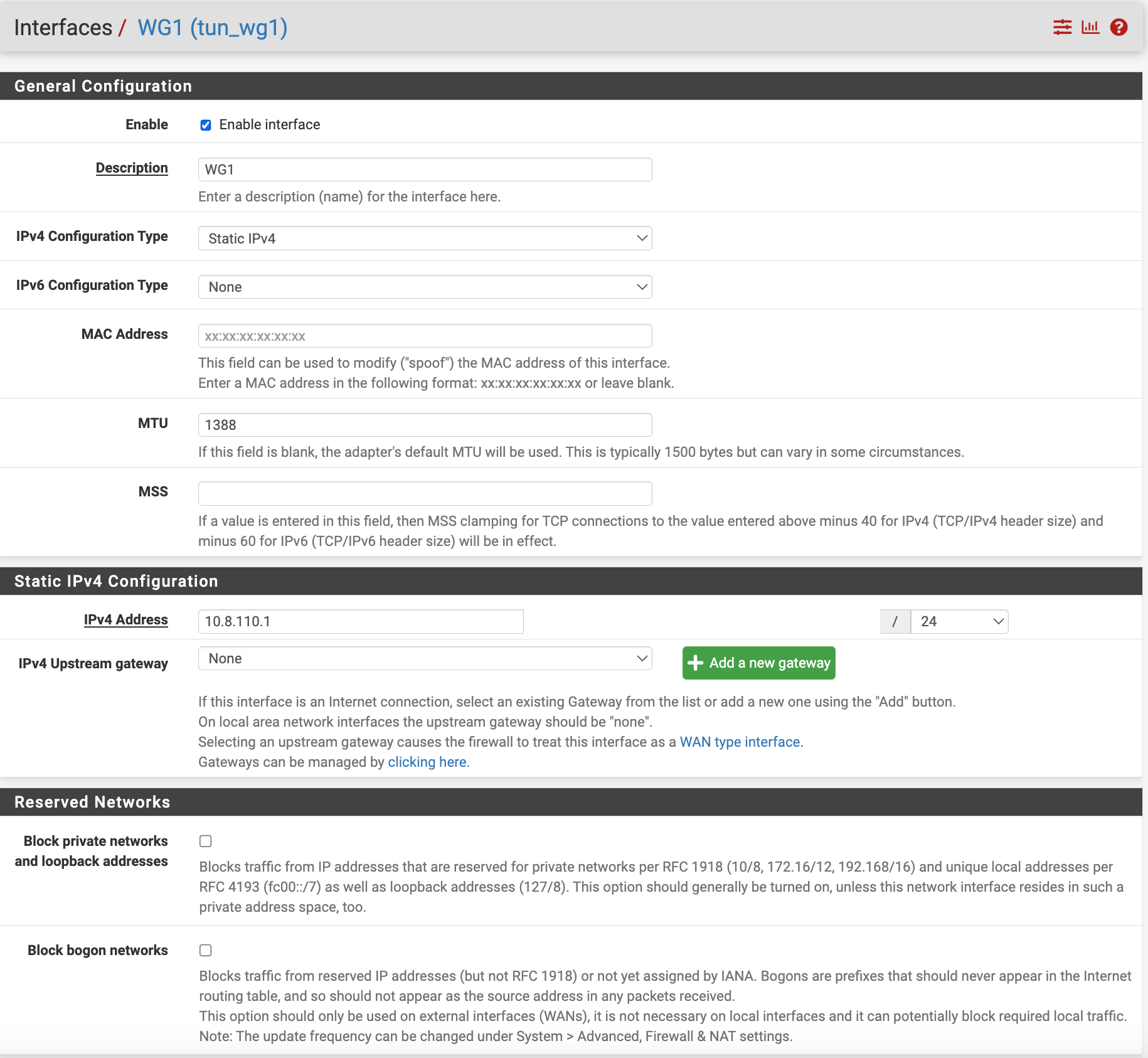
wg1 interface settings:
Firewall for the WG interface (wg1)
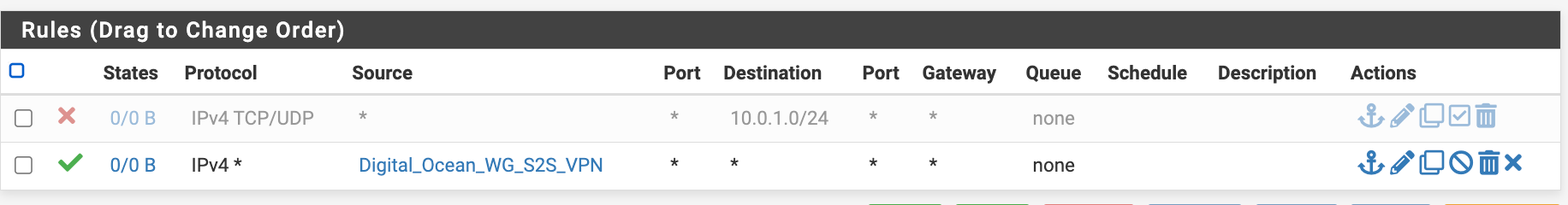
Digital_Ocean_WG_S2S_VPN has value of 10.8.110.0/24
Isn't there a log file somewhere where the WG service would log attempted connections? It seems based on firewall rules and firewall logs there would be traffick passed through to the listening process on 51821. Within the linux client on digital ocean its possible to do dynamic kernel logging. I think within pfSense the wireguard stuff isn't within the kernel but a user space utility?