Should i create an allow rule? Netbios
-
@Operations no that is just not used any more to be honest. its broadcast pfsense wouldn't do anything with it at all be it you allowed it or blocked it.. I really has zero use currently..
Really the only thing you could do is setup rules so that noise is not even logged by pfsense.. It sure isn't going to do anything with it be it you allowed it or not.. Just setup a rule so you don't see that noise.
I mean its possible that windows client are still sending out - but its useless nonsense.. Anything a windows AD would need to find would be dns these days not old school broadcast traffic.
Do you have some old school windows clients on your network? That suff hasn't been really needed since the old windows 3.11 days. Name resolution in windows since windows 2000 has been done via dns.
A router has never done anything with broadcast traffic anyway.. that its logged at all is just noise.
-
@johnpoz said in Should i create an allow rule? Netbios:
@Operations no that is just not used any more to be honest. its broadcast pfsense wouldn't do anything with it at all be it you allowed it or blocked it.. I really has zero use currently..
Really the only thing you could do is setup rules so that noise is not even logged by pfsense.. It sure isn't going to do anything with it be it you allowed it or not.. Just setup a rule so you don't see that noise.
I mean its possible that windows client are still sending out - but its useless nonsense.. Anything a windows AD would need to find would be dns these days not old school broadcast traffic.
Do you have some old school windows clients on your network? That suff hasn't been really needed since the old windows 3.11 days. Name resolution in windows since windows 2000 has been done via dns.
A router has never done anything with broadcast traffic anyway.. that its logged at all is just noise.
No old clients. All Windows 10/11 and server 2019/2022.
How do i create a rule to not show these blocks in the log?
Create a block rule and turn the log option check box off? -
@Operations said in Should i create an allow rule? Netbios:
Create a block rule and turn the log option check box off?
exactly - create a rule that either allows it or doesn't log, or sure block and doesn't log - as said pfsense sure isn't going to answer that broadcast on its own, nor would it do anything with it so be it you allow or block is up to you.. you just need a rule that doesn't log that traffic before it gets to your default deny that is logging it.
But normally your any any rule if not logging would allow that traffic. This is the default lan rule. Do you mind posting your rule set, and an actual firewall hit that is logged to see why its being logged in the first place.
edit: for example
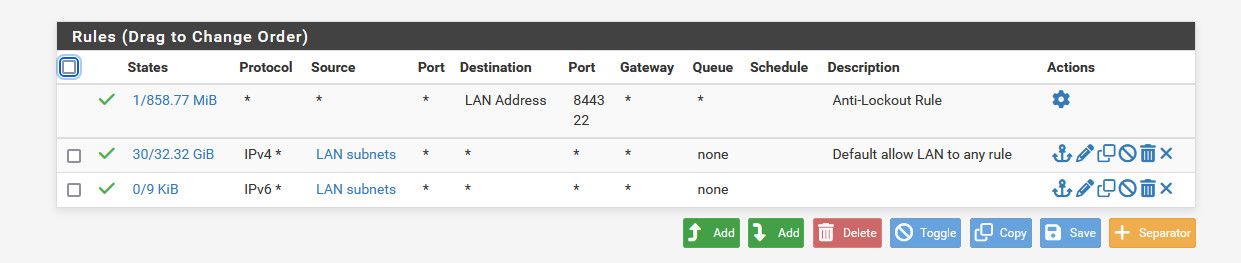
The default rules of lan to any would not log this traffic
172.16.20.5 => 172.16.20.255:138
because that source IP 172.16.20.5 would be your lan and any would allow this 172.16.20.255:138, are you maybe seeing such traffic on an interface that is not your lan?
So unless you turned on logging for this rule, traffic to the broadcast address .255 would be allowed and not logged.. Unless you setup logging on you rule, or turned on the logging of allow..
Posting up the rules you have on the interface your seeing this log, and a firewall hit showing what rule logged it - I am assuming the default deny is logging it? Would be helpful in best way to make sure you not logging that, if you don't want to see it in your logs.
-
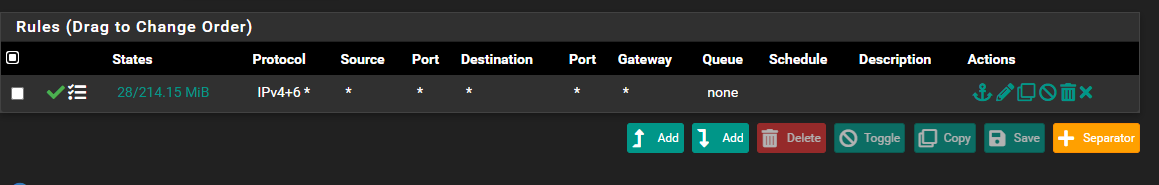
@johnpoz The first one is the Server vLAN, where the DC's are (172.16.10.0/24):
Second screenshot is the DMZ LAN. Where i am seeing the block we are talking about (172.16.20.0/24):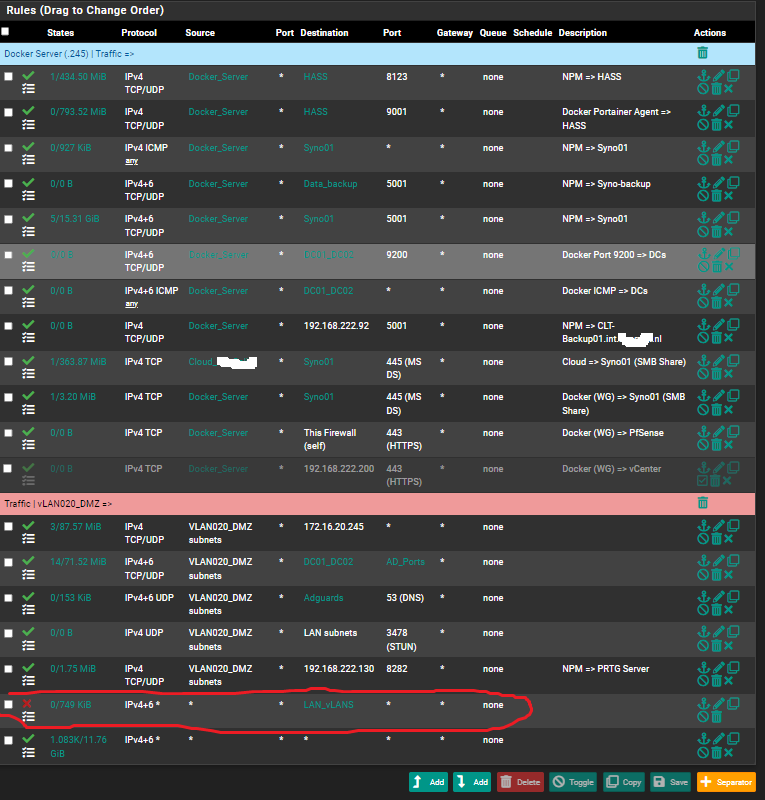
This last rules set is my default LAN (192.168.222.0/24):
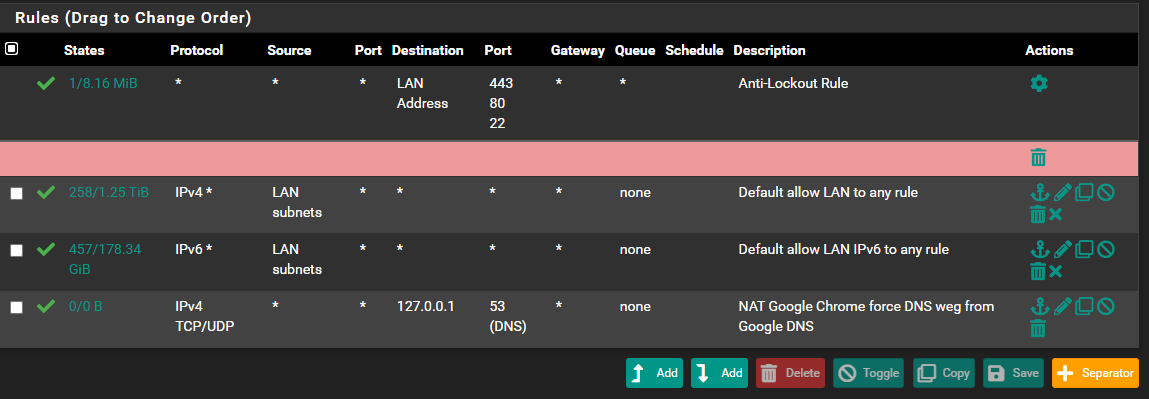
This is the fw log block:
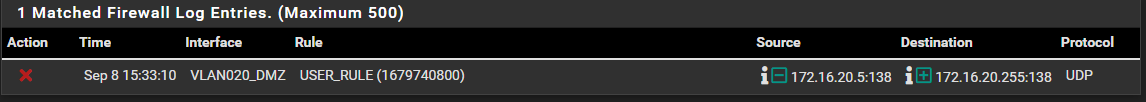
I have made a red circle round the user rule which is mentioned in the block.
-
@Operations so not sure what exactly is in your lan_vlans alias, but sure if that destination broadcast is not allowed by that rule and you have it logging then yup you would see that logged.
To not log it just put in a rule right above that rule that blocks say any traffic to port 138 and doesn't log.
example from my rules
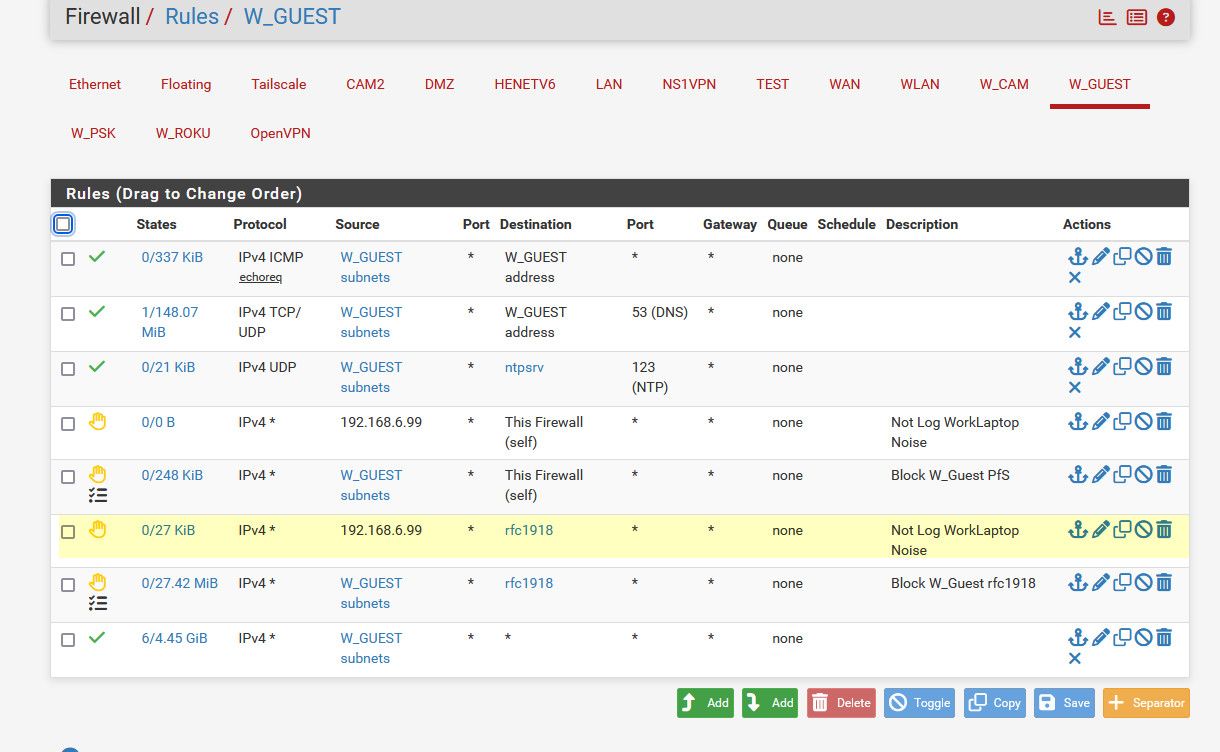
My work laptop which gets that 6.99 IP from dhcp reservation on my guest network.. Like to send out a bit of noise when not on the work vpn - you know it looking for work stuff that it can't get to anyway when its not connected to its vpn.. So I just put a rule above the other rfc1918 rule that I do want to see if other devices on my guest network are trying to talk to stuff I didn't allow it to talk too.
-
@johnpoz said in Should i create an allow rule? Netbios:
@Operations so not sure what exactly is in your lan_vlans alias, but sure if that destination broadcast is not allowed by that rule and you have it logging then yup you would see that logged.
To not log it just put in a rule right above that rule that blocks say any traffic to port 138 and doesn't log.
Lan_vlans alias is RFC1918. I should have mentioned that. I have log turn ON to check / make sure i am not blocking things i shouldnt block.
-
@Operations see my edit, I posted an example from my rules where I don't want to log a specific IPs noise.. You could for sure just make such a rule for only port 138 if that is the only noise you don't want to see.
-
@johnpoz said in Should i create an allow rule? Netbios:
@Operations see my edit, I posted an example from my rules where I don't want to log a specific IPs noise.. You could for sure just make such a rule for only port 138 if that is the only noise you don't want to see.
Yes i have seen it, thanks. Why do you reject instead of block? Should i been doing reject instead of block?
-
@Operations reject in local can reduce retrans.. Since your telling the client right away hey you ain't getting there.. No reason to wait and retrans, and then retrans again again before giving up..
So locally a reject vs just block (drop it) can be handy - but you would almost never setup say your wan to reject.
But if the block is on a local network and local traffic from something on my network, yeah I like reject vs just block.
-
@johnpoz said in Should i create an allow rule? Netbios:
@Operations reject in local can reduce retrans.. Since your telling the client right away hey you ain't getting there.. No reason to wait and retrans, and then retrans again again before giving up..
So locally a reject vs just block (drop it) can be handy - but you would almost never setup say your wan to reject.
But if the block is on a local network and local traffic from something on my network, yeah I like reject vs just block.
Ok. Thanks for educating me.
I am seeing the same block (same IPs) with port 137. This is the same right? Also old stuff and just create non logging rule right? -
@Operations yeah pfsense not going to do anything with broadcast traffic one way or the other. If you don't want such traffic in your logs then yeah just create rule to not log it.