isolated VLAN Internet access
-
Hi all. I am new to PFSense and while I have been learning a lot, despite reading a lot of posts on the forum, I still am not solving what should be an easy problem.
I have set up and have the following working: blockerng, snort, and avahi.
I have LAN, VLAN1 and VLAN2.
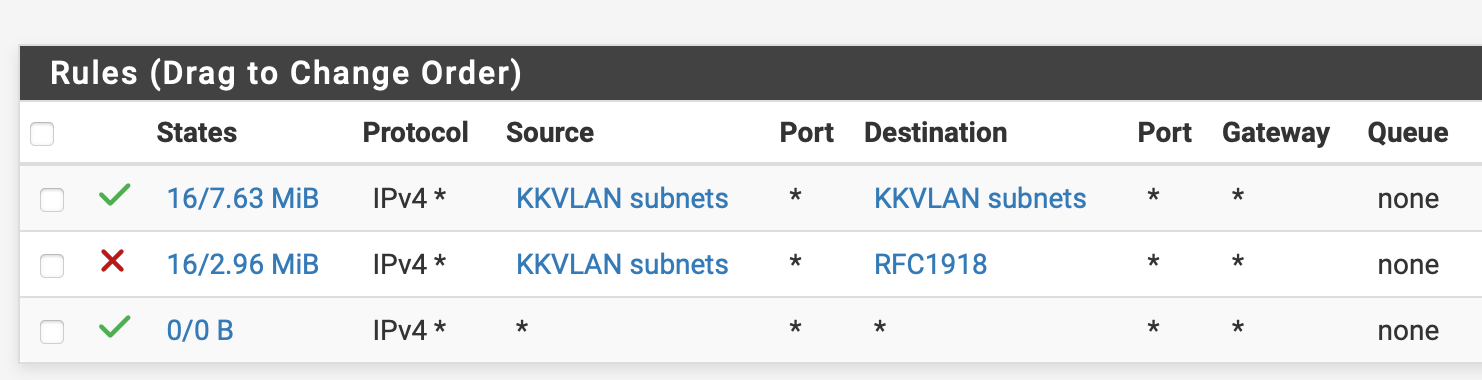
The vlans have internet access with only vlan to everywhere rule. IPV4/VLAN1 address///*
If I replace the allow vlan1 to anywhere rule with the following in order to block vlan to vlan and lan communications I lose internet access.
allow IPV4/VLAN1 address//VLAN1 address/
allow IPV4/VLAN1 address//!private_networks/The DHC server shows that each lan/vlan has a dns server at .1 address of its subnet so I am not sure what is wrong.
I tried IPV4/TCP-UDP/vlan1/*/127.0.0.1[DNS server address according to dashboard]/DNS which I read on a post but that did not work.
Any help is appreciated.
-
If you post pictures of the rules, it is easier to read.
What is in the alias private_networks? Is this a listing of the RFC1918 addresses? -
@AndyRH thanks for your response. Here are images. I changed the local network definition name but otherwise the same.
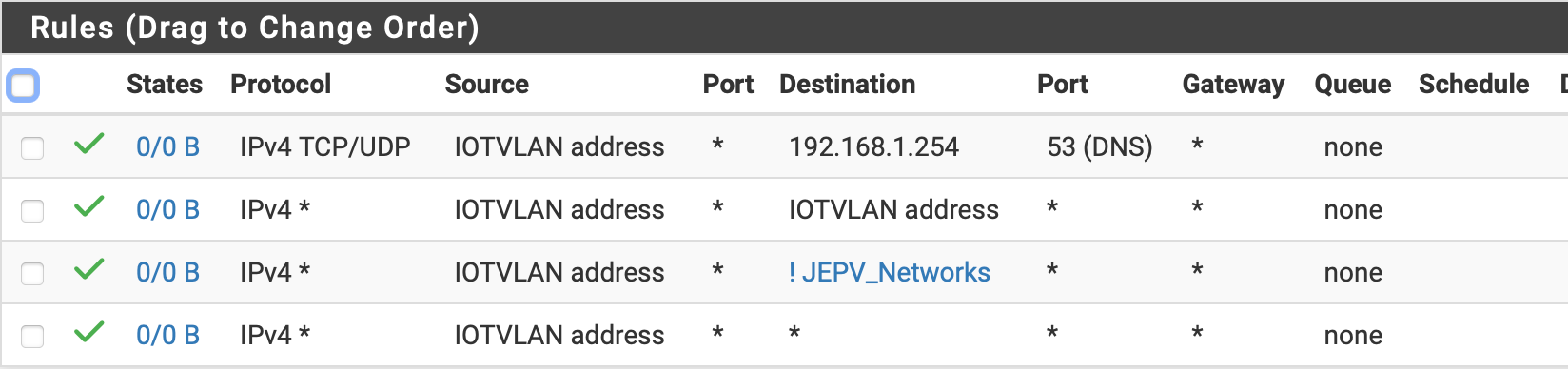
That last rule should not be necessary if the next to the last rule is doing it job. If I get rid of the next to the last rule I get internet access.
-
Your allow any rule should be subnet not address.
The 3rd rule says no to the alias, it does not say yes to the internet, as it should be. Also, I think it should be subnet, not address.
The 4th rule is needed.
Others will have better help and possibly correct me. -
Actually all of them should be subnet, not address as source.
The XXX address is just the interface address itself, meaning in your case, 192.168.1.254. Nothing else. The XXX subnet would be all addresses in that subnet.
Allowing IOTVLAN Address to 192.168.1.254 is allowing it to itself. Useless.
Change the source to IOTVLAN subnet on all rules.Your second rule does the same as the first rule, plus allows anything else to the interface. So delete the second rule. The first rule is also not needed to block access to other subnets, the allow all at the bottom will allow DNS if it's not blocked before it.
The 3rd rule would be better to block the IOTVLAN subnet to "ALIAS" and make the ALIAS all rfc1918 addresses. That way if you add another subnet with a 10.0.1.0/24 network, it would also already be blocked by the alias. No need to do any editing for the new network.
The 4th rule will then allow anything else not already blocked, including internet access.So if all you want to do is block access to other local subnets, but still allow all the the internet, you only need 2 rules. Block rfc1918, and allow all.
-
-
-
@Stingo Sorry, I mis-spoke in the previous post. You'll need to add the allow DNS Before the block rule. The RFC Alias includes the interface address on each subnet, so that gets blocked also.
What's the point of the first rule? -
@Jarhead said in isolated VLAN Internet access:
What's the point of the first rule?
While it is not good, it should allow for local DNS, don't you think? It is clearly doing something.

-
How's your setup?
Pfsense and modem?
Pfsense behind another router?
Double NAT? -
@Jarhead what should the DNS rule look like? I want to be sure I get it right.
The purpose of the first rule is to allow intra vlan communication since the second rule is blocking all the subnets including subnet that the VLAN is on. The first tule allows instructions within the subnet.
My old rule created an alias for the lan and vlan subnets and then gave access to everything but not the vlan subnets. (with the inverted button I understood that !private_nets = let all through except private nets.). That was supposed to replace the all open rule but whenever it was active I lost internet on the vlan.
@the-other nothing fancy. Just PFsense router and TPLink switch. Most of the vlan clients are wireless over a TPlink AP. The vlan works fine until I block the other subnets and the lan in particular. It is almost as if the subnet is getting DNS from the lan. I thought DNS was supposed to be connected through 192.168.20.1 but I obviously am still too uninformed on the mysteries of networking. :-)
-
@Stingo said in isolated VLAN Internet access:
The purpose of the first rule is to allow intra vlan communication
pfsense is not involved in communication between devices on the same network.
That rule should really allow clients to access dns on pfsense IP on that vlan though - but if your clients are pointing to a IP for dns that is on another network of pfsense your block rfc1918 rule would prevent that.
Here is example locked down rules for an interface that might be helpful
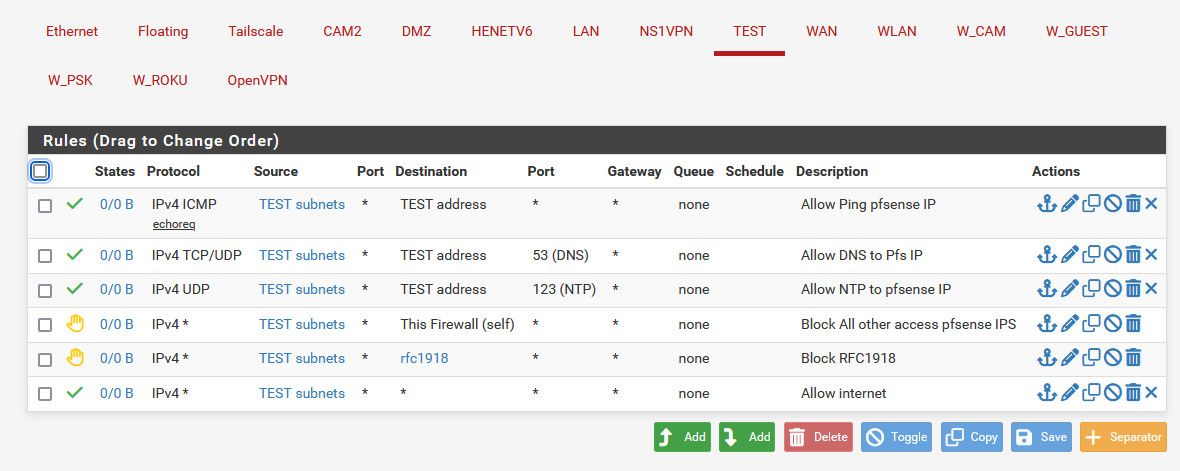
The rules description say what the rule does.
The block rule there to pfsense IPs "this firewall" prevents say access to the pfsense web gui on the public wan IP, which would be allowed by the last rule that is any any to allow internet access.
-
@johnpoz This is extremely helpful. Thank you very much.
I understood that if I tell the firewall on VLAN20 "dont allow any calls to these private subnets" and the private subnets include the VLAN20 subnet then I need a rule allowing the VLAN20 subnet to the the VLAN20 subnet first. Then again I am just trying to dig through a ton of of stuff online to get to the gold. :-)
Netgate has good notes but they could be better.
Thanks again.
-
@Stingo yeah if you block all rfc1918 it would block access to pfsense IP address that is rfc1918.. So yeah you need rule(s) above the block rfc1918 rule that allows access to pfsense address for say dns.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.. So while yes your rule there on top should allow access to pfsense IP on that vlan.. It a bit overboard for allowing access to 1 IP, the rule should just be to pfsense address.
But your saying that rule isn't even working? Which would make no sense unless your clients were talking to some other IP on pfsense or another network for dns?
-
@johnpoz the rules that you shared above worked fantastically. I think the problem was in the rules that I did not have for NTP or DNS. I hope you know you probably helped prevent a divorce or a murder since I put my wife on a separate vlan so she had lost internet connection. She was getting damn scary.
One question since I am trying to learn. Why the ping rule? Why does the vlan need to ping echoreq the vlan address?
-
@Stingo its there for ability to test.. if wanted to actually make sure you could talk to pfsense.. Not something you need, but I like to be able to validate I can actually talk to my router/dns etc..
-
@johnpoz good idea. I think I'll keep the rule. Thanks again. Most of the fun so far has been learning with PFSense. I just wish there were clearer guides out there.