Automatic IP blocking
-
Ok so we created a honeypot that takes logs IPs, we then take that data and parse it out do some voodoo magic, and now we have a output of if a new IP hits the honeypot, we have their IP in n8n to then do what ever.
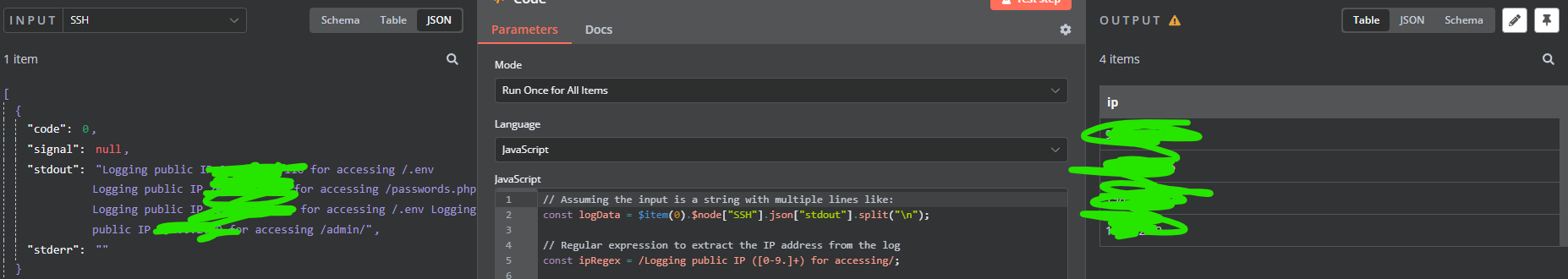
I was thinking of possible doing http posts to our firewall on a a allias list called "blocklist" and to add new IPs as they come in, and applying changes via a cronjob all automated
however was thinking maybe there is a easier way, does anyone have a easy way?
(also yes we are aware of pfblocker we already have it installed, however, can never have enough security) -
@bubbaboi so you put up a honeypot I take it on a port you don't actually host real stuff on.. So you can find out who hits it so you can block them.. Block them from accessing what?
Are you serving up say stuff on a different port, and you want to block anything that hits your honeypot on port X from accessing your real services on port Y?
Just trying to understand the point, I have run honeypots in the past, it can interesting to see what they do once they get on, etc.
There are loads of lists that already list IPs hitting honeypots, are you wanting to contribute to those sorts of lists? Seems like just reinventing the wheel here.. Especially if your not actually hosting any services for real and just have your honeypot services open.
-
@johnpoz yes, scanners and attackers will hit this server, in a matter of a day of it being up, about 100 ips have hit it, most of which scanners, some of which testing actually exploits, all of which are not on any block lists, yet. But yes it logs their IP, and then we will block them on the wan firewall rules, just a global block IE.
-
@bubbaboi all IPs are block out of the box anyway.. So unless your hosting services on other ports collecting the IPs of the scanners on the internet which will be in the 100's of thousands most likely.. Not sure what is the point.
And known scanners are listed, I block a few of them myself, etc.. and when I notice a new one I look for a list of their IPs and block them, etc.. But I actually host services, that I don't want the scanners to see.
But unless you want to contribute to a list, or service that provides such list.. Which many of them already have the methods providing your logs to them.. I am not really seeing the point to this.. Unless you are actually hosting services on other ports, and want to block some IP that hits you on say ssh, from in the future talking to your service on 443, etc.
-
@johnpoz yes we do actually host services, we have many services, and yes we have 3 things setup
22 ssh honetpot
8443/80/8080 http/https honeypot
443 honeypot with nginx thats if they hit a certain DNS record -
@bubbaboi If you can put your IPs in a file you can pull them with a URL (table) alias.
https://docs.netgate.com/pfsense/en/latest/firewall/aliases.html#url-aliasesOr use pfBlockerNG to pull a feed.
-
@SteveITS Ah yup, completely forgot about that. Was also looking at using the new API, but its on the next version, so will either be updating, or using that, one of the 2, would prefer to use the API, but would rather not come ruin a weekend night updating firewalls.