OpenVPN Peer to Peer ( SSL/TLS ) no ping from siteServer to siteClient
-
Hi everyone,
I'm trying to setup my first Peer to Peer ( SSL/TLS ) to replace all my pre-shared keys tunnels.
I followed this tutorial
[https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html](link url)And the connection is established. After trying a couple things, I'm able to reach the siteServer from the siteClient. But the opposited doesn't work. And I don't understand why.
siteClient:
192.168.11.0
No Tunnel settingssiteServer
192.168.18.0
ipv4 tunnel network 10.3.101.0/24
ipv4 local network 192.168.18.0/24
ipv4 remote network 192.168.11.0/24clientOverride
ipv4 tunnel network 10.3.101.0/24
ipv4 remote network 192.168.11.0/24--
Rules on both sites
OpenVPN
ipv4* * * * * *WAN Rules
ipv4 UDP IP_siteClient port* ThisFirewall port 1196Same rule on the siteServer
ipv4 UDP IP_siteServer port* ThisFirewall port 1196--
route on the siteClient
10.3.101.0/24 link#9 U 10 1500 ovpnc2
10.3.101.2 link#5 UHS 11 16384 lo0
192.168.18.0/24 10.3.101.1 UGS 12 1500 ovpnc2route on the siteServer
10.3.101.0/24 link#10 U 11 1500 ovpns3
10.3.101.1 link#5 UHS 12 16384 lo0
192.168.11.0/24 10.3.101.2 UGS 13 1500 ovpns3--
Diagnostic
Ping is working on the siteServer on
10.3.101.1
10.3.101.2Ping is not working on the siteServer on
192.168.11.1Ping is working on the siteClient on
192.168.18.1- other devices on the network
Any idea on how to fix this ?
I got plenty of Peer to peer VPN running and I was always able to fix it, but here I'm struggling.Also, the siteServer is already running a Peer to peer (shared key) OpenVPN tunnel, and the connection is working fine on both sides. The difference I found on the siteServer routes is, there is this route for the shared key VPN:
192.168.40.2 link#9 UH 8 1500 ovpns2So there should also be a similar route for destination 10.3.101.2 pointing to ovpns3 but there isn't. Is that normal ? If not, how to fix it ?
What's weird is that on the siteClient, there is also a route missing for 10.3.101.1 but it works anyway. There is only a route for 10.3.101.2
Best regards
-
@info385 said in OpenVPN Peer to Peer ( SSL/TLS ) no ping from siteServer to siteClient:
clientOverride
ipv4 tunnel network 10.3.101.0/24The clients tunnel network must not be the tunnel network address, but a certain available IP out of the tunnel subnet above of 2.
If it still doesn't work, enhance the server log level to 4, reconnect and check in the log if the CSO was applied properly.
-
Hello viragoman,
Thanks for replying.
I've change the ipv4 tunnel network to 10.3.105.0/24
It doesn't work either, same issue.Best regards
-
@info385
No, not this way.Assuming the severs tunnel network is 10.3.101.0/24, in the CSO state for instance 10.3.101.100/24.
This presumes, that the server uses subnet topology, which is the default mode. -
I confirm the topology settings: Subnet.
I changed the CSO tunnel network to 10.3.101.100/24
And I can confirm that it is applied, this route is on the client:192.168.18.0/24 10.3.101.1 UGS 12 1500 ovpnc2
But I still have no ping from 18.0 to 11.0 network.
I don't understand why I'm struggling as I run a couple Peer to Peer ( Shared Key ) and it's working fine. -
@info385 said in OpenVPN Peer to Peer ( SSL/TLS ) no ping from siteServer to siteClient:
I changed the CSO tunnel network to 10.3.101.100/24
And I can confirm that it is applied, this route is on the client:192.168.18.0/24 10.3.101.1 UGS 12 1500 ovpnc2
This route has nothing to do with the CSO, however. It is pushed from the server due to the "remote networks" settings.
As mentioned above, this can only be verified in the server log, after you've set a proper log level.
Can you post the server log, please?
But I still have no ping from 18.0 to 11.0 network.
Consider that the access can also be blocked by the destination device.
You can verify with packet capture on the client side if the packets are transmitted properly.I don't understand why I'm struggling as I run a couple Peer to Peer ( Shared Key ) and it's working fine.
Shared key mode works somewhat different.
If you don't need DCO you can use a /30 tunnel network, then the CSO stuff would not be necessary.
-
How do I change the log level ?
-
@info385
VPN > OpenVPN > Servers > Edit > Verbosity level = 4 -
@info385 I just solved this problem. While the wizard sets things up correctly at the server end, you must manually add an OpenVPN firewall rule at the client to allow reverse traffic into the client network
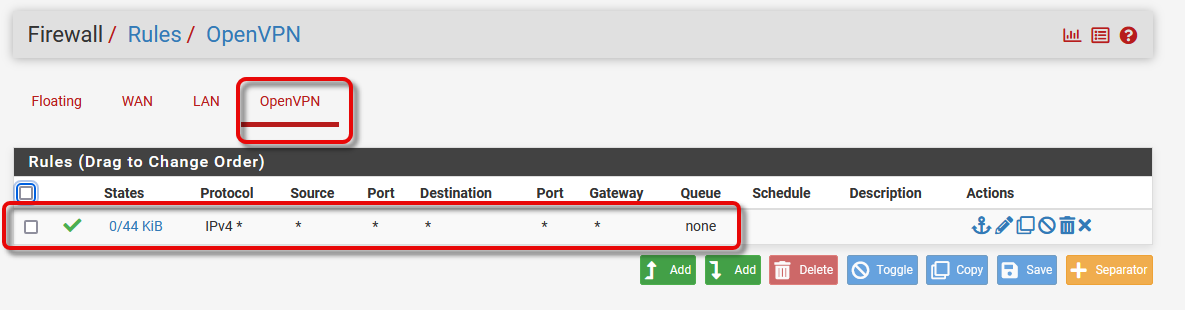
Now if I could just get DNS to work.... :-)
-
Thank you all for your help.
The OpenVPN rule was already created.
I started a packet capture on the client on ovpnc2 and initiated a ping from the server.
It shows nothing.I tried the opposite way, packet capture on the server, ping on the client, the log shows the incoming ICMP echo request from the tunnel.
Here is the log:
Sep 24 23:52:43 openvpn 51546 MANAGEMENT: Client disconnected
Sep 24 23:52:45 openvpn 51546 event_wait : Interrupted system call (fd=-1,code=4)
Sep 24 23:52:45 openvpn 51546 SENT CONTROL [vpn_ssl_remote]: 'RESTART' (status=1)
Sep 24 23:52:46 openvpn 51546 MULTI: Connection attempt from 18.48.13.121:4264 ignored while server is shutting down
Sep 24 23:52:47 openvpn 51546 TCP/UDP: Closing socket
Sep 24 23:52:47 openvpn 51546 /sbin/route delete -net 192.168.11.0 10.3.101.2 255.255.255.0
Sep 24 23:52:47 openvpn 51546 Closing TUN/TAP interface
Sep 24 23:52:47 openvpn 51546 /sbin/ifconfig ovpns3 10.3.101.1 -alias
Sep 24 23:52:47 openvpn 51546 /usr/local/sbin/ovpn-linkdown ovpns3 1500 0 10.3.101.1 255.255.255.0 init
Sep 24 23:52:47 openvpn 79241 Flushing states on OpenVPN interface ovpns3 (Link Down)
Sep 24 23:52:47 openvpn 51546 SIGTERM[hard,] received, process exiting
Sep 24 23:52:48 openvpn 90203 Note: --data-cipher-fallback with cipher 'AES-256-CBC' disables data channel offload.
Sep 24 23:52:48 openvpn 90203 Current Parameter Settings:
Sep 24 23:52:48 openvpn 90203 config = '/var/etc/openvpn/server3/config.ovpn'
Sep 24 23:52:48 openvpn 90203 mode = 1
Sep 24 23:52:48 openvpn 90203 show_ciphers = DISABLED
Sep 24 23:52:48 openvpn 90203 show_digests = DISABLED
Sep 24 23:52:48 openvpn 90203 show_engines = DISABLED
Sep 24 23:52:48 openvpn 90203 genkey = DISABLED
Sep 24 23:52:48 openvpn 90203 genkey_filename = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 key_pass_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 show_tls_ciphers = DISABLED
Sep 24 23:52:48 openvpn 90203 connect_retry_max = 0
Sep 24 23:52:48 openvpn 90203 Connection profiles [0]:
Sep 24 23:52:48 openvpn 90203 proto = udp4
Sep 24 23:52:48 openvpn 90203 local = '172.31.255.6'
Sep 24 23:52:48 openvpn 90203 local_port = '1197'
Sep 24 23:52:48 openvpn 90203 remote = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 remote_port = '1194'
Sep 24 23:52:48 openvpn 90203 remote_float = DISABLED
Sep 24 23:52:48 openvpn 90203 bind_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 bind_local = ENABLED
Sep 24 23:52:48 openvpn 90203 bind_ipv6_only = DISABLED
Sep 24 23:52:48 openvpn 90203 connect_retry_seconds = 1
Sep 24 23:52:48 openvpn 90203 connect_timeout = 120
Sep 24 23:52:48 openvpn 90203 socks_proxy_server = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 socks_proxy_port = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 tun_mtu = 1500
Sep 24 23:52:48 openvpn 90203 tun_mtu_defined = ENABLED
Sep 24 23:52:48 openvpn 90203 link_mtu = 1500
Sep 24 23:52:48 openvpn 90203 link_mtu_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 tun_mtu_extra = 0
Sep 24 23:52:48 openvpn 90203 tun_mtu_extra_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 tls_mtu = 1250
Sep 24 23:52:48 openvpn 90203 mtu_discover_type = -1
Sep 24 23:52:48 openvpn 90203 fragment = 0
Sep 24 23:52:48 openvpn 90203 mssfix = 1492
Sep 24 23:52:48 openvpn 90203 mssfix_encap = ENABLED
Sep 24 23:52:48 openvpn 90203 mssfix_fixed = DISABLED
Sep 24 23:52:48 openvpn 90203 explicit_exit_notification = 1
Sep 24 23:52:48 openvpn 90203 tls_auth_file = '[INLINE]'
Sep 24 23:52:48 openvpn 90203 key_direction = 0
Sep 24 23:52:48 openvpn 90203 tls_crypt_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 tls_crypt_v2_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 Connection profiles END
Sep 24 23:52:48 openvpn 90203 remote_random = DISABLED
Sep 24 23:52:48 openvpn 90203 ipchange = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 dev = 'ovpns3'
Sep 24 23:52:48 openvpn 90203 dev_type = 'tun'
Sep 24 23:52:48 openvpn 90203 dev_node = '/dev/tun3'
Sep 24 23:52:48 openvpn 90203 tuntap_options.disable_dco = ENABLED
Sep 24 23:52:48 openvpn 90203 lladdr = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 topology = 3
Sep 24 23:52:48 openvpn 90203 ifconfig_local = '10.3.101.1'
Sep 24 23:52:48 openvpn 90203 ifconfig_remote_netmask = '255.255.255.0'
Sep 24 23:52:48 openvpn 90203 ifconfig_noexec = DISABLED
Sep 24 23:52:48 openvpn 90203 ifconfig_nowarn = DISABLED
Sep 24 23:52:48 openvpn 90203 ifconfig_ipv6_local = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 ifconfig_ipv6_netbits = 0
Sep 24 23:52:48 openvpn 90203 ifconfig_ipv6_remote = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 shaper = 0
Sep 24 23:52:48 openvpn 90203 mtu_test = 0
Sep 24 23:52:48 openvpn 90203 mlock = DISABLED
Sep 24 23:52:48 openvpn 90203 keepalive_ping = 10
Sep 24 23:52:48 openvpn 90203 keepalive_timeout = 60
Sep 24 23:52:48 openvpn 90203 inactivity_timeout = 300
Sep 24 23:52:48 openvpn 90203 session_timeout = 0
Sep 24 23:52:48 openvpn 90203 inactivity_minimum_bytes = 0
Sep 24 23:52:48 openvpn 90203 ping_send_timeout = 10
Sep 24 23:52:48 openvpn 90203 ping_rec_timeout = 120
Sep 24 23:52:48 openvpn 90203 ping_rec_timeout_action = 2
Sep 24 23:52:48 openvpn 90203 ping_timer_remote = ENABLED
Sep 24 23:52:48 openvpn 90203 remap_sigusr1 = 0
Sep 24 23:52:48 openvpn 90203 persist_tun = ENABLED
Sep 24 23:52:48 openvpn 90203 persist_local_ip = DISABLED
Sep 24 23:52:48 openvpn 90203 persist_remote_ip = DISABLED
Sep 24 23:52:48 openvpn 90203 persist_key = ENABLED
Sep 24 23:52:48 openvpn 90203 passtos = DISABLED
Sep 24 23:52:48 openvpn 90203 resolve_retry_seconds = 1000000000
Sep 24 23:52:48 openvpn 90203 resolve_in_advance = DISABLED
Sep 24 23:52:48 openvpn 90203 username = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 groupname = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 chroot_dir = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 cd_dir = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 writepid = '/var/run/openvpn_server3.pid'
Sep 24 23:52:48 openvpn 90203 up_script = '/usr/local/sbin/ovpn-linkup'
Sep 24 23:52:48 openvpn 90203 down_script = '/usr/local/sbin/ovpn-linkdown'
Sep 24 23:52:48 openvpn 90203 down_pre = DISABLED
Sep 24 23:52:48 openvpn 90203 up_restart = DISABLED
Sep 24 23:52:48 openvpn 90203 up_delay = DISABLED
Sep 24 23:52:48 openvpn 90203 daemon = ENABLED
Sep 24 23:52:48 openvpn 90203 log = DISABLED
Sep 24 23:52:48 openvpn 90203 suppress_timestamps = DISABLED
Sep 24 23:52:48 openvpn 90203 machine_readable_output = DISABLED
Sep 24 23:52:48 openvpn 90203 nice = 0
Sep 24 23:52:48 openvpn 90203 verbosity = 4
Sep 24 23:52:48 openvpn 90203 mute = 0
Sep 24 23:52:48 openvpn 90203 gremlin = 0
Sep 24 23:52:48 openvpn 90203 status_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 status_file_version = 1
Sep 24 23:52:48 openvpn 90203 status_file_update_freq = 60
Sep 24 23:52:48 openvpn 90203 occ = ENABLED
Sep 24 23:52:48 openvpn 90203 rcvbuf = 0
Sep 24 23:52:48 openvpn 90203 sndbuf = 0
Sep 24 23:52:48 openvpn 90203 sockflags = 0
Sep 24 23:52:48 openvpn 90203 fast_io = DISABLED
Sep 24 23:52:48 openvpn 90203 comp.alg = 0
Sep 24 23:52:48 openvpn 90203 comp.flags = 24
Sep 24 23:52:48 openvpn 90203 route_script = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 route_default_gateway = '10.3.101.2'
Sep 24 23:52:48 openvpn 90203 route_default_metric = 0
Sep 24 23:52:48 openvpn 90203 route_noexec = DISABLED
Sep 24 23:52:48 openvpn 90203 route_delay = 0
Sep 24 23:52:48 openvpn 90203 route_delay_window = 30
Sep 24 23:52:48 openvpn 90203 route_delay_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 route_gateway_via_dhcp = DISABLED
Sep 24 23:52:48 openvpn 90203 management_addr = '/var/etc/openvpn/server3/sock'
Sep 24 23:52:48 openvpn 90203 management_user_pass = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 management_log_history_cache = 250
Sep 24 23:52:48 openvpn 90203 management_client_user = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 management_flags = 256
Sep 24 23:52:48 openvpn 90203 key_direction = 0
Sep 24 23:52:48 openvpn 90203 ciphername = 'AES-256-CBC'
Sep 24 23:52:48 openvpn 90203 authname = 'SHA256'
Sep 24 23:52:48 openvpn 90203 replay = ENABLED
Sep 24 23:52:48 openvpn 90203 mute_replay_warnings = DISABLED
Sep 24 23:52:48 openvpn 90203 replay_time = 15
Sep 24 23:52:48 openvpn 90203 test_crypto = DISABLED
Sep 24 23:52:48 openvpn 90203 tls_client = DISABLED
Sep 24 23:52:48 openvpn 90203 ca_path = '/var/etc/openvpn/server3/ca'
Sep 24 23:52:48 openvpn 90203 dh_file = '/etc/dh-parameters.2048'
Sep 24 23:52:48 openvpn 90203 extra_certs_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 pkcs12_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 cipher_list = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 tls_cert_profile = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 tls_export_cert = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 verify_x509_name = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 ns_cert_type = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 65535
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_ku[i] = 0
Sep 24 23:52:48 openvpn 90203 remote_cert_eku = 'TLS Web Client Authentication'
Sep 24 23:52:48 openvpn 90203 ssl_flags = 192
Sep 24 23:52:48 openvpn 90203 renegotiate_packets = 0
Sep 24 23:52:48 openvpn 90203 tls_exit = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_protected_authentication = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_private_mode = 00000000
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_cert_private = DISABLED
Sep 24 23:52:48 openvpn 90203 pkcs11_pin_cache_period = -1
Sep 24 23:52:48 openvpn 90203 pkcs11_id_management = DISABLED
Sep 24 23:52:48 openvpn 90203 server_network = 10.3.101.0
Sep 24 23:52:48 openvpn 90203 server_network_ipv6 = ::
Sep 24 23:52:48 openvpn 90203 server_netbits_ipv6 = 0
Sep 24 23:52:48 openvpn 90203 server_bridge_ip = 0.0.0.0
Sep 24 23:52:48 openvpn 90203 server_bridge_pool_start = 0.0.0.0
Sep 24 23:52:48 openvpn 90203 push_entry = 'route 192.168.18.0 255.255.255.0'
Sep 24 23:52:48 openvpn 90203 push_entry = 'topology subnet'
Sep 24 23:52:48 openvpn 90203 push_entry = 'ping 10'
Sep 24 23:52:48 openvpn 90203 ifconfig_pool_defined = ENABLED
Sep 24 23:52:48 openvpn 90203 ifconfig_pool_end = 10.3.101.254
Sep 24 23:52:48 openvpn 90203 ifconfig_pool_netmask = 255.255.255.0
Sep 24 23:52:48 openvpn 90203 ifconfig_pool_persist_refresh_freq = 600
Sep 24 23:52:48 openvpn 90203 ifconfig_ipv6_pool_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 n_bcast_buf = 256
Sep 24 23:52:48 openvpn 90203 tcp_queue_limit = 64
Sep 24 23:52:48 openvpn 90203 virtual_hash_size = 256
Sep 24 23:52:48 openvpn 90203 learn_address_script = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 client_disconnect_script = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 client_config_dir = '/var/etc/openvpn/server3/csc'
Sep 24 23:52:48 openvpn 90203 tmp_dir = '/tmp'
Sep 24 23:52:48 openvpn 90203 push_ifconfig_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 push_ifconfig_ipv6_defined = DISABLED
Sep 24 23:52:48 openvpn 90203 push_ifconfig_ipv6_local = ::/0
Sep 24 23:52:48 openvpn 90203 enable_c2c = DISABLED
Sep 24 23:52:48 openvpn 90203 duplicate_cn = DISABLED
Sep 24 23:52:48 openvpn 90203 cf_max = 0
Sep 24 23:52:48 openvpn 90203 cf_per = 0
Sep 24 23:52:48 openvpn 90203 cf_initial_per = 10
Sep 24 23:52:48 openvpn 90203 max_routes_per_client = 256
Sep 24 23:52:48 openvpn 90203 auth_user_pass_verify_script_via_file = DISABLED
Sep 24 23:52:48 openvpn 90203 auth_token_lifetime = 0
Sep 24 23:52:48 openvpn 90203 auth_token_secret_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 port_share_port = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 vlan_accept = all
Sep 24 23:52:48 openvpn 90203 vlan_pvid = 1
Sep 24 23:52:48 openvpn 90203 auth_user_pass_file = '[UNDEF]'
Sep 24 23:52:48 openvpn 90203 library versions: OpenSSL 3.0.12 24 Oct 2023, LZO 2.10
Sep 24 23:52:48 openvpn 90203 DCO version: FreeBSD 14.0-CURRENT amd64 1400094 #1 RELENG_2_7_2-n255948-8d2b56da39c: Wed Dec 6 20:45:47 UTC 2023 root@freebsd:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_2-main/obj/amd64/StdASW5b/var/jenkins/workspace/pfSense-CE-snapshots-2_7_2-main/sources/F
Sep 24 23:52:48 openvpn 90472 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/server3/sock
Sep 24 23:52:48 openvpn 90472 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sep 24 23:52:48 openvpn 90472 Diffie-Hellman initialized with 2048 bit key
Sep 24 23:52:48 openvpn 90472 WARNING: experimental option --capath /var/etc/openvpn/server3/ca
Sep 24 23:52:48 openvpn 90472 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Sep 24 23:52:48 openvpn 90472 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Sep 24 23:52:48 openvpn 90472 TLS-Auth MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1250 tun_max_mtu:0 headroom:126 payload:1600 tailroom:126 ET:0 ]
Sep 24 23:52:48 openvpn 90472 ROUTE_GATEWAY 172.31.255.5/255.255.255.252 IFACE=igb0 HWADDR=00:0d:b9:5e:92:40
Sep 24 23:52:48 openvpn 90472 TUN/TAP device ovpns3 exists previously, keep at program end
Sep 24 23:52:48 openvpn 90472 TUN/TAP device /dev/tun3 opened
Sep 24 23:52:48 openvpn 90472 do_ifconfig, ipv4=1, ipv6=0
Sep 24 23:52:48 openvpn 90472 /sbin/ifconfig ovpns3 10.3.101.1/24 mtu 1500 up
Sep 24 23:52:48 openvpn 90472 /usr/local/sbin/ovpn-linkup ovpns3 1500 0 10.3.101.1 255.255.255.0 init
Sep 24 23:52:48 openvpn 90472 /sbin/route add -net 192.168.11.0 10.3.101.2 255.255.255.0
Sep 24 23:52:48 openvpn 90472 Data Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ]
Sep 24 23:52:48 openvpn 90472 Socket Buffers: R=[42080->42080] S=[57344->57344]
Sep 24 23:52:48 openvpn 90472 UDPv4 link local (bound): [AF_INET]172.31.255.6:1197
Sep 24 23:52:48 openvpn 90472 UDPv4 link remote: [AF_UNSPEC]
Sep 24 23:52:48 openvpn 90472 MULTI: multi_init called, r=256 v=256
Sep 24 23:52:48 openvpn 90472 IFCONFIG POOL IPv4: base=10.3.101.2 size=253
Sep 24 23:52:48 openvpn 90472 Initialization Sequence Completed
Sep 24 23:52:48 openvpn 90472 Connection Attempt MULTI: multi_create_instance called
Sep 24 23:52:48 openvpn 90472 18.48.13.121:4264 Re-using SSL/TLS context
Sep 24 23:52:48 openvpn 90472 18.48.13.121:4264 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Sep 24 23:52:48 openvpn 90472 18.48.13.121:4264 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Sep 24 23:52:48 openvpn 90472 18.48.13.121:4264 Control Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1250 tun_max_mtu:0 headroom:126 payload:1600 tailroom:126 ET:0 ]
Sep 24 23:52:48 openvpn 90472 18.48.13.121:4264 Data Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ]
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=vpn_ssl_remote, C=CH, ST=Town, L=City, O=MyRemoteCompany1, OU=DepartmentRemoteInc
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=internal-ca, C=CH, ST=Town, L=City, O=MyRemoteCompany1, OU=DepartmentRemoteInc
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY SCRIPT OK: depth=1, CN=internal-ca, C=CH, ST=Town, L=City, O=MyRemoteCompany1, OU=DepartmentRemoteInc
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY OK: depth=1, CN=internal-ca, C=CH, ST=Town, L=City, O=MyRemoteCompany1, OU=DepartmentRemoteInc
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY KU OK
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 Validating certificate extended key usage
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 ++ Certificate has EKU (str) TLS Web Client Authentication, expects TLS Web Client Authentication
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY EKU OK
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY SCRIPT OK: depth=0, CN=vpn_ssl_remote, C=CH, ST=Town, L=City, O=MyRemoteCompany1, OU=DepartmentRemoteInc
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 VERIFY OK: depth=0, CN=vpn_ssl_remote, C=CH, ST=Town, L=City, O=MyRemoteCompany1, OU=DepartmentRemoteInc
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_VER=2.6.8
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_PLAT=freebsd
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_TCPNL=1
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_MTU=1600
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_NCP=2
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_PROTO=990
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_LZO_STUB=1
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_COMP_STUB=1
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 peer info: IV_COMP_STUBv2=1
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 TLS: tls_multi_process: initial untrusted session promoted to trusted
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519
Sep 24 23:52:49 openvpn 90472 18.48.13.121:4264 [vpn_ssl_remote] Peer Connection Initiated with [AF_INET]18.48.13.121:4264
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 MULTI_sva: pool returned IPv4=10.3.101.2, IPv6=(Not enabled)
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 MULTI: Learn: 10.3.101.2 -> vpn_ssl_remote/18.48.13.121:4264
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 MULTI: primary virtual IP for vpn_ssl_remote/18.48.13.121:4264: 10.3.101.2
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Data Channel MTU parms [ mss_fix:1400 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ]
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Outgoing dynamic tls-crypt: Cipher 'AES-256-CTR' initialized with 256 bit key
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Outgoing dynamic tls-crypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Incoming dynamic tls-crypt: Cipher 'AES-256-CTR' initialized with 256 bit key
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Incoming dynamic tls-crypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sep 24 23:52:49 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 SENT CONTROL [vpn_ssl_remote]: 'PUSH_REPLY,route 192.168.18.0 255.255.255.0,route-gateway 10.3.101.1,topology subnet,ping 10,ping-restart 60,ifconfig 10.3.101.2 255.255.255.0,peer-id 0,cipher AES-256-GCM,protocol-flags cc-exit tls-ekm dyn-tls-crypt,tun-mtu 1500' (status=1)
Sep 24 23:52:50 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Data Channel: cipher 'AES-256-GCM', peer-id: 0
Sep 24 23:52:50 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Timers: ping 10, ping-restart 120, inactive 300
Sep 24 23:52:50 openvpn 90472 vpn_ssl_remote/18.48.13.121:4264 Protocol options: explicit-exit-notify 1, protocol-flags cc-exit tls-ekm dyn-tls-crypt
Sep 24 23:52:53 openvpn 90472 MANAGEMENT: Client connected from /var/etc/openvpn/server3/sock
Sep 24 23:52:53 openvpn 90472 MANAGEMENT: CMD 'status 2'
Sep 24 23:52:53 openvpn 90472 MANAGEMENT: Client disconnected -
@info385
Nothing to see in the log regarding applying the CSO. So probably it wasn't.Ensure that the common name you stated in the CSO matches the common name in the respective client certificate.
-
@viragomann As I have only 1 client, I can remove the CSO.
If so, what changes do I apply ?I confirm that the client certificate name was matching the common name of the CSO.
-
@info385
If the CSO is properly applied the OpenVPN server should log this with verbosity level 4 or higher.Without CSO, change the tunnel network mask to /30 and disable DCO if used currently.
-
@viragomann Thanks. It's fixed.
So basically switching /24 to /30 solved the issue.
Thank you again!