How to allow syslog-ng from DMZ to LAN?
-
Hello, I have attempted in different ways but still the syslog-ng traffic is not passing from the DMZ server to the LAN monitoring station.
Please help much appreciated.
DMZ: 192.168.2.0/24
LAN: 10.10.0.0/16 -
@selroc syslog is normally udp 514, so create a rule on your dmz interface that allows talking to whatever IP your monitoring station is on your lan. Unless your using some other port? Or tcp? Just make the appropriate rule.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated - so your rule needs be above where you would block or policy route traffic.
Post up a picture of your dmz rules. Do you have any rules in your floating tab, they are evaluated before interface rules.
Also keeping in mind that the syslog sender in your dmz needs to be using pfsense dmz IP as its gateway, and any firewall rules the host wanting to accept the syslog needs to allow for it.
-
Thank you, here a screenshot of DMZ firewall rules:
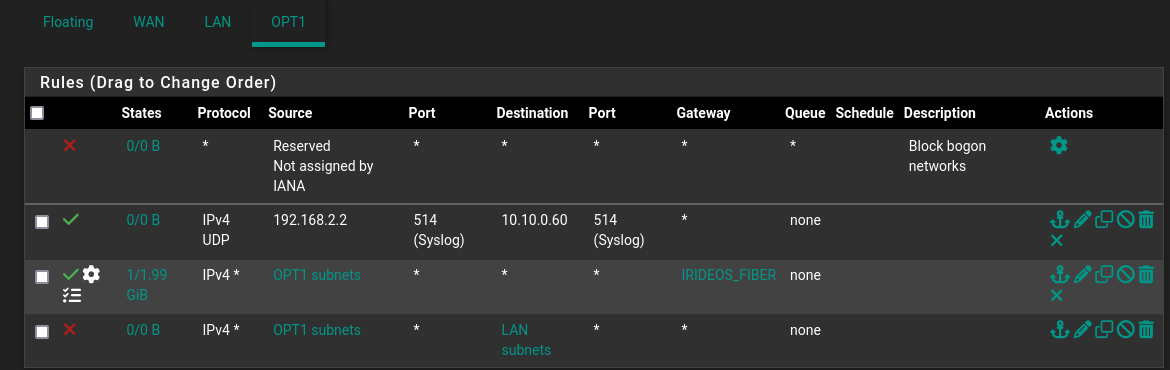
-
@selroc well your source is going to be some random port, not 514 so that is why that rule is never triggering.
also its pretty pointless to block bogon on your local side.. How would any IP be source of ingress into that interface? And your rules that allow traffic state it has to be a opt1 subnet for the source anyway. So any other IP as source would never be allowed in the first place.
And your rule below that forces all traffic out your gateway there, your syslog traffic would be allowed by that rule but your forcing it out a gateway that can't get to your syslog server.
Your rule blocking to your lan should really be above your any rule that allows anything, but forces it out your fiber gateway.. There is little reason to policy route unless you have more than one gateway and want traffic to use a specific one. Do you have more than 1 gateway to get to the internet, a vpn connection? etc..
-
Does it look better now?
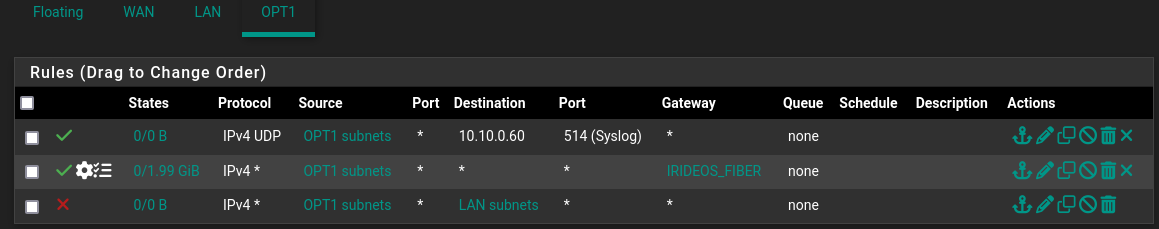
-
@selroc that syslog rule should work now.. If that is the IP your sending to and your sending udp 514 and not tcp or some other port. But I see no triggers on it as of yet see the 0/0 B that means no traffic has even triggered that rule.
Have you sent syslog traffic? Do you have any rules in floating that might supersede your syslog allow rule?
I would move your block to lan above your policy route rule. Depending on your settings if that gateway goes down, that rule could just be there without the policy route, which would allow access from anything on your opt1 to talk to anything on any of your other networks.
-
Yes there is one rule to block inbound ssh:
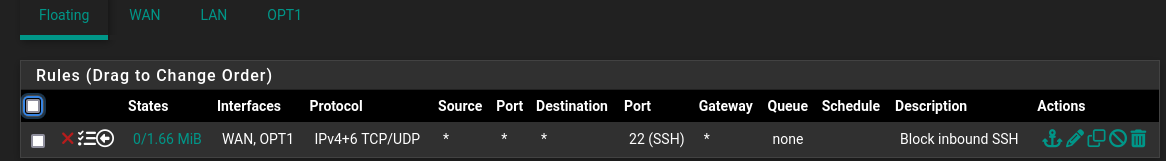
-
@selroc well that would have nothing to do with it.. So are you sending syslog and are you seeing numbers change on the states from 0/0 if not then your not sending to port 514 udp, or not to that IP or that device is not using pfsense as its gateway.
-
Yes there is traffic now:
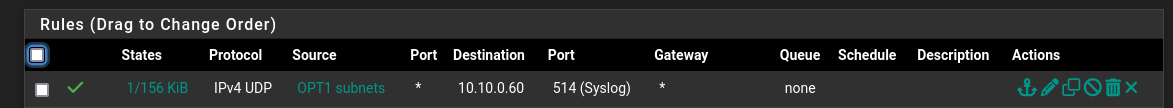
-
@selroc great, so your working then.
-
Thank you very much for your prompt help.