Routing LAN traffic to OpenVPN Client
-
I have a Synology NAS offsite as a client to my PFSENSE router via OpenVPN on subnet 192.168.11.x
This is connected fine and I can ping my NAS from the routerAdditionally, where I am connected to to my VPN with a client offsite I can access the computers on my LAN on subnet 192.168.77.x no problem
I can ping the NAS from my PFSENSE router which is the OpenVPN server and receive the replies
However, when I try to ping the NAS from a machine on the LAN, or access its network shares I cannot do so.
I have added the following rules to the firewall to see if I can move things along but I feel I am missing something. Can anyone point to what I am doing wrong?
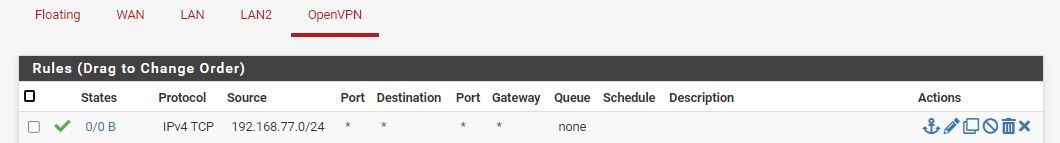
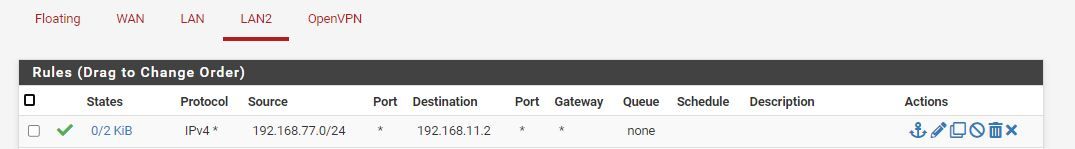
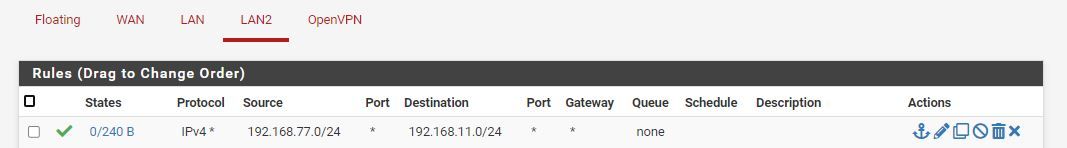
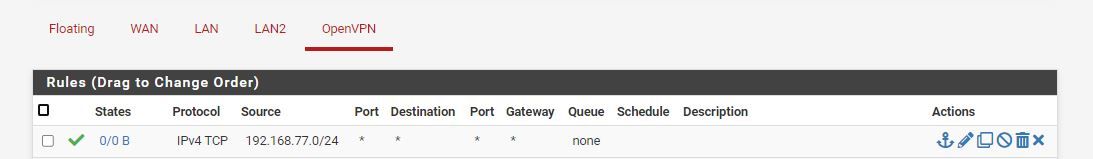
-
@AddleDIT
The NAS might block access from outside of its own subnets. You will have to configure its firewall to allow it.
I assume, that the route to the LAN is added properly to the NAS, but you should verify this also.BTW: The rule on the OpenVPN with the LAN subnet as source is pretty useless. Rules have to be defined on the interface, where the initiate connection is coming in. The VPN interface will never see a packet coming in from the LAN subnet, however.
-
I put a windows machine with an SMB network share on the same VPN offsite and I still have the same issue on that machine also. The two offsite VPN clients SMB cannot be accessed while connected to the VPN nor can they be pinged, but interestingly RDP does work both ways.
There is no firewall on the NAS or the Windows computer, so I am pretty sure this is a routing issue.
-
@AddleDIT
Also Windows blocks access from outside of its subnet by default.Do you try to access the SMB by IP or by host name? IP should work at least.
I cannot help you with your devices firewalls. But you can investigate, whats going on, on pfSense with Diagnostic > Packet Capture.
Select the VPN interface, enter 445 in the port filter, start the capture and try to access the NAS.
Stop the capture and post, what you get. -
I am using IP, not hostname
Here is a packet capture from the call on the NAS to the point it says can't connect
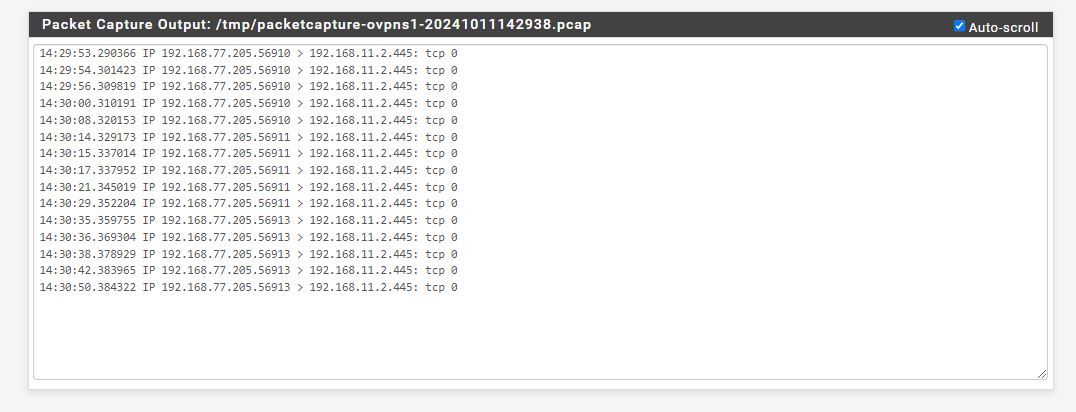
I made the Open VPN server an interface
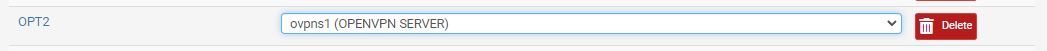
And stuck it in a bridge with the LAN and rebooted
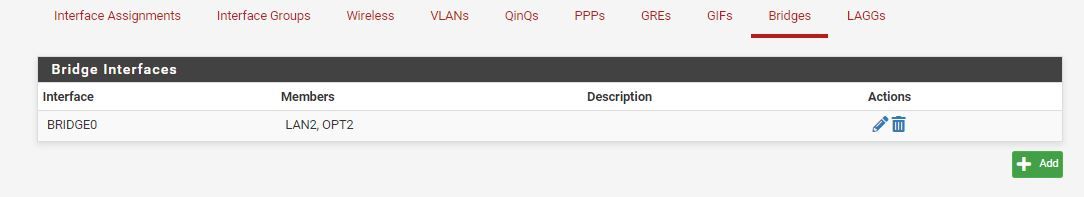
Now I can ping the openvpn server gateway on 192.168.11.1 and get replies from my desktop, but cant ping the NAS from same
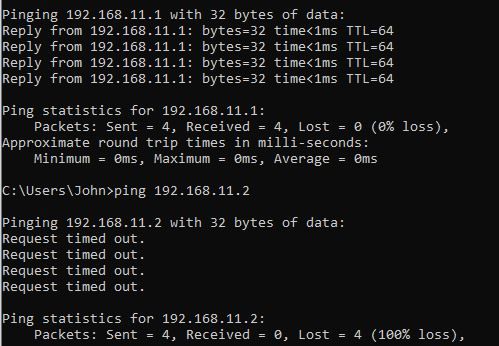
If I test the port from the openvpn server interface it works
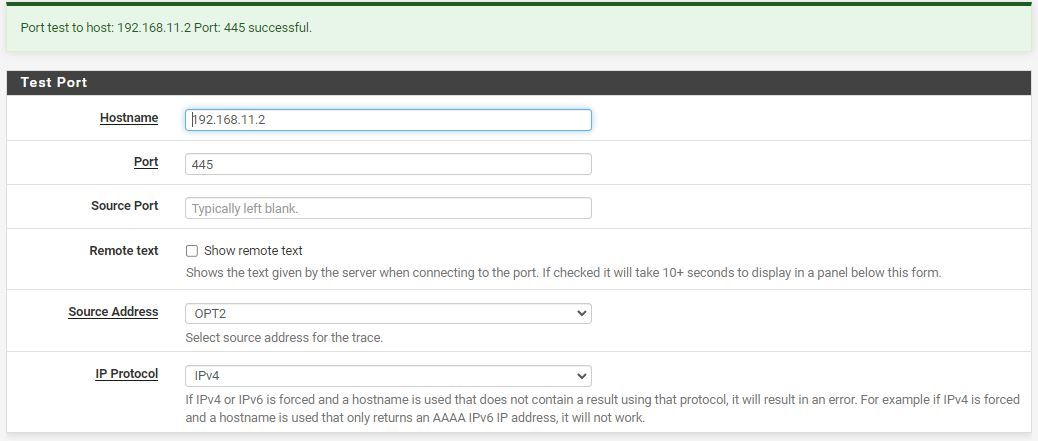
But if I try the same from my lan interface it does not
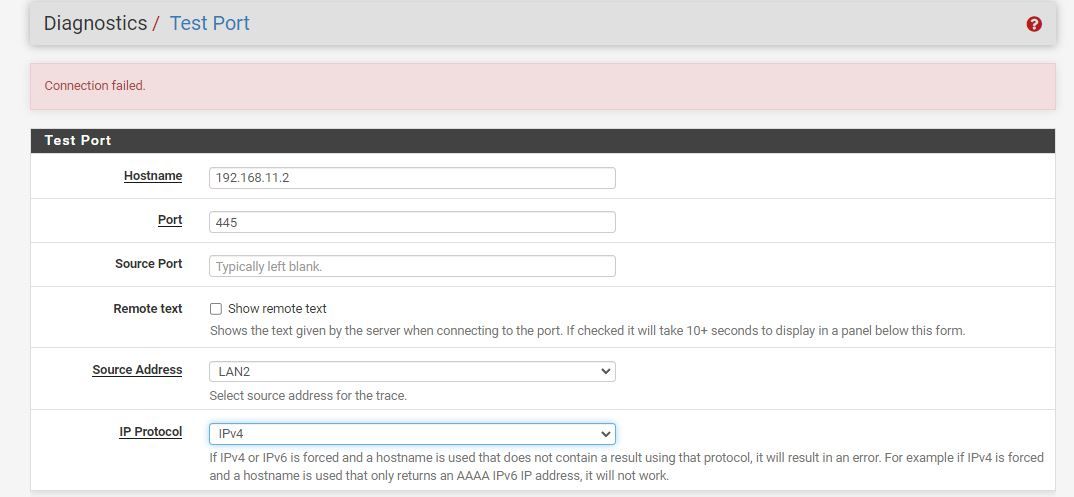
-
@AddleDIT
So you see only request packets, but no replies. This indicates, that the access is blocked by the destination device as I suspected first.Bridging the VPN to the LAN is not recommended at all! If you don't know, how to configure your NAS properly to accept access from the remote network, your should better do masquerading on pfSense.
-
I have done this but the performance is woeful with both the clients on the VPN. Or do you mean something different? I might try it the other way around and make the NAS a VPN host
-
@AddleDIT
I'm talking about natting the traffic. I don't expect this to have any impact noticeable on the impact on the performance. Rather bridging does.