Firewall and routing for my LAN
-
@kramnoraa said in Firewall and routing for my LAN:
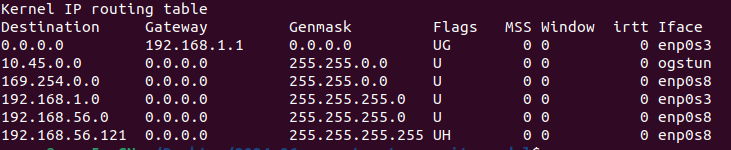
On the pfsense web gui, I created two LAN interfaces, for the pfsense (.3) and the 10.45.0.3/16 (for the 5g network and user equipment traffic)
I guess, the 5g and the user equipment need to be within the same layer 2 subnet.
So your only one option to control the traffic between both on pfSense is to connect them to efferent interfaces and bridge these on pfSense.Since you're running pfSense virtualized, it's easy to add an additional virtual interface to it.
-
@SteveITS Nothing is on a VPN as of yet.
Right I see, maybe my understanding is wrong.
I am able to monitor all the connections in the pcaps, but i wanted to create a specific rule for the user equipment machine (10.45.0.2 and 192.168.56.115) and the ftp machine (192.168.56.121) that would let me pass/reject traffic.
All 3 machines are in my LAN but since the communication for the 5g and user equipment uses the 10.45.0.0/16 and the ftp uses the 192.168.56.121, i was hoping i could create specific rules for the traffic filtering? Is this not possible? -
@viragomann Thank you for the tips. I need my 5g machine + user equipment machine and FTP machine to be in the same LAN, is there a way to control the traffic between these without connecting them to ethernet interfaces? I wanted the setup to be somewhat like this, is this possible?
-
@kramnoraa said in Firewall and routing for my LAN:
I need my 5g machine + user equipment machine and FTP machine to be in the same LAN,
Why the FTP? It's currently in a different subnet than the 5g and it can be accessed across a router.
is there a way to control the traffic between these without connecting them to ethernet interfaces?
To control the traffic between the VMs on pfSense, you have to put the firewall in between them to force the traffic over it.
This requires, that you create separate virtual network on the host for each, the 5g and user equipment. Also add virtual interface in each network to pfSense. In pfSense assign interfaces and enable them. Then bridge both, assign an interface to the bridge and set and IP, which the VMs use as gateway to access the FTP and the internet.
For instance, I've bridged the interfaces HafIoT and HafIoT2:


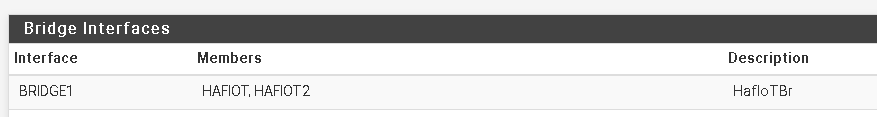
HafIoT is a VLAN for a wifi. HafIoT2 is virtual network on the host, which an LXC is connected to.
So my TV in the HafIoT WLAN and the LXC, which is running a DLNA server, are within the same L2 subnet and I can watch videos served by the DLNA. -
This post is deleted! -
@viragomann Thanks for the info once again!
I am using the ftp just as a service that the user equipment can connect into, for simulation purposes. Can i not have the FTP on my LAN and still achieve what i want?
Can i not use pfsense as a routing and firewall solution? I can monitor absolutely all the traffic flow from the pcaps, so i assumed that I'd be able to add firewall rules for this as well. Is that not the case ?
I'll have to do some research on bridging and try to understand what you mentioned above, this is a longshot but any chance you'd be able to put this in a diagram form so it would be easier to understand ? Would be extremely appreciated. Thanks for the replies once again
-
@kramnoraa How is 10.45.0.2 connecting to pfSense? Do you have an IP alias on LAN for that subnet? A second interface?
10.45.0.2 cannot talk to 192.168.56.115 directly if they are in different subnets.
In general, one way would be to have two internal interfaces on pfSense, LAN and LAN2, and then firewall rules control flow between the two networks.
-
@SteveITS I've got two interfaces on pfsense, LAN (192.168.56.3 | pfsense IP) and LAN 2 (10.45.0.3 | for the 5g and ue)
10.45.0.1 is the 5g networks IP from the tunnel it creates (ogstun), has a 192.168.56.116 IP aswell on the enp0s3 adapter
10.45.0.2 is the user equipment IP from the tunnel it creates (uesimtun), has a 192.168.56.115 IP aswell on the enp0s8 adapter
192.168.56.121 is the FTP machine's IP and only has one enp0s8 adapterive allowed all traffic flow in the firewall rules on both interfaces from LAN to LAN2. With this, i can monitor the .115 to .116 connection and response (user and 5g) and can monitor the 10.45.0.2 to .121 (user to ftp connection) in the pcaps.
Since im able to monitor these connections with the created interfaces, i assumed i can configure a specific rule that will allow/reject the user to ftp traffic.
I have ip routes on the individual machines for this communication to work before i started using pfsense, i am using pfsense for a firewall and routing solution so that i can get rid of the ip routes on the individual machines, monitor the traffic flow and allow/reject traffic based on the IP's in the firewall rules. But until now i can only monitor the traffic, if i get rid of the routes on the individual machines, i cant connect the user to the ftp machine and cant create specific rules to enable the flow, not too sure where im going wrong
-
That should work as long as all devices are using pfSense as their default route. I suspect they are not though.
-
@stephenw10 I've tried using pfsense 192.168.56.3 IP as the default for each machine, but no luck.
If i use the pfsense IP as the default gateway on each machine, do i need to configure static routes on pfsense similar to how I was using the ip routes on the each individual machine for the traffic to flow again?
Because once i add the default gateway and remove the ip routes i had on the machines for the communication before, the user machine cant access the ftp machine anymore from the 10.45.0.2 IP to the 192.168.56.121 IP
-
@kramnoraa Did firewall rules on LAN2 allow access to that server on LAN?
Does any firewall on the FTP server allow access from the other subnet?
If two devices on two pfSense networks both use pfSense as their gateway then the routing is all automatic and you just need firewall rules to allow it.
Allow ICMP and then test with ping/traceroute.
-
@kramnoraa said in Firewall and routing for my LAN:
10.45.0.1 is the 5g networks IP from the tunnel it creates (ogstun), has a 192.168.56.116 IP aswell on the enp0s3 adapter
10.45.0.2 is the user equipment IP from the tunnel it creates (uesimtun), has a 192.168.56.115 IP aswell on the enp0s8 adapter@kramnoraa said in Firewall and routing for my LAN:
Because once i add the default gateway and remove the ip routes i had on the machines for the communication before, the user machine cant access the ftp machine anymore from the 10.45.0.2 IP to the 192.168.56.121 IP
I think, I got you wrong first. So forget the bridge.
I don't know, how the tunnel between the user equipment (uesimtun) and the 5g networks (ogstun) work. But I can imagine, that the user equipment sets the default route to the 5g, when connecting.
This means the connection to the FTP would be directed across the 5g. Maybe this is an issue.For proper routing, the 5g would have to masquerade the source IP.
However, it's not clear to me, how the 5g goes to other subnets / the internet. You wrote, you gave pfSense an IP in LAN2 (10.45.0.3). But if this is just a tunnel network between the 5g and the user, I don't expect, that there goes any traffic to the pfSense LAN2 interface.
Maybe you can clarify the function of the tunnel. -
@viragomann For the internet, yes, the route goes through the 5g network, but for the FTP there's no such route to go through the 5g network, the source IP is the user equipment's tunnel IP thats created when i build the equipment, 10.45.0.2 directly to the FTP server, 192.168.56.121, this is confirmed with a tcpdump and since the connection only works when i create a route on the user machine to direct all traffic to the FTP's IP via the user equipment tunnel
The pfSense's IP in LAN is 192.168.56.3, the LAN2 IP in pfsense is 10.45.0.3.
To my knowledge as of yet, the connection should go from the user to 5g network and then to the FTP server but since i'm not too sure how to do that, i'm sticking with the user equipment connecting directly to the FTP server, with the user equipments tunnel IP, 10.45.0.2 > 192.168.56.121
How can i allow/block the ftp or icmp traffic from 10.45.0.2 to 192.168.56.121 with no routes on the machines and only routes on the web gui? is this possible
-
@SteveITS I'm able to monitor the packets from LAN2 to LAN, cant control access
There is no firewall on the FTP server, ufw is disabled and i'm only using the pfsense as a firewall
I've tried using the default gateway on each individual machine but not sure why it isn't working, will try it again now
-
@kramnoraa said in Firewall and routing for my LAN:
For the internet, yes, the route goes through the 5g network, but for the FTP there's no such route to go through the 5g network
And how can the machine differ this without a specific static route for the FTP?
If the the default route goes to the 5g, without specific routes, it will send traffic to all destinations outside of its own subnet to the default gateway, which is the 5g.How does the 5g go to the internet? Does it have a certain tunnel on its own or does it use 192.168.56.3 as upstream gateway?
-
@viragomann I've added static routes on both the user machine and the ftp machine to allow traffic between them based on their IP's, since the traffic gets sent to the 5g network by default, maybe i need to specify a route on the 5g machine itself to forward traffic to the ftp machine's IP ?
The 5g network when ran, creates a tunnel 'ogstun' that handles the traffic for the 5g network, from the open5gs docs, i've added this rule ' sudo iptables -t nat -A POSTROUTING -s 10.45.0.0/16 ! -o ogstun -j MASQUERADE ' when building the network for internet access i believe ( i might be wrong).
Would i add a rule somewhat like ' sudo iptables -t nat -A POSTROUTING -s 10.45.0.0/16 -d 192.168.56.121 -j ACCEPT ' to allow traffic from the user equipment, to the 5g network and then to the ftp server? instead of the user equipment's tunnel IP, 10.45.0.2 directly accessing the ftp server with the static route on the two machines
-
@kramnoraa said in Firewall and routing for my LAN:
I've added static routes on both the user machine and the ftp machine to allow traffic between them based on their IP's,
The static route on the user machine should be all you need.
since the traffic gets sent to the 5g network by default, maybe i need to specify a route on the 5g machine itself to forward traffic to the ftp machine's IP ?
We have to know, how the 5g goes out to get further. I requested this above.
Can you post its routing table, when the 5g network is running? -
Routing table for the machine thats running the 5g network ^
-
@viragomann
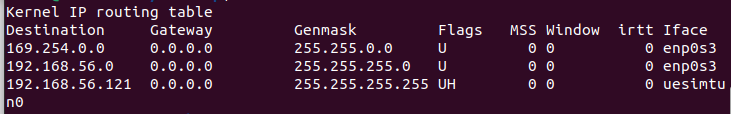
Routing table for user equipment machine ^ -
@kramnoraa said in Firewall and routing for my LAN:
Routing table for the machine thats running the 5g network ^
Why is the default gateway 192.168.1.1? You didn't mention this subnet till now.
Shouldn't it rather be 192.168.56.3?Also I don't get, why the user machine has a route for the FTP bound to uesimtun, since it should have an IP in the LAN on enp0s3.