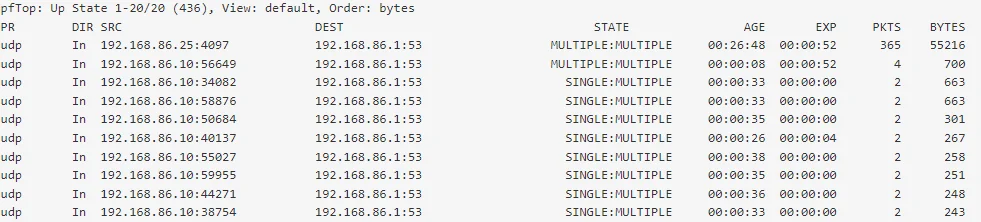
pfSense Firewall rules don't seem to have any effect ?
-
@abesh said in pfSense Firewall rules don't seem to have any effect ?:
TOPOLOGY : ATT Modem (Passthrough) -> pfSense -> TP Link AXE5300 (mesh in AP mode)
You can see the pfSense interfaces as gates. pfSense can control any packet, which tries enter a gate and going though. However, it has no effect on packet flow outside.
Traffic from a devices connected to the wifi to another wifi device doesn't pass your pfSense and hence cannot be controlled.
When you insert pfSense into your network as a router, it provides a DHCP and server and a DNS resolver for your LAN by default.
If you don't want to use the DNS Resolver on pfSense, but use the pihole only, enter its IP into the DHCP server settings of your LAN at "DNS Servers".
If you want to use the DNS Resolver, but forward all requests to the pihole, enter its IP in System > General Setup > DNS Servers and enable Services > DNS Resolver > General Settings > DNS Query Forwarding. -
@viragomann Thank you ! That makes a lot of sense. I would make the changes that you suggest as they seem to be the cleanest.
Do you think I gain anything at all with the setup that I have with pfSense as a firewall, because it's being bypassed ? -
@abesh
You cannot control the traffic between your wifi devices this way, but you can control traffic between your devices and the WAN.
For usual home use this will have not a big benefit.To control traffic between your devices, you will have to segment your network, so that you have an interface on pfSense for each segment.
-
@viragomann Awesome ! Thank you, that makes a lot of sense :)
-
@viragomann If I want to catch any rogue DNS requests to a internet DNS server and redirect that to pihole, how would I go about it ? I am guessing I need to create a rule for the WAN interface ?
-
@abesh It is not hard to force to PiHole. There are similar instructions to force to pfSense.
https://forum.netgate.com/topic/156453/pfsense-dns-redirect-to-local-dns-server?_=1663853296484
-
-
@viragomann @AndyRH You guys rock! I have my work cut out :) Thank you !
-
I have been reading up on this and am going to try it out tomorrow. Couple of questions :
- Do I need a managed switch to get this working ? I am guessing YES.
- Do I have to create two VLANs - Home (all home devices) and DMZ (pihole) or can I do with LAN and a VLAN (DMZ for Pihole). Which subnet should pfSense be part of ? pfSense has a passthough external ipas well as an internal one (192.168.1.1 - same subnet as mt ATT modem)
- The pfSense web interface is also accessible via the external IP. Is there a way to disable this ?
- And lastly, i have configured the pfSense DNS Resolver as a forwarder to Pihole and also set the DNS settings to the Pihole DNS. This actually causes all DNS traffic to go solely to the Pihole. Therefore do I achieve anything extra in going through with the effort of setting up VLANs?
-
it’s a bad idea to have pfSense exposed to the Internet. By default it is not. Are you accessing the WAN IP from the internet, or LAN? The latter is allowed because LAN has a default allow rule. (The packet is through the gate and pfSense knows what to do with it, “that’s me!”). WAN has no rules so blocks all traffic by default.
Re: DNS:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html -
@SteveITS You are correct ! I was accessing the WAN Ip from the LAN !!! Thanks so much !
-
@SteveITS And also, are you implying that I donot need to do the entire setup at all?
-
@abesh said in pfSense Firewall rules don't seem to have any effect ?:
Do I have to create two VLANs
No, this will work with a single subnet. My example covers multi-VLAN. Just do the steps for your 1 VLAN.
-
@abesh said in pfSense Firewall rules don't seem to have any effect ?:
are you implying that I donot need to do the entire setup at all?
No, tbh I didn't read the rest. It was late for me and I thought I'd address that one point about the WAN IP.
-
-
@SteveITS said in pfSense Firewall rules don't seem to have any effect ?:
Re: DNS:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.htmlSo I tried this but landed into issues. I think I know what the issue but but not quite sure how to solve it.
On my pfSense I run the DNS Resolver with forwarding turned on to pihole. Pihole runs unbound locally and answers queries.
The NAT port forwarding above redirects all DNS queries back to the pihole, including the ones originating from it and thus I am not able to resolve anything.
Any idea how would I get past this other than moving the pihole to a VLAN of its own ? Thanks again @AndyRH @SteveITS ! -
@abesh This may help. I point pfSense and PiHole to an outside DNS. DHCP points the clients to PiHole. PiHole points to pfSense for the local domain home.arpa.
This arrangement prevents a reference loop. pfSense is the root for home.arpa.
My PiHoles serve DNS for several VLANs, including the one they are on.pfSense does not do anything where it would need ad blockings so there is no useful reason to have it go to PiHole.
Another tidbit, the OS running PiHole sometimes will have DNS resolution problems, to prevent this I also point the PiHole OS to an outside DNS. This also solves the problem of how to fix PiHole if the OS cannot resolve internet names. I like to use DHCP reservations, so I do it with DHCP. It is also valid to use static settings.
Later consider having 2 PiHoles for redundancy, with the settings to force DNS to PiHole, if PiHole is down you cannot resolve names. -
@AndyRH Awesome ! Thank you :) Isn't the setup then sort of similar to one that I started with ?