2 VPN in the same server but separate network
-
Hi I have a Phisycal server where I create different Virtual Machine, I need create 2 sperate group and with 2 VPN, If I enter in VPN1 I see only the NET1 (192.168.1.xxx) VPN2 only NET2 (192.168.10.1) and NET1 can't see Net2 and Net2 Can't see Net1
If I create 2 VPN is all ok but I can't isolate the Network If I scan I see alway the other Network.
Must create a new Pfsense for the new network? -
@Stefano-Coccia
Just restrict access for each VPN accordingly.Do you have two VPN servers or just two clients?
NET1 and NET2 are assigned to pfsense interfaces?
If you are on the NET1 VM, can you access anything in NET2 and vice versa?
-
Hi I have a server with hyperV (wan, lan1 and lan2) inside a VM with Pfsense, now I have Vpn (Wan to Lan), and I need create wan2 to lan2, but if I do in the same pfsense lan2 see lan1... and I donato want... or I create another Pfsense server or I don't understand how I can do...
-
@Stefano-Coccia
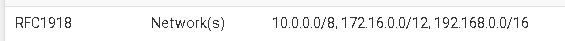
I created an networks alias:
Then I use this in the firewall rules to allow internet access:
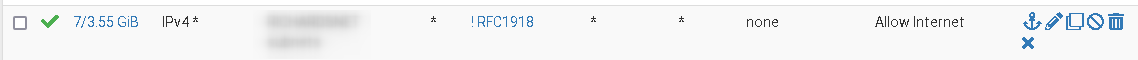
The alias includes all RFC 1918 (private) network ranges.
Note that in the rule "invert. match" is checked. So the pass rule is only applied to traffic with other destinations then the alias.To allow access to internal services like DNS, you need to add additional rules then. E.g.