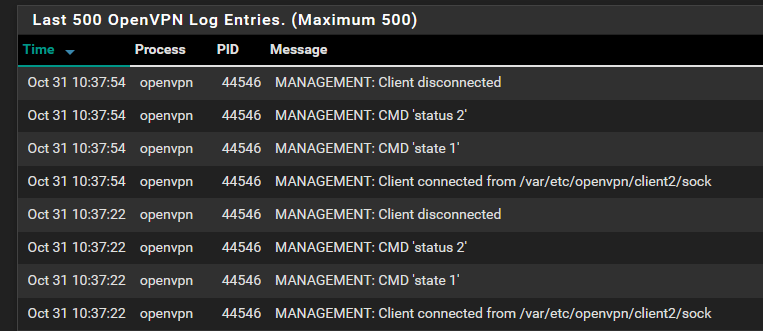
OpenVPN-Server on pfsense - cannot estabilish connection
-
@br8bruno Right at the bottom of the openvpn server instance's config page.
However you should still see some logging, with default log level, when a client attempts to connect. If you don't, it suggests the client isn't reaching the port. In which case, probably something blocking. If you have the vpn server listening on the WAN, you should still be able to reach this from the LAN without opening the WAN, for testing purposes. -
@br8bruno said in OpenVPN-Server on pfsense - cannot estabilish connection:
Ok, I have found the first problem.
The automatic rule that the wizard generates was below my "block-all" rule on WAN. Now I am able to connect.
I just cant access the internet, nor any client in the home network when connected to the VPN.Either you need to configure rules for the vpn subnet and/or the client is not using the vpn to route traffic concerned. You may need to push additional routes and/or allow traffic from vpn client subnet to your lan. You can assign the vpn server instance to a new interface or use the global openvpn rules tab.
-
Ok. So this goes somewhat in line with what I thought was happening.
Can you maybe please explain what you mean with the "use the global openvpn rules tab"? I don't see where I could be adding traffic rules in any setting of the openvpn server. -
@br8bruno
The openvpn rules tab is under firewall rules. The other way, as you suggested, is assigning the server instance a new interface and adding rules there.
The best place to refer to is the netgate docs. Also check out the recipes. -
Thank you for the help. I went the route of creating the interface and configuring it. That worked out fine.
I now can connect. And I can reach everything on my network that I setup in the firewall rules.I just have one issue left.
I have to use IPv6 to reach the pfsense, so I configured the OpenVPN Server to work with it, and that is fine.
But when I am connected to the VPN, I only get an IPv4 assigned to the client. How can I get the client to receive an IPv6, like in my other interfaces? The configuration of the interface for the OpenVPN Server does not have the same configuration as the interface for a VLAN. You can actually only enable it.
-
I also just noticed that the wizard created a very open rule for OpenVPN (not the interface of the OpenVPN Server.
What does this do, since I am adding rules to the interface? Should I need block all on the OpenVPN tab?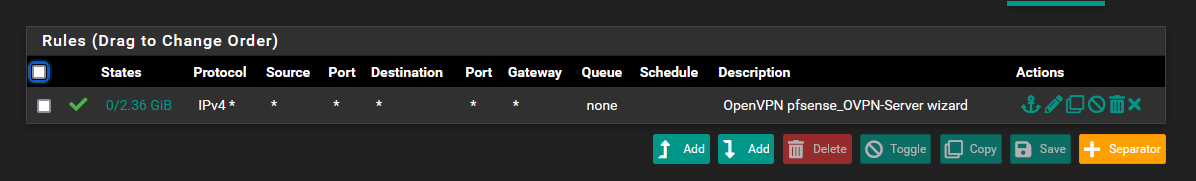
-
Presumably that rule got added under the openvpn tab's rules. I did not use the wizard. It seems overly permissive and AIUI would also apply to any vpn server or client instance you add in future.
Just disable it, clear related states, then check your own rules are matching traffic and working as expected. Then delete that rule.
I'm not sure about tunneling IPv6 qu. Check 'Endpoint Configuration' and 'Tunnel Settings' under the OpenVPN server config.
BTW You don't need to add explicit block all rules at the end as any traffic not handled by preceding rules is dropped, by default. -
Thanks!
You are a life savior!
Once I added a IP for the IPv6 network under Tunnnel Settings as you recommended, then the clients started getting an IPv6 as well.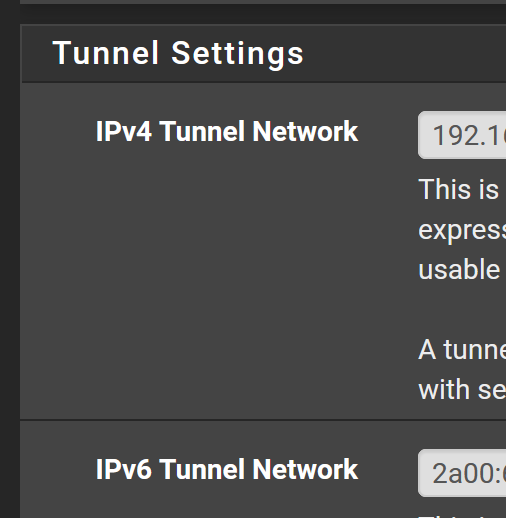
-
Now the next issue, Gateways...
Why were 2 new Gateways created when I created the OPVN-Server?
I have only one WAN, so I got one gateway for IPv4 and IPv6 each. That seems good an logical to me.But then I have a couple of VPN clients, that also created gateways automatically.
And now I also have 2 new gateways for the OVPN-Server, one for IPv4 and one for IPv6. Is that really necessary?
In the main menu from pfsense it is always displayed as offline for some reason.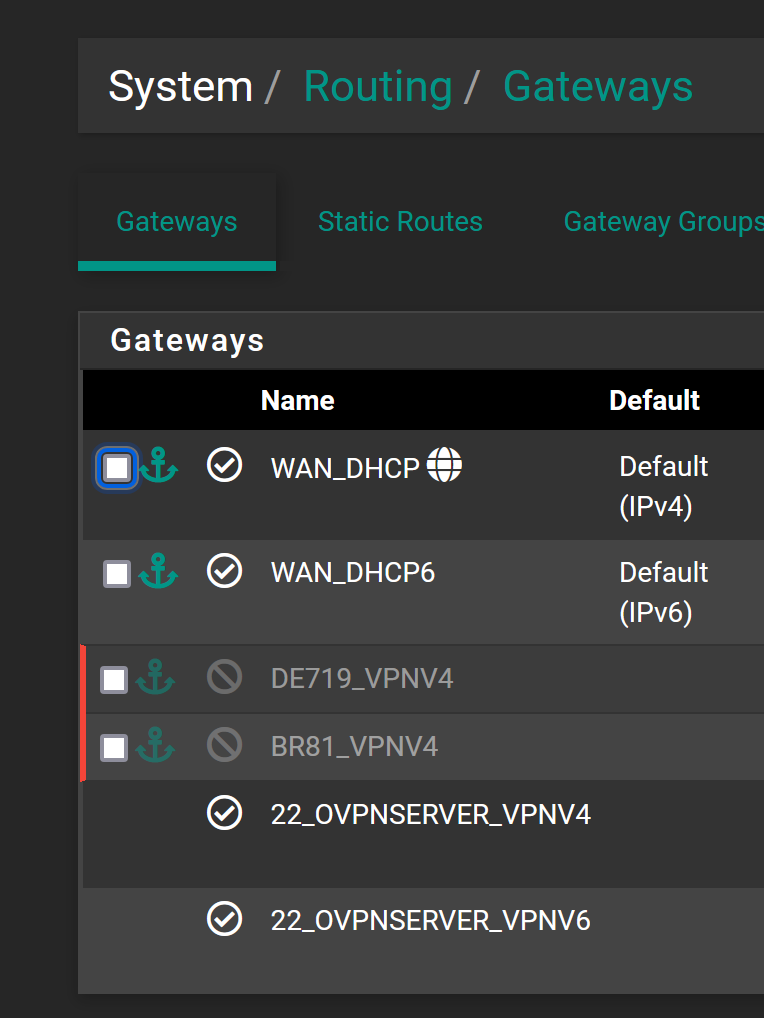
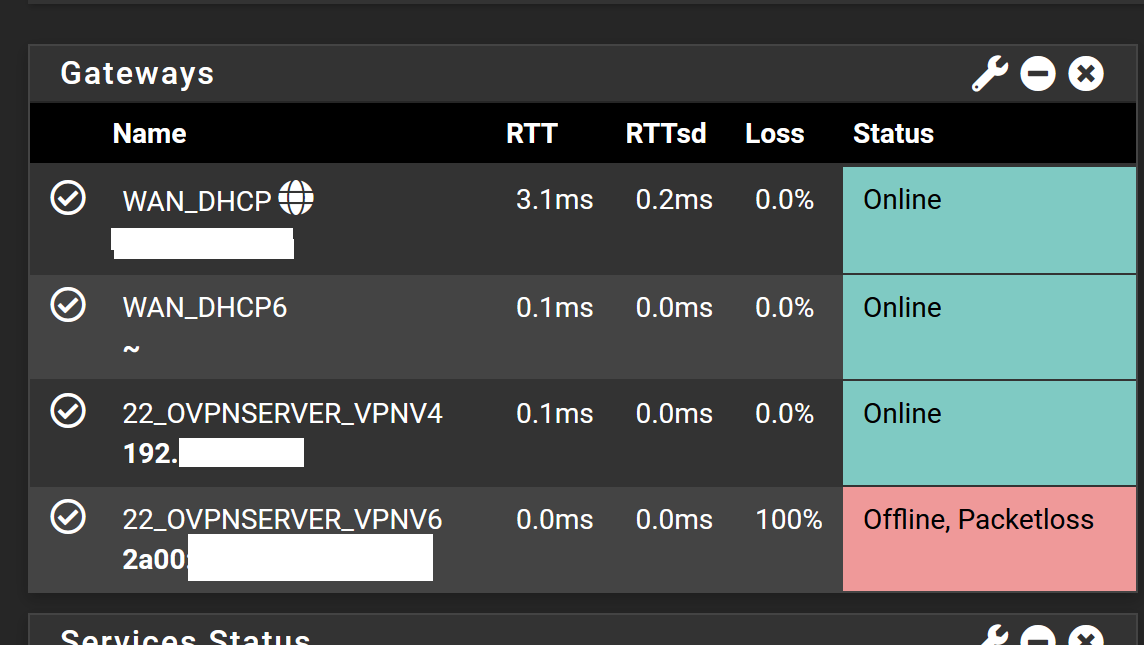
-
@br8bruno Gateways seem to get created for both openvpn server and client instances. Whilst I believe it is not absolutely necessary, that is how it is done in pfsense and you are then able to policy route (select a non-default gateway) in your firewall rules.
EDIT: You can turn off the gateway creation in the openvpn server|client config.