Bridge Setup is IMHO weird! Seems to complex!
-
I have a relative complex network at home. On top of the network pfSense and as first layer below that two main switches;
- one 1G-switch
- one 10G-switch
Up to now the 1G-network and the 10G-network did have their own management vlan. Reason for that is that the 1G and the 10G network should be independent. However I did not like that. The logical way to combine the two vlans was to create a bridge inside pfSense.
So I looked into that option and, in the end I discovered that that did not worked the way I did expect. My expectation was as follows
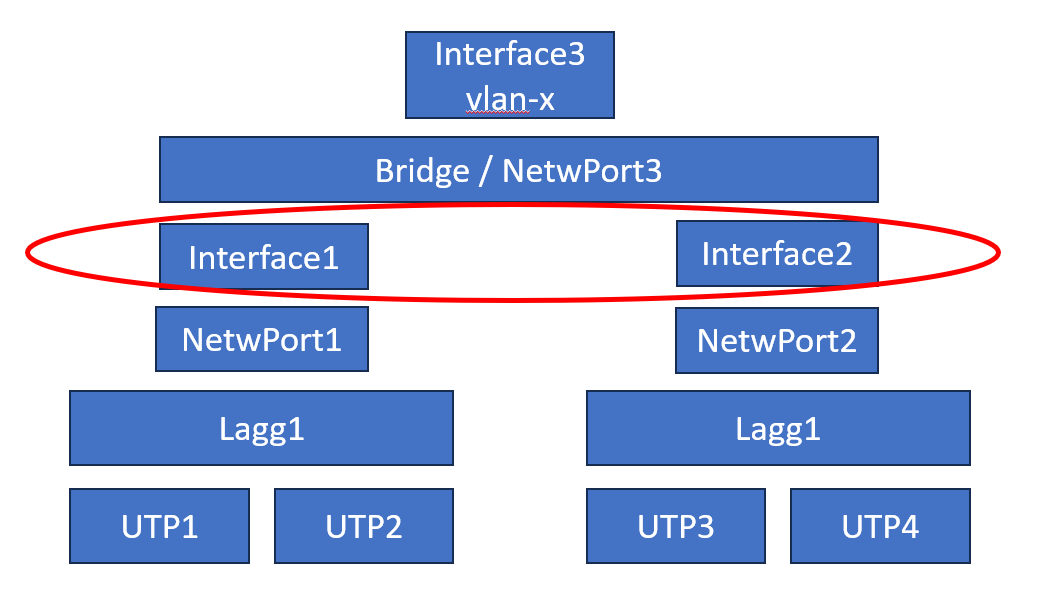
- the UTP/SFP-trunks are the lowest level
- the trunks are combined to a lagg
- the lagg is carrying a couple of vlans
- certain vlan-x lagg1 and vlan-x lagg2 are combined in a bridge
(to keep it simple I assume each vlan has its own bridge) - the bridge is the network-port towards a GW / the pfsense FW-core
However .... not so .....
- each lagg is tied towards a network-port
- that port tied to the pfSense-core
- than to the bridge
- than again to another pfSense-core GW
That just seams one layer too much !!
What ever, I just do not understand this complexity!!
See picture below
-
@louis2 said in Bridge Setup is IMHO weird! Seems to complex!:
The logical way to combine the two vlans was to create a bridge inside pfSense.
No.. Why would you ever bridge vlans together? Each vlan should be on its own layer 3 IP scheme.. If you want to combine 2 vlans together, then move one half into the other vlan and change its IPs to match that IP scheme.
Where you would "bridge" is you wanted to combine 2 different types of network interfaces together.. But they would be the same vlan. Or if you wanted to split a vlan where you could control traffic that flows over the bridge - but it would still be 1 vlan.
If you want all 4 of those ports in the same lagg, then do that, you can run multiple vlans over that lagg if you wanted too.
-
First there is a small but annoying fault in the picture, which may have confused you. At the left it is Lagg0 and the right it is lagg1 !!!
That did put you on the wrong lagg I think
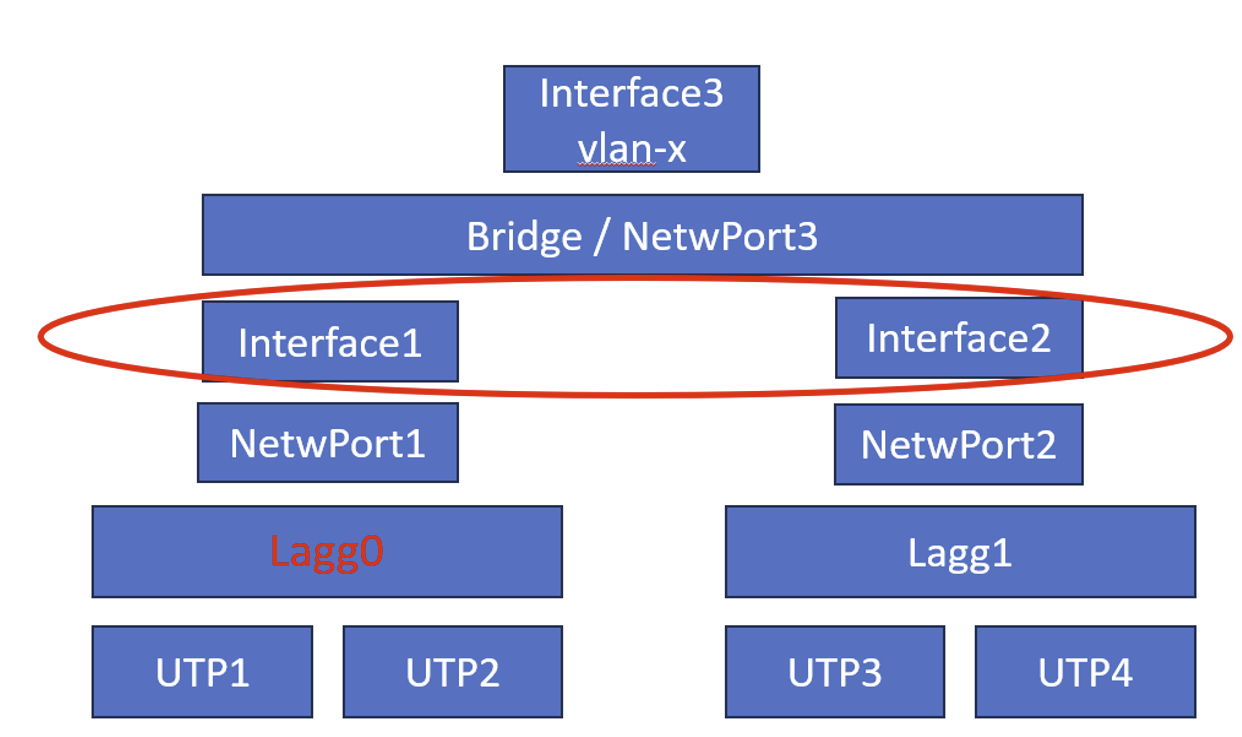
So you might not have understand the problem. There where two vlan's which I did want to combine in one vlan.
Lagg0 is carrying the 1G-vlans, Lagg1 the 10G-vlans. That are different vlans for in most cases different purposes. As example. The network below Lagg1 is my NAS etc.
The vlan they have in common is the management vlan. And where that were two management vlan's in the past, it is now one vlan for the whole network. To be able to route that one vlan across the 1G-network below lagg0 and the 10g network below lagg1, I did need the bridge.
So, I hope we agree on that.
Second point, being the reason for this topic, I really do not understand the strange setup / structure of the bridge setup. I really think that there is a strange and nor necessary layer.
-
@louis2 not sure what your trying to accomplish from that picture to be honest.. You want to carry the same vlans over 2 different interfaces?
Are you trying to plug both of these switches into different interfaces on pfsense, and have them both carry the same vlans? That would work fine if pfsense had switch ports.
Plug your 10ge into pfsense and then daisy chain your 1ge off your 10ge.. Now you can do whatever you want with vlans on any port any switch.. No bridging involved. Lagg between pfsense and the 10ge, and even lagg between the 10ge and your 1ge if you want. Only reason you would connect the 10ge into pfsense vs the 1ge is that pfsense actually had 10ge interfaces.
Call your 10ge your core switch, and your 1ge an Access switch ;)
Bridges are a solution to specific problems, they don't turn individual interfaces into switch ports. The only time it makes sense to "bridge" is when you have 2 different types of connection, say wifi and wired, or you need to connect in a fiber connection into your switching infrastructure and the sfp for your switch is delayed in shipment or something and you need to bring it up now, and your router just happens to have a fiber interface you could use.
Or for some reason you need to filter traffic between devices on the same vlan, and you can't isolate them to a different vlan for some crazy reason, and you want to filter traffic between where you split the vlan with a bridge.
-
Are you trying to plug both of these switches into different interfaces on pfsense, and have them both carry the same vlans In special cases like the managment lan, Yes!
And I am not filtering within one vlan of course, but I do filter all outgoing traffic and surely do not allow traffic from vlan-1 to pass to vlan-2 without explicit allowance.
I have two separate networks works for very good reason. Surely in the past the 10G network site was not exactly stable. When making configuration changes, I often had troubles. That has become much much better after software updates.
Even today the 1g network is more stable, partly due to the fact I make more changes in the 10G one. So even today I prefer a situation were I have two networks, which can function independently.
But still the question related to the very weird way the bridge is situated inside pfSense ....
-
@louis2 to be honest I don't get why anyone would bridge on their router.. I wouldn't do it unless is was the only way to bring something up, it would run just long enough until I could get the equipment needed to do it correctly.
So you only want to carry this management vlan to both switches? Currently they both carry different vlans via their uplinks to pfsense?
What I would do is connect the switches together for only this network/vlan and uplink that via 1 of the switches to pfsense.
-
Currently they both carry different vlans via their uplinks to pfsense? Yep that was previous situation.
And yep I do have a limmited number of vlan's in a trunk between the two switches. But for the essential management vlan, I did not like that.
Note that the bridge I implemented does work as intended! I just do not understand the IMHO crazy way it is implemented !!