Captiv portal and vouchers integration with ssid on wlc 9800
-
Nice.
Your "cat /tmp/rules.debug | grep cpzoneid" shows how the portal works.This :
ether pass on { igb3.10 } tag "cpzoneid_2_rdr"tags all the packets coming into your portal interface with "cpzoneid_2_rdr".
This is the magic :
rdr on igb3.10 inet proto tcp from any to ! <cpzoneid_2_cpips> port 80 tagged cpzoneid_2_rdr -> 192.168.200.1 port 8002I read this as follows:
For the "tagged cpzoneid_2_rdr" tagged traffic do this :
Redirect (rdr) TCP traffic from anybody (all the devices on the portal network) with a destination that is not <cpzoneid_2_cpips> (= the pfSense captive portal interface IP or 192.168.200.1) to the portal interface (= the pfSense captive portal interface IP or 192.168.200.1) port 8002 (where 8002 is the http - not https - captive portal web server) as seen here :@Jozy said in [Captiv portal and vouchers integration with ssid on wlc 9800](/post/1196793): > tcp6 0 0 *.8003 . LISTEN > tcp4 0 0 *.8003 . LISTEN > tcp6 0 0 *.8002 . LISTEN > tcp4 0 0 *.8002 . LISTENwhere port 8002 is used for "http" and port 8003 is the "https" interface;
Btw : https is used when
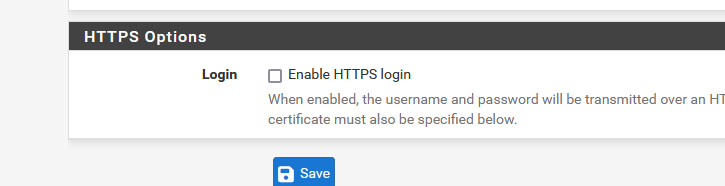
is checked.Be ware, using https means you have to use a certificate that and portal user trusts ( !! ).
It might still work, with the classic browser warning that tells you you use a self signed certificate (and not trusted).Extra info :
See the nginx portal web server config file which is called something like :
/var/etc/nginx-cpzone1-CaptivePortal.confIn the "server" block, you see how redirecting is applied.
This works because :
When an Ethernet connection is created, first, the DHCP client does it's work.
When done, the network client has an IP, a gateway, a DNS and a network (mask).
If I take the example of @johnpoz this would be :
IP : 192.168.200.1
DNS 192.168.100.1 ( !! so pfSense is the 'DNS' for the assigned captive portal network clients)
Gateway : 192.168.200.1 ( !! )
Network : 255.255.255.0 or /24And now the real magic kicksz in : every device, actuall : every OS, as soon as a ethernet connection comues up, fires up a https request.
For an Apple device, this http (not / never https !) will be :
http://captive.apple.com/hotspot-detect.html
Click on it to see what is happens.
It should return a 6 letter "html page" showing just "Success".
If this is not the case, the presence of a captive portal is suspected.
The device will open up a web browser (or show a notification to the user somewhere) and it will visit the same link again http://captive.apple.com/hotspot-detect.html and time, as this is a browser request : a classic http = port 80 request, it will get redirected to the 192.168.200.1 IP - port 8002, and you'll be able see what happens.And what will show up ? Our login portal !
Another info page : See here : Status > System Logs > System GUI Service
where you can see the https requests from the captive portal web server. -
@Gertjan nice write up..
@Jozy you could always just have the wlc do the captive portal as well, the one reason I could see having pfsense doing it is if you also had wired devices on this same network that you wanted to have to use the captive portal as well.
Personally I have little use for captive portal.. For my guests that want to use my guest wifi network I just hand them a card with a qr code on it to get them on the network.. They would hate how long and complex the psk is to type in ;) hehehe
They really only make sense when you need to time limit someones access, or have them pay for access, or can not in anyway just let them know the psk, etc. There are plenty of use cases where it makes sense, but in a home or smb sort of setup not really.
-
@johnpoz said in Captiv portal and vouchers integration with ssid on wlc 9800:
I could see having pfsense doing it is if you also had wired devices on this same network that you wanted to have to use the captive portal as well.
Actually, wireless or wired devices, it's all the same.
After all, captive portal support is mostly handled by the connecting device, not the router/firewall, like pfSense. -
@Gertjan my point was if all he has was wireless devices he wanted on it he could just use the wlc.. Not sure how the wlc would work for wired device on the same vlan as the wifi?
-
@johnpoz
I really dont know what the exact issue is here.
Customer is looking for voucher on Guest SSID and it should be setup but now this is not working. :( -
@Jozy said in Captiv portal and vouchers integration with ssid on wlc 9800:
Customer is looking for voucher on Guest SSID
What do you man by that ? The customer doesn't have a voucher ? He lost it ?
Or do you mean : he doesn't know what to do with it ?
Or does the login screen not show up ?Normally, when installing a captive portal, set up one without any "users" or "vouchers", just this :
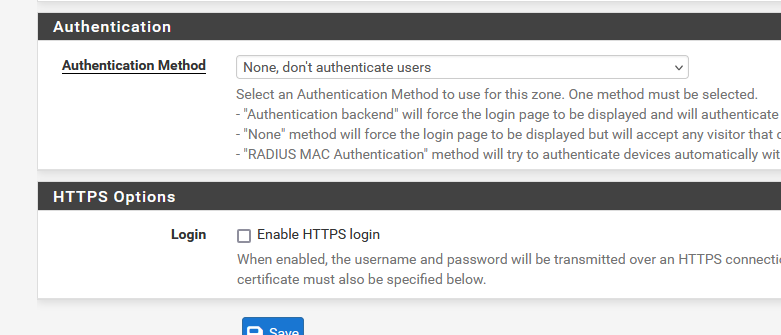
and make sure everything works first.
This 'everything' is actually a lot already.See also here for help : Troubleshooting Captive Portal
@Jozy said in Captiv portal and vouchers integration with ssid on wlc 9800:
but now this is not working.
It worked before ?
-
@Gertjan No, Im trying to configure it first locally at my company environment, then provide it to the customer, since they are looking for that solution.
Anyway, after configuring CaptivPortal, what URL should I use to get CaptivPortal, since port 80 should redirect me to CP but not working.
-
@Jozy said in Captiv portal and vouchers integration with ssid on wlc 9800:
Anyway, after configuring CaptivPortal, what URL
Initially, None.
When set up correctly, a confection device is redirected to the captive portal login page. This user will never know - and doesn't need to know the port (8002, or up) used.Later on, you will want to use https login, as it look 'better' ( and nothing is really http based anymore ).
Then you will have to deal with a domain name, certificates and so on. That is the moment a host name (URL) is mandatory, like "portal.your-domain.tld".
The portal user doesn't have to know this host name (URL) is he will get redirected to it automatically.There are a couple of captive portal videos here https://www.youtube.com/@NetgateOfficial/videos - they are old but still very valid.
-
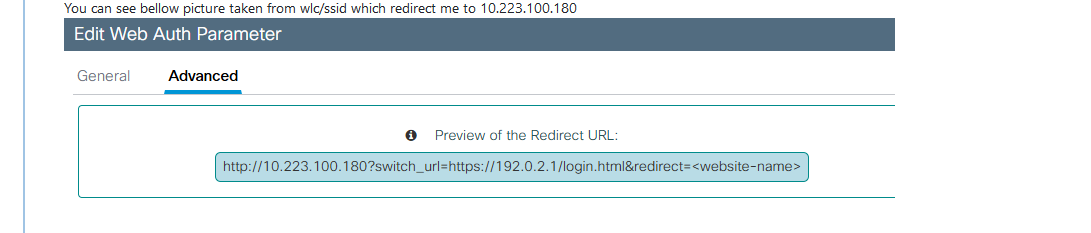
@Gertjan Something which is very interesting i that I can access to pfsense as you can see bellow
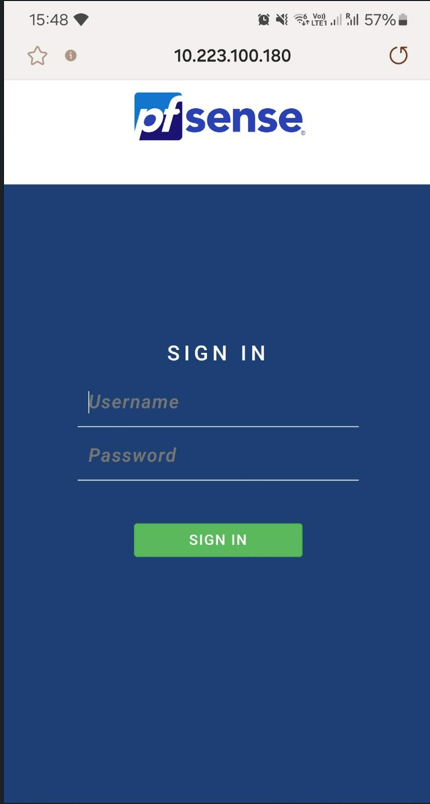
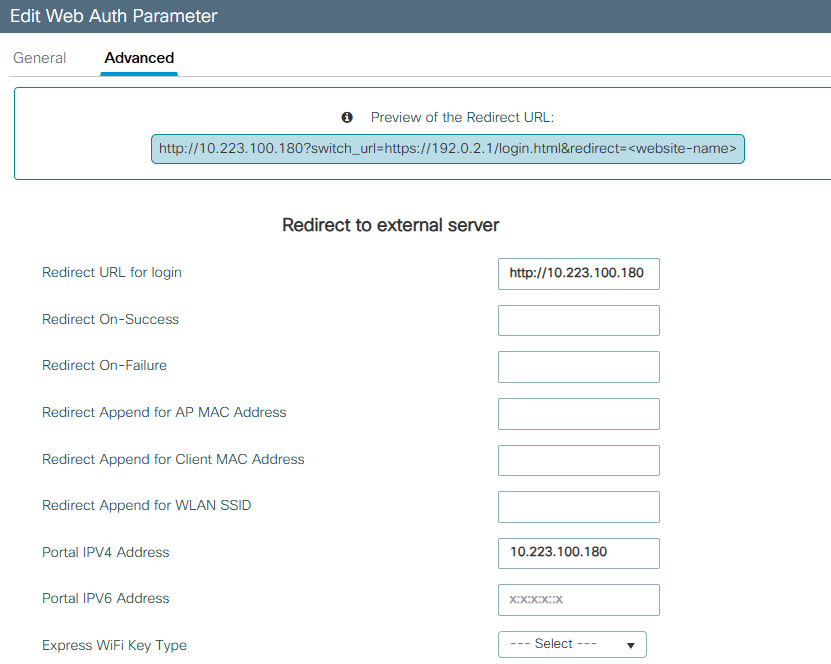
but I should be redirected to captive portal not pfsense page.
After page appear I can easily type username and password of the pfsense and get in which is not something I want.You can see bellow picture taken from wlc/ssid which redirect me to 10.223.100.180
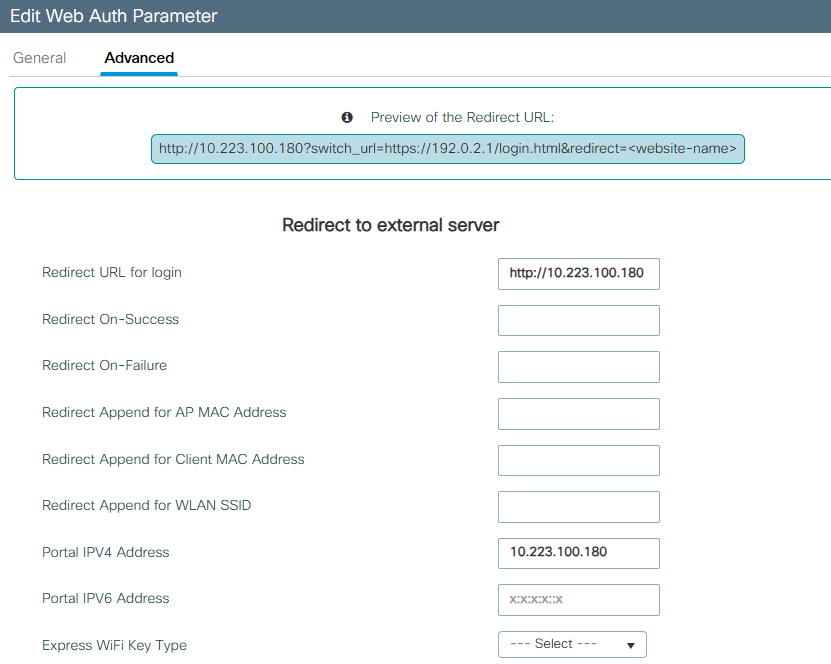
Why redirection to captive portal not working it is weird or should I use some other "redirect URL for login" on wlc?
Anyway I have enable captiv portal and voucher and not working. Can it be some bug on software since Im using it on VMware or?
-
What is thsi :
Are you using some sort of captive portal behind another captive portal ?
Just use 'simple' access points, and it will work ?!
-
@Gertjan its virtual ip address configured on wlc, with or without that address it is the same end.
What do you mean saying "simple" access point?
What would be that simple access point?
-
These, I guess.
I mention these as they work fine for me, I use them. -
@Gertjan Unfortunately I have Cisco wlc and have to try setup it with that one :)
-
TO set up the captive portal, do as the doc and videos tell you.
You don't need any access point or whatever. A captive portal with wired device will also work just fine.
Hook up a dumb switch into the captive portal interface, and hook up a laptop or a desktop PC into the switch.
Now you have everything you need to make it work.When then pfSEnse captive portal works, only then you start to use the "wlc 9800".
If at that moment the captive portal stops working, call Cisco ; -
@Gertjan Captiv Portal is working now. Problem was with WAN interface and DNS forwarder.
Best regards,
Jozy -
@Gertjan @johnpoz Hi guys, here I am again.
So, if you know or had the similar situation.As I mentioned above Captive Portal is working fine, but only working when Im connected to the same network not when enable wifi adapter.
When I try to reach CP while trying to connect to wifi it isnt reachable.
I have Cisco WLC configured and redirections to http://10.223.103.230:8002/index.php?zone=CaptivPortal& which is Captiv Portal it isnt working.
Whan I try to paste http://10.223.103.230:8002/index.php?zone=CaptivPortal&?switch_url=https://192.0.2.1/login.html&redirect=<website-name> while using the same network (10.223.103.58) it is working fine.
I have to monition that 10.223.103.x is wifi subnet.Problem starts when I try to reach Captiv portal while trying to enable wifi adapter and test SSID on both cell phone or PC not working, it doesnt redirects me to nowhere, I just get ip adress over DHCP which is configure on win server and other setup but CP not opening.
Do you know what could be the problem?
Best regards,
Jozy -
@Jozy said in Captiv portal and vouchers integration with ssid on wlc 9800:
I have Cisco WLC configured and redirections to http://10.223.103.230:8002/index.php?zone
You shouldn't be doing anything with captive portal on your wlc if you want pfsense to handle it - if your wifi devices are on a different network then on that network in pfsense setup the captive portal.
-
@johnpoz How should I reach Captiv portal over wifi if I dont put on SSID on WLC redirects me to http://10.223.103.230:8002/index.php?zone=CaptivPortal& ?
-
@Jozy your wifi should just connect your wifi to a wired network on pfsense. No captive portal in your wlc - just setup a ssid, and have your clients connect..
Their dhcp should come from pfsense. On whatever network this is - setup pfsense captive portal on that network.
-
@johnpoz I have wlc where all access points are added and managed by wlc.
So, what would be right setup? Since it is virtual macine where L3 interface would be, on my network l3 router?
For example if I have range 10.223.103.0 for dhcp, lan adress on pfsense it 10.223.103.10
Anyway I have to configure l3 and vlan on trunk and wlc to have access to that dhcp, once I try establish connection over ssid, right?
In that case i should configure Lan ip address as my dhcp relay, right?Jozy