Rule Block traffic from port 0
-
It is a very interesting situation with rule Block traffic from port 0.
I have firewall log like Block traffic from port 0 (1000000107).
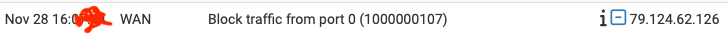
I add this IP address to the aliases and then add a WAN rule to DROP this IP address without logging but I still have this IP address in the log file with the new entries.
This method usually works.Can anyone tell me why it doesn't work?
-
@WhoAmI68 there is a hidden rule that blocks such traffic
cat /temp/rules.debug
# We use the mighty pf, we cannot be fooled. block quick inet proto { tcp, udp } from any port = 0 to any ridentifier 1000000114 label "Block traffic from port 0" block quick inet proto { tcp, udp } from any to any port = 0 ridentifier 1000000115 label "Block traffic to port 0" block quick inet6 proto { tcp, udp } from any port = 0 to any ridentifier 1000000116 label "Block traffic from port 0" block quick inet6 proto { tcp, udp } from any to any port = 0 ridentifier 1000000117 label "Block traffic to port 0"You have block default I would assume, I don't have that set and notice those rules don't have log set.. One way to not log such rules is turn off log default block, then create rules of what you want logged.
edit: if I toggle that to log default, then it does
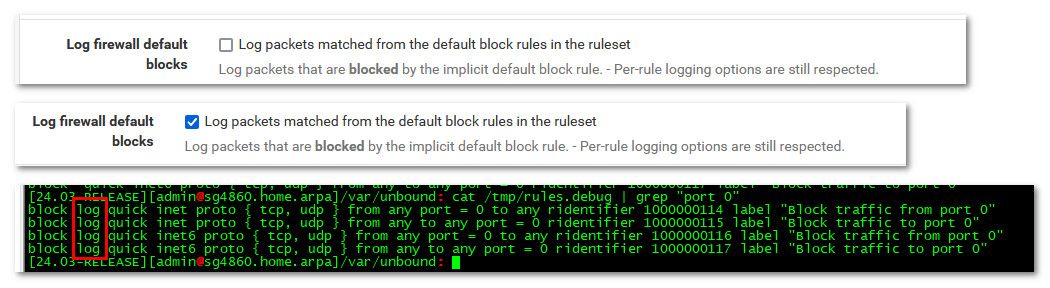
the only thing that seems weird is your rid, yours is 107, when believe the default is 11x - but maybe that has something to do with version or something else like number of interfaces?
But yeah if you log default block, your rules to not log would be after the hidden rules.
-
@johnpoz said in Rule Block traffic from port 0:
You have block default I would assume, I don't have that set and notice those rules don't have log set.. One way to not log such rules is turn off log default block, then create rules of what you want logged.
I know about turn off default log but that's not the way.
I explain what I want to achieve. For exmaple, If some crazy bot is doing 2000 scans a day for about 2 to 4 days so Usually I add this IP address to aliases and set firewall rules to DROP on the WAN without any logging, as a result of which I have clear log file. It is working for this rule Default deny rule IPv4 (1000000103) but not for this one Block traffic from port 0 (1000000107).@johnpoz said in Rule Block traffic from port 0:
the only thing that seems weird is your rid, yours is 107, when believe the default is 11x - but maybe that has something to do with version or something else like number of interfaces?
Maybe be, i do not know. I use Pfsense+ 24.11-RELEASE
-
@WhoAmI68 said in Rule Block traffic from port 0:
It is working for this rule Default deny rule IPv4 (1000000103) but not for this one Block traffic from port 0 (1000000107).
Because of the order of the rules.. Look at the full ruleset
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html#viewing-the-pf-ruleset
If you do not want the noise.. Again turn off default logging, create your own rules to log what you want. Then you can put a rule in not to log specific IPs if they are generating noise with your rule that you do not want to see.
-
@johnpoz Ok, thanks.