Sharing my Wireguard S2S VPN configuration
-
I've created HA S2S Wireguard VPN configuration between pairs of HA'ed pfSense's HA on each side.
pfSense HA must be setup and work also CARP default gateways must be setup for all pfSense interfaces.WG Peers:
Site_1
pfSense1 HA paired with pfSense2- pfSense-1 == wg_tun0 ==> pfSense-3 [Tier1]
- pfSense-1 == wg_tun1 ==> pfSense-4 [Tier2]
- pfSense-2 == wg_tun0 ==> pfSense-3 [Tier1]
- pfSense-2 == wg_tun1 ==> pfSense-4 [Tier2]
Site_2
pfSense3 HA paired with pfSense4- pfSense-3 == wg_tun0 ==> pfSense-1 [Tier1]
- pfSense-3 == wg_tun1 ==> pfSense-2 [Tier2]
- pfSense-4 == wg_tun0 ==> pfSense-1 [Tier1]
- pfSense-4 == wg_tun1 ==> pfSense-2 [Tier2]
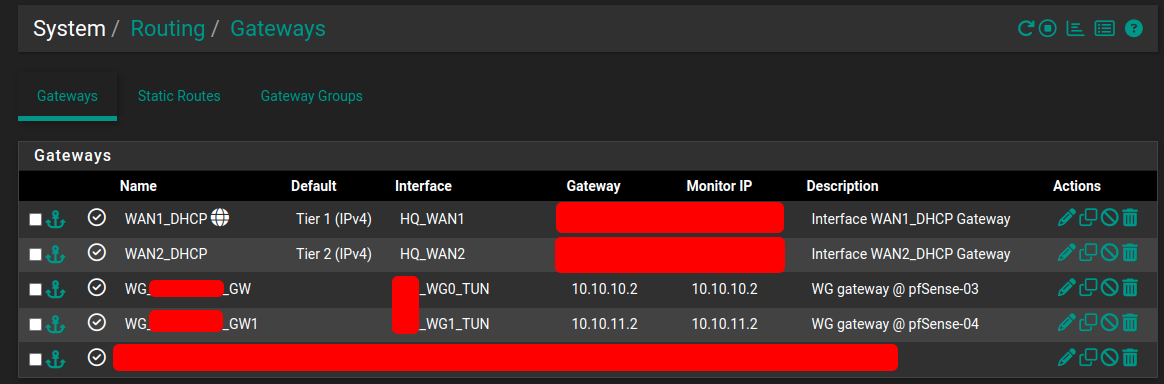
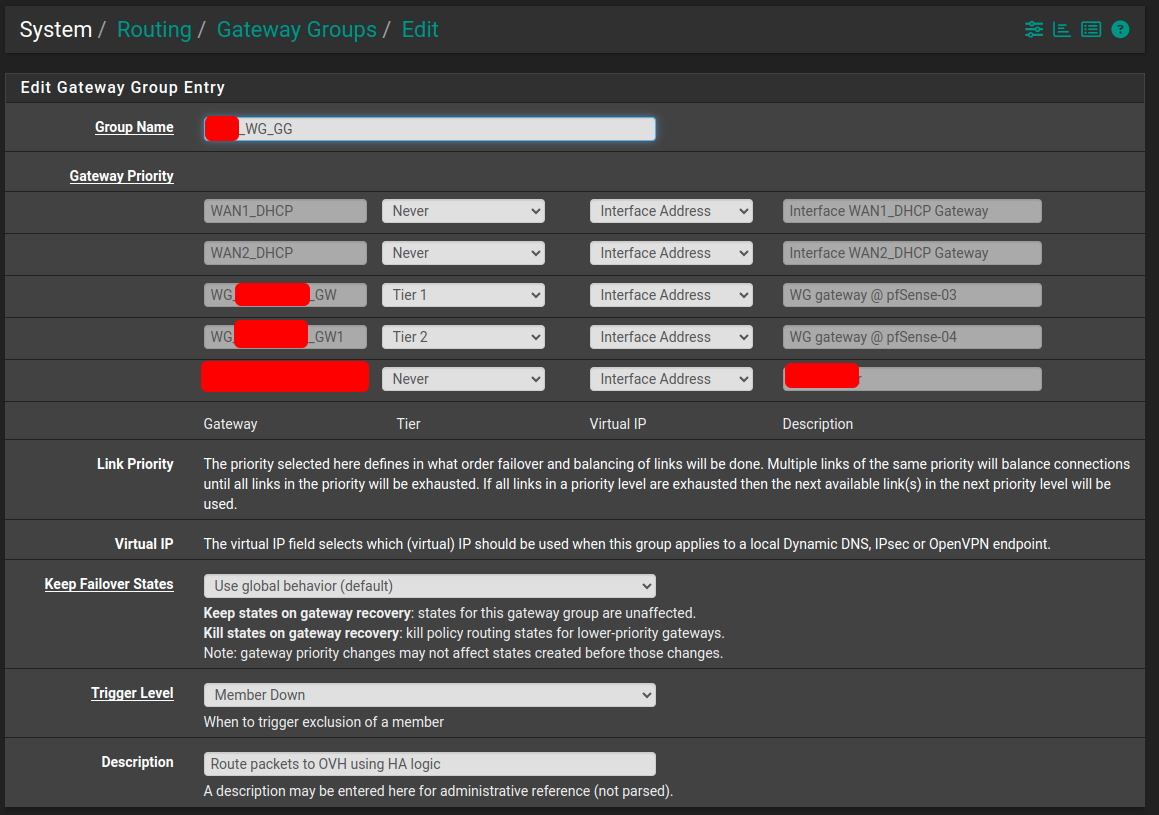
Each pfSense has two Wireguard gateways in a gateway group (see the tiers setup above)
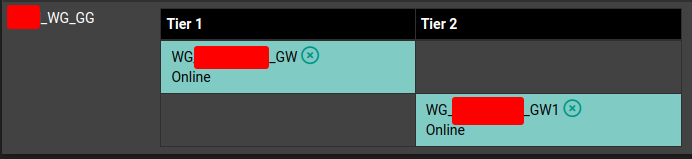
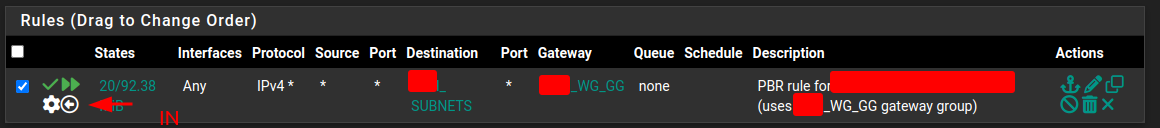
pfSense static routes don't allow using gateway groups as gateways - therefore each firewall has one floating rule, forwarding traffic to another site's subnets (listed in an alias) through above wireguard gateway group.
It works great - i.e. connection between sites survives, if there at least one firewall left on each side. Switching is almost instant - if Tier1 gateway goes down - all new connections are routed through Tier2 gateway. The only one issue(or feature?) - firewalls themselves can't talk to their counterparts at another site. I guess it's because floating rules do not include localhost interface.So far I don't know how to solve this. Any ideas how to do that?
-
Hi,
I'm trying to setup the same HAtoHA setup with 3 sites.
Basic setup is working fine, so pf1 to pf3 in your example.It's not clear to me how you setup the site-to-site tunnels including pf2 and pf4.
You cannot assign the same subnet on different interfaces so I didn't get how you manage the subnets.
May I ask you to elaborate a bit more about Assigned Interfaces, IP and gateways? I would be really handy.For the routing I'd use the same policy routing on each interface. It seems to be more specific and you can use the gateway group as well.
It doesn't solve your issue though, sorry.thanks
-
Interfaces: pfSense1
Each WG tunnel uses own /24 network - i.e. 10.10.10.0/24 and 10.10.11.0/24
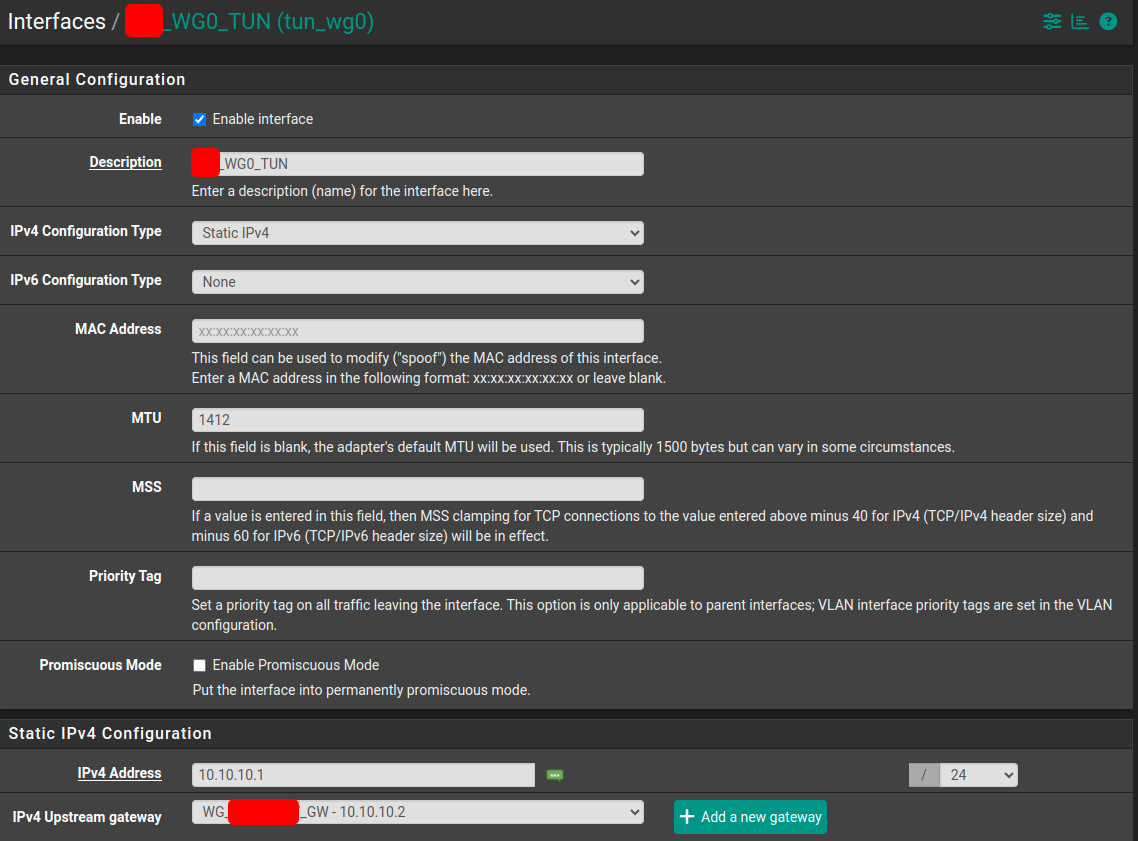
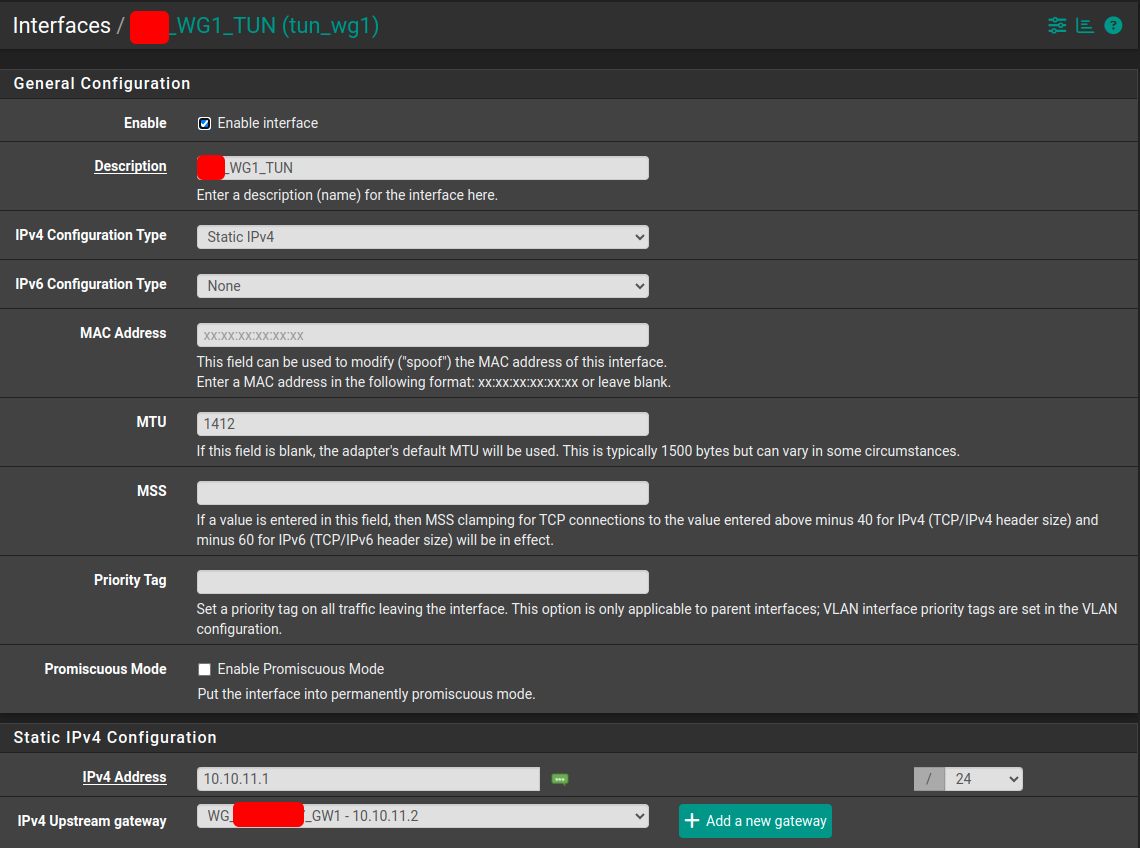
Wireguard Tunnels and peers (status screen)
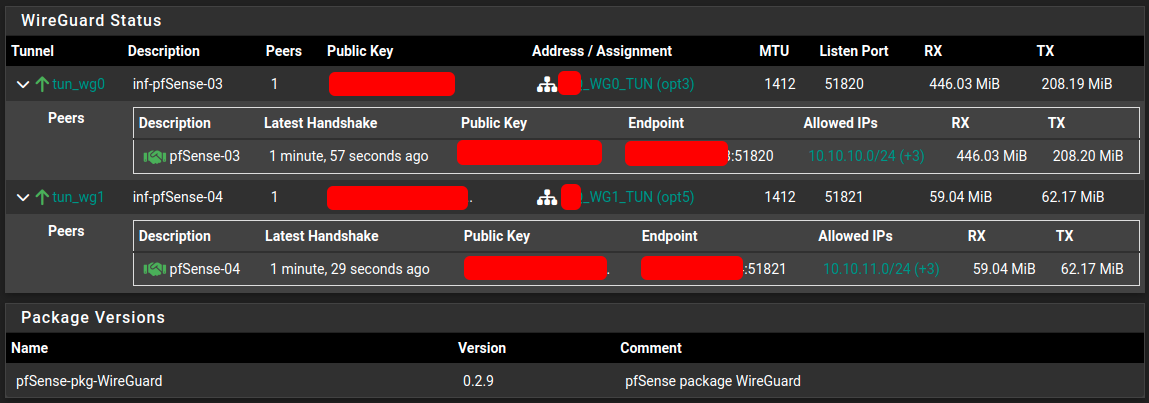
pfSense1 Gateways
**pfSense1 Wireguard Gateway group **
Wireguard Status pfSense1 (left) vs. pfSense3 (right)
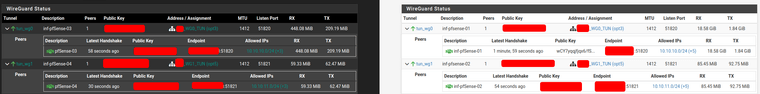
Wireguard Status pfSense2 (left) vs. pfSense4 (right)
-
@CapitanBlack Thank you! that's is what I needed.
I didn't realize I could assign the same IP on pf1 and pf2 wg interfaces.
Now I need to test the failover.