SSL Certifications Not Trusted On My System
-
Greetings all,
I've searched throughout this forum for my answer, though I'm most likely not looking in the right place. For about a month now, I've been learning and configuring pfSense for my host PC. For the most part, I understand it. Unfortunately, as the title states, the certs won't trust. I'm not sure what I'm missing in all honesty. I've used both Let's Encrypt and ZeroSSL for my certificates, with both stating that the certificates are in good standing and aren't having any issues. Not only that, but I'm not hosting pfSense via a web server, either. Furthermore, I'm merely hosting it via VMware. I've entered the Certificate Authority for ZeroSSL, my current provider, alongside the certificate granted via ZeroSSL. To add to this, I'm wanting to use a domain instead of needing to utilize the WAN IP Address. I do have a domain via Namecheap and has DNS via Cloudflare, but proxying is turned off. At this point, I'm stuck. If I put this in the incorrect category, I do apologize. I'll try to answer as soon as I can.
Best,
Salem
-
@Sawami648 said in SSL Certifications Not Trusted On My System:
to utilize the WAN IP Address.
You mean the LAN address, as the pfSense web server GUI is accesible on LAN, not on WAN.
On WAN, nothing should be accessible (security !!)@Sawami648 said in SSL Certifications Not Trusted On My System:
I've entered the Certificate Authority for ZeroSSL
They gave you a certificate ?
You put it where ?@Sawami648 said in SSL Certifications Not Trusted On My System:
I've used both Let's Encrypt and ZeroSSL for my certificates
Both ? Why ?
( I don't get it I guess )What are you trying to do ?
@Sawami648 said in SSL Certifications Not Trusted On My System:
but I'm not hosting pfSense via a web server
pfSense is a system OS, like Windows, Linux, MacOS or FreeBSD, not a web app.
True, pfSense uses a web server, as your AP, printer, NAS, and ISP router to access its parameters.
If you want to use https to access this web server, you can activate a trusted certificate here :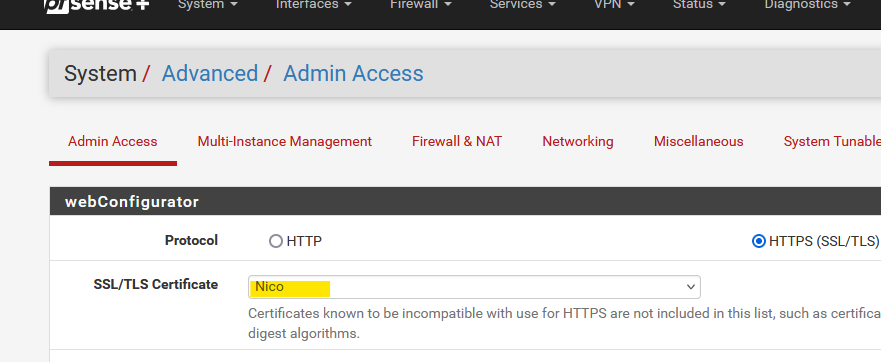
This certificate should be present on the System > Certificates > Certificates page.
For me, the acme pfSense package did that for me.
I've set up the acme pfSense package, as I have a domain name that I use for my pfSense domain :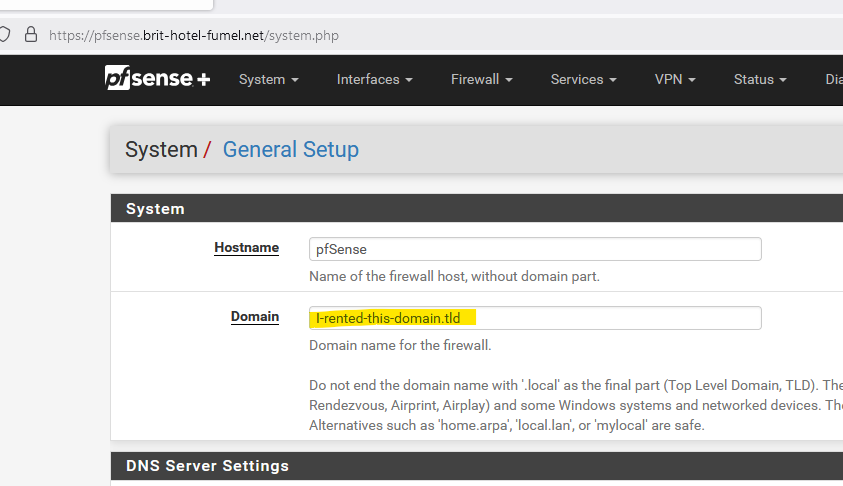
ZeroSSL, Letsencrypt, Cloudflare, Namecheap, VMware ... wow, is it possible to make this even more complex ^^
-
I appreciate your quick response. Yes, I meant LAN. It's late for me, so I'm not as sharp, unfortunately. ZeroSSL gave me a certificate and I installed it via the Certificates' menu within System. As for the Let's Encrypt and ZeroSSL, I realize I could've worded that better. I meant that I've tried both services to see if it was potentially either one that was causing issues. As for the SSL/TLS certificate, I've already put the certificate in the dropdown box, and specified to use HTTPS instead of HTTP. Unfortunately, it still isn't trusted via my browser. Even after placing said certificates in the trusted store authorities group. I do apologize for making it overly complex, I'm just not entirely sure where to go for support on this. I strive to be as in-depth as possible. For example, clicking the "lock" icon within Edge, it states that my certificate is not valid for the site. With that mentioned, I'm honestly open to any solutions at this point.
-
So, you should have something like this :
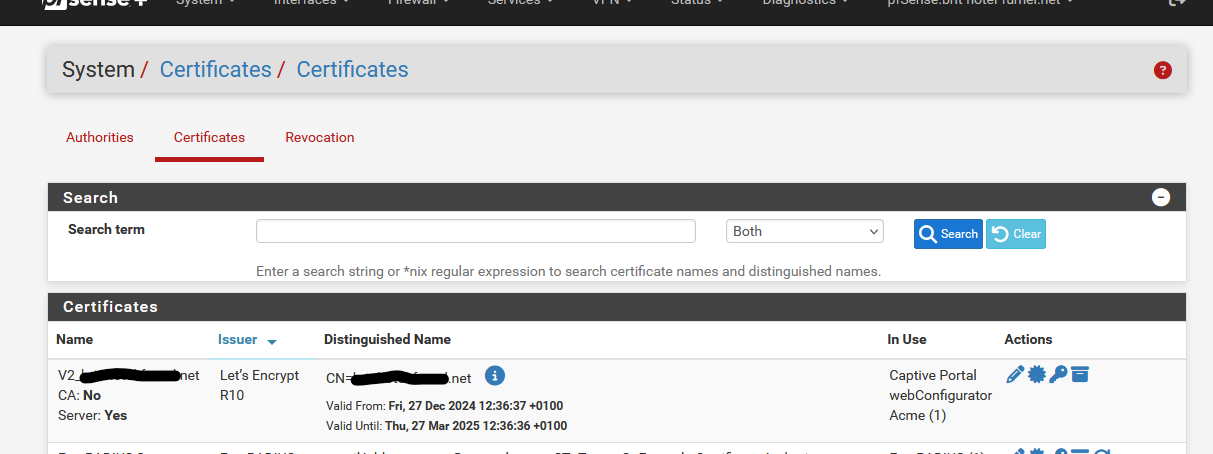
Let'sencrypt signed it, using their intermediate "R10" and their CA. Here you have it :
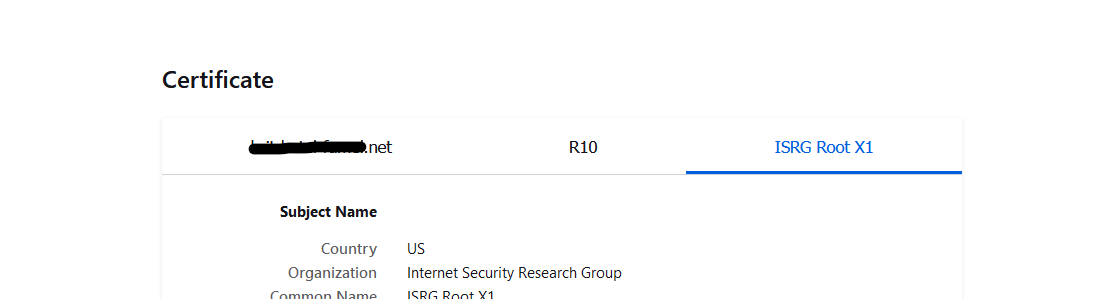
and as "ISRG Root X1" is trusted by every device on planet earth, my certificate is also trusted.
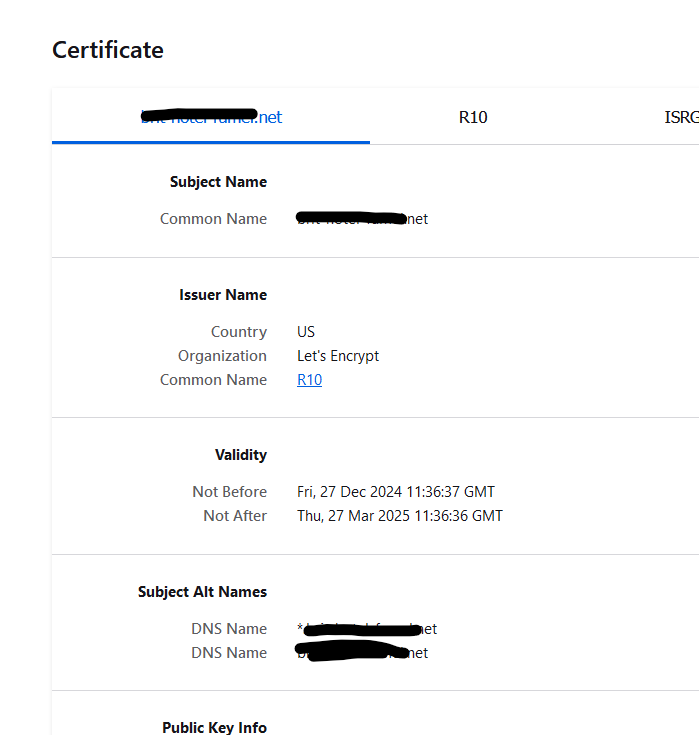
what I've barred out stands for :
What is the reason why your certificate is not trusted ?
-
@Sawami648 what fqdn is your cert for.. How are you accessing pfsense gui?
If the fqdn does not match you will get an error, or if you access via local IP you will get an error the name doesn't match..
If your cert is for say pfsense.publicdomain.tld and you access with say pfsense.home.arpa that would fail.. If you access via 192.168.1.1 that would fail, etc.
Also you mention you tell your browser to trust the cert - doesn't work that way, you need to have the CA of who signed the cert trusted by your browser.. But doesn't matter if your browser trusts the CA or not, if the CN or SAN of the cert doesn't match up with how your accessing it be it fqdn or an IP.
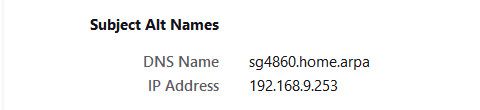
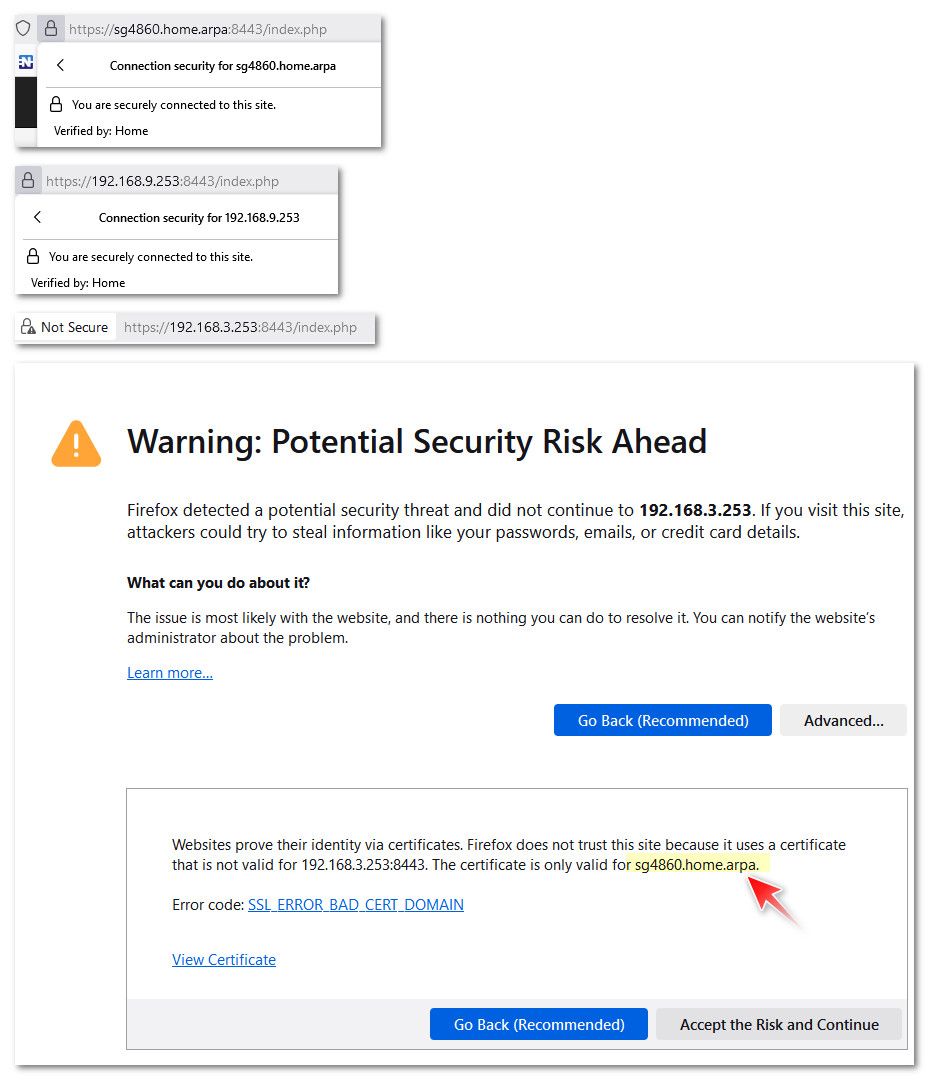
Example my pfsense name is sg4860.home.arpa - see if I access with that name or even IP.. It is trusted because the CN matches, and the SAN also has the 192.168.9.253 IP in it.. But notice it fails if I access it with another IP on pfsense 192.168.3.253
Here is examples of it working with that fqdn or the 192.168.9.253 IP, and the error the browser gives me if access with something that doesn't match up with the cert.
I just created my own CA in pfsense and signed cert pfsense uses for its web gui, and my browser trusts this CA, which is why able to use non puplic domain, and rfc1918 Ips in the cert.
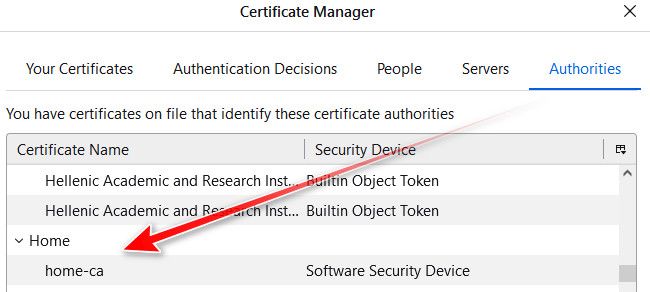
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-