Is UPnP the reason my games don't work?
-
@Uglybrian I followed the UPnP guide from the docs, that's where I got my original configuration from: enable UPnP, no STUN because my WAN interface has a public IP, and enable static port for the outbound NAT rule. The 22325 is not in my alias, so I added it, but I still see the blocked requests and no active UPnP rules :(
I also checked if it was the pfBlockerNG rules, but they don't change anything
-
@semtex99 With UPnP enabled you shouldn't have to set static port, it should work with Outbound NAT in Auto settings. If you play CoD you should see port 3074 show up in the UPnP status page, and probably 28960 as well.
You should not have to add any pass rules for the UPnP ports. You selected the OPT2 interface so that is what it is listening to.You also have an awful lot of rules btw... What is it that you are trying to achieve... why do you have to "allow" pinging 8.8.8.8 for example. Or any of the other allow rules for various thing?
Normally when you have multiple networks, VLAN or using physical ports like you do, you may have general block rules to limit access between them. But if you are ok with OPT2 reaching LAN and OPT1 and reverse, then all you need is one single allow OPT2 to any rule at the bottom, that's it.
And since that one rule is missing, unless you add rules for all the ports that you may or may not need, you will have it blocked by the default rule...IF you run something like PiHole on LAN and want OPT2 devices to use that, yes then you can add a rule sending 53 to the PiHole IP. However, if you use pfsense as DNS, there is no need to add a rule for DNS. It's already the default setting in the resolver (or forwarder), so it will listen and respond on OPT2 already.
The rules to allow from OPT1 and LAN have no effect when placed under OPT2 rules. They need to be under their respective interface ruleset. See the 0/0 B on the left...My guess is that if you cleared up and simplified your rules, a lot, you will get UPnP working fine. Start by putting an allow OPT2 to any rule, just under the pfBlocker rules.
-
@Gblenn Thank you for the detailed explaination! I think you're right, and my initial understanding of how to go about rules was the wrong way around.
My understanding was that it would be considered "unsafe" to allow a pass from OPT2 to any rule, because I read a comment on reddit where someone said that would defeat the purpose of the firewall because it would undo the default deny behaviour. This was how I figured rules should work: deny anything by default and only explicitly allow things you need.
If you say that's better to allow a pass from OPT2 to any rule then that would indeed solve my problem! As i've tried that and that makes it work, but I was under the understanding that it would be bad practice.
To summarize, your advice would be to add a pass from OPT2 to any rule, and then add more rules that block requests below it to fit my needs, instead of what I have now, which is the other way around by going with the default deny behaviour and adding rules for things I want to allow?
-
As an example here is a simplified rule set I use for my iot network.
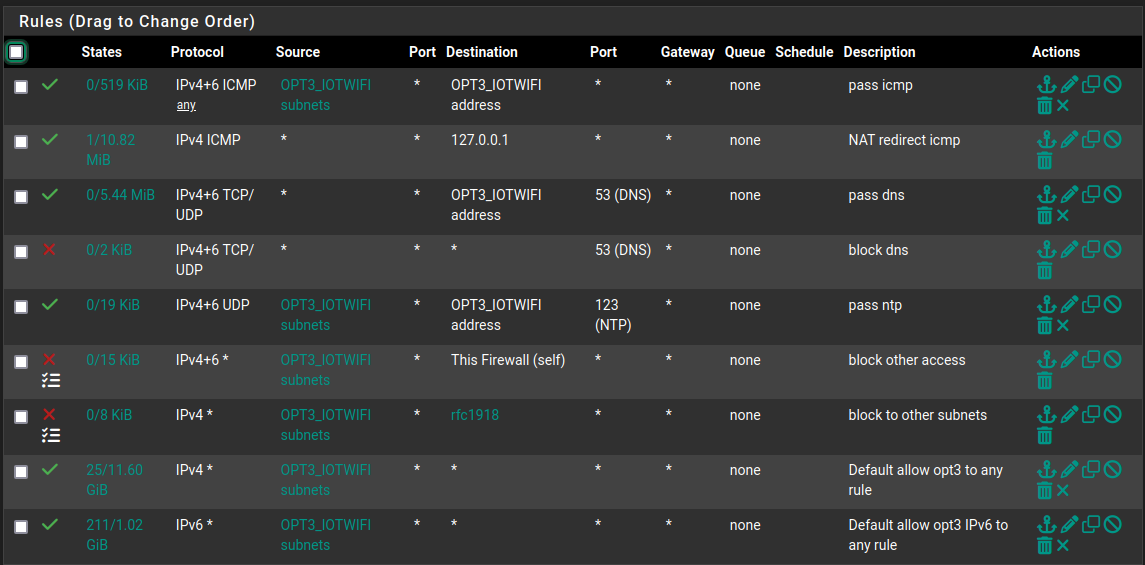
-
@semtex99 said in Is UPnP the reason my games don't work?:
considered "unsafe" to allow a pass from OPT2 to any rule, because I read a comment on reddit where someone said that would defeat the purpose of the firewall because it would undo the default deny behaviour.
Caution reading Reddit. You will tend to get better help here than Reddit.
LAN is born with a default any:any rule. This is outbound. The main purpose of a home firewall is to prevent access in, not out.I suggest you think of your total rules set in the terms of "Outbound block what I want blocked, allow all else." "Inbound, block it all unless I have a reason."
-
@AndyRH @Uglybrian Thanks for the advice! I cleaned up my rules a lot and now have this:

And now the games do in fact seem to be working! Any other things I should consider?Thank you all very much!
-
@semtex99 Looks better now, but there are a few things you might want to consider...
The first rule doesn't do anything since traffic with source and destination OPT2, will not go into pfsense, therefore the 0/0. So remove this rule...
Second rule is your key to getting devices use PiHole so this is good. It's your "policy routing" sending all DNS requests to your PiHole, and then stops processing anothing port "53", perfect!
Third rule doesn't do anything since the second rule already took care of things, remove this.
What is it with SSH that you are trying to block, or protect? Allowing SSH to LAN and OPT1 is catered for by the last, allow to any rule. And a device SSHing from an OPT2 device to another device on OPT2 wouldn't hit the firewall...
Still there seems to be some traffic hitting this Block rule so is there something trying to access something on WAN perhaps? If you want to block that speficially, then change the block rule to have Destination WAN and port 22. And just remove the two Allow SSH rules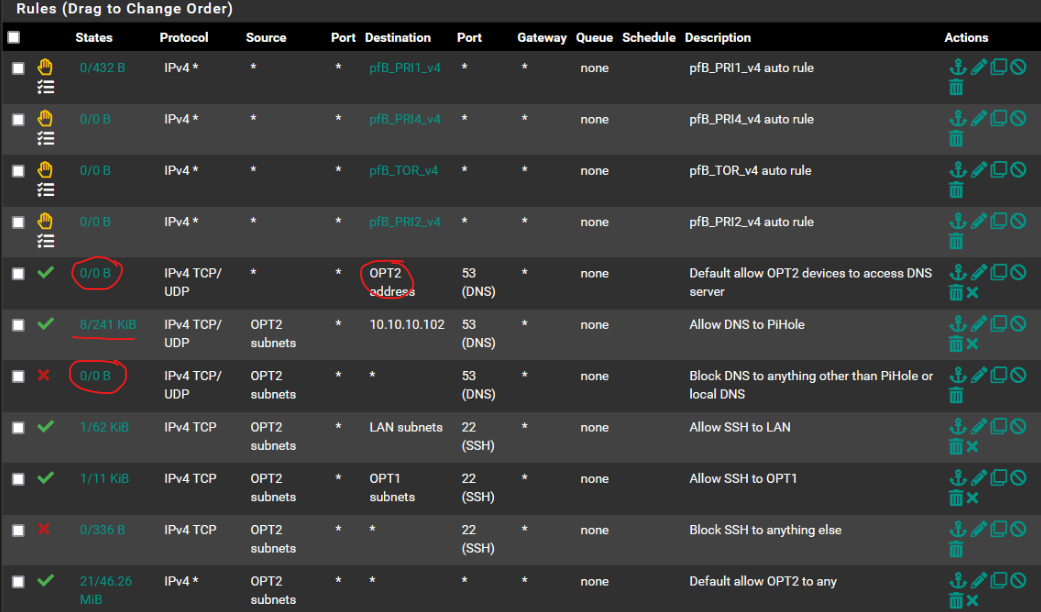
-
@Gblenn Great! I've simplified it even more:

The traffic hitting the block SSH rule was me testing SSH access when I had set the other two rules to OPT2 address by mistake. I want to block SSH access to any destination that isn't in my network, just as a precaution.I think I now understand a bit how the rules are processed. I first thought that any requests that don't hit a specific rule just go down through the rules until it finds one that matches, that's why I had the other block DNS rule: I thought that if a request did not get passed by the pihole rule, it would go through until it hit the allow any rule, and thus be passed. But with your explanation it seems that all traffic with destination port 53 will be blocked if it doesn't meet the requirements for the pihole rule for port 53, and thus won't get processed through the other rules right? Because that rule handles port 53; after it gets blocked by that rule, it isn't processed by any other rules?
-
@semtex99 Yes now it's way simpler and still achieving what you want.
Some thoughts and considerations however...
First of all, without any rule at all under e.g. OPT2, you would still have the default block rule, which blocks EVERYTHING. You don't see it, but it's there...
And this is why we start by adding the "default allow OPT2 to any" rule. It was that default block rule creating problems for you earlier... What CAN work is to start creating allow rules for specific things but, as you have seen already, it makes for a ton of rules and gets complicated very quickly.
And since like @AndyRH said, the LAN side is normally where we want to allow things, it's simpler to start by adding that allow OPT2 to any rule.Now, about the DNS rule though... I'm guessing you have set your PiHole as the DNS for all devices in OPT2, which is done using it's IP, similar to what I have here (in my DHCP Server settings)?
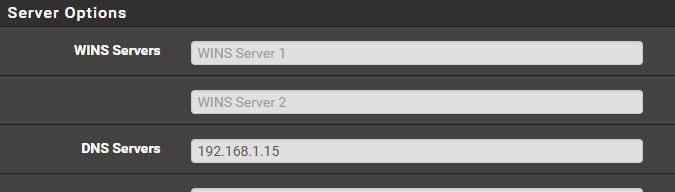
Since you have the allow all rule at the bottom, this will still work, so that rule is sort of redundant. BUT, before you remove it, perhaps you need to consider what your goal is with having three separate networks, LAN, OPT1 and OPT2.
If there are some thoughts about security in this split you have done, then a next step would be to start thinking about what limitations you want to put on each segment. As I wrote earlier, it's common to block communication between segments. It's sort of why we introduce them, like perhaps wifi, IoT/Camera subnets etc. So if we assume OPT2 is used for all your wifi and OPT1 for Cameras and smart devices, you may want to consider two blocking rules in each of those rule sets. Two each because you want to block access to the other two, like LAN and OPT1 from OPT2.
For example, here are the rules in my wifi segment (VLAN) that I have. I do a general blocking of access to any of the other segments from wifi. And then I have allow rules for access only to specific targets like my AdGuard Home server (like PiHole) as well as Chromecast above them. Without those blocking rules, I wouldn't need the allow rules, since the allow all exists at the bottom...
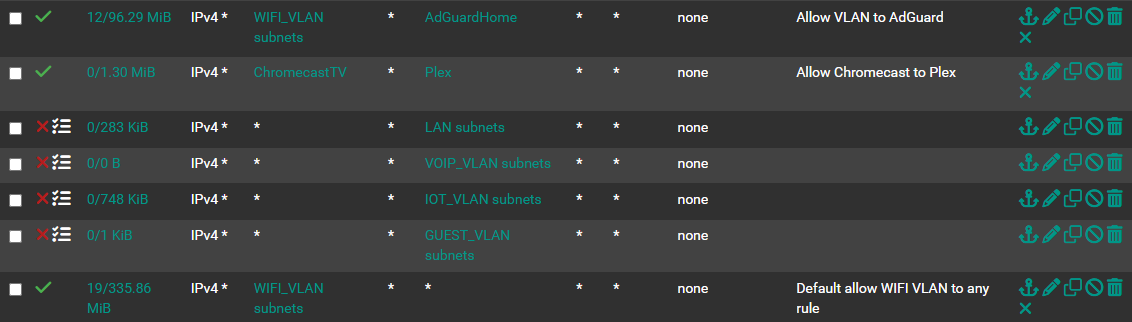
If you have a printer that is connected over wifi, and want to print from a LAN connected PC, you probably need to look at adding the Avahi package. And set it up so that it targets LAN and OPT2 in your case. Perhaps even specify the IP in the printer settings on the LAN connected PC(s).
-
@semtex99 In addition to the rules discussion, there is the gaming aspect...
First of all, you mentioned you have your PC connected over wifi, which isn't an optimal solution. I'd look for ways to connect via cable, but sometimes that's of course not possible, or too difficult.
Although what I said about not needing Static Ports for UPnP to work, it may still be beneficial... I have noticed that it speeds up launching of some games a little bit. Probably since it simplifies some of the negotiations that the games need to make with the servers, about which ports to use.
pfsense will typically give you what's called Symmetric NAT but changing to static ports, you get Port Restricted Cone NAT. You can test it with this tool : https://www.checkmynat.com/. And the rule you used makes sure it only applies to your gaming devices that you put in that alias "games".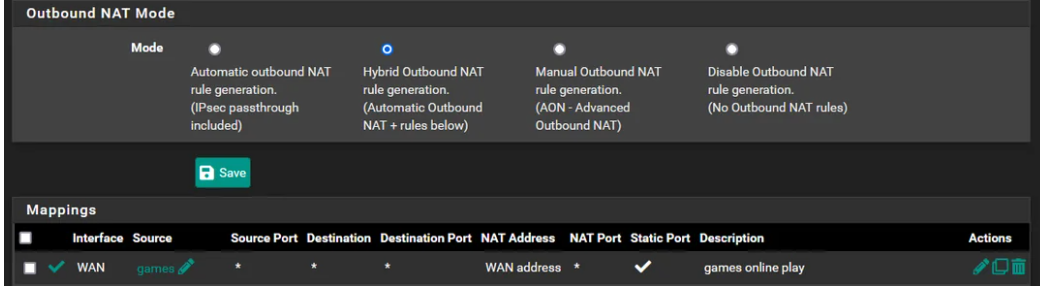
Finally, since UPnP does indeed reduce security in your network it's good practice to use the ACL rules. Which you already mentioned was your intention.
With some testing, and checking what ports various games require and checking the status page for UPnP when playing, you can limit the allowed ports dramatically. As an example, I have found that I only need to allow ports 3074-3076 and 28960-28964 for my PC in order for all my CoD games to work and get Open NAT. No need to allow the full 1024-65534 range... -
@Gblenn That makes it very clear! I do need to start thinking more about the split between the two interfaces, as I've had that split for quite a while but never really had a good reason for it other than to learn how to manage multiple interfaces.
I was thinking about an IOT vlan for all my smart lights etc and just having all the wired devices on one interface (they are now split between LAN and OPT1 with all wirless devices on OPT2).
As for the connection to my pc I unfortunately have to go with wireless, as my homelab is in our pantry and my PC is in our office. We rent an appartment for now so drilling holes to lay cables isn't really an option. I'll just wait until we can buy a house and then I can finally wire up my pc to my homelab :D
You've given me some food for thought, when I get home I'll start to figure out how I want to shape my network a bit better, thanks a lot though for all the help!
-
@semtex99 said in Is UPnP the reason my games don't work?:
OPT2 interface (where my router is connected to)
What router ?
@Gblenn said in Is UPnP the reason my games don't work?:
since UPnP does indeed reduce security in your network
Humm, I'll share you my point of view :
A process 'upnp' that listens on LAN, and open firewall port 'on command' and NATs traffic to that device (or any other device) on command.
No, thanks.
I already have to trust the firewall, and with unpn I also have to trust the application(s) I install on my LAN networks ...upnpn is nice to automate NATting, I fully understand
Its 2025 and are there are still game servers that need upnp ..... wow, I thought unpn was by now abolished....
@Gblenn said in Is UPnP the reason my games don't work?:
With some testing, and checking what ports various games require
If a game server needs to reach the client app, hidden behind a firewall (like pfSEnse, or any other firewall), the the game server creator will detail this out during the installation by showing a FAQ, or a manual or whatever, because the 'game' will fail to run.
The big players, like Blizzard (WoW, my past ... 2005 ?) completely abandoned the need for NAT, or unpn for that matter.Game servers that like to control your hardware right through your firewall... ok, but I would throw all these devices in some sort of DMZ network, totally isolated form all my other LAN type devices.
-
@Gertjan said in Is UPnP the reason my games don't work?:
The big players, like Blizzard (WoW, my past ... 2005 ?) completely abandoned the need for NAT, or unpn for that matter.
What do you mean Blizzard abandoned the need for NAT or UPnP?? Where do you get that from? It's rather the opposite I'm afraid...
Sure, you can play the campaign, and yes will be able to play online on a public server even when you have what's referred to as Strict NAT.
BUT, the second you want to host a game, or play a Private match with your friends, you will need as a minimum to get Moderate NAT and preferably at least one of you shold have Open NAT (the one hosting the game). There is no way you get Open NAT without either UPnP or doing a lot of manual configuration on your port forwarding and outbound NAT rules... -
@Gblenn said in Is UPnP the reason my games don't work?:
What do you mean Blizzard abandoned the need for NAT or UPnP?? Where do you get that from?
Back then, I used my crappy ISP (USB based ?) 'thing', no upnpn for sure, and it wasn't needed.
The I switched to M0n0wall, (from which pfSense was forked a bit later on) : no upnpn.
I still manged to go to '90'.We used to gather up, build a 'massive' MAN, and played together, it was a "bring your PC, hookup the Ethernet cable, and play' experience.
On my pfSense, I never activated the upnpn.But ok, these are my experiences from way back.
Maybe things changed. Not for the better I see.
Humm, as said, needed but well hidden. Great
@Gblenn said in Is UPnP the reason my games don't work?:
online on a public server
Public ? The official Blizzard servers. Why ? Are their 'private' servers now ?
-
@Gertjan said in Is UPnP the reason my games don't work?:
What router ?
Sorry, access point, the Asus RT-AXE7800 in AP mode I mentioned earlier
@Gblenn said in Is UPnP the reason my games don't work?:
With some testing, and checking what ports various games require and checking the status page for UPnP when playing, you can limit the allowed ports dramatically.
This does also seem interesting, I will try to see what ports get used by the various games I play to see if I can make my network more secure. I did notice that most games only use ports in a certain relatively small range, only Pavlov VR uses ports from 20000 to 60000 from what I've seen so far.
For now the practicality of UPnP weighs heavier to me than the potential security risks. I just want to enjoy the games I play with my friends and I'll try to narrow the security down later as my network grows. For example I still have to test if both me and my gf's Wii still work with Mario Kart CTGPR and online play. In that case I just want to play online and not have to figure out which ports I have to pass
-
@Gertjan said in Is UPnP the reason my games don't work?:
Back then, I used my crappy ISP (USB based ?) 'thing', no upnpn for sure, and it wasn't needed.
The I switched to M0n0wall, (from which pfSense was forked a bit later on) : no upnpn.
I still manged to go to '90'.We used to gather up, build a 'massive' MAN, and played together, it was a "bring your PC, hookup the Ethernet cable, and play' experience.
On my pfSense, I never activated the upnpn.Haha, that sounds much like my "journey" as well, starting over 20 years ago with a bunch of friends who I still today regularly play online with, private server matches only.
It started as a small LAN party style in a living room, and evolved into playing online once a week. My firewall/router was a WRT54GL running DDWRT and moved on to Smoothwall and back to DDWRT before settling on pfsense....@Gertjan said in Is UPnP the reason my games don't work?:
Public ? The official Blizzard servers. Why ? Are their 'private' servers now ?
I guess Blizzard (or should we say Microsoft?) is about several things, and I suppose most people recognize them from battle.net where you buy and download the game. But sure, I guess for some of the games they developed and maintain, they also host Public servers, as a means to promote online gaming.
These, and others, are all those you get listed within the game you are about to play. It probably contacts Blizzard, or Steam, to get the IP's of the servers and then list them preferably in order of lowest latency.Private servers exist as well, sometimes even visible in those lists, often with a Padlock next to them, indicating they are Password protected. OR, they are just temporary during matches between groups of people.
Like you can do with nearly all Call of Duty games, post World at War from 2008. You set up your Private match from within the game, and have your firends join you from their friends list or an invite you send them.And THIS is what needs at least Moderate, but preferably Open NAT, or they will not be able to join... UPnP is a huge help in this, and is used on pretty much every consumer router as well.
-
@semtex99 said in Is UPnP the reason my games don't work?:
This does also seem interesting, I will try to see what ports get used by the various games I play to see if I can make my network more secure. I did notice that most games only use ports in a certain relatively small range, only Pavlov VR uses ports from 20000 to 60000 from what I've seen so far.
For now the practicality of UPnP weighs heavier to me than the potential security risks. I just want to enjoy the games I play with my friends and I'll try to narrow the security down later as my network grows. For example I still have to test if both me and my gf's Wii still work with Mario Kart CTGPR and online play. In that case I just want to play online and not have to figure out which ports I have to pass
If you google the game name and port forward, you will get a lot of pages with support information. Sometimes even outlining how to do port forwarding or UPnP on various routers. Often the publisher, or Steam, Blizzard have support pages with this information as well. Use those ports to start with. Setting static port may also narrow things down and could be helpful if you are more than one person playing on line at the same time (same game).
For Pavlov VR, are you sure it actually needs any ports forwarded? As I read it that is mostly if you host your own server that needs to be publicly visible... The fact that it ends up with those high ports could simply be masquerading, and they will change every time...
You could test it and just turn off UPnP to see if it works. When testing these things you need to remember to do a ipconfig /release ipconfig /reload on your gaming PC. Otherwise there is a risk that some states are left over from before you make changes...
-
@Gblenn Good to know! When I get home from work I'll see what ports are needed.
@Gblenn said in Is UPnP the reason my games don't work?:For Pavlov VR, are you sure it actually needs any ports forwarded? As I read it that is mostly if you host your own server that needs to be publicly visible... The fact that it ends up with those high ports could simply be masquerading, and they will change every time...
I suppose I might not even need UPnP with the allow from OPT2 to any rule if I just want to join other people's servers...
@Gblenn said in Is UPnP the reason my games don't work?:
You could test it and just turn off UPnP to see if it works. When testing these things you need to remember to do a ipconfig /release ipconfig /reload on your gaming PC. Otherwise there is a risk that some states are left over from before you make changes...
Will do, thanks for the heads up!
-
@semtex99 said in Is UPnP the reason my games don't work?:
I suppose I might not even need UPnP with the allow from OPT2 to any rule if I just want to join other people's servers...
Exactly, but many games will need a bit more to work well and connect with all servers. It depends a bit on the server side as well...
-
@Gblenn I've done a bit of testing with UPnP disabled and only the allow from OPT2 to any rule, and everything seems to work! The only thing that I get is a moderate NAT on Call Of Duty, but it hasn't inhibited me from playing any matches. I've also only tried PC games for now, tomorrow I'll try some consoles like my PS3 and Wii and see how well that works