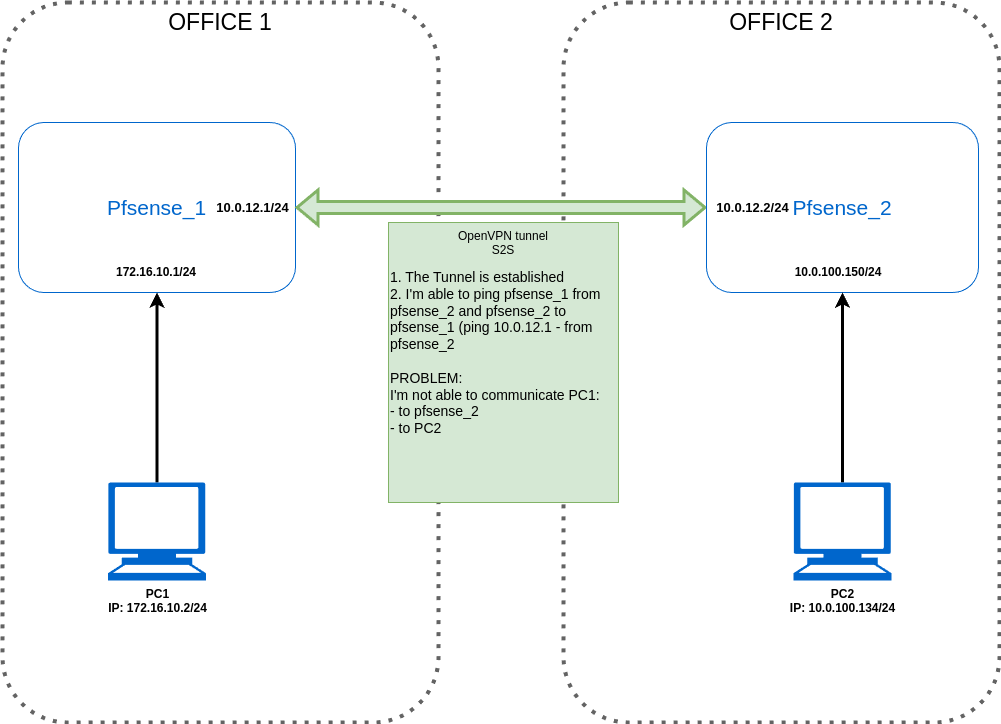
OpenVPN site-to-site communication issue
-
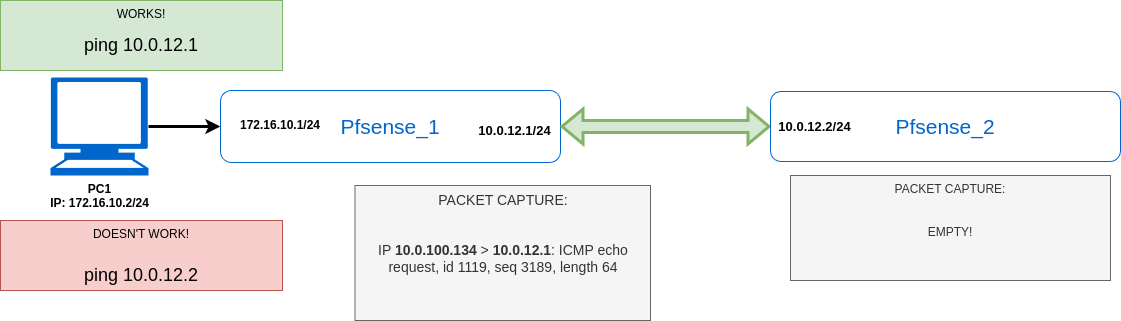
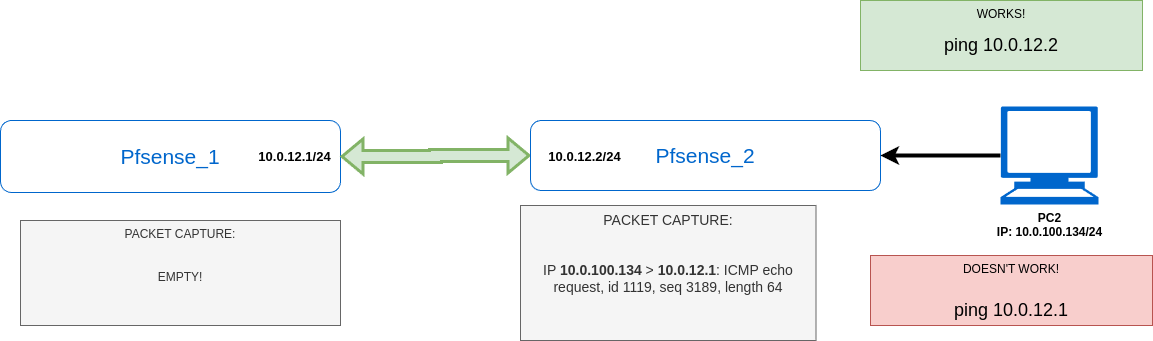
CORRECT SCREEN:
-
@Michal944
Are you missing the client specific override?? -
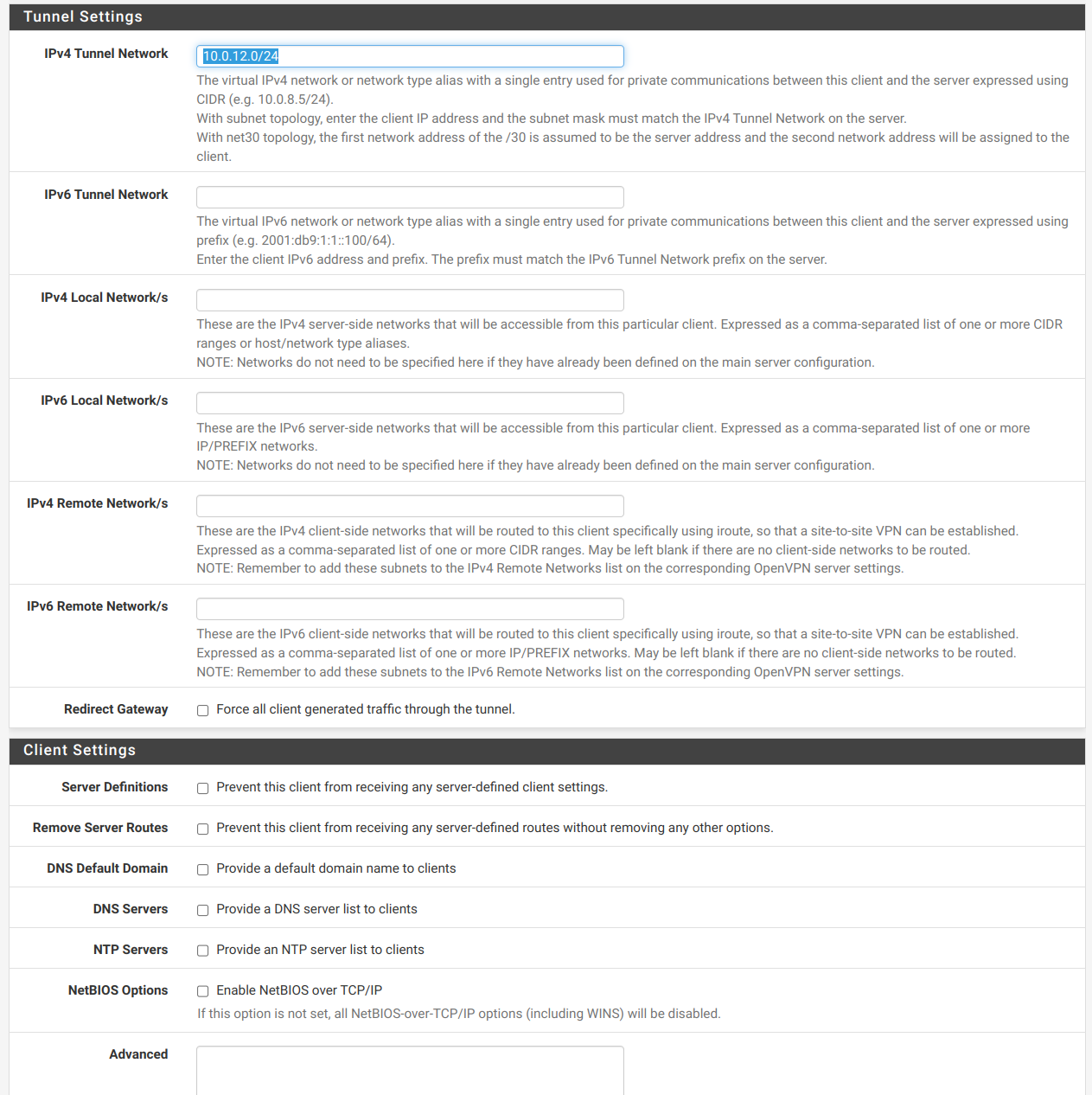
@viragomann I added proper config into Client Specific Overrides.
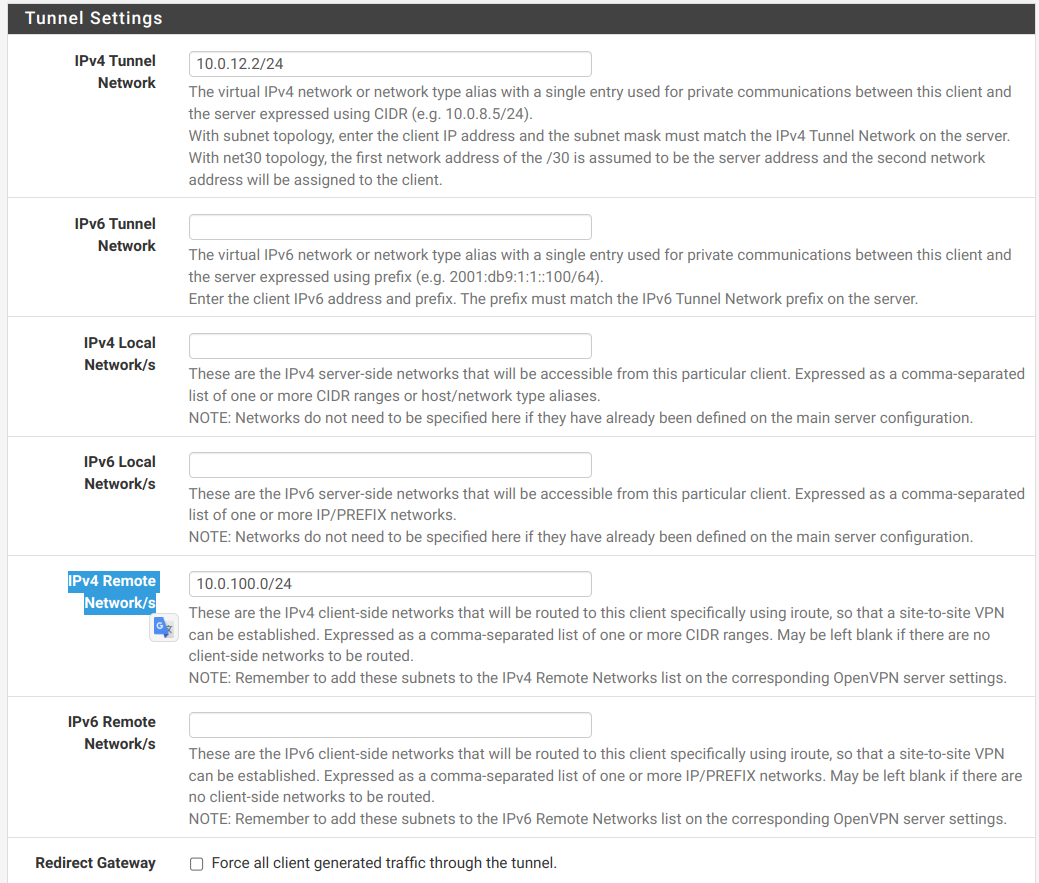
- Common Name: exactly the same as CN client certificate
- IPv4 Tunnel Network: 10.0.12.0/24
-
@Michal944
The IPv4 Tunnel Network has to be a usable IP with the mask, e.g. 10.0.12.15/24.
Also you have to specify the client sides LANs at "Remote Networks" in the CSO as well, aside from the server settings. -
Thank you for you reply @viragomann
I did what you mentioned, but it doesn't resolve the issue:
What I did:
IPv4 Tunnel Network: 10.0.12.2/24 (Pfsense_2 as client)
IPv4 Remote Network/s: 10.0.100.0/24 (Pfsense_2 - office 2)- Restart VPN server
- restart client
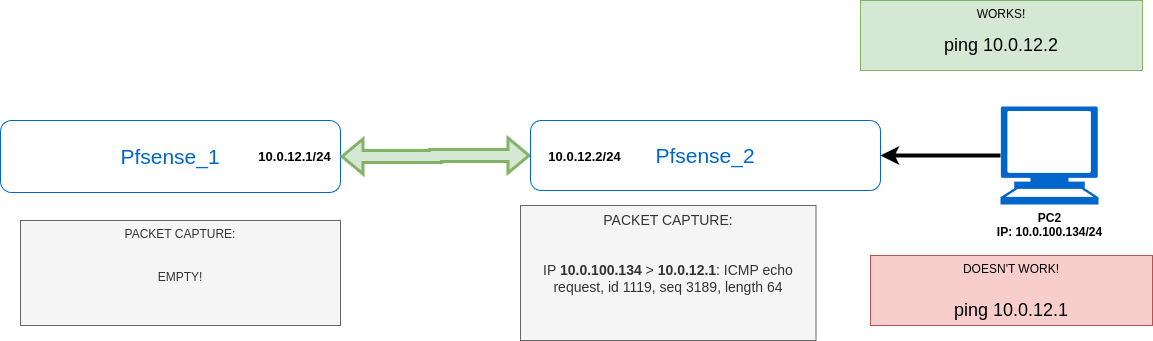
The same problem:
-
I was having the same issues a while ago and i just switched to ipsec for my site2site communications. It works so much better for me and I have never had any drop-outs or issues since. Might be worth a consideration.
-
@Michal944 said in OpenVPN site-to-site communication issue:
IPv4 Tunnel Network: 10.0.12.2/24 (Pfsense_2 as client)
I'd rather use a higher IP. 2 is the first in a /24 used for the default routes added by the OpenVPN server. I'm not sure if it's wise to use it for the certain client.
Moreover if more than one client connect to the server you it's necessary to use a high IP in the subnet, since the CSO does not reserve the IP for a client. The server allocates the IP from the lowest one upwards. So at the time of connection, the IP has to be unallocated.
Ensure that in the server is configured for subnet topology. Otherwise you'd have to specify a /30 tunnel network with the network address in the CSO.
To verify if the CSO is applied properly, set the servers log verbosity level to 4 and reconnect the client. Then check the log. Maybe you can post it here.
-
@viragomann.
Ok, I did everything that you mentioned:
- client IP changed from 10.0.12.2 to 10.0.12.15 (Pfsense_2)
- The routing table changed
from
10.0.100.0/24 10.0.12.2 UGS 29 1500 ovpns4to
10.0.100.0/24 10.0.12.15 UGS 29 1500 ovpns4-
Client Specific Overrides
IPv4 Tunnel Network from 10.0.12.2/24 to 10.0.12.15/24 -
the log level changed to 6 as well.
log:
Jan 17 10:50:37 openvpn 35043 aws/90.xxx.xx.xx4:15814 UDPv4 READ [108] from [AF_INET]90.xxx.xx.xx4:15814: P_DATA_V2 kid=0 DATA len=107 Jan 17 10:50:37 openvpn 35043 aws/90.xxx.xx.xx4:15814 MULTI: bad source address from client [10.0.100.134], packet dropped Jan 17 10:50:38 openvpn 35043 aws/90.xxx.xx.xx4:15814 TUN READ [29] Jan 17 10:50:38 openvpn 35043 aws/90.xxx.xx.xx4:15814 UDPv4 WRITE [53] to [AF_INET]90.xxx.xx.xx4:15814: P_DATA_V2 kid=0 DATA len=52 Jan 17 10:50:38 openvpn 35043 aws/90.xxx.xx.xx4:15814 UDPv4 READ [53] from [AF_INET]90.xxx.xx.xx4:15814: P_DATA_V2 kid=0 DATA len=52 Jan 17 10:50:38 openvpn 35043 aws/90.xxx.xx.xx4:15814 TUN WRITE [29] Jan 17 10:50:38 openvpn 35043 aws/90.xxx.xx.xx4:15814 TUN READ [29]The area is the issue: bad source address from the client [10.0.100.134]
I don't know why. Could you help to figure out what is going wrong? -
@Michal944 said in OpenVPN site-to-site communication issue:
client IP changed from 10.0.12.2 to 10.0.12.15 (Pfsense_2) The routing table changedYou must not specify an IP in the client settings! I didn't not that you did this before.
The IP is allocated by the server.Don't matter about the servers routing table. The roue to the client networks point ever to the second IP in the tunnel subnet, 10.0.12.2 in your case. The routing to the real client IP is done inside OpenVPN if the CSO is applied. You can only see this in the log.
You will never see the clients IP in the routing table.the log level changed to 6 as well.
This gives to much noise. With 4 OpenVPN logs the CSO appliance.
Ensure that you have 10.0.100.0/24 in the server settings and the CSO at "remote networks".
-
@viragomann It works!
I remove the client static IP configuration from the server setup and ping works from both sides.
It was quite difficult but the reason why I didn't read the documentation about s2s OpenVPN connection. Thank you!