Need to setup VLAN with Bridged Mode in pFsense 2.7.2
-
Hi
I have been using pFsense on and off since about 10 years now, but since the last 2+ years i have a small dedicated Intel NUC running as my pFsense at my residence.
The hardware specs are as follows
Intel NUC with Celeron N2807, 8GB RAM, 120GB SSD, Gigabit onboard ethernet (connected to WAN bridged mode) along with TP-Link UE306 (usb to Gigabit ethernet connected to LAN) connected on USB 3.0 port, BIOS upto date, pFsense version 2.7.2.Since my hardware had just 1 GIGABIT ethernet port, i had to resort to using a USB Ethernet hardware running on AX88179 chip which was running fine for about 6 months, but since off late when i had to do a reinstall of pfsense on the machine, my USB GIGABIT dongle crashes religiously every 36-48 hours and forces me to hard reboot the machine.
What i want is stability of the entire setup but cannot change the machine, so what i have come to understand is to setup my pfsense in bridged mode only but using the VLAN methodology.
In simpler terms, what i want is
ISP Router connects to PFSENSE in Bridged Mode via the onboard GIGABIT PORT of the Intel NUC and the same onboard GIGABIT PORT is connected to my 24port GIGABIT SWITCH and then that switch is connected to my MESH and other peripherals/devices.
The 24 port GIGABIT SWITCH that i have does not support VLAN, so i can consider purchasing a small 4/5PORT GIGABIT SWITCH which supports VLAN and gets me up and running with miniscule to no failure.
Kindly help me thru, consider me an absolute NOOB in terms of VLAN.
MUCH THANKS AND REGARDS IN ADVANCE.
BugsBunny -
@dkthedriftking Yes what you are looking for is absolutely doable.
So the managed switch could be set up like this:
Port 1 - Connected to WAN (modem) - set to Untagged VLAN ID 10
Port 2 - Connected to NUC - set to TAGGED VLAN ID 10 and 20
Port 3 - Connected to 24p switch - Untagged VLAN ID 20In pfsense you need to create two VLAN's on igb0 or whatever it's called. VLAN ID 10 and VLAN ID 20 and assign WAN to ID 10 and LAN to ID 20.
What modem/router is it that you have from the ISP? You may have to go into the UI and make sure it does not hand out the IP to the switch MAC, instead of pfsense MAC...
-
@Gblenn Wow! Thanks alot, you really simplified it for me to execute this.
Now before I move forward, let me tell you how the entire setup will be once executed as per your recommendation.
-
ISP Router (Nokia FTTH routegr) to Managed switch (Port1)
-
Managed Switch (Port2) to PFSense hardware (Gigabyte NUC with onboard Realtek Gigabit NIC) (PPPoE Bridged Mode, as in PFSense hardware dials to the ISP)
PFSense hardware is what gets the public IP from the ISP and PFSense hardware is what works as the DHCP server along with AdGuard server for the entire local network.
- Managed Switch (Port3) to existing 24Port Gigabit Switch which connects to the existing local network.
All the above configuration/connections will require setting of VLANs as per your recommendation on the Managed Switch and PFSense hardware level.
Also, The managed switches that I'm considering are SG105E or SG108E, both TP-Link brand; let me know which I should go for.
Now whilst I'm revamping the setup, I have another question hopefully which will get resolved too with the help from you and/or other members on here.
I have another NUC which is running Windows 11 and is on the verge of running Nextcloud for my own private cloud.
To achieve that I have come to understand that I will need a third party service like duckdns or dynudns or no-ip since getting a static IP is out of question.
I believe I have fairly decent knowledge of port forwarding but all that has went down the drain while doing so on PFSense even when I have setup everything like it should be if the port forward is to happen on the ISPs router where no PFSense is involved.
Would be great if you can help me on that too and should you need any information from me to help troubleshoot the same then do let me know.
Much thanks and regards.
-
-
@dkthedriftking So when running NextCloud you want to make sure you have a secure connection and one good way of handling that is using HAProxy in pfsense. Or run a separate instance of e.g. Nginx Proxy manager.
Get your duckdns, dynu or whichever one you like. What you then need to do is the following, in principle.- Set up Dynamic DNS under Services in pfsense. So that pfsense can monitor and keep it updated pointing at your IP
Duckdns provide really good instructions of how to set it up, once you have created a first domain name. Click install in the menu and select pfsense... and follow the instructions - Set up NextCloud and set it to allow your nextcloud.duckdns.org FQDN and the IP of pfsense (needs to be set in the config)
- Set up HAProxy to use HTTPS, get a certificate for your nexctloud.duckdns.org and point to the IP of your NextCloud server.
- Go into System > Advanced under Firewall & NAT and enable NAT Reflection and Pure NAT.
Now you can use nextcloud.duckdns.org on your PC from behind pfsense, as well as from phones and other devices when external.
- Set up Dynamic DNS under Services in pfsense. So that pfsense can monitor and keep it updated pointing at your IP
-
Much thanks, again; BUT, what you explained in principle sounds simple but im in the blind, AGAIN!

My DuckDNS is already set in my pfsense, have tried opening entire traffic from WAN to all ports on the said NextCloud Machine but its still unsuccessful.
PFA some screenshots for your reference as to what all i have tried till now and guide me further.
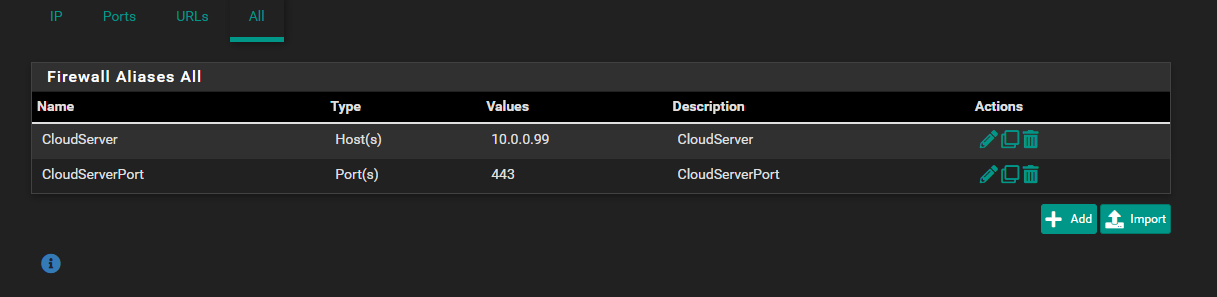
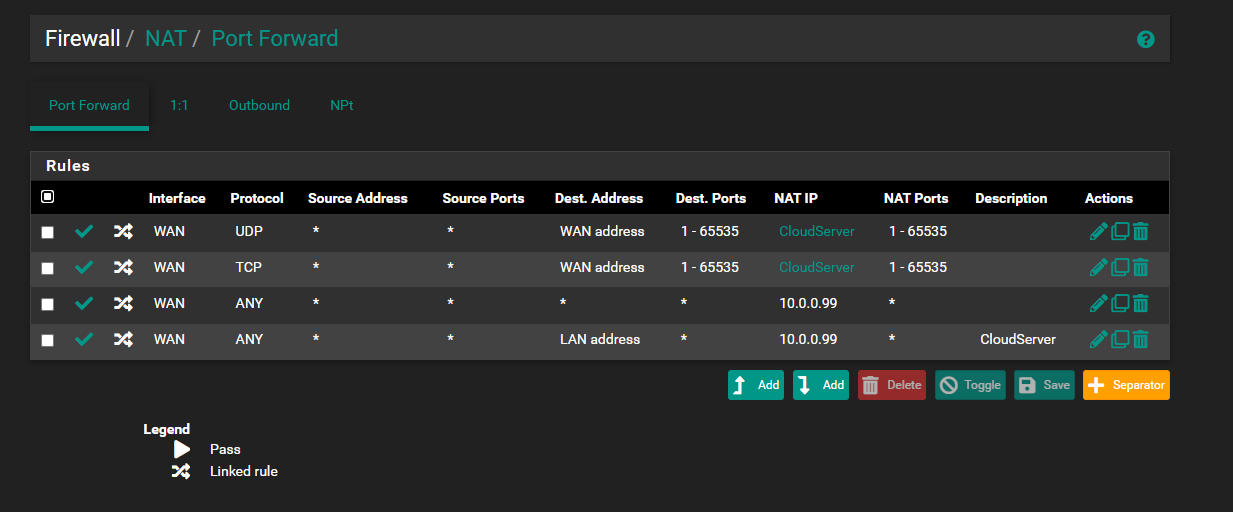
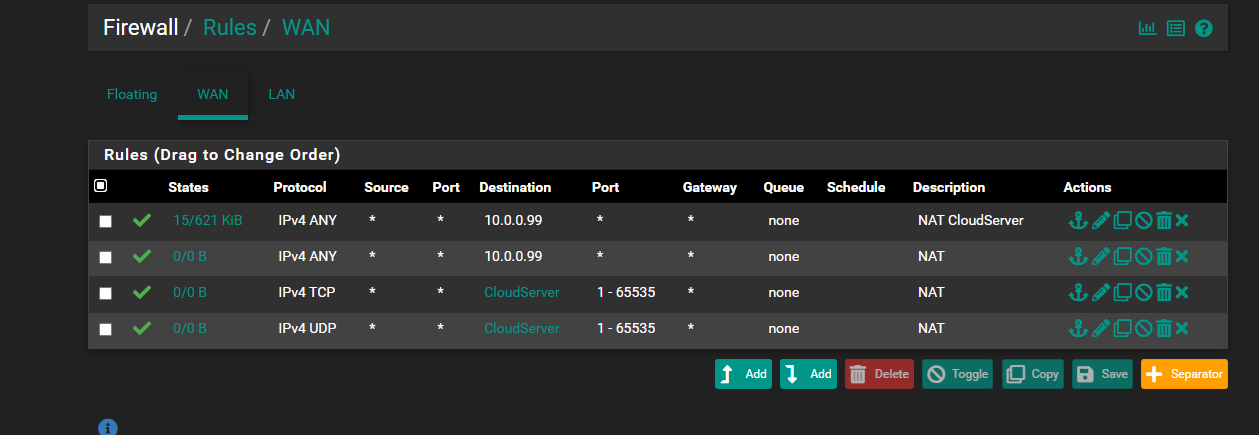
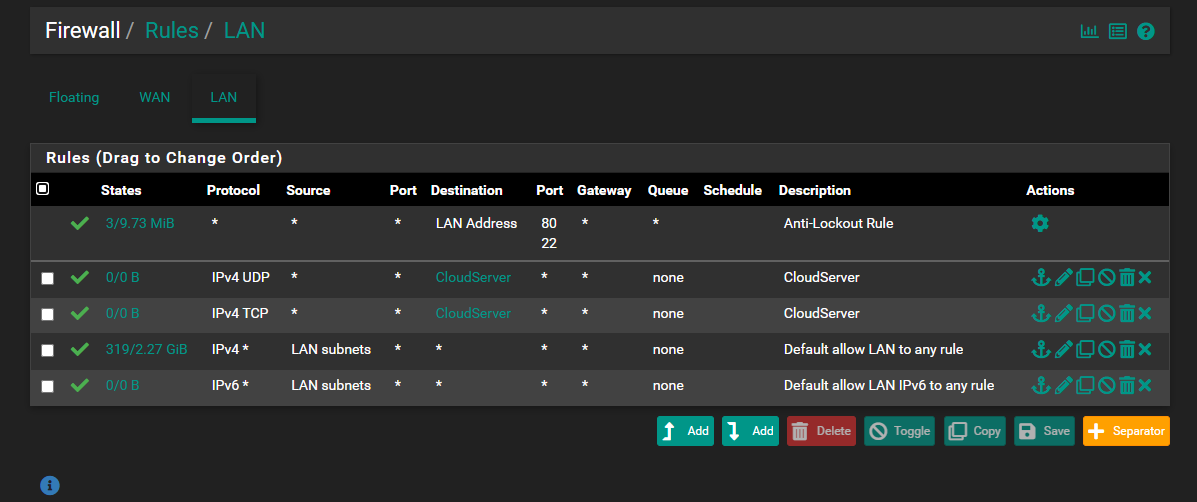
edit: public IPs snipped by mod (johnpoz)
-
@dkthedriftking said in Need to setup VLAN with Bridged Mode in pFsense 2.7.2:
Much thanks, again; BUT, what you explained in principle sounds simple but im in the blind, AGAIN!
My DuckDNS is already set in my pfsense, have tried opening entire traffic from WAN to all ports on the said NextCloud Machine but its still unsuccessful.
Oh, please don't do that... port 443 only! Remove that rule asap, you have essentially put the server on the internet.
AND, I think it's probably better to use HAProxy to handle the certificates for you. And in that case, you don't open 443 towards NextCloud, but HAProxy instead (and port 80 used during certificate setup).However, nothing of this will work until you have set NextCloud to accept communication from pfsense IP, as well as the domain name you hae from DuckDNS. I'm assuming you can access NextCloud locally though?
I do agree, things may look simple in principle, but still not that simple to implement...
-
@dkthedriftking your port is open - but your sending gibberish on that IP, not a ssl cert - you sure you want your public IP exposed on the forum - your screenshot lists your public IP - would you like me to edit that..
You just get back this
"eac7aade88daff9311cdd8fcf9577f4af7477f7c2d4e899a " -
@johnpoz said in Need to setup VLAN with Bridged Mode in pFsense 2.7.2:
would you like me to edit that..
Considering the fw rules in place, if you can redact the IP, it's a good thing to do...
-
@Gblenn agree - done.
So seems there is a local cert for nextcloud.local, but its listening on port 8080

@dkthedriftking I would as suggested by @Gblenn shutdown that all ports forward.. And look to correct your https issues..
Using a selfsigned cert can work - but its going to be problematic if you want anyone other than yourself to use it because they are not going to trust the cert and get a warning.
You prob want to look into using acme (lets encrypt) to get a valid cert for whatever the fqdn that points to your public IP via your ddns entries.
-
@johnpoz Yes, I noticed that as well, so clearly things are working fine with NC and port forwards.
You prob want to look into using acme (lets encrypt) to get a valid cert for whatever the fqdn that points to your public IP via your ddns entries.
@dkthedriftking
So take a look at HAProxy and try to set it up so that you secure your setup with a real signed certificate. Alternatively, perhaps depending on how you installed NextCloud on that machine... is it virtualized? You could install Nginx Proxy Manager which it likely even simpler to set up for this purpose, and other future servers. -
@Gblenn
Hi, again. And also to fellow members who are reading this.Below is the list of equipment I have, and have listed them in the order of they should be connected so as to run VLANs perfectly (as per me).
-
ISP provided Device. Recieves fibre cable, works as an ONT, has 4 Gigabit LAN ports and 2 antenas supporting 2.4 and 5G WiFi. With the help of the ISP technician, I have gotten it to work in bridge mode (PPPoE) so that my pFsense device is the one that gets the public IP from the ISP. For the bridge mode to work, it's set to VLAN100 and it runs on Port4 of this device.
-
PFSense device is a mini PC gigabyte brand with just one onboarding Gigabit NIC. Till date was using a USB3.0 to Gigabit LAN adaptor so as to have 2 NIC, one each for WAN (PPPoE bridged mode) and LAN respectively. But now the USB NIC adaptor is acting up every couple of days and I need to power off the machine and then power on. So I intend to make use of VLANs so as to do the WAN and LAN work using the onboard Gigabit NIC of the mini PC.
-
For VLAN I have a TL-SG105E. What setting should I do on this device and which VLAN ID should be set.
-
For distributing internet all across my place (wired/wifi) I am using a 24 Port (Gigabit) switch which does not support VLAN. All wired devices and my Mesh are connected to this.
I hope I have been able to explain it all clearly. If not then do let me know.
Request you to helps me out in this
Many thanks and regards
BugsBunny -
-
@dkthedriftking I'm not sure you need to care about the VLAN 100 towards pfsense, since I'm guessing the ISP device should work with non VLAN aware home routers as well. I'm thinking the key thing for your here is to use port 4 on the ISP device.
What you need to do in the switch, and in pfsense, is to make sure you use VLAN to split the switch into two separate parts. One for the WAN side and one for the LAN side.
Let's say you use Port 1 to connect to your ISP Device port 4, and port 2 connects to your NUC and ports 3-5 are your LAN side ports.
On the switch you will need to set up two VLAN's, for example ID 100 and 200.
In the TL-SG105E menu, you select VLAN and then 802.1Q VLAN.
There you select Enable and click Apply.
Then you type 1 in the VLAN ID field and select port 1 as NOT MEMBER of VLAN ID 1, and click the Add/Modify button below the port list. This is a safety measure to make sure that port only carries VLAN 100 traffic.
Then you type 100 instead and select both ports 1 and 2 as Tagged Members, and again click Add/Modify.
Now you type 200 and select port 2 as Tagged Member and ports 3-5 as Untagged Members, and click Add/Modify.
Then you select 802.1Q VLAN PVID Setting from the menu and type 200 and tick the boxes for ports 3-5 and Apply.In pfsense you need to create VLANs with ID's 100 and 200. Then create the WAN interface with VLAN 100 off of the parent interface. And similarly for the LAN interface using ID 200 instead.
IF for some reason that doesn't work for the WAN side, you could try setting Port 1 as an untagged member of ID 100. Then that VLAN becomes internal to your switch and pfsense and will not involve the ISP device. In this case you could use a different ID for that VLAN.
-
for doing this task ,
you'd better buy hardware with multiple network cards for the NUC
Mini PC Windows Intel N100, Celeron J6412, HDMI, DP, RS232, COM, RJ45, LAN, PCIE, Wi-Fi, fanless,