pfSense inside LAN
-
Hello community!
I'm totally green on pfSense so bear with me.
we are trying to establish one secure department (LAN) in the office, where clients on that LAN can talk to each other and have access to internet but no incoming traffic from "outside".
i have setup pfSens 2.7.2 with some basic config and it works well. I can access web gui and clients are getting ip from DHCP and have contact with internet and no incoming traffic..
Thing is that we need access to some of the clients on that lan from "outside" which means that we need RDP from local LAN and from internet. Our main FW is already configured with VPN access to local LAN, so we basically need access to pfSense LAN from local LAN.
local LAN setup.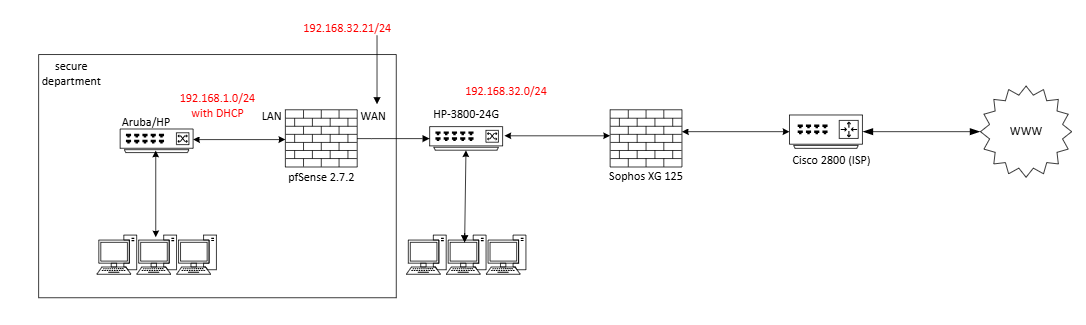
-
@n00bie
So did you allready set the static routes for the LAN on the firewalls in front of pfSense?If so you just need to add a pass rule to the WAN for TCP/UDP, source = any (or whatever you want), destination = LAN subnet (or an alias, which you have added to the desired hosts), destination port = MS RDP.
To allow access from the local subnets, you also need to go to the WAN interface settings and remove the check at "block private networks".
-
@viragomann
I haven't done anything on Sophos FW.
I was on google, for the past few days, trying to find a similar case for pfSense, with no luck.
Not quite sure on how to tell Sophos FW, that there is as new LAN behind 192.168.32.21 interface.
"block private networks" on WAN int. has been unchecked.
That Cisco box, from ISP, is not reachable for me, only ISP has access to that one. -
@n00bie You can either create NAT rules/port forwards (.32.21:3014 -> .1.14:3389), or in the Sophos add a static route so 192.168.1.0/24 is sent to 192.168.32.21 (and allow the traffic there via WAN firewall rule). I don't know Sophos to tell you how, but it should be findable.
-
@n00bie
After adding the pass rule for RDP, I mentioned above, you should already be able to access your hosts from 192.168.32.0/24, which might you call "LAN".However, consider that the computers will block access from outside of the subnet by default. You will have to allow RDP access from outside on their firewalls as well.
To get access from behind the VPN, you need to
- add the department LAN to the VPN, so that its traffic is routed over the connection.
- add a static route for the department LAN on the Sophos
Iss the VPN terminated on the Sophos or on the Cisco.
If you cannot configure the VPN, you can only forward traffic to the department LAN on the Sophos at its best.
-
@viragomann @SteveITS
For now im focusing on getting this work inside our office LAN. Nothing has been done on Sophos FW. VPN is terminated on Sophos.
I have done so far (not working config):
On client inside secure dep. i have one incomming rule (windows FW) and one outgoing rule, that allows port 3389.
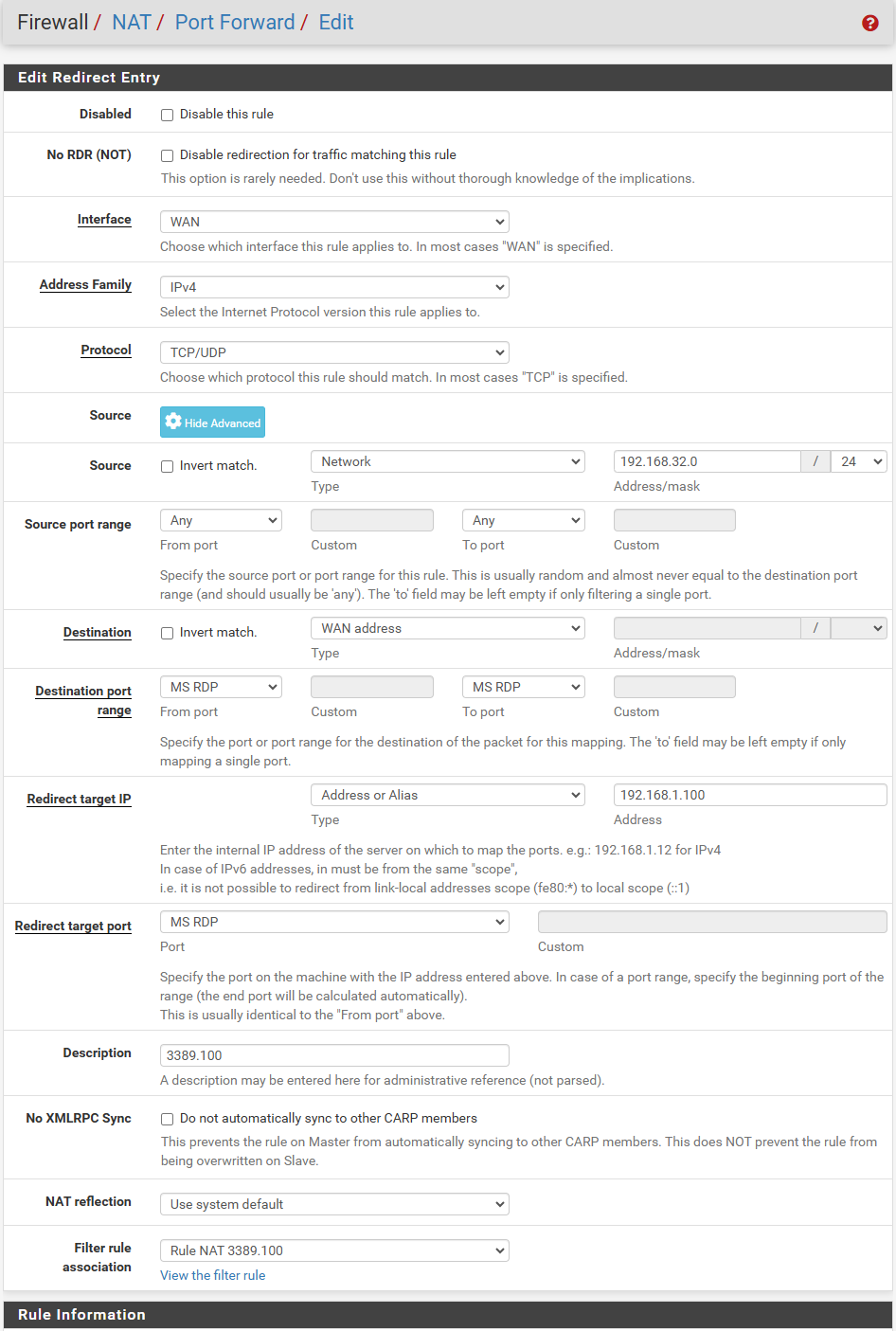
On pfSense i have created this NAT rule.
And its not working (RDP to 192.168.32.21 and 192.168.1.100 are no go).
-
@n00bie
There is one additional point, I didn't think of before.
The LAN devices in 192.168.32.0/24 themself need a static route for the department LAN pointing to pfSense.
If they get the IP from a DHCP, you can probably deploy the route with it. Otherwise you would need to add a route on each device you want to access the department LAN.Another (better) way would be to cut the pfSense from the LAN and put it into a separate network segment with the Sophos (maybe a VLAN). Then you only need to route on the Sophos.
-
@viragomann
Office LAN get IP from local DHCP server but i was hoping that config is only needed on pfSense.
NAT rule is self explainng :)
when TCP/UDP on 192.168.32.21 send it to 192.168.1.100:3389. Right?
I would rather have solution on pfSense and not involving Sophos, as those two boxes are 2 stories apart. -
@n00bie
If the LAN devices doesn't pull their DHCP lease from pfSense, there is nothing pfSense can do to affect the routes.But yes, you can port forward the traffic on the pfSense WAN to the devices behind. But you NAT rule seems wrong.
Source: 192.168.32.0/24 (or any or an alias also including VPN tunnel pool)
source port: any
destination: WAN address
destination port MS RDP
redirect target: any IP in the department LAN
redirect target port: MS RDPFor further devices to access, you can either add additional IPs to pfSense WAN or use other ports.
In case of alternative ports use the this as destination port, e.g. 3388, but at redirect target as well MS RDP. -
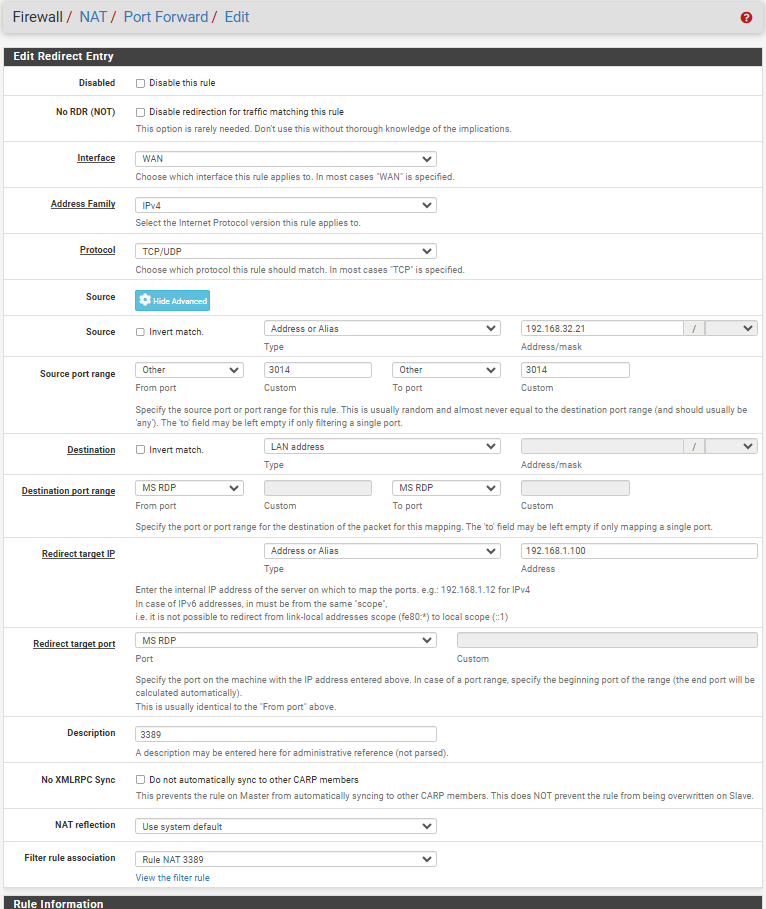
@n00bie Agreed, source ports are always random. If you change that your setup should work to RDP to 192.168.32.21:3389.
Or if you meant to use 192.168.32.21:3014 then set 3014 as the destination port.
-
@viragomann @SteveITS
Thank you gentlemen!
It works now. viragoman put me in right direction.
No need to open any ports on clients windows FW or anything else, just correct NAT rule.
I have 2 clients in secure dep., one with 3389 and second with 3390 RDP port (have to change default RDP in windows).
Then clone standard NAT rule and just change redirect target and RDP port.
Here is my config, that works.