Is there any way pfsense can connect as a client for a VPN providers and a server for remote LAN access on different tunnels simultaneously?
-
I have followed this tutorial for pfsense as a client : https://forum.netgate.com/topic/196006/guide-setup-a-wireguard-tunnel-to-vpn-provider-multiple-vpn-tunnel-setup
and this one for the pfsense server for remote LAN access : https://www.wundertech.net/how-to-set-up-wireguard-on-pfsense/
for some reasons I can't connect to remote LAN when my pfsense is connected to the VPN provider.
-
Hi @philjoyal, I set up yesterday a Wireguard Server on my pfSense and successfully connected a Wireguard client (Android) to it. The client is able to reach the LAN and Internet via the pfSense.
The pfSense itself connects via Wireguard to a VPN provider.My assumptions for your issues are:
- Missing firewall rules for the Wireguard SERVER interface on your pfSense
- NAT outbound rules
The static route I mentioned in the other thread is NOT relevant.
Now, regarding the settings. When I refer now to the Wireguard tunnel, it's always the tunnel with the Wireguard Server on your pfSense and your clients. My Wireguard client network is 10.100.0.1/24.
- Firewall rules:
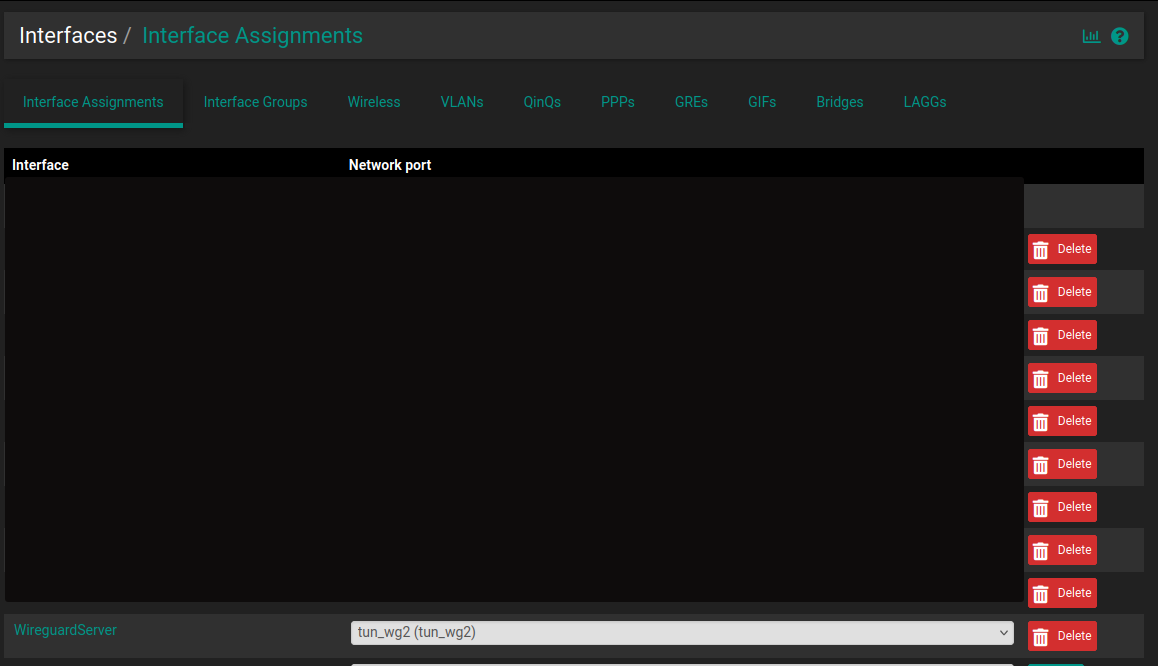
When you create the Wireguard tunnel, you 'll get a new network port. You will need to assign this new network port to a new interface (Interface > Interface Assignments) in order to be able to define firewall rules afterwards.
In my case, the new created network port is tun_wg2.
I renamed the interface from OPT9 to WireguardServer and specified the IPv4 settings I used for the clients of the Wireguard tunnel:
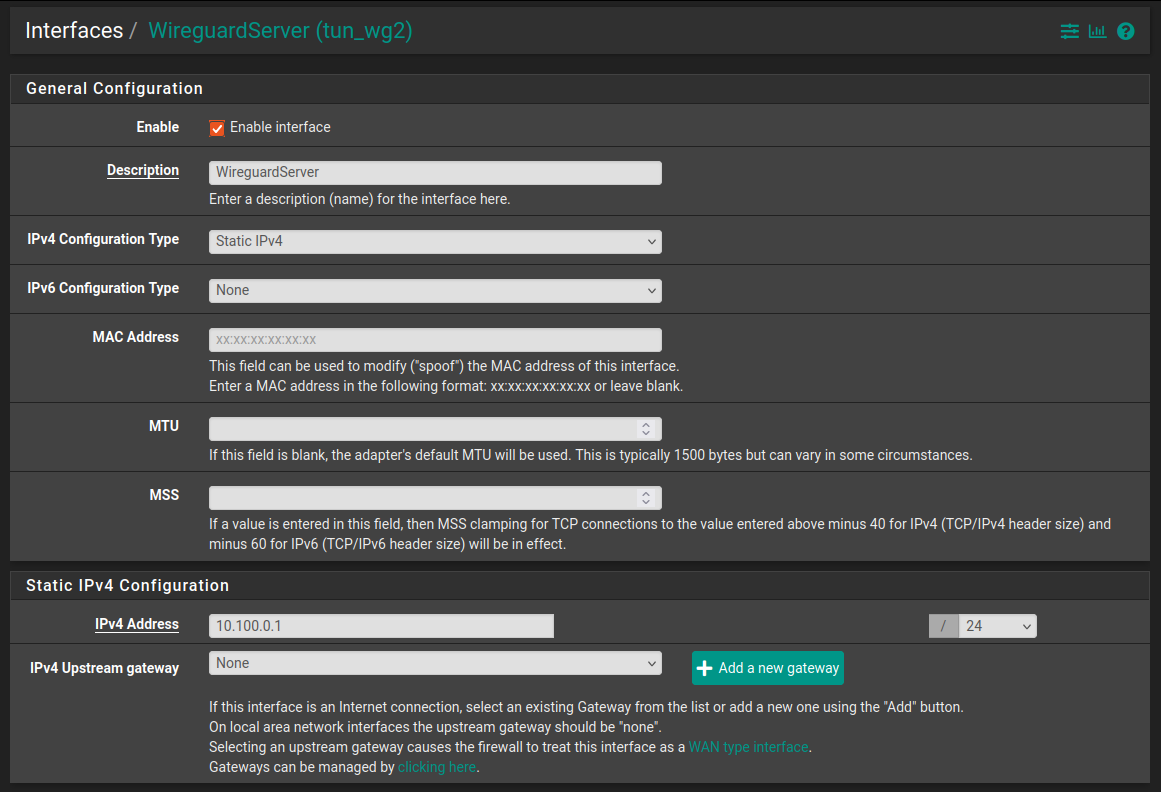
! I disabled the DHCP server for this interface !
Now, the firewall rules need to be defined for that interface in order to allow traffic from the Wireguard clients.
When you go to Firewall > Rules, you will realize that there is a the interface. In my case: WIREGUARDSERVER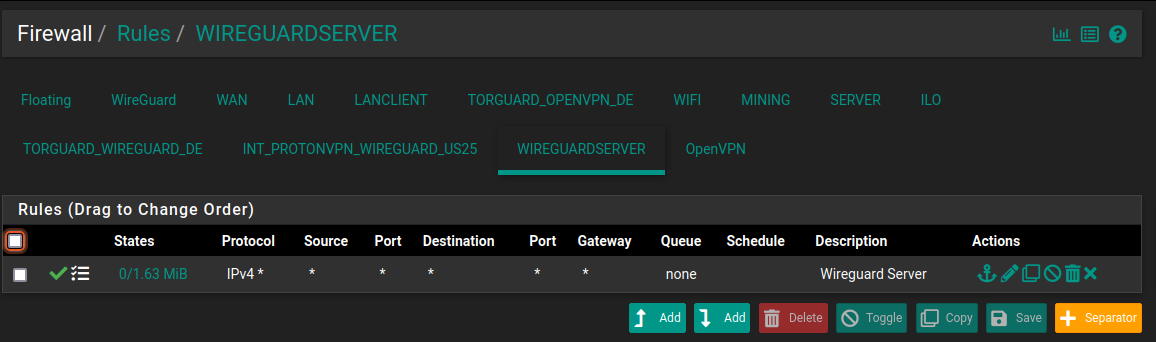
For the sake of simplicity, I'll allow all traffic for now.
- Outbound NAT
Here you need to ensure that the Wireguard clients (10.100.0.0/24) are allowed for outbound traffic via the Wireguard VPN tunnel to your VPN provider.
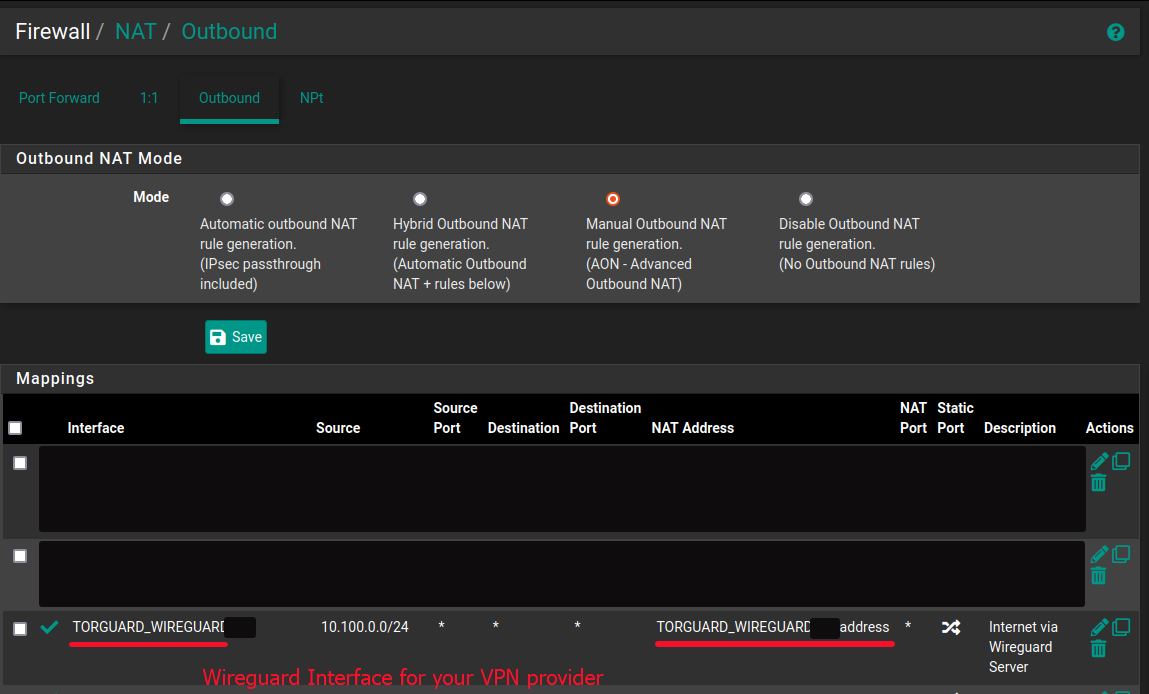
This should do the trick with your config.
My clients can connect now to my pfSense via Wireguard and connect to my LAN and to the internet. When I check the public IP of my Wireguard clients then the public IP of the VPN provider is shown. So everything works fine -
@LaUs3r For some weird reasons everything works fine now. Rechecked and tried all your inputs and didn't work. So I've set back to my originals settings it still didn't work but then after a few minutes everything was working fine. Did a reboot to check and everything is fine now. I'll have o investigate this more. Thank you for all your time and help!!!
cheers
-
@philjoyal , good to read. let's hope it stays that way

-
@LaUs3r well I've been playing a bit and found out my current configuration is half working as it should. First I have to let the WAN as the default gateway (opposite of what you configured in your guide) and second problem is that my client doesn't have internet access (bad) when connected to the LAN but have full access to machine on the LAN (good). I'll keep looking into that.
-
After I did setup my pfSense Wireguard server, my Wireguard clients had no access to LAN and Internet too.
But: I could see the blocking of the traffic in the logs which is completely normal as no firewall rule was defined for the Wireguard interface, i.e. all my 10.100.0.1/24 was blocked.That's why it's so important that you assign the interface and define the rule.
If you want, re-post all of your settings (tunnel, interface assignments, outbound nat, firewall rules, etc.).
Probably it would be best not to redact much of the information (IPs yes, but names should be ok) -
@LaUs3r When
I check logs (status > system logs > firewall) and see nothing relevant. I edit names and all personnal info (giving names can lead to security breach. in my opinion)