OPENVPN PIA Installed and working but lost VLAN access
-
Hi all,
I'd appreciate some advice please.
I have installed OPENVPN with PIA sucessfully and it works. I have set it up to route several devices on (default) VLAN1 to route out via the VPN Interface and that works.
The problem is that the selected devices on VLAN1 cannot now communicate with the other VLANs (3&4). The non-VPN devices continue to work fine.
I have a rule on VLAN1 to direct non-VPN devices to the WAN Interface but that doesn't appear to have an affect.
I presume my issue is with the firewall rules. Any suggestions where to investigate be appreciated. Thanks, Ian -
@webrat11 said in OPENVPN PIA Installed and working but lost VLAN access:
I have set it up to route several devices on (default) VLAN1 to route out via the VPN Interface and that works.
So I guess, you did this with a policy routing rule.
To apply this rule to upstream traffic only, you have to limit its destination to outside addresses, i.e. non-private ones.Best to do this is to create an alias for private subnets (this ones you know) and use it in the policy routing rule as destination with "invert match" checked.
This is my RFC 1918 alias:
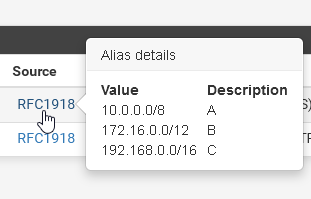
It includes private IPv4 ranges.
In your case, you have to place it as destination in the policy routing rule and check "Invert match". Then this rule is only applied to any other IP than the ranges in the alias. -
Hi, thanks for posting so quickly. I understand what I need to do in principle but not so sure about the detail.
Yes, I , you did this with a policy routing rule. (Tagged)
I have two rules on VLAN1 and two aliases.
One rule to allow VPN devices to VPN Gateway and another for the remaining devices to allow route to default WAN Gateway. Aliases are VPN_Devices, 3 IPs from with the VLAN1 and Non_VPN_Subnets is a list of the other VLAN addresses.
What I have done isn't working. I have attached a screenshot of the rules.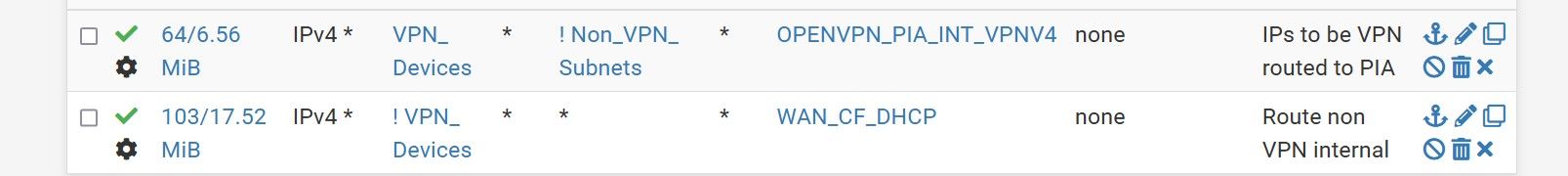 .
.What have done wrong please. thanks, Ian
-
@webrat11
So I presume, that the Non_VPN_Subnets alias contains you local subnets, which you want to be able to access from "VPN_Devices". This should work properly then.But with the second rule, you force all other destinations to the WAN gateway. Note that this also includes destination, which are not included in "Non_VPN_Subnets". Hence if this is applied to local destinations you will not be able to access it.
You should set the gateway to "any" in this rule. -
That did the trick.

Thank you again. Pleased to have it working.