Redirect IPv4 Gateway - Force all client-generated IPv4 traffic through the tunnel does not work
-
When setting up an OpenVPN server, if I enable the Redirect IPv4 Gateway - Force all client-generated IPv4 traffic through the tunnel option, my VPN tunnel does not work. I am unable to ping any hosts on my LAN or browse the internet.
If I disable this option however, I can browse the internet and ping my hosts.
As far as traffic hitting my firewall, I cannot see any (looking at the traffic monitoring on my firewall states)
From my reading other posts here, it has been stated that it might be a NATing issue. Here are my outbound NAT rules:
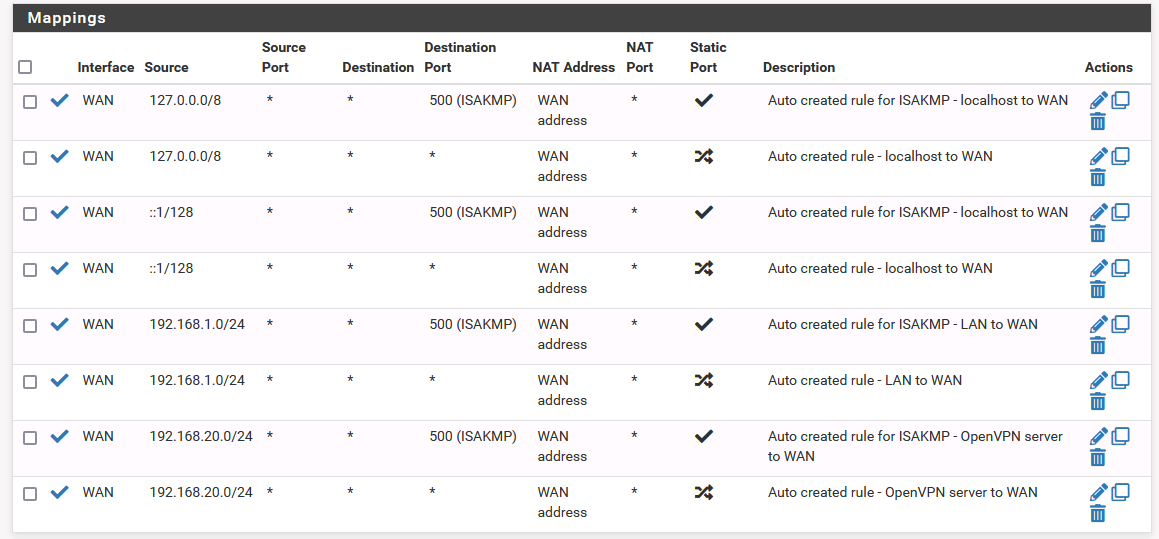
192.168.20.0/24 is the network for my VPN.
I would prefer to enable this option since for most scenarios, I need all my traffic to flow through my VPN.
Any thoughts?
-
@sparkman123 said in Redirect IPv4 Gateway - Force all client-generated IPv4 traffic through the tunnel does not work:
When setting up an OpenVPN server, if I enable the Redirect IPv4 Gateway - Force all client-generated IPv4 traffic through the tunnel option, my VPN tunnel does not work
That's what I use.
No mappings needed.
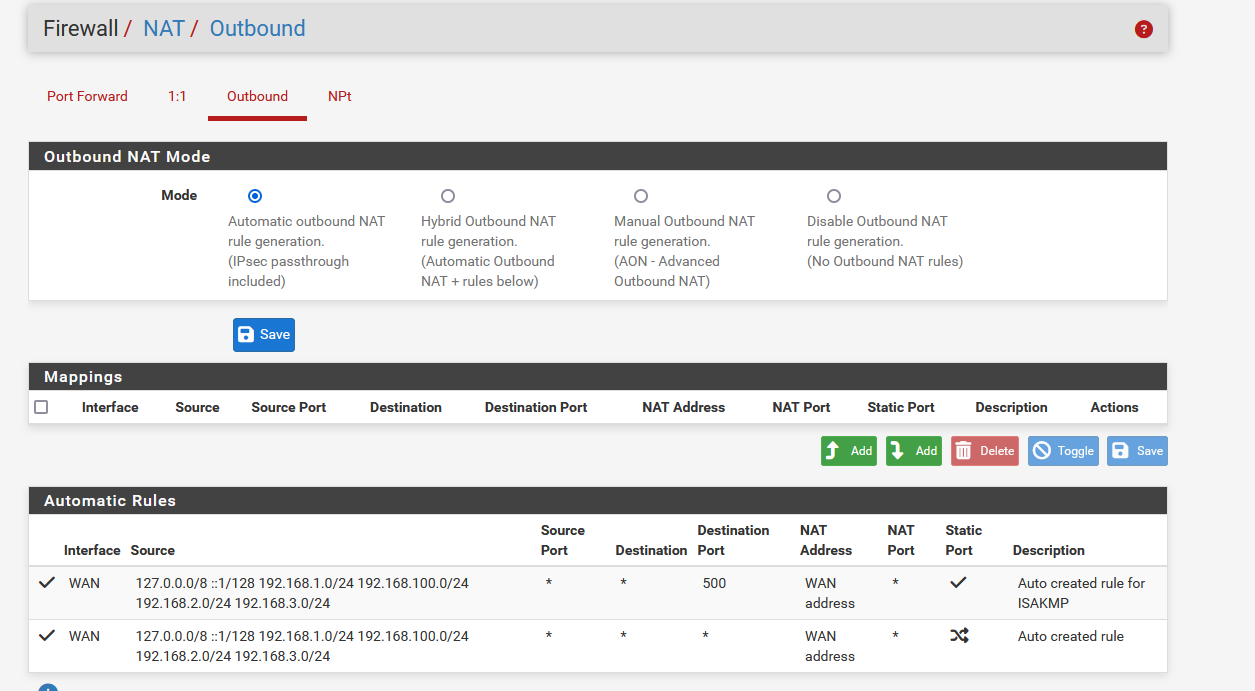
Set up with, for example : OpenVPN Remote Access Configuration Example
Don't forget to add rules on the OpenVPN interface - or instantiate it and set the rules on that interface.
-
I figured out the problem. Apparently there's something screwy regarding the bridged connections for my VMs (pfSense and OpenVPN clients) where if I try to force all traffic through the OpenVPN connection, it won't work (I am running VmWare Workstation)
I solved it by switching the external (WAN) and OpenVPN client box to NAT, and it worked just fine.