routing openvpn road warrior setup
-
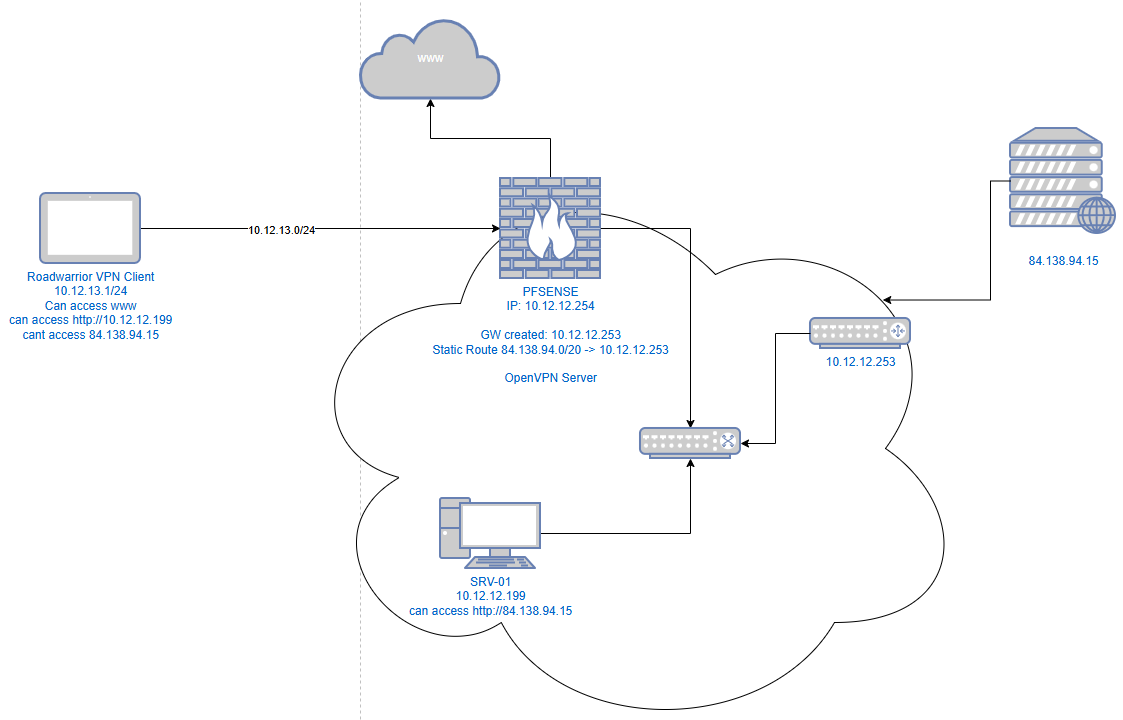
Question: do i need any further configuration so my roadwarrior vpn client user can access the ressources behind the 10.12.12.253 router and if yes can you explain? -
btw. i have another seup, where the additional router is plugged not in the switch but in the opt1 of the pfsense like:
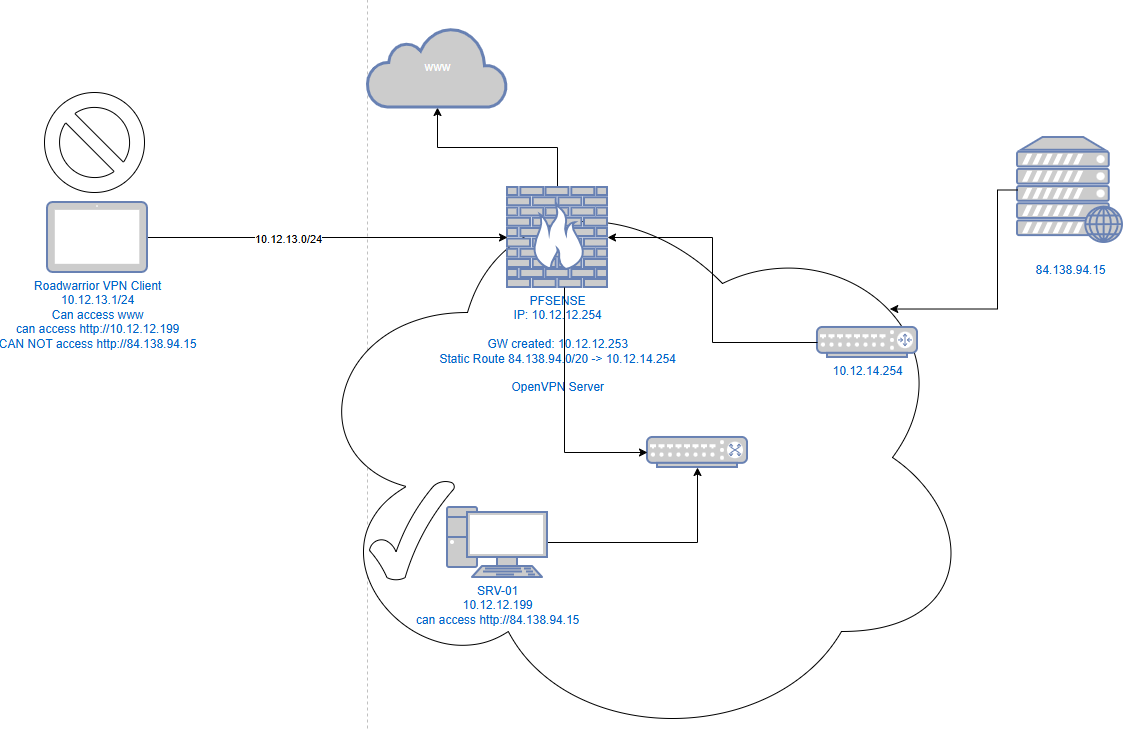 and there the road warrior can access the webserver behind the router only using the static route.. what am i missing?
and there the road warrior can access the webserver behind the router only using the static route.. what am i missing? -
what i think is, i need smth like a hidenat rule so packets from the vpn client will be send from the pfsense to the other router with the ip of the pfsense because the other router does not know where to send the packets with the ip of the openVPN tunnel adresses but for some reason i cant figure out how to set that up
-
@justanotherpfsenseadm said in routing openvpn road warrior setup:
Question: do i need any further configuration so my roadwarrior vpn client user can access the ressources behind the 10.12.12.253 router and if yes can you explain?
You also need to add a static route for the OpenVPN tunnel network on the other router and point it to pfSense.
If there is no possibility to do this you can masquerade the traffic on pfSense to get at least one-way access from the VPN client to the server.
-
@viragomann thx for your respone! i found a solution my self already.. guess it is what you pointed out
as far as i have no access to the other router i needed to create a 1:1 NAT rule with:
External IP: Lan Adress
Internal IP: 10.12.13.2
Destination IP: Alias with all Networks or single IPs behind or connected devices to 10.12.12.253 like 84.138.94.15i think that is what you call masquerade right?
-
@justanotherpfsenseadm
The 1:1 NAT translates the source IIP and destination IP of traffic in both directions:- In traffic from 10.12.13.2 to 84.138.94.15 it translates the source IP into the LAN address (S-NAT).
- Traffic from 84.138.94.1 to the LAN address is forwarded to 10.12.13.2 (D-NAT).
I don't think, that you really need the latter one.
Also, it only works for the single IP. If there connects multiple clients to the OpenVPN server only the first one can access 84.138.94.15.If you only need to enable access for OpenVPN clients to the server you can go with only an S-NAT rule.
You can configure this with an outbound NAT rule. Enable the hybrid outbound NAT mode. Then add a rule:
interface: LAN
source: OpenVPN tunnel network
destination: 84.138.94.15/32
translation: LAN address -
@viragomann oh ok, i will try that, thank your for that hint!
btw. do you know why this is not needed when the router is pluged not in the switch but in the opt1 port with a different network like in image 2?
-
@justanotherpfsenseadm
If the interface is configured as a DHCP client it possibly gets a gateway from the DHCP, or you've stated the gateway by yourself in the interface settings.
In theses cases pfsense automatically adds an outbound NAT rule.You can verify automatically generated rules at the bottom of the outbound NAT page.