Why do no floating rules match?
-
@Rockojfonzo where are those 2 networks at exactly connected to pfsense?
-
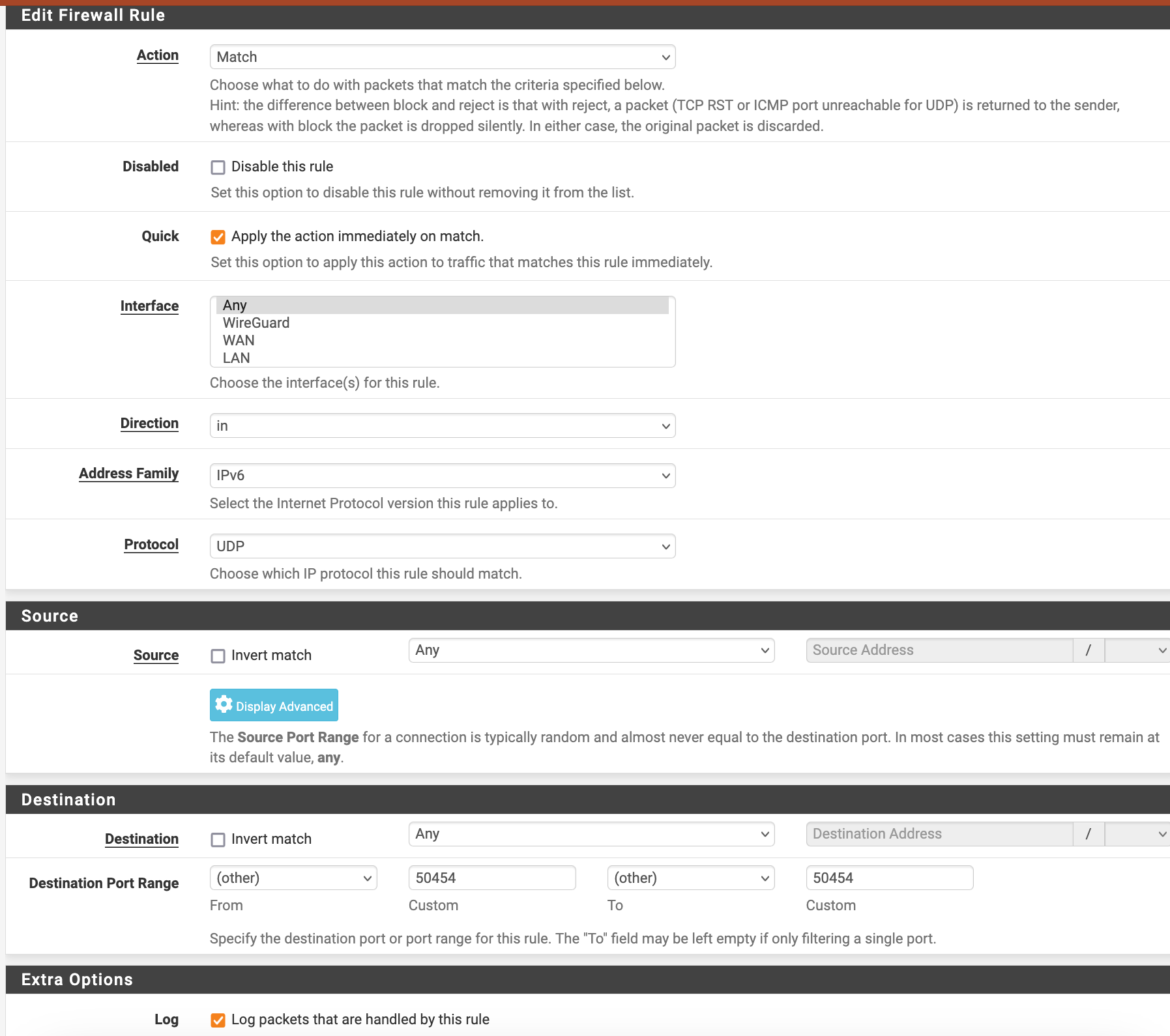
@johnpoz 192.168.100.0 is the remote side of the Wireguard tunnel (tun_wg0 so to say), 192.168.11.0 is on LAN (igc1)
I can match to destination 192.168.100.100:445 on LAN (which is "in" on LAN, out to Wireguard), but I need to limit (and therefore match) the packets that go out on LAN.
-
@Rockojfonzo I for sure do not know enough about how/where the firewall ties into the wireguard interface, etc.
Might be better to bring this up in the wireguard section.. On how to set limiters on this.. This seems like more related to that than actual firewall where packets enter and leave a physical interface or vlan.
Same could be related to say an ipsec or openvpn tunnel.. I have never tried tried or wanted to set a limit on such a connection. I have put some firewall rules on the openvpn interface - but never tried to match traffic so I could limit, etc. Maybe its just not possible, or need to do it a different way then match in a firewall rule?
-
@Rockojfonzo No worries, wouldn't do if I'm not interested. And I can't let go :) ... a SysAdmin thing, no sure.
After replacing the UPD simple-server with a Wireguard tunnel I observe the same as you, nothing gets logged.
Even if I enable logging for the default 'Wireguard' interface - in the firewall rules - allow-all-ip6 generic rule. The rules works and I can ping the pfSense from outside with it but it does not get logged. Not sure if that's a bug a limitation.
I guess @johnpoz suggestion makes sense to ask it in the wireguard section.
-
@patient0 Yeah, I read a lot about traffic shaping and VPN in the last days. That's why I didn't dream about doing something in the tunnel. But at least on the WAN interface or the (to my understanding) "de-VPNed" packets on the LAN interface should be "loggable".
However, thank you guys for all your energy and insights. I'll head over to the wireguard section and nag people there. ;-)
AND I will set up a similar thing on a pristine sophos xg that sits here and waits for installation. Let's see if it's worth the money. >:-) -
R Rockojfonzo referenced this topic on
-
Last notice on this: I built a setup with a Sophos XGS which doesn't support wireguard but IPsec. There I could track traffic (but only on non-floating rules!) without any problems, matching on addresses and/or ports.
So it seems to be only wireguard-related.