Unable to set up matching rules for traffic with Wireguard
-
Hi there,
I already tried to get answers in the "Firewalling" section but we're out of ideas there.I have a perfectly working WG tunnel that connects remote network 192.168.100.0/24 with local 192.168.11.0/24.
Now I want to just limit the traffic somehow. And for that I need a matching FW rule.
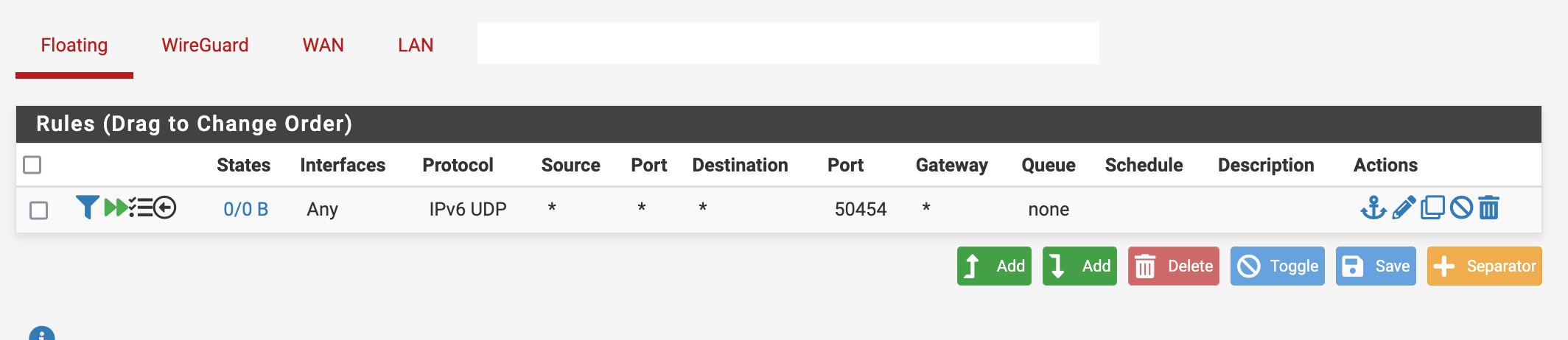
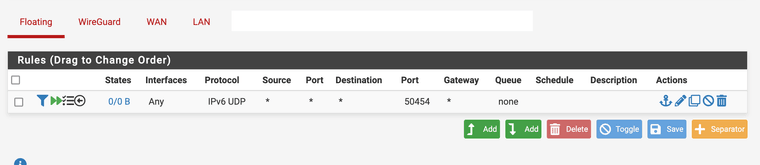
First attempt: The whole tunnel, running on port 50450:
[2.7.2-RELEASE][admin@fw]/root: tcpdump -ni igc2 port 50454 tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on igc2, link-type EN10MB (Ethernet), snapshot length 262144 bytes 20:21:17.215574 IP6 2abc:1234:1234:30::2ac4.50454 > 2abd:11:5678:5678::e228:6dff:feb9:4ae8.50454: UDP, length 96 20:21:17.215589 IP6 2abc:1234:1234:30::2ac4.50454 > 2abd:11:5678:5678::e228:6dff:feb9:4ae8.50454: UDP, length 96 20:21:17.233468 IP6 2abd:11:5678:5678::e228:6dff:feb9:4ae8.50454 > 2abc:1234:1234:30::2ac4.50454: UDP, length 96 20:21:17.233699 IP6 2abd:11:5678:5678::e228:6dff:feb9:4ae8.50454 > 2abc:1234:1234:30::2ac4.50454: UDP, length 96Rule: no match, no logging:
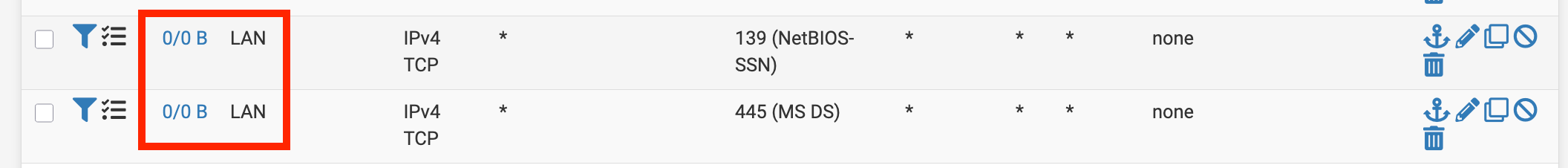
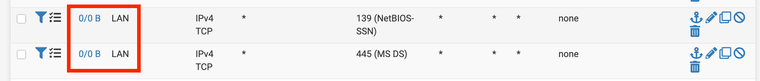
Next: Trying to match i.e. SMB 445 or 139 on LAN:
[2.7.2-RELEASE][admin@fw]/root: tcpdump -ni igc1 port 445 or port 139 tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on igc1, link-type EN10MB (Ethernet), snapshot length 262144 bytes 21:06:49.795443 IP 192.168.11.6.43750 > 192.168.100.100.445: Flags [F.], seq 3855556357, ack 853146708, win 229, options [nop,nop,TS val 1399014346 ecr 112590208], length 0 21:06:49.795459 IP 192.168.11.6.43752 > 192.168.100.100.445: Flags [S], seq 334166509, win 29200, options [mss 1460,sackOK,TS val 1399014346 ecr 0,nop,wscale 7], length 0 21:06:49.814822 IP 192.168.100.100.445 > 192.168.11.6.43752: Flags [S.], seq 3542171948, ack 334166510, win 28960, options [mss 1460,sackOK,TS val 112593711 ecr 1399014346,nop,wscale 7], length 0 21:06:49.814986 IP 192.168.11.6.43752 > 192.168.100.100.445: Flags [.], ack 1, win 229, options [nop,nop,TS val 1399014365 ecr 112593711], length 0 21:06:49.833525 IP 192.168.100.100.445 > 192.168.11.6.43750: Flags [F.], seq 1, ack 1, win 227, options [nop,nop,TS val 112593711 ecr 1399014346], length 0 21:06:49.833684 IP 192.168.11.6.43750 > 192.168.100.100.445: Flags [.], ack 2, win 229, options [nop,nop,TS val 1399014384 ecr 112593711], length 0Floating Rules (direction any, I tried "in" and "out" also): no match, no logging
I also tried this as an interface "Pass" rule.Are there any ideas you fine people have? Or is this impossible due to the nature of wireguard?
Thanks a lot!
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.