Removal of LAGG
-
Hi,
Further to an earlier post regarding changing the LAN card to a SFP+ card and no VLANs working - never did get it sorted.
However, I now have a spare PC with same config as the running one so can play about more!
Either way I decided to take it step by step this time.
First step was to remove the LAGG from Pfsense to first switch. I updated the LAGG to remove igb3 (LAGG was using igb2 & igb3) and all ok. Then I updated the interfaces (LAN plus all the VLANs) to use igb3 rather than lagg0. At this point there was no longer any internet access and APs down despite all the interfaces (WAN, LAN & VLANs) showing as up. Could ping from the pfsense PC out to google etc but not from LAN side.
Confirmed that the switch connected to the LAGG had been updated correctly to disable it and could connect to pfsense and switch via laptop and could ping all internal devices but not external. Now at a loss as to what I've done wrong!
It can't be that hard to remove a LAGG surely. I've also rebooted Pfsense but it made no difference.
I looked at previous posts for this but they suggested as I have done??
Any thoughts?
Steve -
@stevencavanagh you sure your rules are right if you changed interfaces around? Check that you have rules on the interface and also if dns is listening on the interface, etc.
Can you ping pfsense IP from your devices? What about your outbound nat?
-
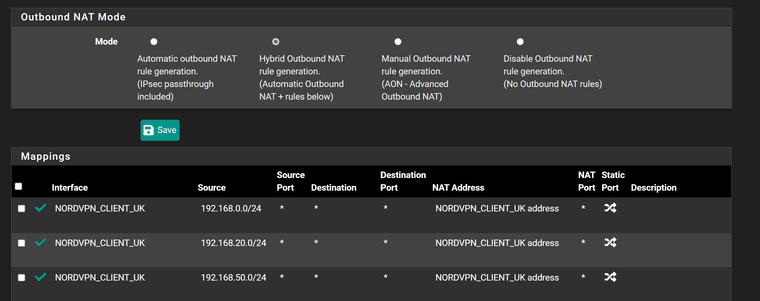
At this point I have only removed one part of the LAGG, would that affect any firewall rules? Could not see any that it would affect, neither in outbound NAT
-
@stevencavanagh yes, i could ping pfsense
-
@stevencavanagh not sure all you did - but that is what I would check off the list first. Changing interfaces could for sure lead to something changing.
If you can ping pfsense IP, and its the clients gateway, but can not ping 8.8.8.8 for example - either your rules are very limited, or outbound nat comes to mind. I would validate it.
Or what comes up very often where users saying internet doesn't work - its not actually a connectivity issue, but they are trying name resolution to www.google.com vs just a simple ping to an IP. And dns is the problem.
I would get a constant ping going to 8.8.8.8 for example - check your state table is being correctly natted to your wan IP? Or sniff (packet capture on pfsense) and validate that way.
-
Just to confirm, yes I can ping pfsense and it is the client gateway and no I cannot ping 8.8.8.8 from client but can from pfsense via wan. Which interface rules should I be concentrating on?
-
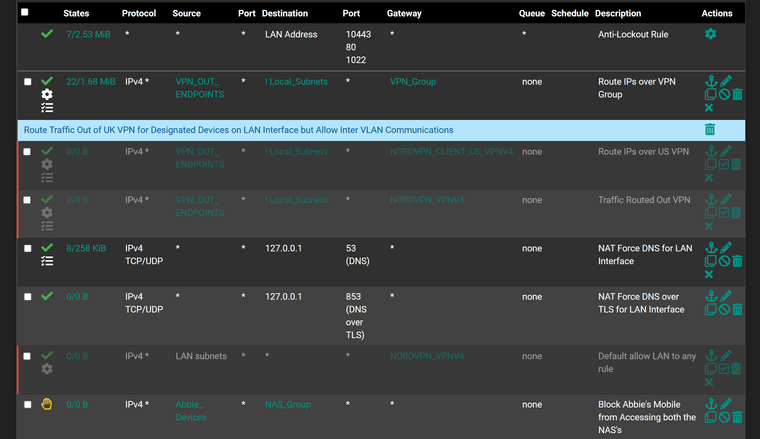
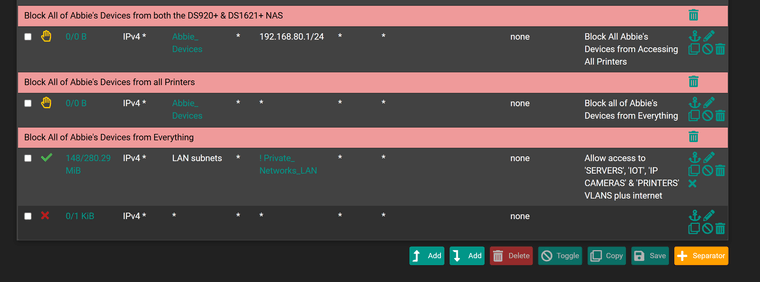
@stevencavanagh it would be the interface rules your client is talking too.. Unless you have some floating inbound/outbound rules.
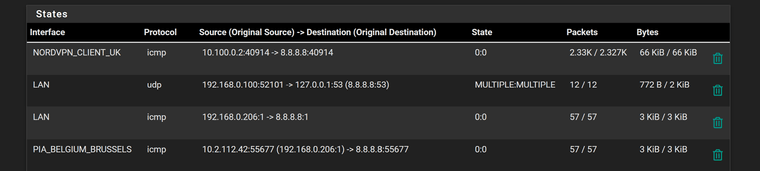
So when you try and ping 8.8.8.8 from your client - do you see state tables showing it went out the wan with the correct natted IP?
You should see 2 states..
Your lan side state, and then the outbound nat state
Where it is natted to your public IP.
-
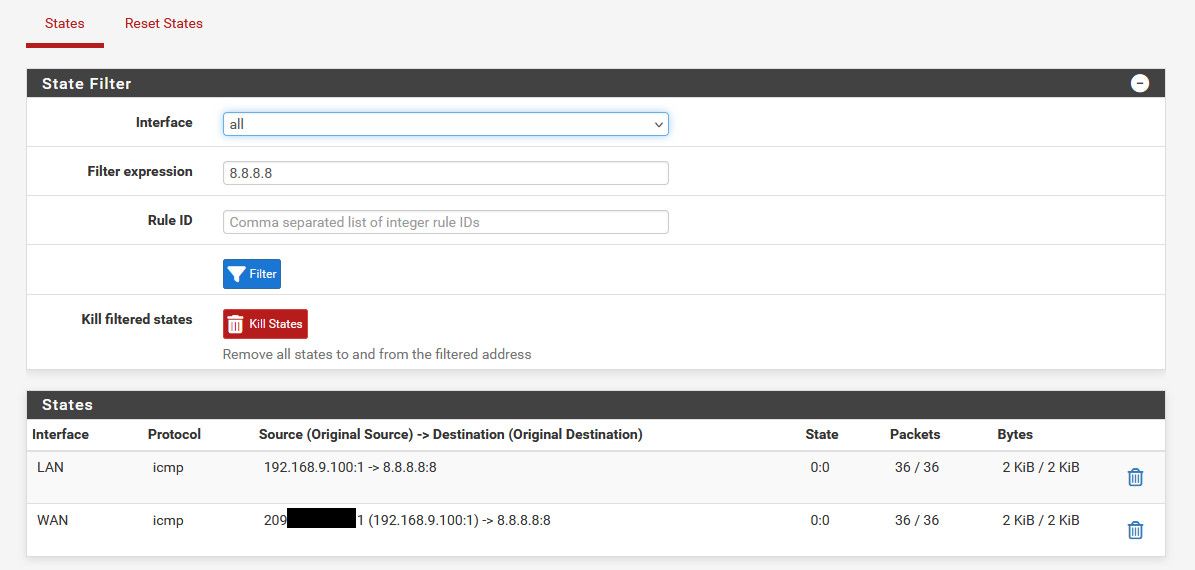
This is what I get from the working pfsense PC:-
I will now go and connect up the modified one and post back.
Btw - cannot see anything in NAT or firewall rules that reference the interface ie. igb3 instead of lagg0 as that is the only change I have made
-
@stevencavanagh so you also have vpn involved.. Another variable in the puzzle.
-
I do have it set up so it sends some traffic from certain IPs (mainly PCs) via the VPN group
-
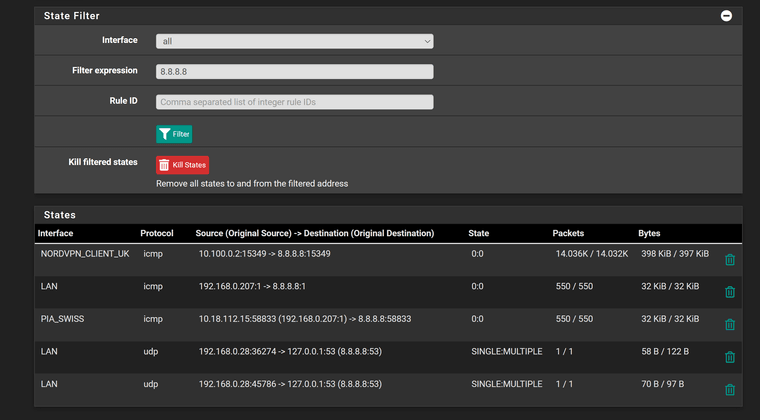
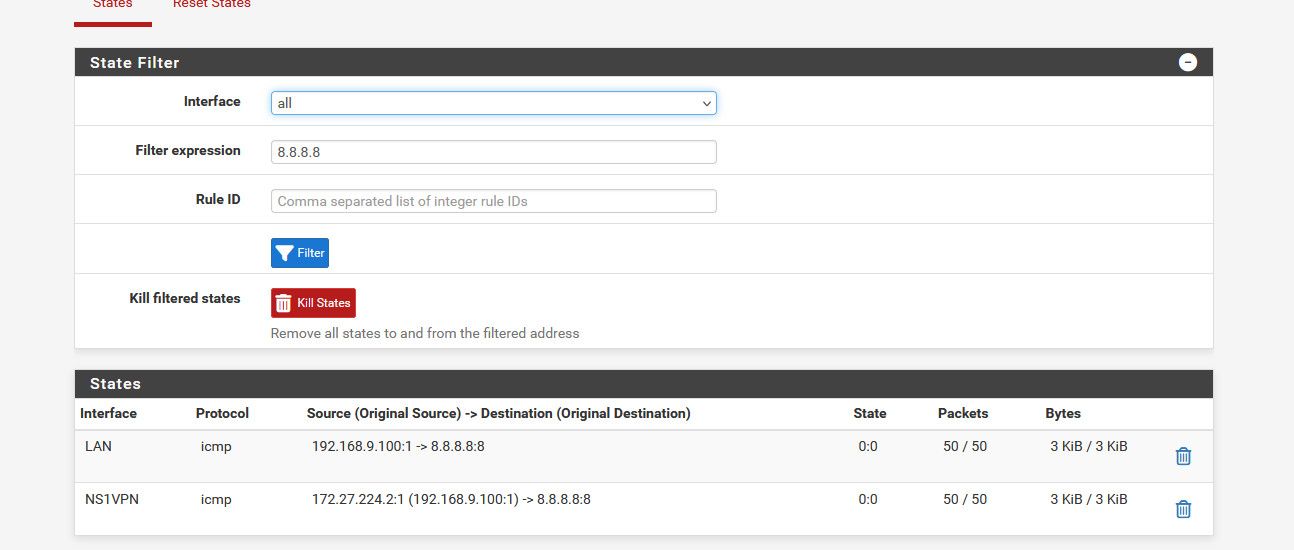
States with new pfsense PC connected ie. using igb4 for LAN and all VPNs and LAGG disconnected (igb2 & igb3).
Can ping pfsense from client via switch but no internet still. Ping continuously running to 8.8.8.8 and failing
-
@stevencavanagh well sure don't see any nat going on..
Looks like it sends it out your nordvpn_client interface unnatted to what should be what looks like your 10.100.0.2 address
I see 192.168.0.100 sending to 8.8.8.8, and then see your nordvpn interface send 192.168.0.100 to 8.8.8.8 -- when it should be natted
-
Sort out get it, so this mean I have an issue in the outbound nat?
-
Cant see anything wrong in NAT
-
-
@stevencavanagh well its not going to work if you don't nat..
Here I just setup a policy route. To route traffic out a vpn client I have for testing.. You can see its natted to the vpn IP.
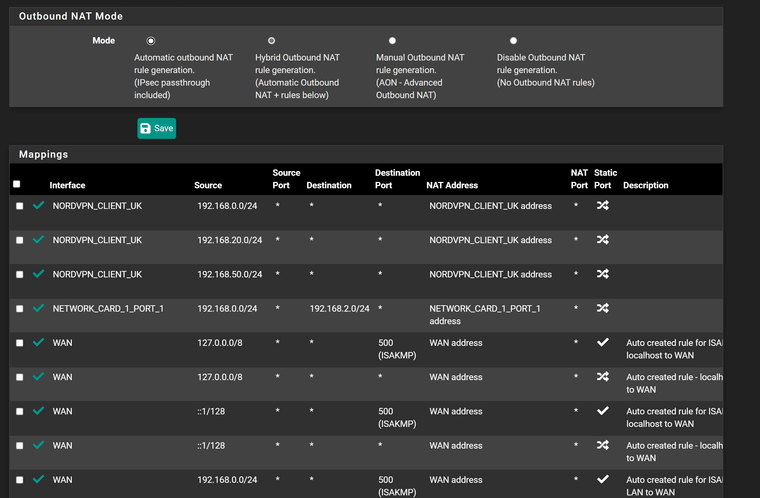
Without a full picture there is no way to know what you have missing.. What is the rest of the nat outbound rules.. What are the rules on the interface client is hitting.
But if your vpn client sends on the traffic with a source of 192.168.0.100 your vpn service isn't going to do anything with it.. So yeah no response.
-
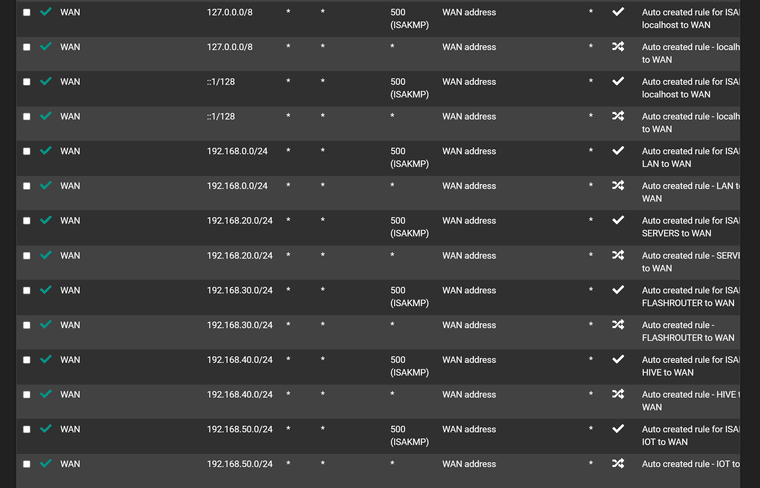
What I cannot get my head around is that same NAT rules work fine on old interface but not on new. I cannot find anywhere in pfsense where the interface is used except LAGG and assignments.
-
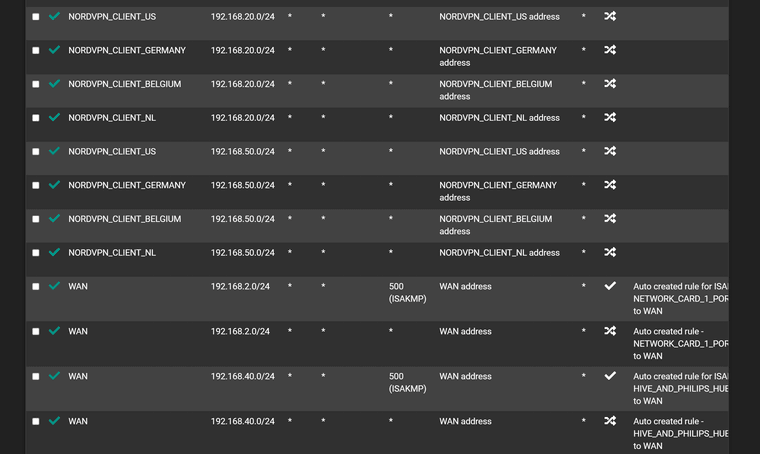
LAN interface rules
-
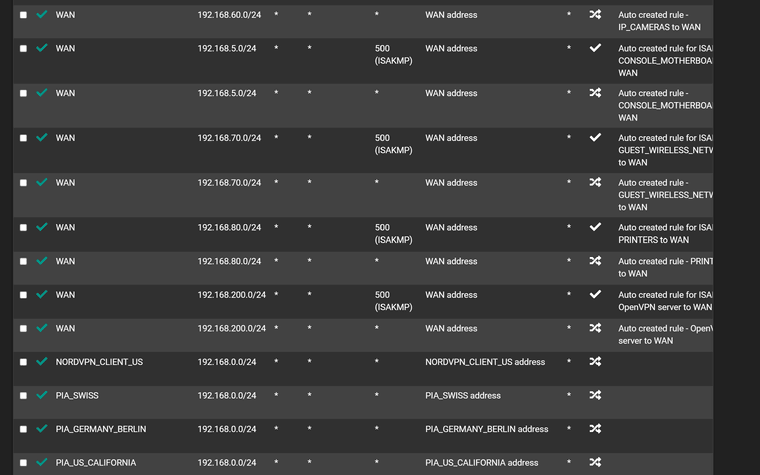
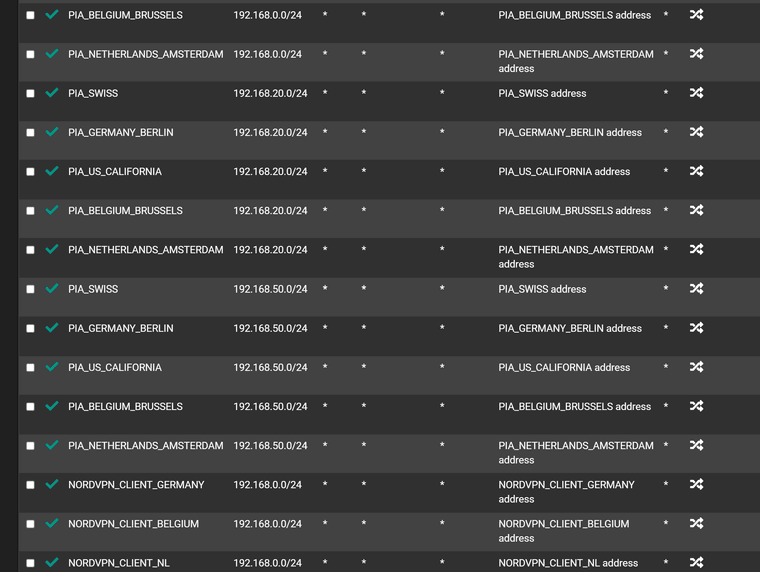
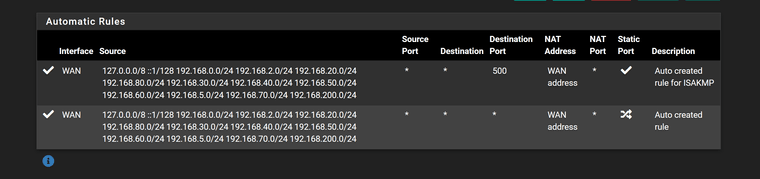
Outbound NAT
-
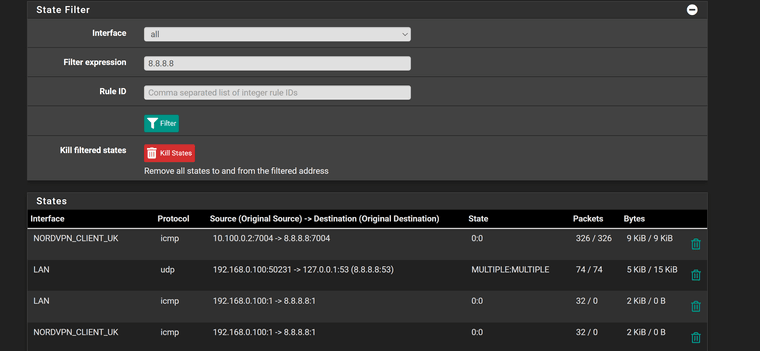
Not changed anything but...............
It now all works and only thing that seems to have changed is it is using PIA Belgium as VPN...........