Can someone explain why this rule gets triggered by Snort 3:19187?
-
@bmeeks Everything is identical between these machines when it comes to browser settings.
In the morning my smart TV was off, but I am still seeing this attempt. So the connection is coming from 8.8.8.8 and going to my VLAN. I don't really understand this behaviour because it must be initialized through pfsense or my switch. It is trying to reach out to my TV. Nowhere in my network I am using 8.8.8.8.Does the DNS resolver need to be restarted after saving changes?
1 UDP Attempted User Privilege Gain 8.8.8.8 53 10.0.10.2 37844 3:19187 PROTOCOL-DNS TMG Firewall Client long host entry exploit attemptCan Google not loading be related to Snort being in legacy mode and blocking 8.8.8.8? It always gets put on my block list when this alert pops up and I manually remove it. My block list otherwise is very limited with only 6 IPs on it. I also manually added 8.8.8.8 to the Pass List in Snort but it still ends up there again. Doesn't seem to work or maybe the Pass List must be activated somewhere else to work?
-
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
my Samsung Smart TV and set 8.8.8.8 as the DNS server inside the DHCP server on pfsense
Moments later :
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
Nowhere in my network I am using 8.8.8.8
?
Even if you undid all you've done, a samsung TV will probably also use 8.8.8.8.
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
So the connection is coming from 8.8.8.8 and going to my VLAN
That's new.
8.8.8.8 is a (DNS) server .
Example : The CNN web server won't contact your browser neither. Its your browser contacting the web server, and the web sever will answer back. Ones.
That's how Internet works.@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
Does the DNS resolver need to be restarted after saving changes?
When you change settings, or do nothing and just hit this button :
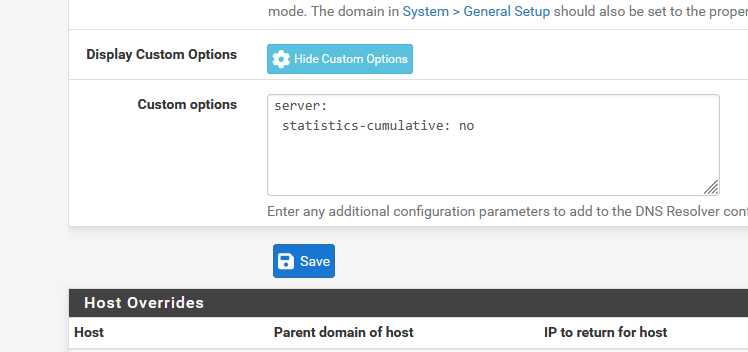
the config file of the resolver will be regenetared, and the resolver process will be restarted.
You saw this on top of the screen when you saved :
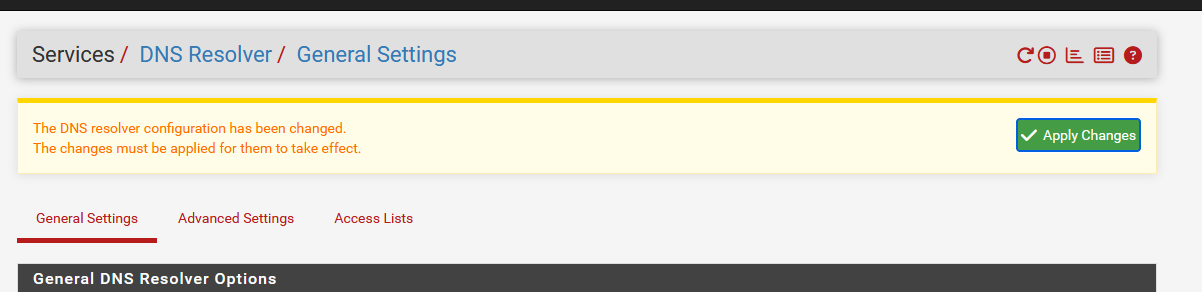
The actual regeneration of the config, and restart will happen as soon as you hit Apply.
-
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
Can Google not loading be related to Snort being in legacy mode and blocking 8.8.8.8? It always gets put on my block list when this alert pops up and I manually remove it.
Of course! That will impact anything that wants to communicate with IP address 8.8.8.8. Isn't that why you are running Snort in blocking mode in the first place -- to block stuff it thinks is bad? When you run Snort in blocking mode, then it certainly is going to block stuff. And everything that is blocked is most likely going to impact something on your network that was trying to communicate with the IP address Snort decided to block.
But as I've mentioned, 9 times out of 10 Snort gets it wrong and blocks stuff that is not malicious at all! Thus you have broken apps on your network because Snort is falsely blocking things that should not in reality be blocked. My recommendation to you is to immediately turn off the blocking mode in Snort. Go to the INTERFACE SETTINGS tab and uncheck the option to Block Hosts. Save that change and restart Snort on the interface. Then go to the BLOCKS tab and clear all the blocks. I bet things work better then. Just let Snort run in IDS mode (non-blocking) for several weeks to get a feel for what is normal traffic on your network. But I do not recommend running the package at all on a home network.
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
I also manually added 8.8.8.8 to the Pass List in Snort but it still ends up there again. Doesn't seem to work or maybe the Pass List must be activated somewhere else to work?
When you create a Pass List, you must manually assign it to an interface, save that change, then restart Snort on the interface so it sees the change. The Pass List is assigned on the INTERFACE SETTINGS tab.
But you are being tripped up by false positives, and the resulting unnecessary blocks inserted by Snort are breaking your network functionality. Turn it off and just relax!
-
@Gertjan said in Can someone explain why this rule gets triggered by Snort 3:19187?:
?
Even if you undid all you've done, a samsung TV will probably also use 8.8.8.8.
I removed 8.8.8.8 in pfsense DHCP server. I thought I mentioned it in the thread somewhere. So I found it strange that I am still seeing 8.8.8.8. Also checked the IP settings on the TV and DNS server is set to 10.0.10.1
And why is 8.8.8.8 the Source IP aka incoming connection? I also see Amazon and Akami IPs trying to get to my TVs IP. You can see it in the log here:2025-03-28 15:13:38 3 TCP Unknown Traffic 13.32.99.109 80 10.0.10.2 42980 120:3 (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE 2025-03-28 15:13:36 3 TCP Unknown Traffic 184.24.77.155 80 10.0.10.2 39331 120:3 (http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE 2025-03-28 15:13:07 1 UDP Attempted User Privilege Gain 8.8.8.8 53 10.0.10.2 51187 3:19187 PROTOCOL-DNS TMG Firewall Client long host entry exploit attempt 2025-03-28 15:13:07 1 UDP Attempted User Privilege Gain 8.8.8.8 53 10.0.10.2VLAN. 51187 3:19187 PROTOCOL-DNS TMG Firewall Client long host entry exploit attempt@bmeeks said in Can someone explain why this rule gets triggered by Snort 3:19187?:
But as I've mentioned, 9 times out of 10 Snort gets it wrong and blocks stuff that is not malicious at all!
I usually manually remove the IPs on the blocklist if they have a good reputation. But a few I left in there since they had bad reputation. For example this one. Would you unblock it?
https://otx.alienvault.com/indicator/ip/142.250.186.78
https://www.abuseipdb.com/check/142.250.186.78
Or this one which shows as a worm from January 25th and is located in Moscow
https://otx.alienvault.com/indicator/ip/2.16.168.118@bmeeks said in Can someone explain why this rule gets triggered by Snort 3:19187?:
My recommendation to you is to immediately turn off the blocking mode in Snort. Go to the INTERFACE SETTINGS tab and uncheck the option to Block Hosts. Save that change and restart Snort on the interface. Then go to the BLOCKS tab and clear all the blocks. I bet things work better then. Just let Snort run in IDS mode (non-blocking) for several weeks to get a feel for what is normal traffic on your network. But I do not recommend running the package at all on a home netwo
This is what I actually did. I let it run for about 3 weeks in non blocking mode. So things were broken before I even turned on the Block Mode. But maybe I should just turn it off. I just find it strange what I am seeing on my Samsung TV.
@bmeeks said in Can someone explain why this rule gets triggered by Snort 3:19187?:
Of course! That will impact anything that wants to communicate with IP address 8.8.8.8.
When I am using Google with Cloudflare set as my DNS in Firefox. Would 8.8.8.8 being on my blocked host list impact my search or prevent google search from loading?
-
@rasputinthegreatest: what interface are running Snort on? If your WAN, then you will see all kinds of noise there that can safely be ignored. The default configuration of pfSense is to DENY ALL on the WAN interface. That means it will accept no incoming unsolicited connection attempts at all. That is 100% secure and nobody from the Internet can initiate a connection unsolicited to your LAN. By "unsolicited", I mean without a device on your LAN first starting the conversation by sending a SYN packet. Research how stateful inspection firewalls operate to understand better.
But when you run Snort on an interface, it sees traffic on that interface before any firewall rules have been applied. So, when running on the WAN, it's going to see and alert on all the Internet noise but your default firewall rules are going to deny that traffic entry into pfSense and thus your LAN. So, Snort on the WAN will block needlessly because the firewall was already going to drop that traffic.
It sounds to me like you have tweaked too many things in your pfSense setup without fully understanding the implications of tweaking them. And that's why you are having issues. For example, you should not do anything to the DNS Resolver settings. Leave them at their default. Do NOT put any DNS servers in the SYSTEM > GENERAL SETTINGS box. Leave those blank and pfSense will default to using the local
unbounddaemon in resolver mode. Do not put any DNS servers in the DHCP settings. pfSense will default to handing out itself as the DNS server your LAN clients should use. And lastly, uninstall Snort and forget about using it. It is obviously not helping and is in fact making the situation worse.If you do a fresh pfSense install and don't change a single thing except maybe the IP subnet to use on your LAN, then things will just work. You do not have to add anything else -- no extra packages, don't touch any DNS settings, and generally don't touch DHCP except to enable it on the LAN if desired.
-
@bmeeks It's only my LAN interface since I heard WAN makes no sense.
I have reversed all these settings already to a vanilla pfsense install. So far I don't feel a difference in speed or website resolving unfortunately. Sometimes I need to refresh a page for it to properly load since it won't on first try. I also disabled Snorts blocking mode for now and just use it to monitor stuff. I was a lot more paranoid when I started getting into this stuff and seeing all these connections but pfsense at least gives me a peace of mind. Like you said. It's probably a set and forget situation for a home user. -
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
So far I don't feel a difference in speed or website resolving unfortunately.
Well, if you have reset pfSense to more or less its default settings and are still having issues, the next thing to check is your physical connection with your ISP. You may have problems with traffic flow down at layer 2 or perhaps layer 3 on your ISP's side.
You can post the content of your pfSense system log (under STATUS > SYSTEM LOGS) around the time you are experiencing issues with speeds or DNS resolution. Are all your LAN clients pointed to your pfSense firewall's IP address as their DNS Server?
-
@bmeeks Sorry for the late response. Some devices I don't trust are directly connected to the ISP router on a guest wifi. For example FireTV stick. Any client that sits behind the pfsense firewall has the DNS set to 192.168.1.1
I am using Proxmox on a server and noticed that in my VMs Mozilla Firefox struggles to load websites. If I switch to a Chromium based browser everything resolves instantly. I am starting to think the issue migh be Firefox itself. -
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
If I switch to a Chromium based browser everything resolves instantly. I am starting to think the issue migh be Firefox itself.
Be aware that Firefox defaults to using DoH, I believe, and it will attempt to communicate with a trusted partner DNS server over HTTPS. If you have something in your security setup that interferes with Firefox's ability to communicate with the DoH server that Firefox chooses on its own, then it will have trouble resolving hostnames and thus websites will appear slow or timeout completely.
When using a browser that supports DoH, and when that option is enabled, the browser chooses its own DNS server and ignores any DNS servers you attempt to provide. If that chosen server is blocked, the websites will be sluggish or timeout.
-
@bmeeks I never actively blocked anything regarding FIrefox and have no IPs blocked that belong to Firefox. It only happens in a VM so it must be the Proxmox layer that blocks something but couldn't find anything online about it.
-
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
o it must be the Proxmox layer that blocks something but couldn't find anything online about it.
Read again :
Virtualizing with Proxmox VE
VE
Did you notice that no where it's said that "Proxmox passes some traffic and block other traffic", or that it contains a hidden, "not-known" firewall.
So, I tend to think that, ones set up correcly, traffic passes. Proxmox doesn't handle UDP and TCP traffic that has a destination port 53 - also know as DNS traffic - differently.That said, imho, first, set up pfSense on a bare metal device. Ones that's done, works fine, you can go ahead and add a 'VM' into the mix.
Bare metal == way simpler. -
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
@bmeeks I never actively blocked anything regarding FIrefox and have no IPs blocked that belong to Firefox. It only happens in a VM so it must be the Proxmox layer that blocks something but couldn't find anything online about it.
I don't think you understood my point. Firefox, unless the "use secure DNS" option is disabled, will use the DNS services of trusted partners (meaning they have a deal with each other) for IP resolution using DoH (DNS over port 443 using SSL). If you have anything on your firewall (Snort, Suricata, pfBlockerNG, etc.) that is blocking DoH destination IPs or is attempting to do that, it would confuse the DoH lookups the Firefox browser attempts. It has nothing to do with IP addresses specifically related to FireFox itself.
@Gertjan did a good job explaining how Proxmox is pretty much going to be agnostic in terms of traffic. It is not going to be selectively blocking things unless you have have something misconfigured.
-
@bmeeks another question since I am still seeing something I can't explain. My phone was usually just connected to my guest wifi on my ISP router. I now connected it to an Access Point for the first time and seeing something I can't really make heads or tails of.
1 UDP Attempted User Privilege Gain 192.168.179.1 53 192.168.1.73 49294 3:19187 PROTOCOL-DNS TMG Firewall Client long host entry exploit attempt192.168.179.1 is the guest wifi on my ISP router and my phone is 192.168.1.73 that is connected to my Access Point that sits behind my pfsense box that sits behind the ISP router.
How can a guest wifi be the source if I am on another wifi and those networks should be totally isolated from each other by pfsense default WAN rules that block bogon and private networks.
Is this just happening because my phone has both networks saved but the source is 192.168.179.1 and not the other way around which would make more sense if my phone was reaching out to the guest network. But the guest network tried to reach my phone.
I don't see that behaviour from other phones on my wifi access point that sits behind pfsense but my phone has a lot of foreign IPs as source coming in.
-
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
@bmeeks another question since I am still seeing something I can't explain. My phone was usually just connected to my guest wifi on my ISP router. I now connected it to an Access Point for the first time and seeing something I can't really make heads or tails of.
1 UDP Attempted User Privilege Gain 192.168.179.1 53 192.168.1.73 49294 3:19187 PROTOCOL-DNS TMG Firewall Client long host entry exploit attempt192.168.179.1 is the guest wifi on my ISP router and my phone is 192.168.1.73 that is connected to my Access Point that sits behind my pfsense box that sits behind the ISP router.
How can a guest wifi be the source if I am on another wifi and those networks should be totally isolated from each other by pfsense default WAN rules that block bogon and private networks.
Is this just happening because my phone has both networks saved but the source is 192.168.179.1 and not the other way around which would make more sense if my phone was reaching out to the guest network. But the guest network tried to reach my phone.
I don't see that behaviour from other phones on my wifi access point that sits behind pfsense but my phone has a lot of foreign IPs as source coming in.
This is a DNS reply back to IP address 192.168.1.73 (which you said is your phone). The addresses listed in a Snort alert are SOURCE IP and PORT followed by DESTINATION IP and PORT.
-
@bmeeks The source is 192.168.179.1 (my ISP guest wifi) and there should be no way it can even reach my phone through the pfsnse firewall since it is a seperate network that should be blocked by the bogon/private networks rule. Maybe I misunderstand something. If I am not even connected to my guest wifi but an access point behind my pfsense. How is there communication between those two networks? I doubt my phone can be connected to both at the same time. Or is my phone periodically checking for availability of my guest wifi and that causes an alert?
-
@bmeeks said in Can someone explain why this rule gets triggered by Snort 3:19187?:
And Google or Cloudflare or NextDNS or OpenDNS would not get your DNS queries handed to them on a silver platter.
But your ISP will—which already has quite a bit more private information about you to correlate with your lookup data before selling all of the above.
@bmeeks said in Can someone explain why this rule gets triggered by Snort 3:19187?:
What is the next thing your client does? Yep, it connects to that IP address. So, all your ISP has to do is log the IP addresses you connect to and they know where you are going via a simple reverse DNS query or matching the IP with ASN lists.
The vast majority of services nowadays, including the naughty ones, make use of worldwide CDNs. So it's quite a bit more difficult (if not outright impossible) than the ISP simply performing a PTR or ASN lookup.
I thought you were going to suggest SNIs being sniffed from SSL handshakes—which currently is a real concern. But 1). it's presumably slightly more resource-intensive (i.e., larger packets, more complex parsing) for the ISP; and 2.) it'll continue to be mitigated by Encrypted Client Hello as adoption spreads.
Gotta ultimately pick your poison. One 'security and privacy'-maximizing solution in the current state of affairs might be to configure both Cloudflare and Quad9's DoT-capable resolvers (making sure to also specify the
cloudflare-dns.comanddns.quad9.netdomains respectively) in pfSense's DNS settings; configure Unbound to forward via DoT; and any/all other outbound UDP/53 and TCP/853 traffic blocked, together with a heavy dose of known-DoH server IP filtering via pfB. -
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
The source is 192.168.179.1 (my ISP guest wifi) and there should be no way it can even reach my phone through the pfsnse firewall since it is a seperate network that should be blocked by the bogon/private networks rule. Maybe I misunderstand something.
A diagram of how your network is connected would be most helpful here. I am not sure what is connected to what.
Where are you running the Snort instance that logged the last posted alert? Be aware that Snort places any interface it runs on in promiscuous mode. This will cause Snort to see all traffic traversing that physical interface.
The Snort alert you last posted is part of a DNS reply sent back to your client (you said this was your phone) by whatever device resides at 192.168.179.1. So, your phone initially sent a request which I assume was a DNS lookup request to somewhere. A state was created for that traffic, and when the targeted host replied its stateful reply was sent back to your phone (or whatever the IP address at 192.168.1.73 is).
Snort runs outside the firewall rules engine. That means Snort sees traffic on interfaces before any firewall rules have been applied.
-
[ Internet ] | | [ FritzBox Router ] Guest Wi-Fi: 192.168.179.1 | | (WAN port) [ pfSense Firewall ] WAN: 192.168.178.40 LAN: 192.168.1.1 | | [ Access Point / Wi-Fi ] | | [ Phone Device ] IP: 192.168.1.73As you can see my Fritzbox guest network is on 192.168.179.1. My WAN is on .178.
My pfsense is on 192.168.1.1I don't know how 179 could reach 178 because the guest wifi in a Fritzbox is completely isolated and I disabled that devices in that network can even communicate with each other.
-
@rasputinthegreatest said in Can someone explain why this rule gets triggered by Snort 3:19187?:
[ Internet ] | | [ FritzBox Router ] Guest Wi-Fi: 192.168.179.1 | | (WAN port) [ pfSense Firewall ] WAN: 192.168.178.40 LAN: 192.168.1.1 | | [ Access Point / Wi-Fi ] | | [ Phone Device ] IP: 192.168.1.73As you can see my Fritzbox guest network is on 192.168.179.1. My WAN is on .178.
My pfsense is on 192.168.1.1I don't know how 179 could reach 178 because the guest wifi in a Fritzbox is completely isolated and I disabled that devices in that network can even communicate with each other.
You did not tell me which interface you are running Snort on, so I still can't give you a concrete answer. But I can tell you that your Snort alert shows the device at IP 192.168.179.1 attempted a communication with a device at 192.168.1.73. Now, whether that communication attempt was successful or not I cannot say because I don't know which pfSense interface Snort was running on when it captured that traffic.
Perhaps things are not configured as you believe ??
-
@bmeeks Sorry for the missing info. Snort is running on the LAN interface on my pfsense port. Behind that port sit a switch and behind that switch is my Access Point. I don't think there is a faulty configuration because those networks are totally separate from each other. I don't know how traffic would be able to pass through that. Here are my settings that might be relevant.
General Setup:
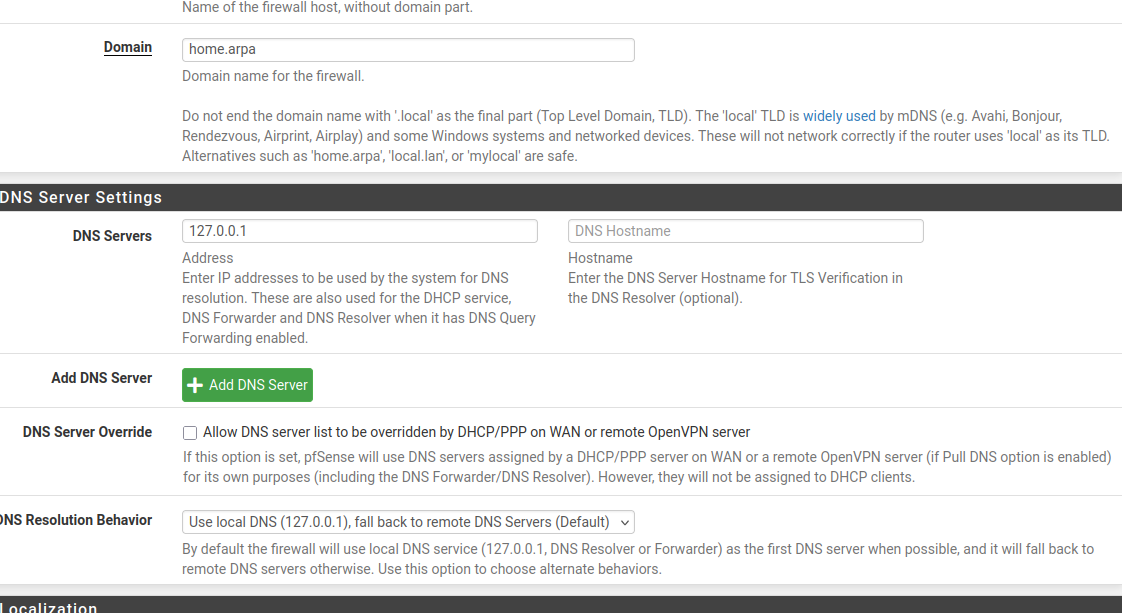
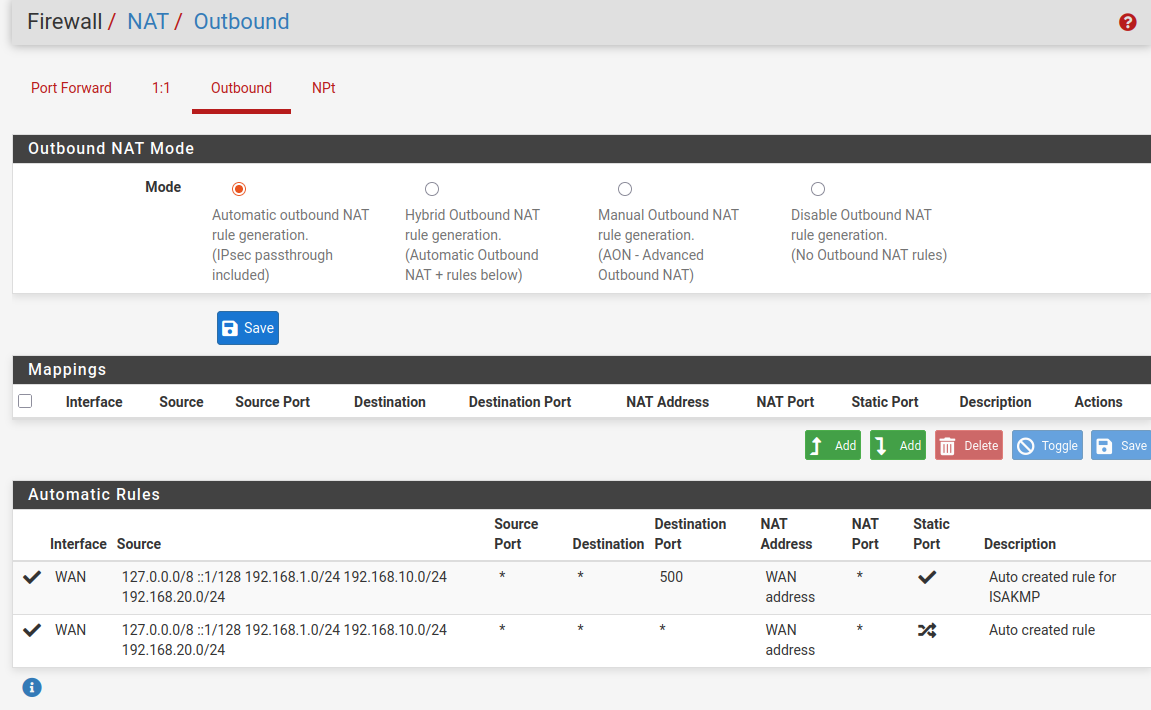
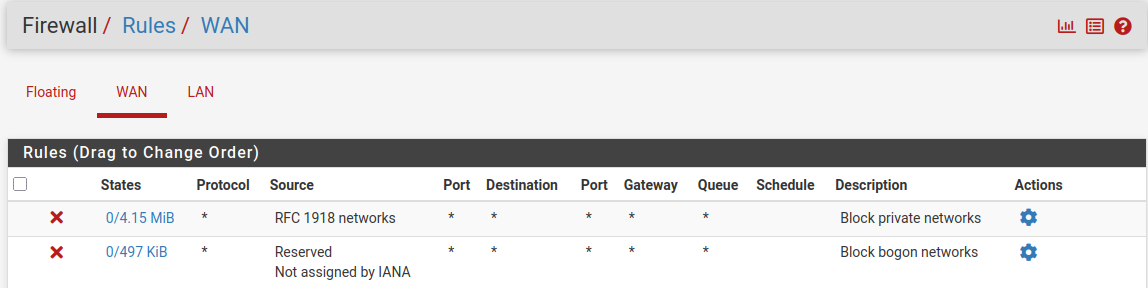
If I am using my Fritzbox without pfsense the network 192.168.178.1 can't even see 192.168.179.1
It's strange that it happend here. I don't have a good explanation.