using !rfc1918 won't work?
-
I've setup my servers VLAN with specific allow rules, those work like they should, but I also have some blocking rules, but there is something strange going on, maybe I'm doing something wrong...
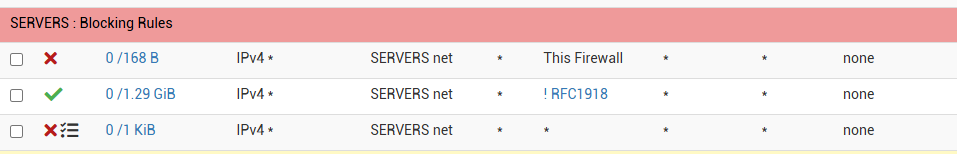
Whe I try to ping from a PC in the 10.10.70.x vlan to a pc in the 10.10.20.x vlan, the !RFC1918 firewall rule isn't stopping that traffic, it is stopped by the last rule in the image above?
The RFC1918 is an alias, setup with the following:
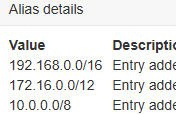
So I assume that part is correct?
What am I missing?
-
@houseofdreams on what interface/network is 10.10.70.x?
The rules on an interface are for traffic coming from the interface/network to the router (e.g. on interface LAN, for traffic from LAN to the router/world).
If you want to prevent 10.10.70.x to reach 10.10.20.x you have to set a rule on the 10.10.70.x interface. There your !RFC1918 rule would work.
-
All VLANS are on the same interface (vmx2)
10.10.70.x -> VLAN70
10.10.20.x -> VLAN20
....The more questions I ask on this forum, the more I seem to be doing wrong :/
I assumed that VLANS keep ALL traffic seperated from eachother, but now you say that even a "simple" RFC1918 blocking rule won't work when using vlans?
-
@houseofdreams said in using !rfc1918 won't work?:
the !RFC1918 firewall rule isn't stopping that traffic
It is an allow-rule (green), why should it stop anything. Indeed the traffic is stopped by the last rule or, if this rule would be missing, by the default deny rule, which always comes last and is not visible.
-
@Bob-Dig
Look at the ! (exclamation mark) before the RFC1918 alias. I made the rule, allowing all traffic, except the rfc1918 traffic? Or at least I assume this is how I think the "Invert match" option is supposed to work?
Now, when I tried reversing the rule, so make it a blocking rule and removing the "Invert match" checkbox, the rule actually does work.
So what use had this "Invert match" checkbox then?
-
@houseofdreams said in using !rfc1918 won't work?:
All VLANS are on the same interface (vmx2)
No no, maybe it's an issue of term: if you have created a VLAN and assigned it to an interface on pfSense that counts as an interface. And as a result it gets it's own firewall rule tab.
Can you show us the interface assignments ? And what firewall rules you have for which interface/vlan?
The more questions I ask on this forum, the more I seem to be doing wrong :/
Some clever man (not me!) wrote/said: the more you know, the more you know what you don't know.
-
@houseofdreams said in using !rfc1918 won't work?:
So what use had this "Invert match" checkbox then?
It is doing exactly what it means, inverting. Your rule is allowing IPv4-traffic from servers.net IP-addresses towards everything not in RFC1918, so usually the internet. But the rule itself is not blocking anything, it is only partially allowing things, it is an allow-rule afterall.
-
@houseofdreams said in using !rfc1918 won't work?:
All VLANS are on the same interface (vmx2)
Firewall rules are per interface, which are in your case virtual.
You have firewall page called 'VLAN70' with its own rule set.
You can (should) use a firewall alias called 'VLAN70.net' which stands for "10.10.70.0/24".
The same for VLAN20 - and 10.10.20.0/24.Your SERVERS.net is another interface I presume ?
This :

is not normal.
The alias "This Firewall" stand for all the IPs pfSenses uses (all interface and the pfSense localhost = 127.0.0.1) so none of the devices connected to the SERVERS.net can use the DNS services of pfSense ..... Are you sure that's what you want ?
Normally, you can 'trust' your servers as they are manged by you, the admin, and not some ignorant end-user.The next one is also strang :

You pass traffic that goes to 'everything' (the entire internet) except local IP'S (RFC1918 networks or IPs)
But wait, your SERVERS.net hosts servers, right ?
Servers never contact other (client ?!) devices. Its a client "from somewhere" that contact the servers, and then the server, over the created state, which isn't on the SERVERS.Net interface, will answer.
Ok, true, servers can decide to initiate an auto-going connection to another server, like : they contrat the Microsoft Update services to check if there is an update, or they go out using the NTP protocol to sync the time.
Or a DNS host name has to be resolved, and the server (a mail server !) connects to ... pfSense (something you forbid with the first rule) or some other DNS server, like 8.8.8.8. ... etc. -
@houseofdreams said in using !rfc1918 won't work?:
he !RFC1918 firewall rule isn't stopping that traffic, it is stopped by the last rule in the image above?
which is exactly what should happen..
So with this traffic walk through your rules.
ping from a PC in the 10.10.70.x vlan to a pc in the 10.10.20.xDoes any of that traffic match this firewall? Nope unless 20.x was a firewall IP that rule doesn't match, so down to the next rule
Is 20.x NOT (you have bang !)? Nope it is a rfc1918 so that rule doesn't trigger either, down to next rule.
Is 20.x Anything? Yup that would be included in your * (any) as destination, that rule triggers and says block that traffic.
Rules are evaluated top down, as the traffic enters an interface from the network that interface is attached too.. First rule to trigger wins and no other rules are evaluated..
-
This is the complete ruleset of VLAN 70 (SERVERS)
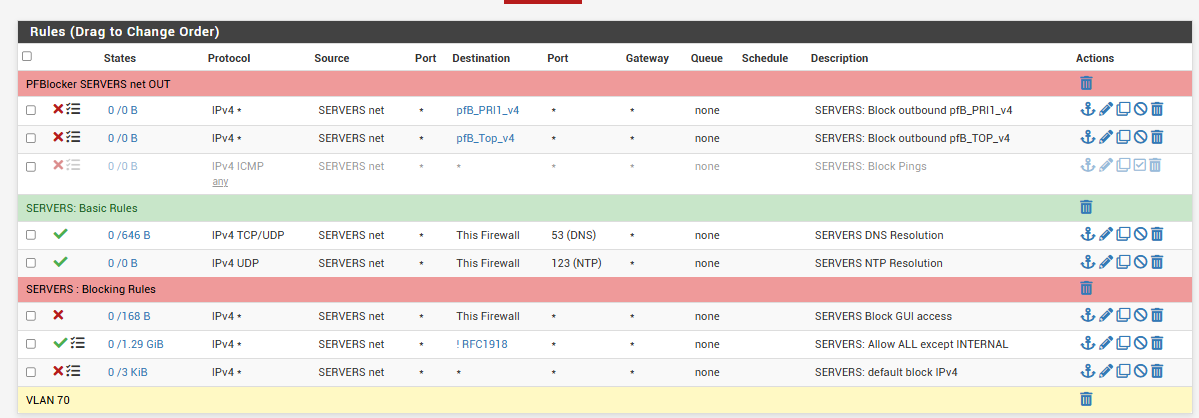
Maybe it's easier to explain what I'm trying to accomplish?
I want to configure, that all servers in VLAN70 SERVERS only can contact the internet, but nothing else on the other VLANS. In short, this would be very easy to do I assume, I think I'm seriously overcomplicating things..
What I also wanted, I allready know that it's not possible with my current setup: I want to isolate each server on VLAN70, so that each server can only reach the internet, but no other server in the same vlan. But as I said, I allready got the idea that this isn't going to be possible without major changes, or am I wrong?
PS: the first 2 rules are PFBlocker rules, to make sure that even if a server should be hacked, most known IP targets are blocked outgoing. (But yeah, even a mediocre hacker could easily go around this, but I'm trying to make it at least a little more difficult)
PS: with the "Block GUI access" rule, I want to accomplish, that no server can contact the PFsense gui. All DNS / UTP are still allowed
-
@houseofdreams said in using !rfc1918 won't work?:
I want to configure, that all servers in VLAN70 SERVERS only can contact the internet, but nothing else on the other VLANS.
Your rules do that.. But I wouldn't use a allow !rfc rule there.. I would block access to rfc, and let your last rule be an any any rule.
Here is an example of rule set that allows specific stuff to pfsense, ping, dns, ntp.. But blocks access to all other networks locally, because they are all rfc1918 IPs, and then last rule allows anything else - ie internet
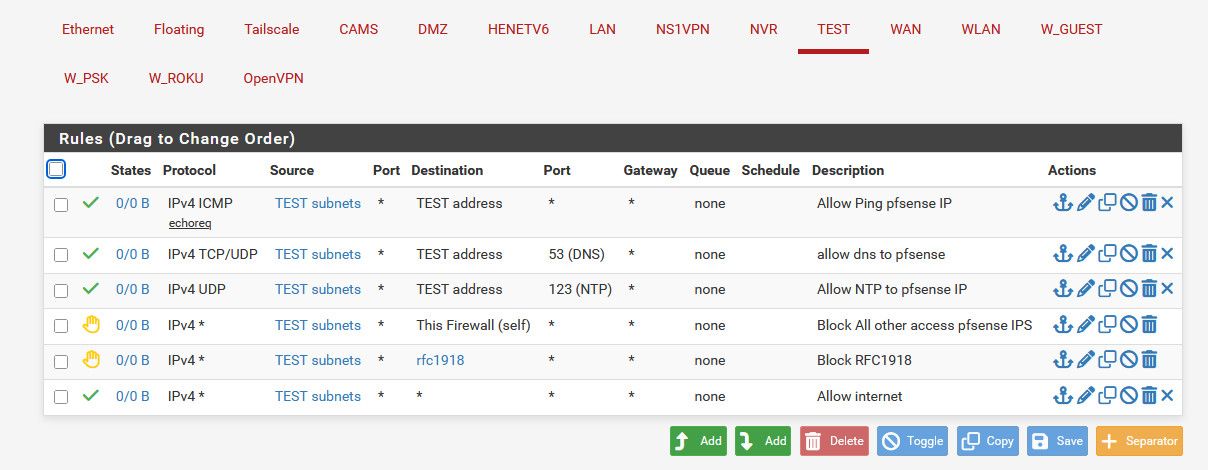
If your goal is to block access to say the web gui, your ! rfc rule would allow access to the pfsense wan IP - which is normally a public IP, so not rfc1918..
-
@houseofdreams said in using !rfc1918 won't work?:
that all servers in VLAN70 SERVERS only can contact the internet, but nothing else on the other VLANS.
"Servers" never** initiate a connection to another device.
Servers serve.
They accept connections going to (into) the servers.** as said above, servers can also make outgoing connection for their own houskeeping. They won't go looking for stuff on some RFC1918 range == your local (V)LANs, except if you told them to do so.
DNS requests is another example. -
@houseofdreams said in using !rfc1918 won't work?:
But as I said, I allready got the idea that this isn't going to be possible without major changes, or am I wrong?
You are right this time. If you want to separate all servers from each other, every server needs its own (V)LAN. I do this too.