NAT from internet host through WAN to VPN connected host on specific tcp port
-
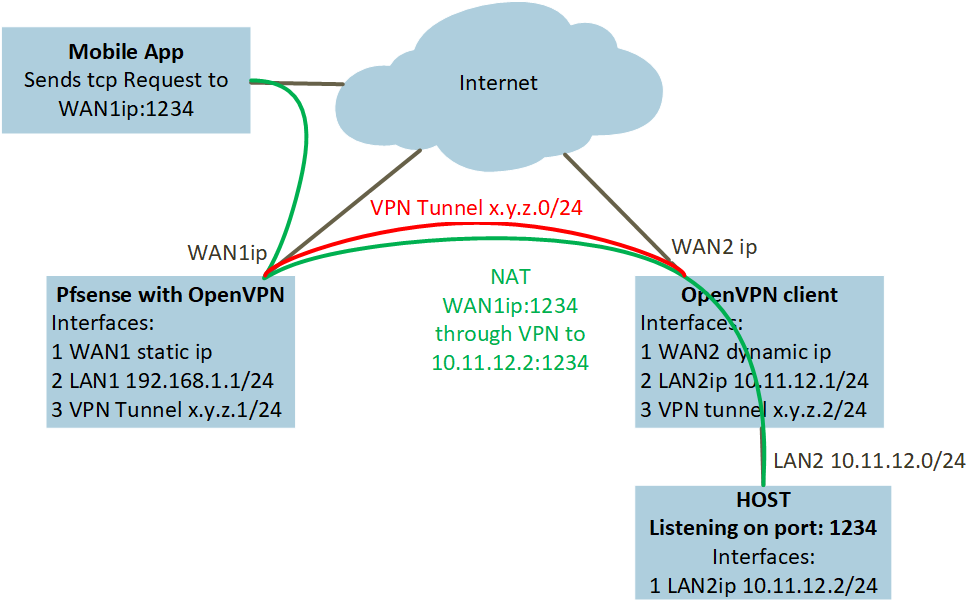
I need to configure pfSense with OpenVPN to service a internet connected mobile app. Just as i have tried to visualize on the drawing.
The App connects to WAN1ip:1234 this has to be NAT to the host on LAN2ip:1234.From LAN1 it is possible to ping LAN2 hosts.
From LAN2 it is possible to ping LAN1 hosts.
From LAN1 and LAN2 it is possible access internet.
LAN2 is not required to access internet through VPN.What i have done is:
- Outbound Nat Mode is set to Hybrid Outbound NAT rule generation.
- A NAT from WAN1ip:1234 to LAN2ip:1234 are created.
- A VPN interface is created.
- Default rule for tab OpenVPN is disabled.
- A rule at tab VPN with Protocol IPv4*, Source Any, Port Any, Destination LAN2, port any is configured. The rul shows no traffic.
The result is: - Packets from App through WAN1ip:1234 is passing.
- The app does not get any response, like the request is not forwarded correct or not following the correct return path.
Is there any guides or sugestions how to make this setup function?
-
@Martek said in NAT from internet host through WAN to VPN connected host on specific tcp port:
What i have done is:
Outbound Nat Mode is set to Hybrid Outbound NAT rule generation.And didn't you add a rule?
Basically this might be an issue of the client, routing response packets to its default gateway instead of routing them back to the server.
I don't know its capability, so I cannot give any hints on how to solve this.On the server you can masquerade the traffic destined to the LAN2 IP with an outbound NAT rule on the VPN interface. So the client sees the server IP as source IP in forwarded packets and will route back response packets properly then.
-
@viragomann Thanks for your response.
But I am not sure what I specific must do?
On Firewall > Rule > VPN interface:
i have added the following rule.
Protocol Source Port Destination Port Gateway Queue
IPv4 * * * * * noneOn Firewall > NAT > Outbound:
Mode is set to "Hybrid Outbound NAT rule generation" and i have added the following mappings.
Interface Source Source Port Destination Destination Port NAT Address NAT Port Static Port
WAN1 LAN2 * * 500 (ISAKMP) WAN Address * Yes
WAN1 LAN2 * * * WAN Address * No
VPN LAN2 * * * VPN Address * NoOn Firewall > NAT > Port Forward:
Interface Protocol Source Address Source Ports Dest. Address Dest. Ports NAT IP NAT Ports
WAN1 TCP * * WAN address 1234 HOST 1234There is no static routes configured.
From LAN1 > LAN2 it is possible to connect to hosts on any port.
From LAN2 > LAN1 it is possible to connect to hosts on any port.
LAN2 is not forced to direct traffic through VPN tunnel.
From firewall log i can see that packets hidding WAN1ip:1234 packets is passed and forwarded to HOST:1234.
Nothing more is possible to see in the log. Which makes me Wonder if the fraffik is not forwarded to VPN.I have no idea of what i miss. Any suggestions on how to make this Work?
-
@Martek
Still stepping in the dark about the VPN client and its capabilities. Is it a router, is it pfSense as well or is it something else?
I sadly cannot give straight simple instructions on basis of unknown parameters. -
@viragomann
The client is a device with the OpenVPN support. My posibility is to use "Client Specific Overrides" to adjust that end of the VPN tunnel.The device is a Milesight UR32S which use ADSL for WAN and LTE as a failover. I a host on the lan side receives a connection via the VPN, i expect it will respond with return path via the VPN. That is what happen when i connect from LAN1 to LAN2.
However using "Client Specific Overrides" with "Redirect Gateway: Force all client generated traffic through the tunnel" to be set, doesn't change the result.
-
@Martek said in NAT from internet host through WAN to VPN connected host on specific tcp port:
My posibility is to use "Client Specific Overrides" to adjust that end of the VPN tunnel.
Yeah, the CSO is needed on the server to route the traffic to the proper client. But it doesn't do anything on the client side.
However using "Client Specific Overrides" with "Redirect Gateway: Force all client generated traffic through the tunnel" to be set, doesn't change the result.
I'd expect, that it would work with this option, presumed the route on the client is really added.
This would route any upstream traffic from the client over the VPN, however, but not only responses on the forwarded requests. Is this, what you want?If so the outbound NAT rule on WAN for LAN2, you mentioned above, is needed to get internet access.
For testing the routing, on pfSense try to ping the host in LAN2 from the LAN1 IP. Ensure that the firewall of the host itself doesn't block access from outside.
Also check if the upstream traffic is routed over the VPN by accessing whatismyipaddress.com or something else showing you source IP.