CRASH REPORT CAPTIVE PORTAL
-
Crash report begins. Anonymous machine information:
amd64
14.0-CURRENT
FreeBSD 14.0-CURRENT amd64 1400094 #1 plus-RELENG_23_09_1-n256200-3de1e293f3a: Wed Dec 6 21:00:32 UTC 2023 root@freebsd:/var/jenkins/workspace/pfSense-Plus-snapshots-23_09_1-main/obj/amd64/Obhu6gXB/var/jenkins/workspace/pfSense-Plus-snapshots-23_09_1Crash report details:
PHP Errors:
[06-May-2025 22:06:40 Asia/Manila] PHP Fatal error: Uncaught ValueError: escapeshellarg(): Argument #1 ($arg) must not contain any null bytes in /etc/inc/voucher.inc:247
Stack trace:
#0 /etc/inc/voucher.inc(247): escapeshellarg('\xEF\xBF\xBD\xEF\xBF\xBD\xEF\xBF\xBD\xEF\xBF\xBD\x00LE...')
#1 /usr/local/captiveportal/index.php(207): voucher_auth('\xEF\xBF\xBD\xEF\xBF\xBD\xEF\xBF\xBD\xEF\xBF\xBD\x00LE...')
#2 {main}
thrown in /etc/inc/voucher.inc on line 247No FreeBSD crash data found.
-
I presume you use vouchers ?
What is the pfSense beta version you use - the latest (end of April "20250429") ?I'm not using the beta version after 2.7.2, "2.8.0", but 25.03 latyest beta, and normally I'm not using vouchers.
But I've activated vouchers, created a new roll with 10 vouchers, and tried one :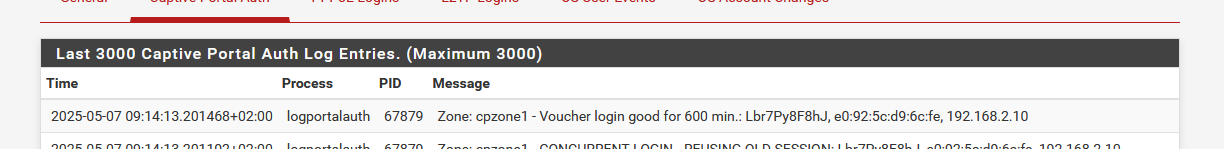
From what I make from the error :
must not contain any null bytes
or, the text string parsed is the voucher code entered 'manually' by the captive portal user on the login page.
The function voucher_auth($voucher) is called with the voucher code, like
voucher_auth("Lbr7Py8F8hJ"); where "Lbr7Py8F8hJ" was entered by the user.
Your portal user entered \xEF\xBF\xBD\xEF\xBF\xBD\xEF\xBF\xBD\xEF\xBF\xBD\x00LE... and yeah, I can see clearly the null byte '\x00'.
Very possible : someone is pasting 'something' into the voucher login page field, and the portal script code isn't fool-proof enough to detect that. I agree, it should disregard text that.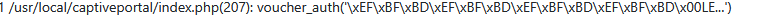
Vouchers are generated with info you've supplied upfront, like :
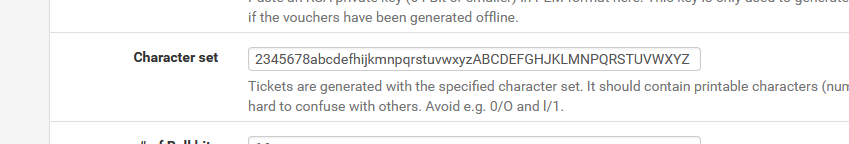
so if a voucher code contain 'text' anything other that what's outside of the character set, like a null byte, it should be disregarded.
It look likes that test is actually done : look here : line 251. The /var/etc/voucher_cpzone1.cfg file contains this info, but that's moments to late, at line 242 just above the escapeshellarg() function already took the bullet - the PHP function escapeshellarg() fails.That said, I 'tested' a voucher code by entering pure BS into the voucher test filed to see if it was valid.
Just for fun, I copy pasted the binary code of the executable /usr/local/bin/voucher" and that will contain loads of null characters.
No PHP errors, all I saw was a big list GUI warnings like :
Note that the erroneous binary chars are copied verbatim to the html GUI output - that's not good neither.
-
@Gertjan Thank you for your response, we will uodate the pfsense to the newest version, and try to check again if it will crash.
-
@Summer1000 said in CRASH REPORT CAPTIVE PORTAL:
will uodate
?
Oops.@Summer1000 said in CRASH REPORT CAPTIVE PORTAL:
amd64
14.0-CURRENT
FreeBSD 14.0-CURRENTand also :
@Summer1000 said in CRASH REPORT CAPTIVE PORTAL:
pfSense-Plus-snapshots-23_09_1-main
I didn't spot the ancient software ...
Yeah, suddenly : you experience ancient bugs.
Good news : solved months ago ^^And it gets better : I'm using the latest beta 25.03 version, with a captive portal, and it works great.