🔒 OpenVPN: Allow Internet via WAN IP but Block LAN Access (Hybrid Split/Full Tunnel)
-
Hi everyone,
I’m trying to configure a somewhat specific setup using pfSense and OpenVPN, and I could use some guidance. Goal:
Goal:
Allow a collaborator to connect via VPN and use my static WAN IP to access the internet, while completely blocking access to the LAN. Current Setup:
Current Setup:- I created an OpenVPN server (TUN mode).
- The client connects to a dedicated VLAN with no access to other interfaces.
- The client should not be able to access the internal LAN.
- The idea is that traffic from the VPN client should exit through my WAN IP (NATed by pfSense), just like a full tunnel.
 Problem:
Problem:
This setup behaves like a split tunnel, so the client continues using its local internet connection.
I found a workaround online suggesting the following lines in the OpenVPN server’s “Advanced Configuration”:push "route 0.0.0.0 128.0.0.0";
push "route 128.0.0.0 128.0.0.0";This does indeed force full tunnel behavior, but it also opens up access to all networks defined in pfSense.
I already have other VPNs configured as full tunnel, so I cannot apply restrictive firewall rules globally, as that might affect those existing VPNs. Security Requirements:
Security Requirements:- NO access to the LAN.
- YES, use of my WAN static IP for outbound internet traffic.
 Questions:
Questions:- Is there a proper way to force all internet-bound traffic from the VPN client through pfSense, while completely isolating it from the LAN?
- Has anyone implemented a similar setup? Any best practices to share?
- Should I be looking into policy-based routing on the OpenVPN interface, or is it better to rely on full tunnel with client-specific rules?
Thanks in advance for any insights!
-
@Aadrem said in
 OpenVPN: Allow Internet via WAN IP but Block LAN Access (Hybrid Split/Full Tunnel):
OpenVPN: Allow Internet via WAN IP but Block LAN Access (Hybrid Split/Full Tunnel):push "route 0.0.0.0 128.0.0.0";
push "route 128.0.0.0 128.0.0.0";This is the same as checking "redirect gateway".
This setup behaves like a split tunnel, so the client continues using its local internet connection.
No, it adds routes to the client for the whole IPv4 range. This is not split tunneling.
The client will only be able to access devices within his local subnet, but any other traffic will be routed over the VPN, and this is what you need in fact.I already have other VPNs configured as full tunnel, so I cannot apply restrictive firewall rules globally, as that might affect those existing VPNs.
You can restrict the rule for pass traffic to WAN / block local subnets to the clients source IP.
You can also assign an interface the the respective OpenVPN server. Then you get a firewall rule tab, where you can add rules for this instance only.
If you only want to allow internet access it's a good advice to create an alias, which includes all private network ranges like this:
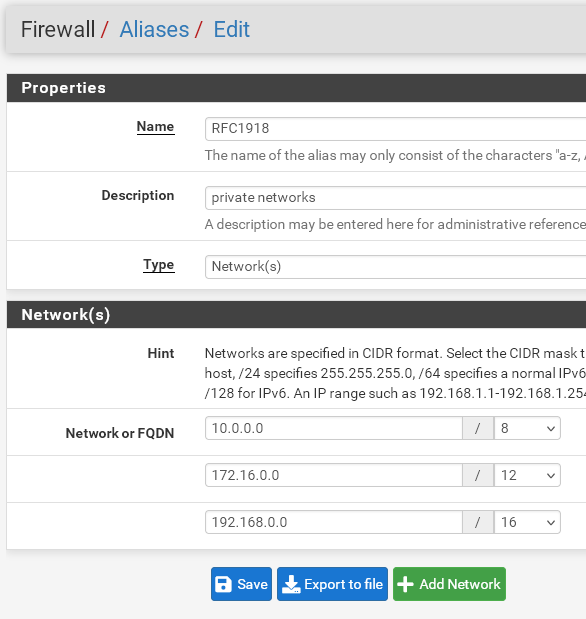
Then you can use it as destination in firewall rules, either in a pass rule with "invert match" checked to restrict the rule to non-private networks only, or in a block rule followed by an allow-any rule.