pfSense as Firewall/Router/Switch all in one - Layer 3 virtual interface?
-
I'm trying to replace a Cisco ASA 5505 with a pfSense firewall. On the Cisco ASA I can assign an inside and an outside interface and hand off to a downstream switch. The downstream switch is L3 capable, so I just run a point-to-point /30 IP between the two and route as I have no need for any additional firewall interfaces (no DMZ for example). But it got me thinking. If I only have a handful of devices behind the firewall and I want to use the pfSense as the firewall/router/switch all in one, can I do that? I don't see a way to create a switched virtual interface where the IP address goes, and then just simply assign ports to the appropriate VLANs (untagged) so that whatever host plugs into that port would get an IP address on the correct VLAN. The physical ports would be purely L1/L2, and the routing would take place at the virtual interface. I see that when I attempt to create a VLAN, it forces me to choose a physical port to assign it to in the form of a parent interface - I don't want to do this. That would mean that even on a small network I'd have to have a physical interface for every VLAN I want to create (or that I wanted to have an L3 interface associated with anyways - I see that I can just create L2 assignments either in the form of a single VLAN or a trunk). This leads me to believe that either pfSense itself doesn't support switched virtual interfaces, or at least not on the hardware I'm using. I've installed the latest stable CE version (2.8.0) on a Cloudgenix ion 2000.
-
@spickles Not following your entire note. Hopefully this is helpful.
First, barring hosts that can tag their own traffic, in general every host that you want to place on a VLAN requires either a switch port somewhere to tag traffic onto the desired VLAN or, for WiFi, an AP that can tag hosts on an SSID onto the desired VLAN. (There are some exceptions to this like using a VLAN-aware switch to tag all traffic from a downstream dumb switch and Ubiquiti's Virtual Network Override, but let's not go there ...)
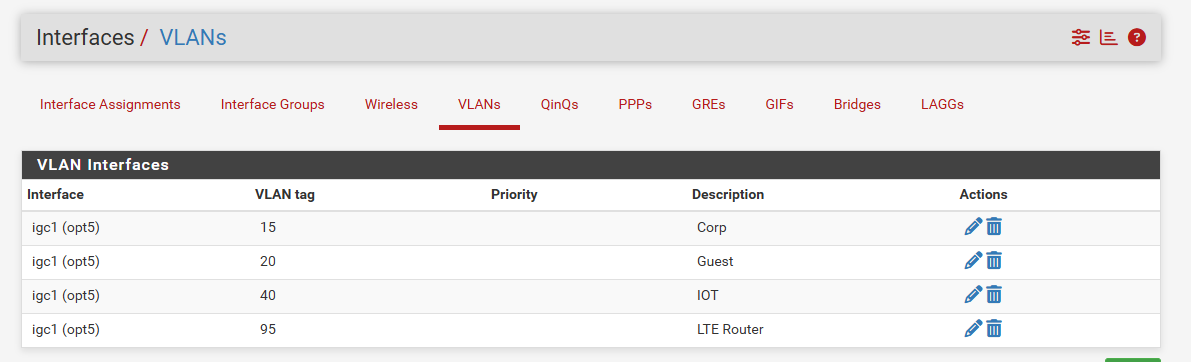
Second, if the question is whether you can create a port on a pfSense box that can process multiple VLANs as separate subnets, the answer is yes. For example, I have a physical port, igc1, carrying 4 tagged VLANs and an untagged one between pfSense and the downstream switch fabric. pfSense routes for all of them.
The four tagged VLANs are all tied to igc1 (so, igc1.15, igc1.20, etc.) under Interfaces>VLANs as shown in the first pic. A pfSense Network Port is created for each. Once created, each can be assigned to an Interface and configured with subnets and addresses under Interfaces/Interface Assignments, have DNS, DHCP, Firewall, etc., just like a physical interface. That's the second pic (black boxes to reduce the distraction of the box's other interfaces). So, 4 tagged VLANs plus 1 untagged on a single port. The untagged interface is igc1.

-
@marcg Thanks for your response. I understand everything you said, but I want to clarify. When creating the VLANs you have port lgc1 (opt5) as the 'parent' interface for all of those VLANs. This is essentially something like how a router-on-a-stick would operate, and that tells me the physical interface has to be up and operational and likely connected to a downstream switch. What I'm looking for is the virtual interface capability. Other hardware vendors allow you to create a VLAN with separate layer 2 and layer 3 components. You create the layer 3 component with the network, default gateway, DHCP, DNS, etc. in one interface with NO requirement to bond it to any physical interface. Then as a separate configuration step you assign the layer 2 components to the interfaces, the VLAN assignment and whether it is tagged or untagged. I do not want to be forced to assign VLANs to a 'parent interface' as I do not plan to attach this pfSense router to anything but clients and APs - no switches. So I want to assign the layer 3 components to a virtual interface that is operational without any dependencies on a physical interface. Then when I add a single PC to a port, I then assign that port to that particular VLAN. In this case it would be untagged because it's the only VLAN on that port. Then when I plug an access point in, then I want multiple VLANs: one untagged for the management plane of the AP and then tagged VLANs for each of the networks/VLANs associated with each SSID. I do not see any way to do this with my current setup, and I do not know if pfSense even has that capability at all. For comparison, two products I know already and use that support this virtual layer 3 interface capability are Cisco and Cradlepoint.
-
@spickles Thanks for the explanation. I think I understand now.
Yes, the example I gave is router on a stick.
I didn't dig deeply, but it appears that while pfSense supports VLAN traffic segregation, it does not support tagging inbound traffic onto a VLAN, i.e., no concept of a PVID that can be set per port (excluding the few Netgate devices with built-in switches). Tagging has to be done downstream: a host that tags its own traffic, a switch or an AP.
You might be able to get something similar to what you describe with bridge groups (haven't played with them myself on pfSense) rather than VLANs. IIUC, each bridge group can be configured with its own router config. That way, all ports in the bridge group would share a gateway/routing/firewall configuration. For individual hosts, their port on the pfSense would be assigned to the relevant bridge group. For the multi-VLAN AP, each VLAN that also support hosts directly attached to the pfSense would be assigned to the bridge group containing those hosts/ports. I've never tested whether VLAN subinterfaces can be assigned to bridge groups, but the GUI seems to support it. The downside of bridge groups is that the bridging is done on the CPU; there's a performance hit.
-
@spickles I would think the easiest way to replace a Cisco ASA 5505 would be use pfsense as a firewall not a router. Keep using your Cisco L3 switch. I do that at my home. I use an Cisco L3 switch and route between my L3 switch and pfsense. You lose pfsense control over your local network. This would not be an issue with you as you will already have that with your L3 switch.
Setup pfsense with no vlans and keep all the vlans on your L3 switch. Then set up your firewall rules and static routes to your L3 switch.